European Telcos Seek 5G Network Fees from Top Internet Users
The operators’ proposal is before the European Commission. Meta objects and warns the EC of damage to business and consumers. What’s the impact on U.S. enterprises?Hedge 179: The State and Future of SONiC with Michael V Dvorkin
SONiC is a long-standing open source network operating system. While it cannot (quite) compete with a full-blown commercial network operating system, SONiC+FR/R can solve a lot of the problems network operators face today. Mike V Dvorkin joins Tom Ammon and Russ White to talk about the current state and future of SONiC.
Case study: Calico Enterprise empowers Aldagi to achieve EU GDPR compliance
Founded in 1990, Aldagi is Georgia’s first and biggest private insurance firm. With a 32% market share in Georgia’s insurance sector, Aldagi provides a broad range of services to corporate and retail clients.
With the onset of the pandemic in 2019, Aldagi wanted to make its services available to customers online. To this end, the company adopted an Agile methodology for software development and re-architected its traditional VM-based applications into cloud-native applications. Aldagi then began using containers and Kubernetes as a part of this process. Using self-managed clusters on Rancher Kubernetes Engine (RKE), Aldagi created distributed, multi-tenant applications to serve its broad EU customer base.
In collaboration with Tigera, Aldagi details its journey using Calico to achieve EU GDPR compliance, in order to share its experience with the rest of the Kubernetes community.

Case study highlights
Because Aldagi’s applications are distributed and multi-tenanted, the company faced three major challenges when it came to achieving EU GDPR compliance:
- Granular access control
- Visibility and security controls for workloads with sensitive data
- Continuous compliance reporting and auditing
By deploying Calico, Aldagi solved these challenges and achieved EU GDPR compliance, Continue reading
IPv6 Buzz 126: What Employers Are Looking For With IPv6 Job Postings
In this episode of IPv6 Buzz, Ed, Scott, and Tom talk about what employers are looking for when IPv6 shows up in a job posting or as an interview question.
The post IPv6 Buzz 126: What Employers Are Looking For With IPv6 Job Postings appeared first on Packet Pushers.
IPv6 Buzz 126: What Employers Are Looking For With IPv6 Job Postings
In this episode of IPv6 Buzz, Ed, Scott, and Tom talk about what employers are looking for when IPv6 shows up in a job posting or as an interview question.Zscaler Gives Digital Experience Monitoring a Shot of AI
ZDX measures user experience metrics providing IT teams with the data they need to identify and troubleshoot performance issues.Announcing Cloudflare Secrets Store


We’re excited to announce Secrets Store - Cloudflare’s new secrets management offering!
A secrets store does exactly what the name implies - it stores secrets. Secrets are variables that are used by developers that contain sensitive information - information that only authorized users and systems should have access to.
If you’re building an application, there are various types of secrets that you need to manage. Every system should be designed to have identity & authentication data that verifies some form of identity in order to grant access to a system or application. One example of this is API tokens for making read and write requests to a database. Failure to store these tokens securely could lead to unauthorized access of information - intentional or accidental.
The stakes with secret’s management are high. Every gap in the storage of these values has potential to lead to a data leak or compromise. A security administrator’s worst nightmare.
Developers are primarily focused on creating applications, they want to build quickly, they want their system to be performant, and they want it to scale. For them, secrets management is about ease of use, performance, and reliability. On the other hand, security administrators are tasked Continue reading
Using LangChainJS and Cloudflare Workers together
We are incredibly stoked that our friends at LangChain have announced LangChainJS Support for Multiple JavaScript Environments (including Cloudflare Workers). During Developer Week 2023 we wanted to celebrate this launch and our future collaborations with LangChain.
“Our goal for LangChain is to empower developers around the world to build with AI. We want LangChain to work wherever developers are building, and to spark their creativity to build new and innovative applications. With this new launch, we can't wait to see what developers build with LangChainJS and Cloudflare Workers. And we're excited to put more of Cloudflare's developer tools in the hands of our community in the coming months.” - Harrison Chase, Co-Founder and CEO, LangChain
In this post, we’ll share why we’re so excited about LangChain and walk you through how to build your first LangChainJS + Cloudflare Workers application.
For the uninitiated, LangChain is a framework for building applications powered by large language models (LLMs). It not only lets you fairly seamlessly switch between different LLMs, but also gives you the ability to chain prompts together. This allows you to build more sophisticated applications across multiple LLMs, something that would be way more complicated without the help Continue reading
How to secure Generative AI applications
I remember when the first iPhone was announced in 2007. This was NOT an iPhone as we think of one today. It had warts. A lot of warts. It couldn’t do MMS for example. But I remember the possibility it brought to mind. No product before had seemed like anything more than a product. The iPhone, or more the potential that the iPhone hinted at, had an actual impact on me. It changed my thinking about what could be.
In the years since no other product came close to matching that level of awe and wonder. That changed in March of this year. The release of GPT-4 had the same impact I remember from the iPhone launch. It’s still early, but it's opened the imagination, and fears, of millions of developers in a way I haven’t seen since that iPhone announcement.
That excitement has led to an explosion of development and hundreds of new tools broadly grouped into a category we call generative AI. Generative AI systems create content mimicking a particular style. New images that look like Banksy or lyrics that sound like Taylor Swift. All of these Generative AI tools, whether built on top of GPT-4 or something Continue reading
Building Cloudflare on Cloudflare


