Updated Public Domain Network Icons
I’ve updated the generic icon set I use in all my presentations to include a Wi-Fi router, an antenna, and a few other things. You can always find them on this page, as well.
![]()
What’s new in Calico v3.26
We are excited to announce the release of Calico v3.26! This latest milestone brings a range of enhancements and new features to the Calico ecosystem, delivering an optimized and secure networking solution. This release has a strong emphasis on product performance, with strengthened security measures, expanded compatibility with Windows Server 2022 and OpenStack Yoga, and notable improvements to the Calico eBPF dataplane.
As always, let’s begin by thanking our awesome community members who helped us in this release.
Community shoutout
Big thanks to our GitHub users afshin-deriv, blue-troy, and winstonu for their valuable contributions in enhancing the Kind installation and VXLAN documentation, as well as improving the code comments.
Additionally, we would like to extend our appreciation to laibe and yankay for their efforts in updating the flannel version and improving the IPtables detection mechanism. Their contributions have been instrumental in improving the overall functionality and reliability of our project.
Finally, a huge thank-you to dilyevsky, detailyang, mayurjadhavibm, and olljanat for going above and beyond in pushing Calico beyond its original scope and for generously sharing their solutions with the rest of the community.
Community-driven enhancement request: Fine-grained BGP route control
The primary responsibility Continue reading
Tech Bytes: Building The Branch Of The Future With Palo Alto Networks SD-WAN And SASE (Sponsored)
Today on the Tech Bytes podcast we explore the branch of the future with sponsor Palo Alto Networks. We talk about how SD-WAN and SASE come together with Digital Experience Management (DEM) to meet the challenges of security, cloud, and hybrid work at the branch.
The post Tech Bytes: Building The Branch Of The Future With Palo Alto Networks SD-WAN And SASE (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Building The Branch Of The Future With Palo Alto Networks SD-WAN And SASE (Sponsored)
Today on the Tech Bytes podcast we explore the branch of the future with sponsor Palo Alto Networks. We talk about how SD-WAN and SASE come together with Digital Experience Management (DEM) to meet the challenges of security, cloud, and hybrid work at the branch.The Essential Skills Every Network Administrator Needs
While network technologies are rapidly advancing, the fundamental talents administrators need to succeed remain relatively unchanged. Learn how mastering just a few basic skills can advance your job and career.Nine years of Project Galileo and how the last year has changed it


If you follow Cloudflare, you know that Birthday Week is a big deal. We’ve taken a similar approach to Project Galileo since its founding in 2014. For the anniversary, we typically give an overview of what we have learned to protect the most vulnerable in the last year and announce new product features, partnerships, and how we’ve been able to expand the project.
When our Cloudflare Impact team was preparing for the anniversary, we noticed a theme. Many of the projects we worked on throughout the year involved Project Galileo. From access to new products, development of privacy-enhancing technologies, collaborations with civil society and governments, we saw that the project played a role in either facilitating conversation with the right people or bridging gaps.
After reflecting on the last year, we’ve seen a project that was initially intended to keep journalism and media sites online grew into more. So, for this year, in addition to new announcements, we want to take the time to reflect on how we have seen Project Galileo transform and how we look toward the future in protecting the most vulnerable on the Internet.
Project Galileo +
The original goal of Project Galileo was simple. Although Continue reading
Default EBGP Policy (RFC 8212)
One of the most common causes of Internet routing leaks is an undereducated end-customer configuring EBGP sessions with two (or more) upstream ISPs.
Without basic-level BGP knowledge or further guidance from the service providers, the customer network engineer1 might start a BGP routing process and configure two EBGP sessions, similar to the following industry-standard CLI2 configuration:
Default EBGP Policy (RFC 8212)
One of the most common causes of Internet routing leaks is an undereducated end-customer configuring EBGP sessions with two (or more) upstream ISPs.
Without basic-level BGP knowledge or further guidance from the service providers, the customer network engineer1 might start a BGP routing process and configure two EBGP sessions, similar to the following industry-standard CLI2 configuration:
Worth Reading: Internet WAN Edge Design
Brandon Hitzel published a detailed document describing various Internet WAN edge designs. Definitely worth reading and bookmarking.
Worth Reading: Internet WAN Edge Design
Brandon Hitzel published a detailed document describing various Internet WAN edge designs. Definitely worth reading and bookmarking.
RIPE 86 Bites – Encryption and Active Network Management
RIPE held a community meeting in May in Rotterdam. There were a number of presentations that sparked my interest, but rather than write my impressions in a single lengthy note, I thought I would just take a couple of topics and use a shorter, and hopefully more readable bite-sized format. Here’s the third of these bite-sized notes from the RIPE 86 meeting, on the topic of the implications of an encrypted content on active network management.Worth Reading: Unbounded TCP Memory Usage
Another phenomenal detective story published on Cloudflare blog: Unbounded memory usage by TCP for receive buffers, and how we fixed it.
