Workflow Enhanced Networking (WEN)
Software Defined Networking (SDN) offered lots of hope, a centralized control-plane, programmable network functions and authenticated network nodes. Once we all stopped laughing and rolling around the floor with rib ache, the reality of SDN dawned quickly. It was a nice academic thought and set of experiments, but for the masses, the original meaning of SDN has changed significantly. The software giants with mountains of cash will drive technology like this early and possibly pave the way for the rest of us eventually, but for the masses of enterprises that vendors serve and that have more immediate requirements, SDN isn’t something that’s had massive adoption. The question of ‘why’ is a pretty obvious place to start and you don’t have to look too far before you find answers.
I will not get in to the overlay and underlay arguments here. These have been done to death already. Lots of organizations and vendors offer various takes on the middle-ground, far left and far right. This isn’t a product pitch either.
This post is around the “next onwards step” as opposed to changing the world. I also ‘feel’, this is the natural pull as opposed to the industry push we’ve come to Continue reading
Have to choose between VMware NSX and Cisco ACI? You’re Not Alone
I keep getting questions along the lines of “should I go with VMware NSX or should I deploy Cisco ACI” every single week, and as you know it’s hard to answer anything but it depends without spending hours on the topic.
That’s exactly what we plan to do in Zurich next Tuesday (May 16th) in a DIGS workshop that will run in parallel with the Data Center & Cloud Day (part of the SIGS Technology Conference).
Read more ...Colombo, Sri Lanka: Six million Internet properties now faster for six million Internet users

We are excited to add four new data centers this week to Cloudflare's growing network, beginning with Colombo, Sri Lanka. This deployment is our 112th data center globally, and our 38th in Asia.
Faster Performance

CC BY-NC-ND 2.0 image by Pavel Dobrovsky
Six million Internet properties using Cloudflare are now even faster across the island country of Sri Lanka. Previously, local visitors to Cloudflare customers were served out of our Singapore or Dubai data centers.
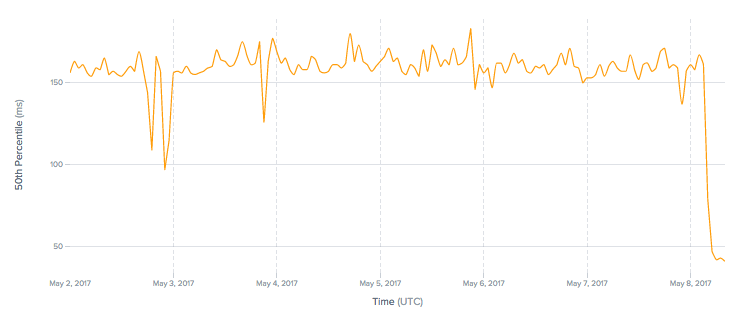 Latency (ms) decreases 4x to Cloudflare customers. Source: Cedexis
Latency (ms) decreases 4x to Cloudflare customers. Source: Cedexis
Sri Lanka added over one million Internet users in the past year alone. At ~30% Internet penetration, there is considerable room to grow.
Next Three Cities
Our deployments to be revealed later this week will provide additional redundancy to existing facilities in North America and Africa.
If you enjoy the idea of helping build one of the world's largest networks, come join our team!
Liveblog: Deploying Containerized OpenStack: Challenges & Tools Comparison
This is a liveblog for an OpenStack Summit session on containerized OpenStack and a comparison of the tools used for containerized OpenStack. The speaker is Jaivish Kothari, from NEC Technologies. Two other speakers were listed on the title slide, but were apparently unable to make it to the Summit to present.
Kothari provides a brief overview of the session, then jumps into a discussion of deployment tools. As illustrated by one of his slides, there’s a huge collection of tools that are used to deploy OpenStack; some are “pure” deployment tools, others are configuration management tools. In this presentation, Kothari says he will focus specifically on OpenStack deployment tools, like Juju (Canonical), Fuel (Mirantis), Crowbar (Dell), and PackStack/TripleO (Red Hat), but I’m not sure how this relates to containerized OpenStack (per the session title).
According to Kothari, some of the challenges in “traditional” (non-containerized) deployment tools are best understood by looking at the challenges in deploying OpenStack:
- Difficulty related to deployment (conflicts due to services configuration, deployment still prone to failures)
- Ongoing lifecycle management of OpenStack components
This whole first section of the presentation was setting up the argument that containerizing your OpenStack control plane will help address these challenges. Continue reading
Liveblog: Kuryr Project Update
This is a liveblog of an OpenStack Summit session providing an update on the Kuryr project. The speakers are Antoni Segura Puimedon and Irena Berezovsky. Kuryr, if you recall, was a project aimed at making OpenStack Neutron functionality available to Docker containers; it has since expanded to also offer Cinder and Manila storage to Docker containers, and has added support for both Docker Swarm and Kubernetes as well.
According to Puimedon, the latest release of Kuryr has a diverse base of contributors, with over 45 active contributors.
So, what will be in the Pike release? For the Kubernetes-specific support:
- This will be the first release
- Support for Kubernetes Services (this leverages LBaaS v2)
- Client- and server-side SSL support
- RDO packaging
What’s planned for Pike, but may not actually make it? (Again, this is for Kubernetes support.)
- Token support
- Resource pools
- Improved support for Services defined as LoadBalancer type
On the Docker side, the following new features and enhancements will arrive in Pike:
- Support for Swarm mode
- IPv4 and IPv6 networking
- TLS support between Docker and the libnetwork plugin
On the Fuxi side, Kuryr is adding support for Manila shares.
At this point, Berezovsky takes over to discuss the release Continue reading
VMware’s Distro of OpenStack Comes Free for vSphere Customers
 The biggest use case for VIO is to create developer clouds.
The biggest use case for VIO is to create developer clouds.
Nokia NFVi Report Webinar Q&A: Why Nokia’s OCP-compliant AirFrame and SDN Solutions form the perfect NFVi Foundation
 Thanks to all who joined us for the Nokia NFVI Report Webinar, Why Nokia’s OCP-compliant AirFrame and SDN Solutions form the perfect NFVi Foundation. Read the full Q&A.
Thanks to all who joined us for the Nokia NFVI Report Webinar, Why Nokia’s OCP-compliant AirFrame and SDN Solutions form the perfect NFVi Foundation. Read the full Q&A.
African Regional Internet & Development Dialogue Tackles the World of Education
Dates 8-9 May, Kigali, Rwanda
The first ever African Regional Internet Development Dialogue (RIDD) was launched in Rwanda, Kigali on the 8 of May 2017, placing SDG 4 on Education at the center of the conversation of the first day of the meeting. Delegates had an opportunity to explore how the Internet can provide quick wins for education, but most importantly come up with real solutions that can be implemented immediately.
For Africa a skilled workforce that utilizes ICTs effectively is a key factor in determining its competitiveness in the global digital economy and fully exploiting its potential for sustainable growth. It is the basis for social and economic development, and the foundation of an Internet for everyone.
Worth Reading: Be careful what you wish for
The post Worth Reading: Be careful what you wish for appeared first on rule 11 reader.