AWS Advanced Networking — Task Statement 1.3: How load balancing works at Layer 3, layer 4, and Layer 7 of the OSI model
< MEDIUM: https://towardsaws.com/aws-advanced-networking-task-statement-1-3-c457fa0ed893 >
Ref: https://aws.amazon.com/elasticloadbalancing/
Why Elastic Load Balancer?
- To Distribute incoming application traffic across EC2 instances / Containers / IP Addresses and these entities, generally, can be called targets and grouped as Target-Groups.
- Another advantage is performing health checks, such as packet-loss or high-latency, and can be integrated with Auto-scaling, hence Elastic.
- Depending on the ELB type and its operational requirement, this can further be subdivided into CLB, ALB, GLB, and NLB.
CLB — Classic Load Balancer
– AWS Recommends ALB today instead of CLB
– Intended for EC2 instances which are built in EC2-Classic Network
– Layer 4 or Layer 7 Load Balancing
– Provides SSL Offloading and IPv6 support for Classic Networks
ALB — Application Load Balancer
- Works at the 7th Layer of the OSI Model.
- Supports applications that run in Containers
- Supports Content-based Routing
- HTTP/HTTPS, Mobile Apps, Containers in EC2, and Microservices benefit greatly from ALB
Why Elastic Load Balancer?
- To Distribute incoming application traffic across EC2 instances / Containers / IP Addresses and these entities, generally, can be called targets and grouped as Target-Groups.
- Another advantage is performing health checks, such as packet-loss or high-latency, and can be integrated with Auto-scaling, Continue reading
Set up your Own wireguard-based Cloud VPN server without installing software on your laptop — GL-A1300 Slate Plus Wireless Router
Note: This requires the purchase of a wireless router which is capable of running a Wireguard package in this case it’s Slate-Plus GL-A1300 and I do not have any affiliate or ads program with them, I simply liked it for its effectiveness and low cost.

The Need :
For one reason many of us want a VPN server which does decent encryption but won’t charge us a lot of money, in some cases, it can be done free of cost and in others for not want us to install a variety of software which messes up with internal client routing and also against some of the IT-Policies, even if it’s a browser-based plugin.
The Choice :
Wireguard: https://www.wireguard.com/ — VPN Software, Software-based encryption, extremely fast and light-weight.
GL-A1300 Slate-Plus — Wireless Router with support for Wireguard which is not a feature in many of the current market routers, had OpenWrt as the installed software.
Features
The GL-A1300 Slate Plus wireless VPN encrypted travel router comes packed with features that will make your life easier while travelling. Here are just a few of the most important:
- VPN Encryption — The GL-A1300 Slate Plus Continue reading
AWS Rekognition — A simple classifier without having to build a lot of in-house or Cloud Environments — Sample Bird-Project
A few weeks ago, I set up a bird feeder and used it to capture bird images, the classifier itself was not that accurate but was doing a decent job, what I have realised is that not every time we end up with highly accurate on-board edge classification especially while learning how to implement them.
So after a few weeks, there were a lot of images some of them sure enough had birds while some of them were taken in Pitch Dark and am not even sure what made the classifier figure out a birdie in the snapshot from the camera.
Now for me in order to make an Image, I have to rely on a re-classifier doing the job for me, initially, I thought I will write a lambda-based classifier as a learning experiment, but then I thought it was a one-time process every 6 months or so, so I went ahead with a managed service option and in this case, its AWS Rekognition, which is quite amazing.
https://aws.amazon.com/rekognition/
Code Snippet used for Classification
import os
import concurrent.futures
import boto3
def detect_birds(image_path):
# Configure AWS credentials and region
session Continue reading
Heavy Networking 690: LACP Is Not Link Aggregation – With Tony Bourke
On today’s Heavy Networking we talk LACP and link aggregation. While bonding two or more links together to act as a single virtual link has been done for decades, LACP and link aggregation aren't the same thing, and the distinction matters. Our guest to get into the differences is network instructor Tony Bourke.
The post Heavy Networking 690: LACP Is Not Link Aggregation – With Tony Bourke appeared first on Packet Pushers.
