Virtual PortChannel (vPC) Cheat Sheet Released

Here is the Cisco Virtual PortChannel (vPC) Cheat Sheet on Nexus platform, which allows links that are physically connected to two different Cisco Nexus 5K/7K Series devices to appear as a single PortChannel to a third device.
If you find a bug or want new content to be added, please report it!
Virtual PortChannel (vPC) Cheat Sheet Released

Here is the Cisco Virtual PortChannel (vPC) Cheat Sheet on Nexus platform, which allows links that are physically connected to two different Cisco Nexus 5K/7K Series devices to appear as a single PortChannel to a third device.
If you found a bug or want new content to be added, please report it!
Cisco Predicts Low Single-Digit Revenue Declines in Q2
 The security portfolio is doing well, though.
The security portfolio is doing well, though.
Microsoft Becomes a Member of The Linux Foundation
 Microsoft has been helping Linux Foundation for years now.
Microsoft has been helping Linux Foundation for years now.
Google Pushes ‘Radical’ Spectrum Model For 5G
 Imagine a neutral-host network where operators and even enterprises share the cost.
Imagine a neutral-host network where operators and even enterprises share the cost.
IBM Drops $200M on New Security Capabilities
 This includes its acquisition of Resilient Systems.
This includes its acquisition of Resilient Systems.
NEC Will Infuse AI Into GE Predix
 Predix is a star at GE's Minds+Machines event.
Predix is a star at GE's Minds+Machines event.
Worth Reading: Cheap IoT Threatens the Internet
The post Worth Reading: Cheap IoT Threatens the Internet appeared first on 'net work.
MikroTik RouterOS new feature – Loop Protect
‘Loop Protect’ – New feature in 6.37rc24
Long-time MikroTik users have been after better loop prevention mechanisms for quite a while now. Rapid STP within bridges was the only feature available up until Fall of 2016 and now MikroTik has released Rapid Spanning Tree in hardware for switched ports as well as a new Loop Protect feature that seems to serve the same function as Cisco’s Loop Guard but not utilize spanning tree to detect the loop. MikroTik’s version compares the source MAC of the loop protect frame with the MAC of the interface it is received on and if they match, it will disable the port until the timer expires and check again for the existence of a loop.
This feature was introduced in 6.37rc24 on August 31st, 2016.

http://wiki.mikrotik.com/wiki/Manual:Loop_Protect
Use cases for ‘Loop Protect’
Loop protect seems to be designed more as an edge port protocol since it physically disables the port upon detection of a loop, whereas STP will leave the port physically active but logically block traffic on that path. Some potential use cases for enabling this feature could include:
- Edge port on a MikroTik device facing the end subscriber equipment Continue reading
MikroTik RouterOS new feature – Loop Protect
‘Loop Protect’ – New feature in 6.37rc24
Long-time MikroTik users have been after better loop prevention mechanisms for quite a while now. Rapid STP within bridges was the only feature available up until Fall of 2016 and now MikroTik has released Rapid Spanning Tree in hardware for switched ports as well as a new Loop Protect feature that seems to serve the same function as Cisco’s Loop Guard but not utilize spanning tree to detect the loop. MikroTik’s version compares the source MAC of the loop protect frame with the MAC of the interface it is received on and if they match, it will disable the port until the timer expires and check again for the existence of a loop.
This feature was introduced in 6.37rc24 on August 31st, 2016.
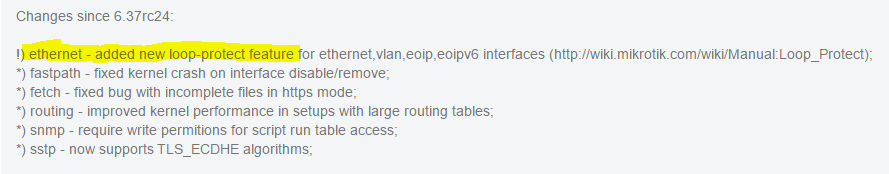
http://wiki.mikrotik.com/wiki/Manual:Loop_Protect
Use cases for ‘Loop Protect’
Loop protect seems to be designed more as an edge port protocol since it physically disables the port upon detection of a loop, whereas STP will leave the port physically active but logically block traffic on that path. Some potential use cases for enabling this feature could include:
- Edge port on a MikroTik device facing the end subscriber equipment Continue reading