Network Break 151: VMworld Recap; Cisco’s IWAN Roadmap
This week's Network Break recaps news from VMworld, analyzes Cisco's IWAN roadmap, discusses a new cloud security product from Juniper & covers more tech news. The post Network Break 151: VMworld Recap; Cisco’s IWAN Roadmap appeared first on Packet Pushers.Ensuring Good with VMware AppDefense
co-author Geoff Wilmington
Traditional data center endpoint security products focus on detecting and responding to known bad behavior. There are hundreds of millions of disparate malware attacks, with over a million getting added every day. In addition, there is the threat of zero-day attacks exploiting previously unknown vulnerabilities. It becomes a never-ending race to “chase bad” without ever staying ahead of the threat landscape. What if we took an opposite approach to security? What if, instead of “chasing bad” we started by “ensuring good”?
![]() VMware AppDefense is a new security product focused on helping customers build a compute least privilege security model for data center endpoints and provide automated threat detection, response, and remediation to security events. AppDefense is focused on “ensuring good” versus “chasing bad” on data center endpoints. When we focus our attention on what a workload is supposed to be doing, our lens for seeing malicious activity is much more focused and as a result, we narrow the exploitable attack surface of the workload down to what we know about.
VMware AppDefense is a new security product focused on helping customers build a compute least privilege security model for data center endpoints and provide automated threat detection, response, and remediation to security events. AppDefense is focused on “ensuring good” versus “chasing bad” on data center endpoints. When we focus our attention on what a workload is supposed to be doing, our lens for seeing malicious activity is much more focused and as a result, we narrow the exploitable attack surface of the workload down to what we know about.
Changing The Way We Secure Compute
AppDefense applies the concept of “ensuring good” by using three main techniques:
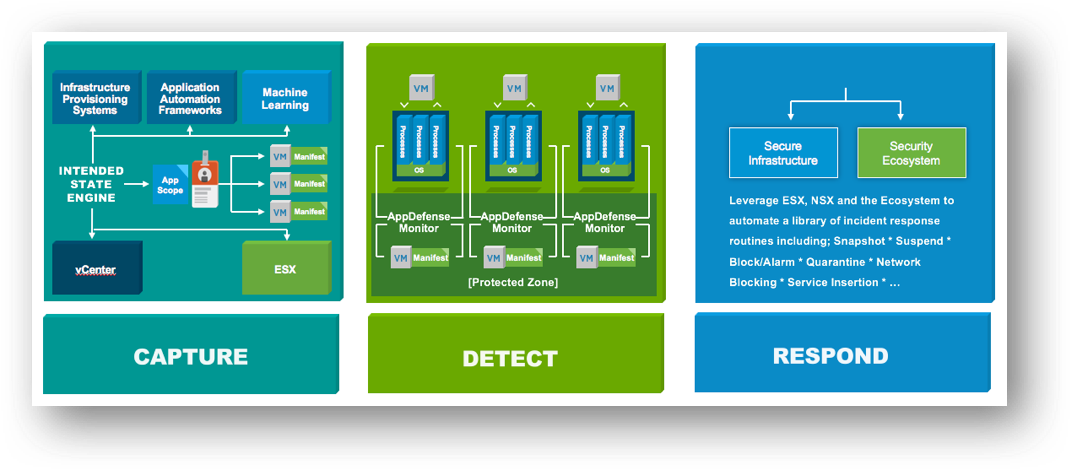
Capture
AppDefense starts by capturing Continue reading
Intent-Based Hype
It all started with a realistic response I got to my automation and orchestration blog post (here’s a unicorn-driving-a-DeLorean one in case you missed it):
Maybe you could also add the "intent-based network" which is also not so far from orchestration?
It got me thinking. The way I understand intent-based whatever, it’s an approach where I tell a system what I want it to do, not how to do it.
Read more ...10 Silly Data Center Memes
Check out these entertaining memes that poke fun at data center life.