Do You Needs 2.5 and 5 Gigabit Ethernet?
Here are some reasons enterprises may want to leverage the new IEEE standard.
Off The Cuff – Cisco Acquiring Viptela
In this Off The Cuff episode of Network Collective, we talk about all aspects of Cisco’s announcement of their intent to acquire Viptela’s SD-WAN product. Who wins in this deal? What happens to Cisco’s existing SD-WAN product line? What happens to the rest of the SD-WAN market? Keith Townsend and Tom Hollingsworth join the Network Collective hosts in breaking down what this means for all involved.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
Audio Only Podcast Feed:
The post Off The Cuff – Cisco Acquiring Viptela appeared first on Network Collective.
Off The Cuff – Cisco Acquiring Viptela
In this Off The Cuff episode of Network Collective, we talk about all aspects of Cisco’s announcement of their intent to acquire Viptela’s SD-WAN product. Who wins in this deal? What happens to Cisco’s existing SD-WAN product line? What happens to the rest of the SD-WAN market? Keith Townsend and Tom Hollingsworth join the Network Collective hosts in breaking down what this means for all involved.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
Audio Only Podcast Feed:
The post Off The Cuff – Cisco Acquiring Viptela appeared first on Network Collective.
Apstra Updates Intent-Based OS
 AOS 1.2 offers “full network transparency.”
AOS 1.2 offers “full network transparency.”
Juniper Control Plane Protection
How Does Internet Work - We know what is networking
I already wrote about Control Plane Protection in one of my previous posts focused on Cisco device configuration. Here we will make the same thing on Juniper device, I was using Juniper SRX300 and Juniper SRX1500 devices in my lab. CoPP ?? Control Plane Protection (CoPP) is a method of protecting processor unit, running services on your network device, against excessive flooding. Excessive flooding of traffic aimed towards your router/firewall processor, being that valid or malicious, is always undesirable and can also be dangerous. A network device, which starts the receive more control traffic that his processor can process, will
Securing Network Automation Video Is Online
The awesome Troopers crew published conference videos, including my Securing Network Automation presentation (more, including slide deck).
Learning Python: Week2 (Printing, Numbers, and Lists) -Part 3
As discussed in last post, ( https://crazyrouters.wordpress.com/2017/02/25/learning-python-kirk-byers-python-course/ ) , i will be sharing the my learning on weekly basis as course continues. This will not only motivate me but also help others who are in phase of learning python 3. Here we are going to discuss the Exercise 2 . Here is the Exercise 2 […]Kubernetes Networking 101 – Ingress resources
I called my last post ‘basic’ external access into the cluster because I didn’t get a chance to talk about the ingress object. Ingress resources are interesting in that they allow you to use one object to load balance to different back-end objects. This could be handy for several reasons and allows you a more fine-grained means to load balance traffic. Let’s take a look at an example of using the Nginx ingress controller in our Kubernetes cluster.
To demonstrate this we’re going to continue using the same lab that we used in previous posts but for the sake of level setting we’re going to start by clearing the slate. Let’s delete all of the objects in the cluster and then we’ll start by build them from scratch so you can see every step of the way how we setup and use the ingress.
kubectl delete deployments --all kubectl delete pods --all kubectl delete services --all
Since this will kill our net-test pod, let’s start that again…
kubectl run net-test --image=jonlangemak/net_tools
Recall that we used this pod as a testing endpoint so we could simulate traffic originating from a pod so it’s worth keeping around.
Alright – now that we Continue reading
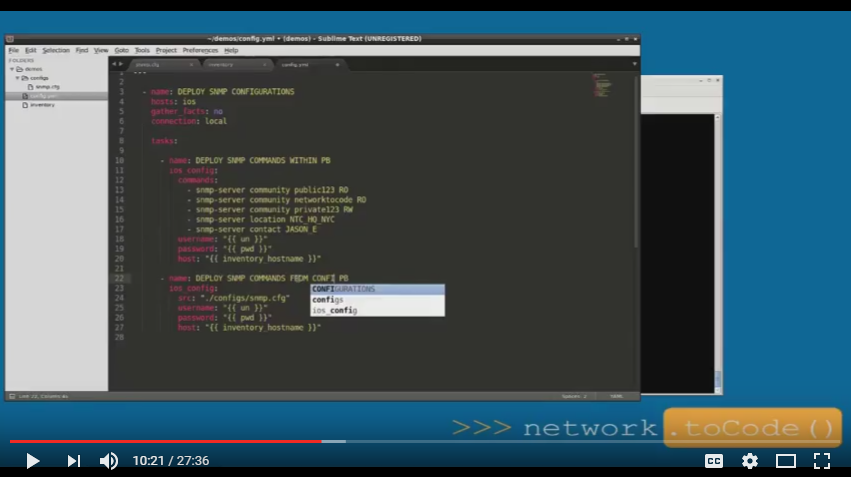
Using the Ansible ios_config Module
I get asked often on how to perform specific network automation tasks with Ansible. There were a few questions recently pertaining to the ios_config module within Ansible core, so I decided to record a video to show different options you have when using it to deploy global configuration commands on IOS devices.
Here is a summary of the four (4) options covered:
- Embed commands in your playbook and reference them using the
commands(or lines) parameter. - Use the
srcparameter and reference a configuration file with one or more commands in it. - Use the
srcparameter and reference a Jinja2 template such that it inserts variables into the template, creating a list of commands, and deploys them to a device. - Use two tasks. In Task 1, use the
templatemodule and reference a Jinja2 template to auto-generate a configuration file. In Task 2, use theios_configmodule and reference the config file built in Task 1 to deploy the commands from the file. This is often used instead of option #3 since it allows you to store/view the config file before deploying fully de-coupling the build and deploy processes.
The video does assume some existing knowledge on using Ansible. The Continue reading
Using the Ansible ios_config Module
I get asked often on how to perform specific network automation tasks with Ansible. There were a few questions recently pertaining to the ios_config module within Ansible core, so I decided to record a video to show different options you have when using it to deploy global configuration commands on IOS devices.
Here is a summary of the four (4) options covered:
- Embed commands in your playbook and reference them using the
commands(or lines) parameter. - Use the
srcparameter and reference a configuration file with one or more commands in it. - Use the
srcparameter and reference a Jinja2 template such that it inserts variables into the template, creating a list of commands, and deploys them to a device. - Use two tasks. In Task 1, use the
templatemodule and reference a Jinja2 template to auto-generate a configuration file. In Task 2, use theios_configmodule and reference the config file built in Task 1 to deploy the commands from the file. This is often used instead of option #3 since it allows you to store/view the config file before deploying fully de-coupling the build and deploy processes.
The video does assume some existing knowledge on using Ansible. The Continue reading
China Mobile Tests VNFs with Enea’s Software
 Enea works for, and competes with, Ericsson and Nokia.
Enea works for, and competes with, Ericsson and Nokia.