Managing Quality: The Other Side of the SDN/NFV Mountain
 2016 may be looked at as the year that SDN and NFV really took hold.
2016 may be looked at as the year that SDN and NFV really took hold.
OSPF Best Practices
OSPF Best Practices Understanding and using best practices is very important though may not be feasible in all networks due to budget , political or other technical constraints. In this post I will explain the best practices on OSPF networks. This best practices come from my real life design and deployment experience , knowledge […]
The post OSPF Best Practices appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
How the IETF community is shaping technology to build a better society
The continued advancement in technological landscape enabling more people having Internet access in the global arena has meant that IETF (Internet Engineering Task Force) remains at the forefront of integrating technology with humanity. In fact, IETF has made significant use of social dimension to articulate its area of work and research. It is beautifully reflected in section 4.1 of the RFC 3935 wherein it states that “We want the Internet to be useful for communities that share our commitment to openness and fairness. We embrace technical concepts such as decentralized control, edge-user empowerment and sharing of resources, because those concepts resonate with the core values of the IETF community”.
Vodafone Selects Nuage for its ‘Project Ocean’ Data Center Virtualization
 Nuage is also working with Vodafone on SD-WAN.
Nuage is also working with Vodafone on SD-WAN.
Amid U.S. Sanctions Breach, ZTE Appoints New Chairman
 The company is separating the roles of chairman and president.
The company is separating the roles of chairman and president.
Taking A Stand Against Corruption
Over the last few months, I’ve noticed that some pages on this site have been returning what appear to be corrupted pages, looking something like this:

Or like this:
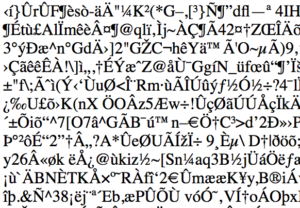
Pretty, aren’t they? Typically if the user hits refresh the page will come back as it should have done first time. I’ve been working for many weeks now to track down why this was happening. One thing I noted is that the corrupted files were smaller than the non-corrupted equivalent, suggesting that the file was either truncated or, more likely, compressed. Opening a downloaded file in a text editor showed that the header of these corrupted pages begins like this:

Some of you are probably feeling smug right now because you know that the first three bytes of a gzip file are 1F 8B 08. The ASCII code for 0x1F is Ctrl-_; there’s no code for 0x8B; ASCII 0x08 is the same as Ctrl-H (i.e. backspace). This should look familiar in the image above: ^_ <8B> ^H. In other words, the client is receiving a GZIPped version of the page but presumably was told that the mime type was text/html. The end result is the garbled mess we saw above. So now Continue reading
