Unlocking IT Success: Navigating Talent Shortages with Integrated Solutions
Integrated solutions help overcome IT talent shortages, streamline IT operations, reduce costs, and empower existing talent.KU039: Prepping For KubeCon North America 2023
Grab a rundown of what to expect at KubeCon NA this year as Kubernetes Unpacked co-host Michael Levan prepares to hit the conference floor.
The post KU039: Prepping For KubeCon North America 2023 appeared first on Packet Pushers.
KU039: Prepping For KubeCon North America 2023
The KubeCon excitement is catching as Michael Levan gets ready to attend for the first time. Grab a rundown of what to expect at the North American event this year as he and Kristina Devochko review sessions and provide advice on how to tackle the massive amount of content that’s on the schedule. A strong... Read more »Hedge 201: Roundtable
It’s time to gather round the hedge and discuss whatever Eyvonne, Tom, and Russ find interesting! In this episode we discuss business logic vulnerabilities, and how we often forget to think outside the box to understand the attack surfaces that matter. We also discuss upcoming network speed increases like Wi-Fi 7 and 800G Ethernet. Do we really need these speeds, or are we just getting caught up in a hype cycle?
IPv6 Buzz 138: Making Sense Of DHCPv6 Prefix Delegation (DHCPv6-PD)
DHCPv6 Prefix Delegation (DHCPv6-PD) is an IETF RFC that lets a router delegate a long-lived prefix, using DHCP, to a requesting router. The hosts discuss how this is used today both by service providers and in the enterprise, and potential impacts on address allocation and planning.
The post IPv6 Buzz 138: Making Sense Of DHCPv6 Prefix Delegation (DHCPv6-PD) appeared first on Packet Pushers.
IPB138: Making Sense Of DHCPv6 Prefix Delegation (DHCPv6-PD)
DHCPv6 Prefix Delegation (DHCPv6-PD) is an IETF RFC that lets one router delegate a long-lived prefix, using DHCP, to a requesting router. What’s the need for this? As the RFC notes, some applications expect stable addresses. It also notes: It is appropriate for situations in which the delegating router does not have knowledge about the... Read more »BGP Labs: Build a Transit Network with IBGP
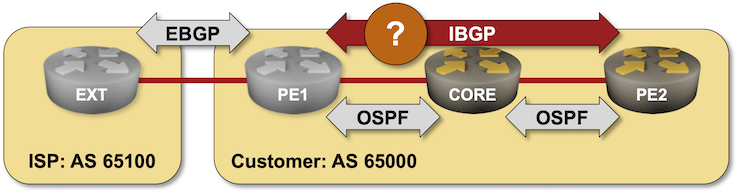
Last time we built a network with two adjacent BGP routers. Now let’s see what happens when we add a core router between them:

BGP Labs: Build a Transit Network with IBGP
Last time we built a network with two adjacent BGP routers. Now let’s see what happens when we add a core router between them:
Cloudflare incident on October 30, 2023

Multiple Cloudflare services were unavailable for 37 minutes on October 30, 2023. This was due to the misconfiguration of a deployment tool used by Workers KV. This was a frustrating incident, made more difficult by Cloudflare’s reliance on our own suite of products. We are deeply sorry for the impact it had on customers. What follows is a discussion of what went wrong, how the incident was resolved, and the work we are undertaking to ensure it does not happen again.
Workers KV is our globally distributed key-value store. It is used by both customers and Cloudflare teams alike to manage configuration data, routing lookups, static asset bundles, authentication tokens, and other data that needs low-latency access.
During this incident, KV returned what it believed was a valid HTTP 401 (Unauthorized) status code instead of the requested key-value pair(s) due to a bug in a new deployment tool used by KV.
These errors manifested differently for each product depending on how KV is used by each service, with their impact detailed below.
What was impacted
A number of Cloudflare services depend on Workers KV for distributing configuration, routing information, static asset serving, and authentication state globally. These services instead received Continue reading