IPv6 Internet router using merchant silicon
Internet router using merchant silicon describes how a commodity white box switch can be used as a replacement for an expensive Internet router. The solution combines standard sFlow instrumentation implemented in merchant silicon with BGP routing information to selectively install only active routes into the hardware.The article describes a simple self contained solution that uses standard APIs and should be able to run on a variety of Linux based network operating systems, including: Cumulus Linux, Dell OS10, Arista EOS, and Cisco NX-OS.
The diagram shows the elements of the solution. Standard sFlow instrumentation embedded in the merchant silicon ASIC data plane in the white box switch provides real-time information on traffic flowing through the switch. The sFlow agent is configured to send the sFlow to an instance of sFlow-RT running on the switch. The Bird routing daemon is used to handle the BGP peering sessions and to install routes in the Linux kernel using the standard netlink interface. The network operating system in turn programs the switch ASIC with the kernel routes so that packets are forwarded by the switch hardware and not by the kernel software.
The key to this solution is Bird's multi-table capabilities. The full Internet Continue reading
The Year in NV Trends for 2016
 The NV market continues to grow and evolve, supporting many different technologies and vendor platforms as customers look for the right mix.
The NV market continues to grow and evolve, supporting many different technologies and vendor platforms as customers look for the right mix.
PQ Show 101: Kentik NPM For Cloud & DDoS Detection (Sponsored)
Kentik CEO Avi Freedman joins us on this sponsored episode to talk about new capabilities in the Kentik platform, including network performance monitoring for the cloud, as well as DDoS and anomaly detection. The post PQ Show 101: Kentik NPM For Cloud & DDoS Detection (Sponsored) appeared first on Packet Pushers.How to Spot a Fake Facebook Account
Ever get a friend request from someone you don’t know and have never met before? More often than not, these accounts are created by criminals looking to harvest your personal information, or scam you in some other fashion.
It typically starts when you receive a friend request from someone you don’t know. And you have no mutual friends in common:
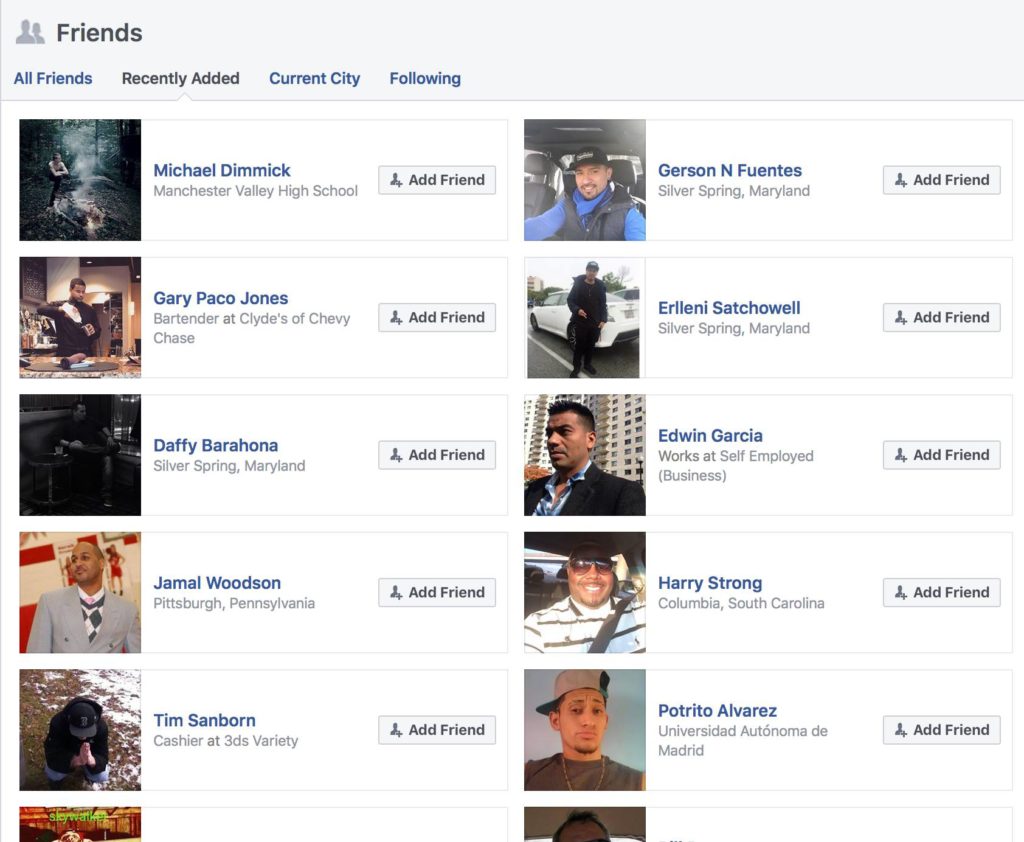
A dead giveaway is looking at their Recently Added Friends. In this case, this person has accumulated a lot of new friends in a very short period of time. Notice they are all guys. Guys are more willing to accept a friend request from someone they don’t know, especially if it’s attached to a pretty face.
