China Unicom Will Test 5G Using Cavium Silicon and M-CORD Racks
![]() The two companies are demonstrating multi-access edge computing in Shanghai this week.
The two companies are demonstrating multi-access edge computing in Shanghai this week.
Silver Peak Touts Service Provider Strategy with China Telecom Deal
 This isn’t China Telecom’s first SD-WAN deal.
This isn’t China Telecom’s first SD-WAN deal.
Google, Nutanix Partnership Boosts Hybrid Cloud Strategy
 Nutanix kicks off its .NEXT 2017 conference today.
Nutanix kicks off its .NEXT 2017 conference today.
VMware Evolve Transform Security is Coming to A City Near You!
 Modern IT professionals face significant security challenges. As digital transformation continues to connect applications, users, and data in the cloud, perimeter security models that once offered businesses protection are no longer sufficient.
Modern IT professionals face significant security challenges. As digital transformation continues to connect applications, users, and data in the cloud, perimeter security models that once offered businesses protection are no longer sufficient.
VMware Evolve Transform Security is Coming to A City Near You!
Modern IT professionals face significant security challenges. As digital transformation continues to connect applications, users, and data in the cloud, perimeter security models that once offered businesses protection are no longer sufficient. Critical visibility into users and endpoints is missing, enforcing policies is difficult, and, in the meantime, cyberattacks are more sophisticated and costly than ever.
What do IT teams need to defend today’s applications, users, and data from potentially brand-damaging attacks?
That’s the question VMware experts will be tackling during our VMware EVOLVE Transform Security events, coming to a city near you. During these half-day, in-person events, you will learn how a ubiquitous software layer can help support the security challenges of the modern business.
VMware experts will guide you through how to:
- Secure application infrastructure and better align security controls to apps
- Secure identity and endpoints to control access and enforce data loss prevention
- Streamline governance, risk management and compliance to limit cyber-attack vectors
Reserve your spot at an upcoming Transform Security-focused VMware EVOLVE event in your city:
The post VMware Evolve Transform Security is Coming to A City Near You! appeared first on Network Virtualization.
Let’s Think Differently to Shape Tomorrow
In 2015 the world made one of the biggest promises to itself in the form of 17 Global Goals set out by the United Nations. These goals – the Sustainable Development Goals (SDGs) – are aimed at achieving extraordinary things in the next 15 years. They are dedicated to fighting injustice and inequalities, ending climate change, beating discrimination, bringing in sustainable energy, and making sure no one goes hungry.
Stupidly Simple DDoS Protocol (SSDP) generates 100 Gbps DDoS
Last month we shared statistics on some popular reflection attacks. Back then the average SSDP attack size was ~12 Gbps and largest SSDP reflection we recorded was:
- 30 Mpps (millions of packets per second)
- 80 Gbps (billions of bits per second)
- using 940k reflector IPs
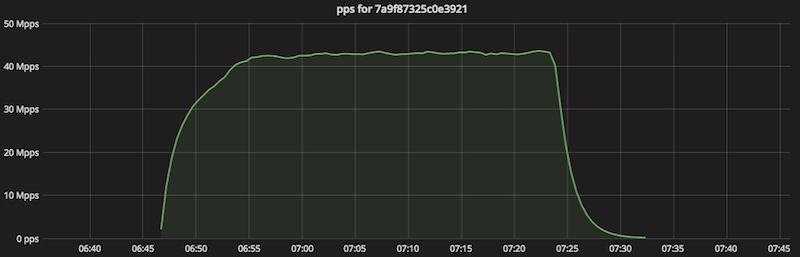
This changed a couple of days ago when we noticed an unusually large SSDP amplification. It's worth deeper investigation since it crossed the symbolic threshold of 100 Gbps.
The packets per second chart during the attack looked like this:
The bandwidth usage:

This packet flood lasted 38 minutes. According to our sampled netflow data it utilized 930k reflector servers. We estimate that the during 38 minutes of the attack each reflector sent 112k packets to Cloudflare.
The reflector servers are across the globe, with a large presence in Argentina, Russia and China. Here are the unique IPs per country:
$ cat ips-nf-ct.txt|uniq|cut -f 2|sort|uniq -c|sort -nr|head
439126 CN
135783 RU
74825 AR
51222 US
41353 TW
32850 CA
19558 MY
18962 CO
14234 BR
10824 KR
10334 UA
9103 IT
...
The reflector IP distribution across ASNs is typical. It pretty much follows the world’s largest residential ISPs:
$ cat ips-nf-asn.txt |uniq|cut -f 2|sort|uniq Continue readingWorth Reading: The blue disco ball
The post Worth Reading: The blue disco ball appeared first on rule 11 reader.
As 5G Looms, Service Providers Need to Consider CGNAT
 The 5G buzz is building and along with it are projections that some 5G networks will launch in 2018, with more widespread deployment in 2019. The launch of 5G networks will contribute to the large-scale proliferation of Internet of Things (IoT) devices.
The 5G buzz is building and along with it are projections that some 5G networks will launch in 2018, with more widespread deployment in 2019. The launch of 5G networks will contribute to the large-scale proliferation of Internet of Things (IoT) devices.
Datanauts 090: AWS Networking Deep Dive
AWS and public cloud networking is not just VLANs. The Datanauts and guest Anthony Miloslavsky explore essential network constructs and architectural choices The post Datanauts 090: AWS Networking Deep Dive appeared first on Packet Pushers.Cisco Vs Ruckus Wireless Systems
High Scale (vSZ-H) - up to10,000 APs, up to 100,000 clients
vSZ-H cluster of 4 - up to 30,000 Continue reading
Programming a Cisco Network Using Python
David Bombal demonstrates how to configure multiple Cisco switches using Python and GNS3.
New Petyawrap Ransomware Attack Again Highlights Critical Need For Security Processes
Whenever there's a new attack on a global scale, the world trusts the Internet a little less. Today we are concerned with the many reports about this new ransomware attack called "Petyawrap", "Petrwrap" or an older name of "Petya."
The sad fact is: this new attack exploits the same vulnerabilities in Windows systems as last month's WannaCry attack.
Fixes have been available for most Windows systems since March 2017!
The same tips Niel Harper provided last month to protect against ransomware also apply here.