Heavy Networking 691: Why OOB Infrastructure Is Critical For IT Ops & Automation With ZPE Systems (Sponsored)
On today’s Heavy Networking podcast, we look at how sponsor ZPE Systems is rethinking Out-Of-Band management for automated, NetOps-driven infrastructure. This includes tasks like device staging, deployments, upgrades, and more. And you don’t just have to take ZPE’s word for it; we also talk to a customer who’s using the products to run a retail business with a lean networking team that supports more than fifty sites.
The post Heavy Networking 691: Why OOB Infrastructure Is Critical For IT Ops & Automation With ZPE Systems (Sponsored) appeared first on Packet Pushers.
Heavy Networking 691: Why OOB Infrastructure Is Critical For IT Ops & Automation With ZPE Systems (Sponsored)
On today’s Heavy Networking podcast, we look at how sponsor ZPE Systems is rethinking Out-Of-Band management for automated, NetOps-driven infrastructure. This includes tasks like device staging, deployments, upgrades, and more. And you don’t just have to take ZPE’s word for it; we also talk to a customer who’s using the products to run a retail business with a lean networking team that supports more than fifty sites.Tia Hopkins on Why the Modern Infrastructure Needs New Resiliency Ideas
In her Network Resilience Boot Camp keynote address, eSentire’s Tia Hopkins discuss why businesses today must re-examine their network resiliency strategies and implement new approaches.Don’t Let the Cybersecurity Trust Mark Become Like Food Labeling
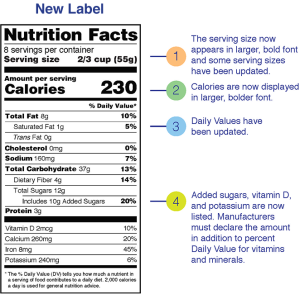
I got several press releases this week talking about the newest program from the US Federal government for cybersecurity labeling. This program is something designed to help consumers understand how secure IoT devices are and the challenges that can be faced trying to keep your network secure from the large number of smart devices that are being implemented today. Consumer Reports has been pushing for something like this for a while and lauded the move with some caution. I’m going to take it a little further. We need to be very careful about this so it doesn’t become as worthless as the nutrition labels mandated by the government.
Absolute Units
Having labels is certainly better than not having them. Knowing how much sugar a sports drink has is way more helpful than when I was growing up and we had to guess. Knowing where to find that info on a package means I’m not having to go find it somewhere on the Internet1. However, all is not sunshine and roses. That’s because of the way that companies choose to fudge their numbers.
Food companies spent a lot of time trying to work the numbers on those nutrition labels for Continue reading
Permitting: The Next Big Enterprise Broadband Challenge
It is ISPs vs. local government with providers waiting for broadband permit approvals that can add costs and delays for enterprise network expansion.Hedge 187: Buffer Bloat with Bjørn T

Buffer bloat causes permanent delay at multiple points along the path between a server and client—but it is hard to measure and resolve. Bjørn Teigen joins Tom and Russ on this episode of the Hedge to discuss the problem, solutions based in routers, and research into how to solve the problem at the host. You can find Bjørn’s recent paper in this area here, and he blogs here.
Migration Coordinator – In Place Migration Modes
In the first part of this blog series, we took a high level view of all the modes that are available with Migration Coordinator, a fully GSS supported tool built into NSX that enables migrating from NSX from vSphere to NSX (NSX-T).
The second blog in this series, will take a closer look at the available options for in-place migrations, along with the pros and cons of each approach.
NSX for vSphere: Fixed Topology
This mode was the very first mode introduced with migration coordinator in the NSX 2.4 release. This mode supports migrating configuration and workloads to NSX, using the same hosts that are running NSX for vSphere. It only needs extra capacity to run the NSX appliances such as the Managers and Edges.
Locating the mode: Marked in red below.