Heavy Networking 690: LACP Is Not Link Aggregation – With Tony Bourke
On today’s Heavy Networking we talk LACP and link aggregation. While bonding two or more links together to act as a single virtual link has been done for decades, LACP and link aggregation aren't the same thing, and the distinction matters. Our guest to get into the differences is network instructor Tony Bourke.Quickly see differences between Zone Versions with Version Comparisons


On the week of July 10, 2023, we launched a new capability for Zone Versioning - Version Comparisons. With Version Comparisons, you can quickly get a side by side glance of what changes were made between two versions. This makes it easier to evaluate that a new version of your zone’s configuration is correct before deploying to production.
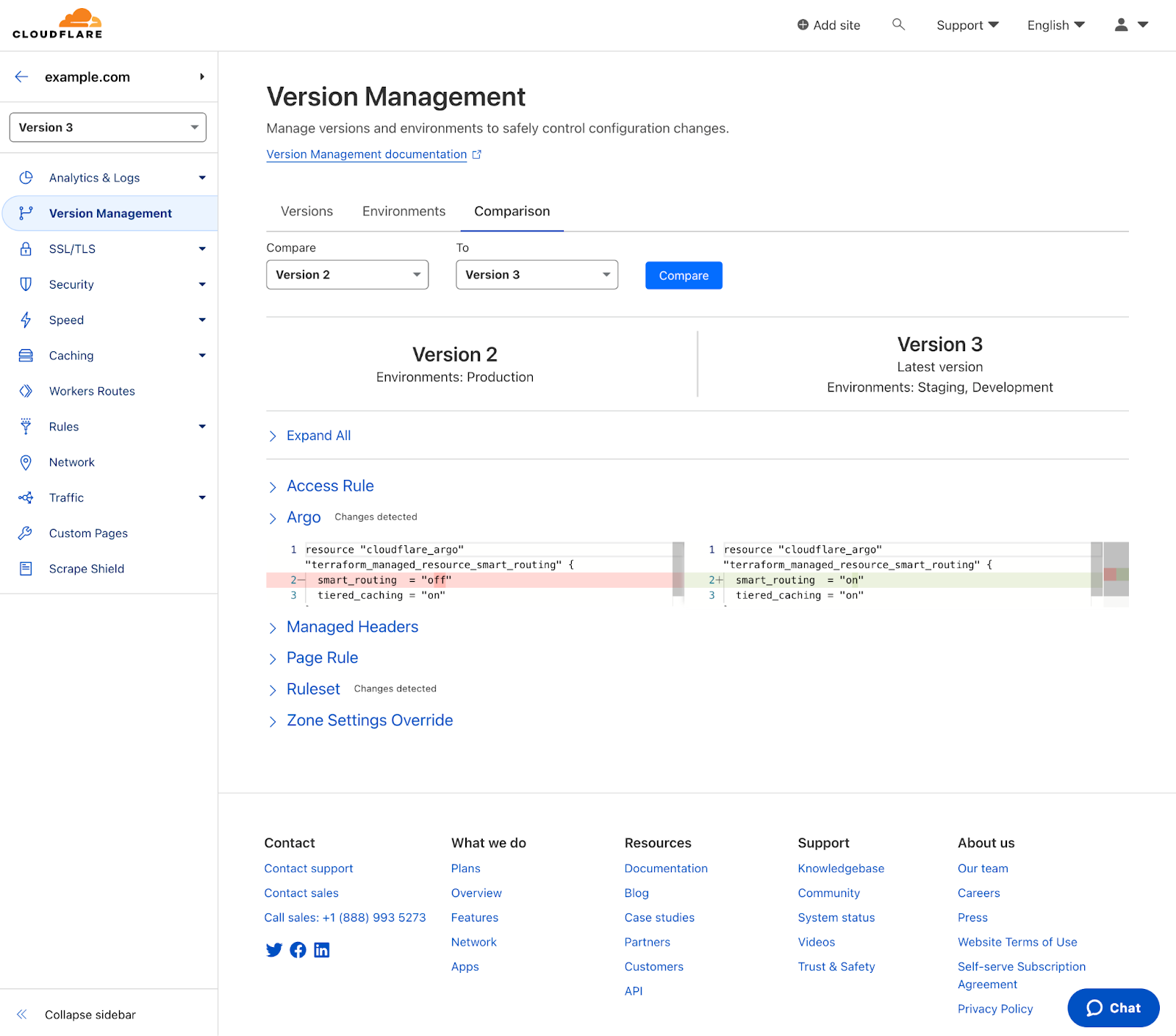
A quick recap about Zone Versioning
Zone Versioning was launched at the start of 2023 to all Cloudflare Enterprise customers and allows you to create and manage independent versions of your zone configuration. This enables you to safely configure a set of configuration changes and progressively roll out those changes together to predefined environments of traffic. Having the ability to carefully test changes in a test or staging environment before deploying them to production, can help catch configuration issues before they can have a large impact on your zone’s traffic. See the general availability announcement blog for a deeper dive on the overall capability.