TL&DR: Moving TCP window every time you acknowledge a segment doesn’t work well with scaled window sizes.
The interesting takeaways:
Worth Reading: Unbounded TCP Memory Usage
Another phenomenal detective story published on Cloudflare blog: Unbounded memory usage by TCP for receive buffers, and how we fixed it.
TL&DR: Moving TCP window every time you acknowledge a segment doesn’t work well with scaled window sizes.
The interesting takeaways:
Back to Basics: A Primer on Communication Fundamentals
Motivation
In our rapidly advancing world, communication speeds are increasing at a fast pace. Transceiver speeds have evolved from 100G to 400G, 800G, and soon even 1.6T. Similarly, Optical systems are evolving to keep up with the pace. If we dig deeper, we will discover that many concepts are shared across various domains, such as Wi-Fi, optical communications, transceivers, etc. Still, without the necessary background, It’s not easy to identify the patterns. If we have the essential knowledge, it becomes easier to understand the developments happening in the respective areas, and we can better understand the trade-offs made by the designers while designing a particular system. And that’s the motivation behind writing this post is to cover fundamental concepts which form the basis for our modern communication system and how they all relate to each other.
Waves
So let’s start with the most fundamental thing, i.e., wave. A wave is a disturbance that carries energy from one location to another without displacing matter. Waves transfer energy from their source and do not cause any permanent displacement of matter in the medium they pass through. The following animation demonstrates this concept.
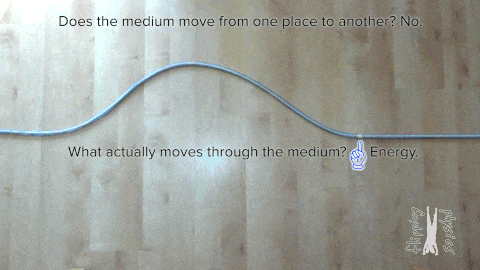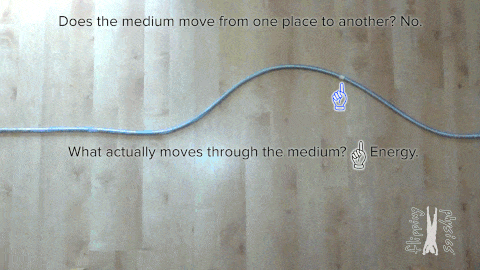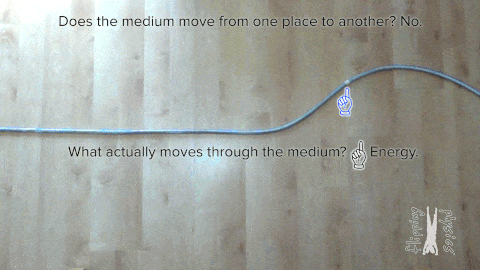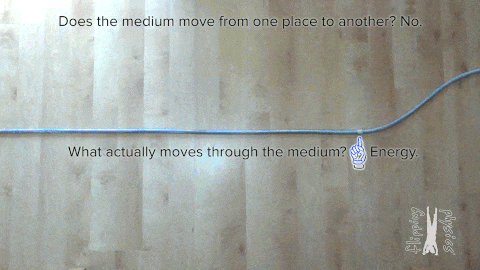
Ocean and sound waves are mechanical waves Continue reading
Back to Basics: A Primer on Communication Fundamentals
Motivation In our rapidly advancing world, communication speeds are increasing at a fast pace. Transceiver speeds have evolved from 100G to 400G, 800G, and soon even 1.6T. Similarly, Optical systems are evolving to keep up with the pace. If we dig deeper, we will discover that many concepts are shared across various domains, such as Wi-Fi, optical communications, transceivers, etc. Still, without the necessary background, It’s not easy to identify the patterns. If we have the essential knowledge, it becomes easier to understand the developments happening in the respective areas, and we can better understand the trade-offs made by the designers while designing a particular system. And that’s the motivation behind writing this post is to cover fundamental concepts which...Heavy Networking 682: Automating Upgrades And Ensuring Compliance With BackBox (Sponsored)
If you’ve shied away from network automation because you’re a network engineer not a coder, fear not. There are network automation approaches that can help you get needful work done and don’t require a computer science degree. On today's Heavy Networking we talk with sponsor BackBox about its practical approach to network automation and dive into use cases including network OS backups and compliance.
The post Heavy Networking 682: Automating Upgrades And Ensuring Compliance With BackBox (Sponsored) appeared first on Packet Pushers.