NSX Prep
- Installation: NSX manager and Edges
- Configuration: None
Pros:
- Workload Migration: Built in
- Bridging: Built in
Cons:
- Customization options: None
- Timing workload migration: No control
- Supported topologies: Only 5
Distributed Firewall, Host and Workload
This mode is useful when the requirement is to migrate only Distributed Firewall configuration.
Locating the mode
This mode is under the “Advanced Migration Modes” marked in red below.

NSX Prep:
Optimizing Network Performance using Topology Aware Routing with Calico eBPF and Standard Linux dataplane
In this blog post, we will explore the concept of Kubernetes topology aware routing and how it can enhance network performance for workloads running in Amazon. We will delve into topology aware routing and discuss its benefits in terms of reducing latency and optimizing network traffic flow. In addition, we’ll show you how to minimize the performance impact of overlay networking, using encapsulation only when necessary for communication across availability zones. By doing so, we can enhance network performance by optimizing the utilization of resources based on network topology.
Understanding Topology Aware Routing
Kubernetes clusters are being deployed more often in multi-zone environments. The nodes that make up the cluster are spread across availability zones. If one availability zone is having problems, the nodes in the other availability zones will keep working, and your cluster will continue to provide service for your customers. While this helps to ensure high availability, it also results in increased latency for inter-zone workload communication and can result in inter-zone data transfer costs.
Under normal circumstances, when traffic is directed to a Kubernetes Service, it evenly distributes requests among the pods that support it. Those pods can be spread across nodes in different zones. Topology Continue reading
Building Supercloud Starts with Multi-Cloud Networking
Supercloud, which enable hybrid IT across the entire IT stack, will become a reality, and the path to get there starts with multi-cloud networking.Protecting data on Apple devices with Cloudflare and Jamf


Today we’re excited to announce Cloudflare’s partnership with Jamf to extend Cloudflare’s Zero Trust Solutions to Jamf customers. This unique offering will enable Jamf customers to easily implement network Data Loss Prevention (DLP), Remote Browser Isolation (RBI), and SaaS Tenancy Controls from Cloudflare to prevent sensitive data loss from their Apple devices.
Jamf is a leader in protecting Apple devices and ensures secure, consumer-simple technology for 71,000+ businesses, schools and hospitals. Today Jamf manages ~30 million Apple devices with MDM, and our partnership extends powerful policy capabilities into the network.
“One of the most unforgettable lines I’ve heard from an enterprise customer is their belief that ‘Apple devices are like walking USB sticks that leave through the business’s front door every day.’ It doesn’t have to be that way! We are on a mission at Jamf to help our customers achieve the security and compliance controls they need to confidently support Apple devices at scale in their complex environments. While we are doing everything we can to reach this future, we can’t do it alone. I’m thrilled to be partnering with Cloudflare to deliver a set of enterprise-grade compliance controls in a novel way that leverages our Continue reading
Worth Reading: Eyes Like Saucers
Gerben Wierda published a nice description of common reactions to new unicorn-dust-based technologies:
- Eyes that glaze over
- Eyes like saucers
- Eyes that narrow
He uses generative AI as an example to explain why it might be a bad idea that people in the first two categories make strategic decisions, but of course nothing ever stops people desperately believing in vendor fairy tales, including long-distance vMotion, SDN or intent-based networking.
Worth Reading: Eyes Like Saucers
Gerben Wierda published a nice description of common reactions to new unicorn-dust-based technologies:
- Eyes that glaze over
- Eyes like saucers
- Eyes that narrow
He uses generative AI as an example to explain why it might be a bad idea that people in the first two categories make strategic decisions, but of course nothing ever stops people desperately believing in vendor fairy tales, including long-distance vMotion, SDN or intent-based networking.
Kubernetes Components: The Basics
Whether you run Kubernetes on-prem, in the cloud, or a combination of the two, one thing holds true – there is always a Control Plane element and a Worker Node element. Without them, Kubernetes wouldn’t exist. This post looks at the Control Plane and the Worker Node, including which components are in each, why each […]
The post Kubernetes Components: The Basics appeared first on Packet Pushers.