Optimizing Network Performance using Topology Aware Routing with Calico eBPF and Standard Linux dataplane
In this blog post, we will explore the concept of Kubernetes topology aware routing and how it can enhance network performance for workloads running in Amazon. We will delve into topology aware routing and discuss its benefits in terms of reducing latency and optimizing network traffic flow. In addition, we’ll show you how to minimize the performance impact of overlay networking, using encapsulation only when necessary for communication across availability zones. By doing so, we can enhance network performance by optimizing the utilization of resources based on network topology.
Understanding Topology Aware Routing
Kubernetes clusters are being deployed more often in multi-zone environments. The nodes that make up the cluster are spread across availability zones. If one availability zone is having problems, the nodes in the other availability zones will keep working, and your cluster will continue to provide service for your customers. While this helps to ensure high availability, it also results in increased latency for inter-zone workload communication and can result in inter-zone data transfer costs.
Under normal circumstances, when traffic is directed to a Kubernetes Service, it evenly distributes requests among the pods that support it. Those pods can be spread across nodes in different zones. Topology Continue reading
Building Supercloud Starts with Multi-Cloud Networking
Supercloud, which enable hybrid IT across the entire IT stack, will become a reality, and the path to get there starts with multi-cloud networking.Protecting data on Apple devices with Cloudflare and Jamf


Today we’re excited to announce Cloudflare’s partnership with Jamf to extend Cloudflare’s Zero Trust Solutions to Jamf customers. This unique offering will enable Jamf customers to easily implement network Data Loss Prevention (DLP), Remote Browser Isolation (RBI), and SaaS Tenancy Controls from Cloudflare to prevent sensitive data loss from their Apple devices.
Jamf is a leader in protecting Apple devices and ensures secure, consumer-simple technology for 71,000+ businesses, schools and hospitals. Today Jamf manages ~30 million Apple devices with MDM, and our partnership extends powerful policy capabilities into the network.
“One of the most unforgettable lines I’ve heard from an enterprise customer is their belief that ‘Apple devices are like walking USB sticks that leave through the business’s front door every day.’ It doesn’t have to be that way! We are on a mission at Jamf to help our customers achieve the security and compliance controls they need to confidently support Apple devices at scale in their complex environments. While we are doing everything we can to reach this future, we can’t do it alone. I’m thrilled to be partnering with Cloudflare to deliver a set of enterprise-grade compliance controls in a novel way that leverages our Continue reading
Worth Reading: Eyes Like Saucers
Gerben Wierda published a nice description of common reactions to new unicorn-dust-based technologies:
- Eyes that glaze over
- Eyes like saucers
- Eyes that narrow
He uses generative AI as an example to explain why it might be a bad idea that people in the first two categories make strategic decisions, but of course nothing ever stops people desperately believing in vendor fairy tales, including long-distance vMotion, SDN or intent-based networking.
Worth Reading: Eyes Like Saucers
Gerben Wierda published a nice description of common reactions to new unicorn-dust-based technologies:
- Eyes that glaze over
- Eyes like saucers
- Eyes that narrow
He uses generative AI as an example to explain why it might be a bad idea that people in the first two categories make strategic decisions, but of course nothing ever stops people desperately believing in vendor fairy tales, including long-distance vMotion, SDN or intent-based networking.
Kubernetes Components: The Basics
Whether you run Kubernetes on-prem, in the cloud, or a combination of the two, one thing holds true – there is always a Control Plane element and a Worker Node element. Without them, Kubernetes wouldn’t exist. This post looks at the Control Plane and the Worker Node, including which components are in each, why each […]
The post Kubernetes Components: The Basics appeared first on Packet Pushers.
Cloudflare Zaraz steps up: general availability and new pricing

This post is also available in Deutsch, Français.
Cloudflare Zaraz has transitioned out of beta and is now generally available to all customers. It is included under the free, paid, and enterprise plans of the Cloudflare Developer Platform. Visit our docs to learn more on our different plans.

Zaraz is part of the Cloudflare Developer Platform
Cloudflare Zaraz is a solution that developers and marketers use to load third-party tools like Google Analytics 4, Facebook CAPI, TikTok, and others. With Zaraz, Cloudflare customers can easily transition to server-side data collection with just a few clicks, without the need to set up and maintain their own cloud environment or make additional changes to their website for installation. Server-side data collection, as facilitated by Zaraz, simplifies analytics reporting from the server rather than loading numerous JavaScript files on the user's browser. It's a rapidly growing trend due to browser limitations on using third-party solutions and cookies. The result is significantly faster websites, plus enhanced security and privacy on the web.
We've had Zaraz in beta mode for a year and a half now. Throughout this time, we've dedicated our efforts to meeting as many customers as we could, gathering feedback, and Continue reading
Day Two Cloud 203: Becoming An SRE – It’s More Than Just Software Skills
If you want to be a Site Reliability Engineer (SRE) you need strong software skills. You also have to be versed in observability, incident response, capacity planning, change management, performance, even security. But wait, there's more! Our guest on today's Day Two Cloud argues you need strong communication skills, emotional intelligence, personal resilience, and the ability to work with a team. Our guest is Amin Astaneh.
The post Day Two Cloud 203: Becoming An SRE – It’s More Than Just Software Skills appeared first on Packet Pushers.
Day Two Cloud 203: Becoming An SRE – It’s More Than Just Software Skills
If you want to be a Site Reliability Engineer (SRE) you need strong software skills. You also have to be versed in observability, incident response, capacity planning, change management, performance, even security. But wait, there's more! Our guest on today's Day Two Cloud argues you need strong communication skills, emotional intelligence, personal resilience, and the ability to work with a team. Our guest is Amin Astaneh.Is Neutral Host the Killer App for Private Wireless?
A more modern approach to lowering the cost and complexity of extending cellular signals indoors is driving a new generation of private cellular wireless within the enterprise.The Arrival of Open AI Networking
Recently I attended the 50th golden anniversary of Ethernet at the Computer History Museum. It was a reminder of how familiar and widely deployed Ethernet is and how it has evolved by orders of magnitude. Since the 1970s, it has progressed from a shared collision network at 2.95 megabits in the file/print/share era to the promise of Terabit Ethernet switching in the AI/ML era. Legacy Ethernot* alternatives such as Token Ring, FDDI, and ATM generally get subsumed by Ethernet. I believe history is going to repeat itself for AI networks.
AWS Advanced Networking Speciality 1.3:Considerations for encryption and authentication with load balancers (for example, TLStermination, TLS passthrough)
< MEDIUM :https://towardsaws.com/aws-advanced-networking-speciality-1-3-considerations-402e0d057dfb >
List of blogs on AWS Advanced Networking Speciality Exam — https://medium.com/@raaki-88/list/aws-advanced-network-speciality-24009c3d8474
Data Protection in ELB
AWS Shared-Responsibility Model defines how data protection applies in ELBs. It boils down to AWS protecting global infrastructure while the service consumer is more responsible for preserving the content and control over the hosted content.
Few important suggestions for accessing/Securing
- MFA for accounts
- TLS 1.2 or TLS 1.3 for AWS resource communication
- Logging with AWS CloudTrail
- Amazon Macie — Discovering and securing sensitive data in S3
- FIP140–2 — Fips Endpoint
Encryption
Encryption at rest: Server-side encryption for S3 (SSE-S3) is used for ELB access logs. ELB automatically encrypts each log file before storing it in the S3 bucket and decrypts the access log files when you access them. Each log file is encrypted with a unique key, which is encrypted with a master key that is regularly rotated.
Encryption in Transit:
HTTPS/TLS traffic can be terminated at the ELB. ELB can encrypt and decrypt the traffic instead of additional EC2 instances or current EC2 backend instances doing this TLS termination. Using ACM (AWS Certificate Continue reading
AWS Advanced Networking Speciality 1.3: AWS Load Balancer Controller for Kubernetes clusters
List of blogs on AWS Advanced Networking Speciality Exam — https://medium.com/@raaki-88/list/aws-advanced-network-speciality-24009c3d8474
Before understanding LoadBalancer Service, it’s worth understanding a few things about NodePort service.
NodePort Service :
NodePort service opens a port on each node. External agents can connect directly to the node on the NodePort. If not mentioned, a randomly chosen service is picked up for NodePort. LoadBalancing here is managed by front-end service, which listens to a port and load balances across the Pods, which responds to service requests.
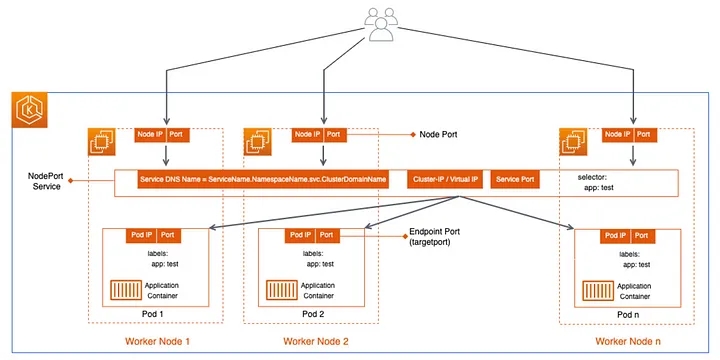
LoadBalancer Service:

Like NodePort Service, the LoadBalancer service extends the functionality by adding a load balancer in front of all the nodes. Kubernetes requests ELB and registers all the nodes. It’s worth noting that Load Balancer will not detect where the pods are running. Worker nodes are added as backend instances in the load balancer. The classic-load balancer is the default LB the service chooses and can be changed to NLB(Network Load Balancer). CLB routes the requests to Front-end, then to internal service ports Continue reading