Why we built Version Comparisons
Diff is a well known and often used tool by many software developers to quickly understand the difference between two files. While originally just a command line utility it is now ubiquitous across Continue reading
Hedge 186: Hardware Root of Trust
The idea of a root of trust is somewhat foreign to network engineers—what is it, and why would it be important? Michael and Marcus from Hedgehog join Tom Ammon and Russ White to discuss how hardware roots of trust work, what problems they are designed to solve for network hardware, and the current state of this technology.
rough transcript will be supplied in a few days
Deploy real-time network dashboards using Docker compose
This article demonstrates how to use docker compose to quickly deploy a real-time network analytics stack that includes the sFlow-RT analytics engine, Prometheus time series database, and Grafana to create dashboards.
git clone https://github.com/sflow-rt/prometheus-grafana.git cd prometheus-grafana ./start.shDownload the sflow-rt/prometheus-grafana project from GitHub on a system with Docker installed and start the containers. The start.sh script runs docker compose to bring up the containers specified in the compose.yml file, passing in user information so that the containers have correct permission to write data files in the prometheus and grafana directories.
All the Docker images in this example are available for both x86 and ARM processors, so this stack can be deployed on Intel/AMD platforms as well as Apple M1/M2 or Raspberry Pi. Raspberry Pi 4 real-time network analytics describes how to configure a Raspberry Pi 4 to run Docker and perform real-time network analytics and is a simple way to run this stack for smaller networks.
Configure sFlow Agents in network devices to stream sFlow telemetry to the host running the analytics stack. See Getting Started for information on how to verify that sFlow telemetry is being received.
Connect to the Grafana web interface on Continue readingOut-of-band Management – Useful Beyond Catastrophe
I was lucky enough to participate in Tech Field Day Extra at Cisco Live a couple weeks months ago. This event brings independent thought leaders together with a number of IT product vendors that were at Cisco Live to share information and opinions. I was not paid to attend, but the organizers did provide some meals while I was there. There is no expectation of providing any content, so the fact that I’m mentioning it says something. It was a great event and worth a few hours to check out the videos. Thanks to Gestalt IT for getting me involved. OpenGear was there, and it was good to see some new faces and hear some new ideas.
For those that live under a rock don’t know, OpenGear traditionally provides out-of-band (OOB) management solutions via hardware appliances that run independently of your network. They, like other vendors in that space, can connect to the cellular data network of choice and provide access to your gear when something fails (what OpenGear calls “worst day”). Over 99.9% of the time, though, you would never use your OOB devices. They’re just going to sit there doing nothing until that day that something fails Continue reading
Out-of-band Management – Useful Beyond Catastrophe
I was lucky enough to participate in Tech Field Day Extra at Cisco Live a couple weeks months ago. This event brings independent thought leaders together with a number of IT product vendors that were at Cisco Live to share information and opinions. I was not paid to attend, but the organizers did provide some meals while I was there. There is no expectation of providing any content, so the fact that I’m mentioning it says something. It was a great event and worth a few hours to check out the videos. Thanks to Gestalt IT for getting me involved. OpenGear was there, and it was good to see some new faces and hear some new ideas.
For those that live under a rock don’t know, OpenGear traditionally provides out-of-band (OOB) management solutions via hardware appliances that run independently of your network. They, like other vendors in that space, can connect to the cellular data network of choice and provide access to your gear when something fails (what OpenGear calls “worst day”). Over 99.9% of the time, though, you would never use your OOB devices. They’re just going to sit there doing nothing until that day that something fails Continue reading
Kubernetes Unpacked 030: What’s Up With WASM? – With Nigel Poulton
In this episode of Kubernetes Unpacked, Michael and Kristina catch up with with Nigel Poulton, an independent consultant, trainer, and content creator to discuss what Web Assembly (WASM) is, why it’s gaining popularity, and whether it can be the future of programming and development.
The post Kubernetes Unpacked 030: What’s Up With WASM? – With Nigel Poulton appeared first on Packet Pushers.