Cloudflare’s website, application security and performance products handle upwards of 46 million HTTP requests per second, every second. These products were originally built as a set of native Linux services, but we’re increasingly building parts of the system using our Cloudflare Workers developer platform to make these products faster, more robust, and easier to develop. This blog post digs into how and why we’re doing this.
System architecture
Our architecture can best be thought of as a chain of proxies, each communicating over HTTP. At first, these proxies were all implemented based on NGINX and Lua, but in recent years many of them have been replaced - often by new services built in Rust, such as Pingora.
The proxies each have distinct purposes - some obvious, some less so. One which we’ll be discussing in more detail is the FL service, which performs “Front Line” processing of requests, applying customer configuration to decide how to handle and route the request.
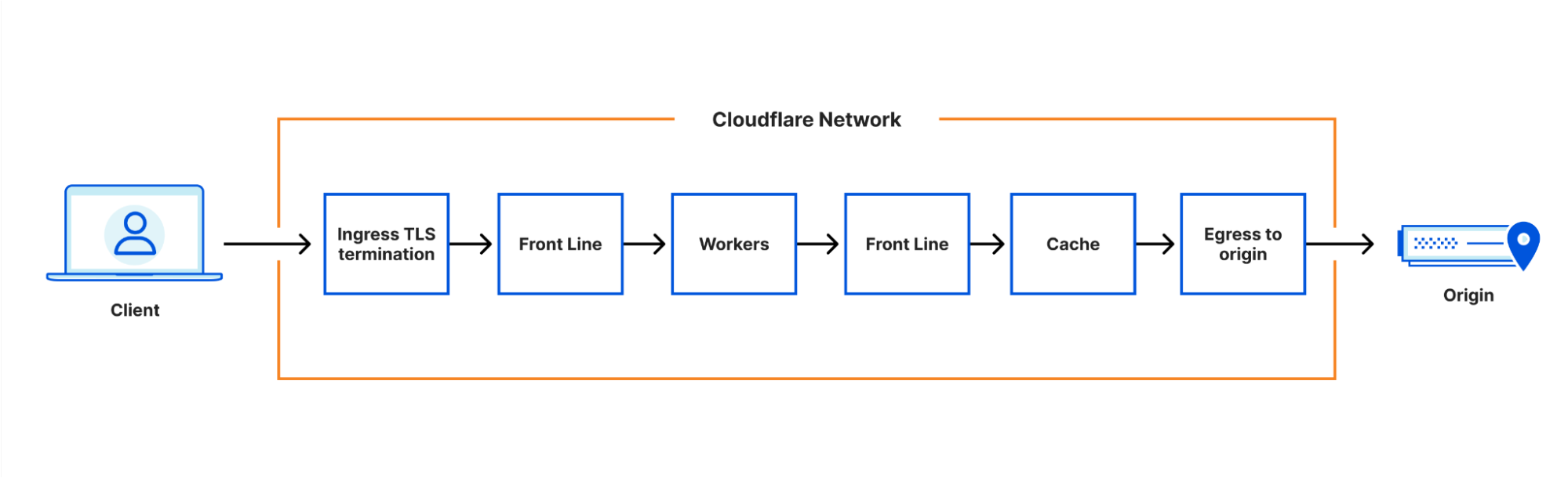
This architecture has worked well for more than a decade. It allows parts of the system to be developed and deployed independently, parts of the system to be scaled independently, and traffic to be routed to different nodes in Continue reading
How Cloudflare is powering the next generation of platforms with Workers
We launched Workers for Platforms, our Workers offering for SaaS businesses, almost exactly one year ago to the date! We’ve seen a wide array of customers using Workers for Platforms – from e-commerce to CMS, low-code/no-code platforms and also a new wave of AI businesses running tailored inference models for their end customers!
Let’s take a look back and recap why we built Workers for Platforms, show you some of the most interesting problems our customers have been solving and share new features that are now available!
What is Workers for Platforms?
SaaS businesses are all too familiar with the never ending need to keep up with their users' feature requests. Thinking back, the introduction of Workers at Cloudflare was to solve this very pain point. Workers gave our customers the power to program our network to meet their specific requirements!
Need to implement complex load balancing across many origins? Write a Worker. Want a custom set of WAF rules for each region your business operates in? Go crazy, write a Worker.
We heard the same themes coming up with our customers – which is why we partnered with early customers to build Workers for Platforms. We worked with the Continue reading
Find the Optimal Level of Automation Abstraction
Tom Ammon sent me his thoughts on choosing the right level of abstraction in your network automation solution as a response to my What Is Intent-Based Networking blog post, and allowed me to publish them on ipspace.net.
I totally agree with your what vs how example with OSPF. I work on a NOS team where if we wanted, we could say, instead of “run OSPF on these links”, do this:
Find the Optimal Level of Automation Abstraction
Tom Ammon sent me his thoughts on choosing the right level of abstraction in your network automation solution as a response to my What Is Intent-Based Networking blog post, and allowed me to publish them on ipspace.net.
I totally agree with your what vs how example with OSPF. I work on a NOS team where if we wanted, we could say, instead of “run OSPF on these links”, do this: