How the Cloudflare global network optimizes for system reboots during low-traffic periods

To facilitate the huge scale of Cloudflare’s customer base, we maintain data centers which span more than 300 cities in over 100 countries, including approximately 30 locations in Mainland China.
The Cloudflare global network is built to be continuously updated in a zero downtime manner, but some changes may need a server reboot to safely take effect. To enable this, we have mechanisms for the whole fleet to automatically reboot with changes gated on a unique identifier for the reboot cycle. Each data center has a maintenance window, which is a time period - usually a couple of hours - during which reboots are permitted.
We take our customer experience very seriously, and hence we have several mechanisms to ensure that disruption to customer traffic does not occur. One example is Unimog, our in-house load balancer that spreads load across the servers in a data center, ensuring that there is no disruption when a server is taken out for routine maintenance.
The SRE team decided to further reduce risk by only allowing reboots in a data center when the customer traffic is at the lowest. We also needed to automate the existing manual process for determining the window Continue reading
The Internet of Moving Things: How to Deploy IoT on the Move
The Internet of moving things presents a different set of network building and orchestration conditions and challenges compared to stationary IoT.Heavy Wireless 006: Building Sustainable, Efficient Backhaul Networks With Ceragon Networks (Sponsored)
Today's Heavy Wireless episode explores building sustainable and efficient backhaul networks with sponsor Ceragon Networks. We discuss the challenges of backhaul, the complementarity of wireless and fiber solutions, the frequencies and protocols used in wireless backhaul, and the concept of disaggregated routing.
The post Heavy Wireless 006: Building Sustainable, Efficient Backhaul Networks With Ceragon Networks (Sponsored) appeared first on Packet Pushers.
Heavy Wireless 006: Building Sustainable, Efficient Backhaul Networks With Ceragon Networks (Sponsored)
Today's Heavy Wireless episode explores building sustainable and efficient backhaul networks with sponsor Ceragon Networks. We discuss the challenges of backhaul, the complementarity of wireless and fiber solutions, the frequencies and protocols used in wireless backhaul, and the concept of disaggregated routing.Build and secure multi-cluster CockroachDB using the Calico clustermesh: A step-by-step guide
This blog is written by Dhiraj Sehgal and Mike Bookham.
Dhiraj Sehgal is the Director of Technical Marketing at Tigera, where he helps customers learn more about Calico and provides best practices for securing cloud-native environments. He is passionate about everything cloud native, from Kubernetes to cloud security and observability.
Mike Bookham is a Channel Solutions Engineer at Cockroach Labs. As part of Mike’s role, he helps a range of different types of partner organizations get familiar with CockroachDB from a technical perspective. Mike has worked with cloud-native technologies for a number of years and specializes in Kubernetes and the surrounding ecosystem.
With the rapid adoption of Kubernetes in organizations and the push to standardize the orchestration of resources with this approach, databases are now also being deployed into Kubernetes. Historically, persistent workloads like databases were not recommended for their deployment into Kuberntes as it was complex to manage how data would be stored. This was a result of Kubertnes originally being designed for non persistent microservice architectures. However, in more recent times new database vendors are emerging with software built from the ground up to run in this environment.
Kubernetes mandates how the networking is deployed and configured in Continue reading
Bring your own CA for client certificate validation with API Shield


APIs account for more than half of the total traffic of the Internet. They are the building blocks of many modern web applications. As API usage grows, so does the number of API attacks. And so now, more than ever, it’s important to keep these API endpoints secure. Cloudflare’s API Shield solution offers a comprehensive suite of products to safeguard your API endpoints and now we’re excited to give our customers one more tool to keep their endpoints safe. We’re excited to announce that customers can now bring their own Certificate Authority (CA) to use for mutual TLS client authentication. This gives customers more security, while allowing them to maintain control around their Mutual TLS configuration.
The power of Mutual TLS (mTLS)
Traditionally, when we refer to TLS certificates, we talk about the publicly trusted certificates that are presented by servers to prove their identity to the connecting client. With Mutual TLS, both the client and the server present a certificate to establish a two-way channel of trust. Doing this allows the server to check who the connecting client is and whether or not they’re allowed to make a request. The certificate presented by the client - the client certificate Continue reading
The day my ping took countermeasures



Once my holidays had passed, I found myself reluctantly reemerging into the world of the living. I powered on a corporate laptop, scared to check on my email inbox. However, before turning on the browser, obviously, I had to run a ping. Debugging the network is a mandatory first step after a boot, right? As expected, the network was perfectly healthy but what caught me off guard was this message:
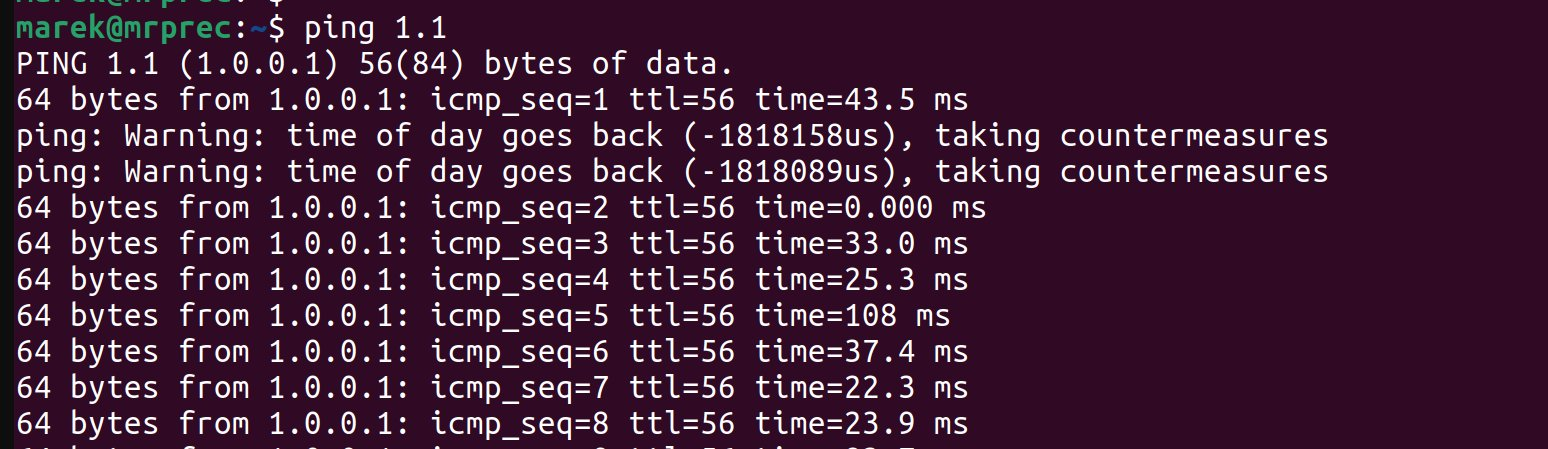
I was not expecting ping to take countermeasures that early on in a day. Gosh, I wasn't expecting any countermeasures that Monday!
Once I got over the initial confusion, I took a deep breath and collected my thoughts. You don't have to be Sherlock Holmes to figure out what has happened. I'm really fast - I started ping before the system NTP daemon synchronized the time. In my case, the computer clock was rolled backward, confusing ping.
While this doesn't happen too often, a computer clock can be freely adjusted either forward or backward. However, it's pretty rare for a regular network utility, like ping, to try to manage a situation like this. It's even less common to call it "taking countermeasures". I would totally expect ping to just print Continue reading
Catalyst SD-WAN – Introduction to Configuration Groups
One of the challenges with Catalyst SD-WAN is managing templates. Depending on how successful you are in standardizing your deployment, you risk ending up with many device templates. This can also be amplified if you have several platforms as each platform requires its own set of device templates. Feature templates, while reusable, offers no concept of grouping feature templates which means that there is a lot of work involved in building a new device template. To overcome some of these challenges, Cisco has introduced Configuration Groups starting with 20.8 and going forward where 20.11 currently has the most features implemented. This is also often referred to as UX 2.0 in some presentations. Let’s take a look at Configuration Groups by looking at the building blocks.
- Configuration Group – Logical grouping of features or configuration that is applied to devices. Similar to a device template but it can be applied to different models.
- Feature Profile – Building block of configurations that can be reused across different Configuration Groups. Example feature profiles are Transport Profile, System Profile, Service Profile.
- Feature – The Feature Profile consists of features. The individual capability to be shared across Configuration Groups such as service Continue reading
Configuring Linux Traffic Control in a Sane Way
Smart engineers were forever using Linux (in particular, its traffic control/queue discipline functionality) to simulate WAN link impairment. Unfortunately, there’s a tiny hurdle you have to jump across: the tc CLI is even worse than iptables.
A long while ago someone published a tc wrapper that simulates shitty network connections and (for whatever reason) decided to call it Comcast. It probably does the job, but I would prefer to have something in Python. Daniel Dib found just that – tcconfig – and used it to simulate WAN link behavior on VMware vSphere.
Configuring Linux Traffic Control in a Sane Way
Smart engineers were forever using Linux (in particular, its traffic control/queue discipline functionality) to simulate WAN link impairment. Unfortunately, there’s a tiny hurdle you have to jump across: the tc CLI is even worse than iptables.
A long while ago someone published a tc wrapper that simulates shitty network connections and (for whatever reason) decided to call it Comcast. It probably does the job, but I would prefer to have something in Python. Daniel Dib found just that – tcconfig – and used it to simulate WAN link behavior on VMware vSphere.
HS051 Things I Wish I’d Known Back When
Oft-asked question that doesn't have a right answer. We discuss non-convential answers that career coaches or self-help twaddle won't give you.
The post HS051 Things I Wish I’d Known Back When appeared first on Packet Pushers.