Adtran Launches Open Network Alliance for Software-Defined Access
 Adtran likens the alliance to Apple's app store ecosystem.
Adtran likens the alliance to Apple's app store ecosystem.
Datanauts 099: Understanding Microservices
Microservices represent the new application architecture, but is it right for everyone? And what do microservices mean for infrastructure design? The Datanauts explore microservices with guest Bryan Boreham of Weaveworks. The post Datanauts 099: Understanding Microservices appeared first on Packet Pushers.Small Site Multihoming with DHCP and Direct Internet Access
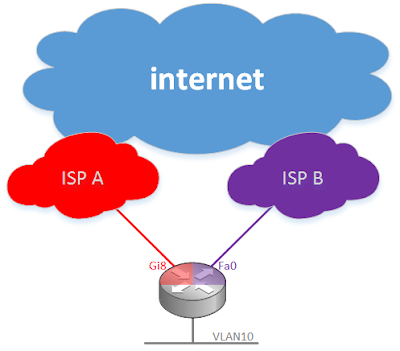
Cisco recently (15.6.3M2 ) resolved CSCve61996, which makes it possible to fail internet access back and forth between two DHCP-managed interfaces in two different front-door VRFs attached to consumer-grade internet service.Prior to the IOS fix there was a lot of weirdness with route configuration on DHCP interfaces assigned to VRFs.
I'm using a C891F-K9 for this example. The WAN interfaces are Gi0 and Fa8. They're in F-VRF's named ISP_A and ISP_B respectively:
First, create the F-VRFs and configure the interfaces:
ip vrf ISP_A
ip vrf ISP_B
interface GigabitEthernet8
ip vrf forwarding ISP_A
ip dhcp client default-router distance 10
ip address dhcp
interface FastEthernet0
ip vrf forwarding ISP_B
ip dhcp client default-router distance 20
ip address dhcp
The distance commands above assign the AD of the DHCP-assigned default route. Without these directives the distance would be 254 in each VRF. They're modified here because we'll be using the distance to select the preferred internet path when both ISPs are available.
Next, let's keep track of whether or not the internet is working via each provider. In this case I'm pinging 8.8.8.8 via both paths, but this health check can be whatever makes sense for your situation. So, Continue reading
Startups have Screwed Up Work Culture
Dan Lyons talks about the dysfunctional side of working at a startup.
The post Startups have Screwed Up Work Culture appeared first on EtherealMind.
Worth Reading: IoT needs a paradigm shift
The post Worth Reading: IoT needs a paradigm shift appeared first on rule 11 reader.
History Of Networking – Juliusz Chroboczek – Babel Routing Protocol
Babel is a relatively new routing protocol when compared to some of the more well established options, but due to some of its design considerations, it is very well suited for routing on distributed mesh networks. Babel’s creator, Juliusz Chroboczek, joins the Network Collective team in discussing how Babel came about, some of the design decisions when creating it, and what the future looks like for this emerging technology.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post History Of Networking – Juliusz Chroboczek – Babel Routing Protocol appeared first on Network Collective.
History Of Networking – Juliusz Chroboczek – Babel Routing Protocol
Babel is a relatively new routing protocol when compared to some of the more well established options, but due to some of its design considerations, it is very well suited for routing on distributed mesh networks. Babel’s creator, Juliusz Chroboczek, joins the Network Collective team in discussing how Babel came about, some of the design decisions when creating it, and what the future looks like for this emerging technology.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post History Of Networking – Juliusz Chroboczek – Babel Routing Protocol appeared first on Network Collective.
IS-IS Overload Bit – Why IS-IS Overload bit is used ? What are the use cases ?
IS-IS Overload Bit – Why IS-IS Overload bit is used ? What are the use cases ? In this post, I will explain the Overload bit which is an important feature of IS-IS routing protocol. When a router which runs an IS-IS routing protocol have resource issue (CPU, Memory), device shouldn’t receive network traffic. […]
The post IS-IS Overload Bit – Why IS-IS Overload bit is used ? What are the use cases ? appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
How Accurate Is Your Protocol Analyzer?
When it comes to packet capture, a hardware analyzer will produce different results vs. a software-based tool.