CCIE DCv2 Techtorial @ Cisco Live US 2016
This morning I’m in Las Vegas for Cisco Live 2016, and am attending TECCCIE-3644 – CCIE DC Techtorial which focuses on the new CCIE Data Center v2 updates.
I’m live blogging the session so please feel free to submit your questions for the CCIE team as a comment here and I’ll try to get an answer for you.
Slides from the session are available here.
Update 6 – 13:55PDT - UCS will be running 3.x, not 2.x as currently listed on the blueprint.
Update 5 – 11:30PDT - Starting Storage Networking now. Interested to see what the scope is going to be now with the MDSes removed and the N9K’s added.
Update 4 – 09:15PDT - One major format change for the CCIE DCv2 Lab Exam is the introduction of the Diagnostics section, similar to other tracks such as RSv5. Here are some highlights and demo questions illustrating the format of the Diag section.
- Diag section consists of one or more independent Tasks.
- Each Task can have one or more Questions.
- Questions are typically 1 point apiece, but could be 2 or 3 points.
- Each Question within a task is graded individually. It is possible to get Task Continue reading
Pseudowire Headend Termination (PWHT) For Juniper MX
I’ve been doing quite a lot of MX BNG stuff this year, so I thought I’d run through another quite flexible way of terminating broadband subscribers onto a Juniper MX router.
The feature is called Psuedowire headend termination, “PWHT” or simply Psuedowire head-end “PWHE” depending on whether you work for Cisco or Juniper? but it essentially solves a relatively simple problem.
In traditional broadband designs – especially in DSL “FTTC” or Fibre Ethernet “FTTP” we’re used to seeing large numbers of subscribers, connecting into the ISP edge at layer-2 with PPPoE or plain Ethernet. This is normally performed with VLANS, either via an MSAN (DSL/FTTC) or as is the case with Ethernet FTTP subscribers – a plain switched infrastructure or some form of passive-optical (PON/GPON) presentation:
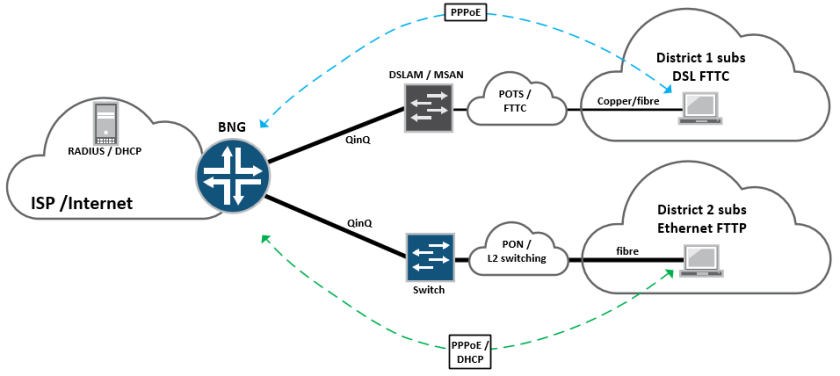
These subscribers then terminate on a BNG node on the edge of the network, which would historically have been a Cisco 7200, GSR10k, Juniper ERX or Redback router, which essentially bridges the gap between the access network and the internet.
For very large service providers with millions of subscribers this sort of approach normally works well, because their customer base is so large; it makes sense for them to provision a full-size BNG node Continue reading
Saving Money with IOT Water Heater
About six months ago I installed an Energy Efficient water heater. This unit is what is known as a heat pump water heater. For those not familiar with refrigeration, this works by moving heat instead of creating heat. By contrast, traditional electric water heaters use resistance coils to heat the water. This new unit also has traditional coils that can be used for high demand or high temperature settings as well.
I guess by now everyone is wondering what this has to do with the topics we discussed at PacketU. To better understand the relationship, you can see that this Water Heater is also Connected to the Internet. The primary reasons I wanted to connect it to the Internet was to schedule the modes around my family’s usage patterns and control vacation mode from a mobile phone. When purchasing this unit I was quite skeptical and was concerned about transitioning from a simple conventional model to a mode that literally has moving parts.
I wanted to follow up and share my experience and why I now believe this was a good decision. I have been tracking my energy usage since installation and the results are promising. Without changing any other habits Continue reading
Docker Security presentation at Bangalore meetup
This link captures the slides on “Docker Security Overview as of release 1.12” that I presented at Docker Meetup, Bangalore on July 9, 2016.Firepower Indications of Compromise
Several days ago I wrote an article about Firepower Sinkhole rules. While I was confirming this in a lab, I temporarily created a custom DNS sinkhole rule. That rule classified requests for temp.packetu.com as Command and Control and returned an IP address of 1.1.1.1. What I later noticed is that this caused my laptop to be classified with an IOC.
Indications of Compromise (IOCs) can be thought of as reasons why Firepower Management Console believes a host cannot be trusted or is otherwise affected by malware. These can be found in multiple places in the UI. I find the Context Explorer to be a good middle ground for most SecOps team members and a good place to notice whether current IOC’s exist.
My network is rather simple and I only currently have one IOC. In any case, I can use the Context Explorer to launch the host information for the impacted host.

Once the Host Profile screen is launched, I can get a little more about information about the activity that causes Firepower to believe that this is a compromised host.

Also notice that there is a garbage can icon to the right of the Indication of Compromise that was Continue reading
General – Network Engineering vs Coding
Introduction
There has been a lot of talking about the future of the network engineer for the last couple of years. Many articles have declared that we MUST learn to program or we will be banished from the world by the programming overlords! I definitely do not agree with this bold statement but lately I have started to learn Python. Why?
Why Learn Programming?
As a network architect I probably won’t ever write a line of code or at least very rarely so. So why bother learning?
I didn’t learn a lot of programming back in my days of school. I fiddled around a bit with Basic, some Pascal and then at the university I tried some C# and C++. I never felt connected with programming. I never felt that I was good at it. This surprised me a bit because I’ve always been good at learning things. I’m good at analyzing things, troubleshooting things and I have a strong background in maths and science in general. I had all the skills that good programmers normally have so why couldn’t I learn programming? Because I struggled I didn’t enjoy doing it so I never pushed through until it “clicked”.
Later Continue reading
Network Analytics that tracks every packet, every application flow
As the business world re-tools itself to become dramatically more digital-centric, and their adoption of leading edge technology such as...Is David Goeckeler Overseeing 50% of Cisco Revenues?
 Other thoughts in advance of Cisco Live.
Other thoughts in advance of Cisco Live.
Cisco’s Tom Edsall: On Policy, Webscale Giants & Containers (Part 2)
 Edsall discusses what 'application-centric' really means and how webscale players change the industry.
Edsall discusses what 'application-centric' really means and how webscale players change the industry.
Cisco’s Tom Edsall: On Policy, Webscale Giants & Containers
 Edsall discusses what 'application-centric' really means and how webscale players change the industry.
Edsall discusses what 'application-centric' really means and how webscale players change the industry.