Also note that there are no mutual friends in common:
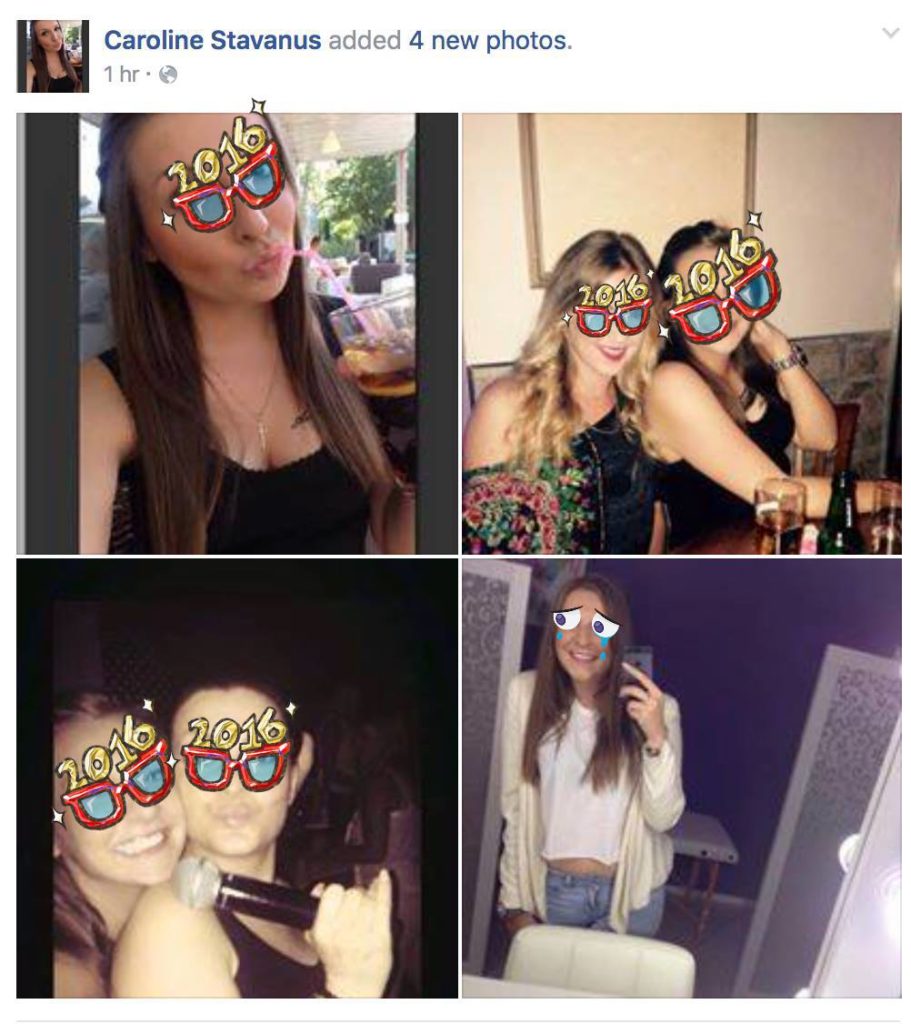
Another tell tale sign is that all the pictures associated with the account have been added quite recently, in this case, in the last hour. This indicates this is a new account, not one that has been a legitimate account for a long time:
NOTE: Pictures have been masked to protect the innocent. In this case, some unknowing girl has had her pictures harvested by the scammer for the purpose of running this endeavor.
If they don’t respond to an inquiry Continue reading
Gen-Z Promises Performance Boost
Industry consortium is developing a new interconnect to avoid storage bottlenecks.
What IT Teams Really Want This Holiday Season
IT pros' wish list runs the gamut from IoT standards and continuing education to real time off.
Would You Use Avaya’s SPBM Solution?
Got this comment to one of my L2-over-VXLAN blog posts:
I found the Avaya SPBM solution "right on the money" to build that L2+ fabric. Would you deploy Avaya SPBM?
Interestingly, I got that same question during one of the ExpertExpress engagements and here’s what I told that customer:
Read more ...QKD – How Quantum Cryptography Key Distribution Works
How Does Internet Work - We know what is networking
QKD – Quantum key distribution is the magic part of quantum cryptography. Every other part of this new cryptography mechanism remains the same as in standard cryptography techniques currently used. By using quantum particles which behave under rules of quantum mechanics, keys can be generated and distributed to receiver side in completely safe way. Quantum mechanics principle, which describes the base rule protecting the exchange of keys, is Heisenberg’s Uncertainty Principle. Heisenberg’s Uncertainty Principle states that it is impossible to measure both speed and current position of quantum particles at the same time. It furthermore states that the state of observed particle will change if and