Is IPV6 Dual-Stack really a best method for IPv6 design ?
There are mainly three IPv6 transition methods; Dual-Stack, Tunnelling and Translation. Careful engineers can understand the difference between IPv6 migration and IPv6 transition. All of these three technologies are used to bring IPv6 protocol capabilities in addition to IPv4, they are not migration mechanisms. Migration means removing IPv4 completely and running only IPv6 only in […]
The post Is IPV6 Dual-Stack really a best method for IPv6 design ? appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
A.T. Still University greatly improves firewall performance and security with cost-effective VMware NSX solution
ATSU revolutionized its schools and clinics with the cost-effective security solution, VMware NSX, which increases firewall performance, meets HIPAA compliance, automates services, and improves agility, resulting in more affordable tuition and better healthcare services.
Some of the business benefits:
- easy implementation
- cost effective
- better application performance
“VMware NSX is the most revolutionary development in our data center security in more than a decade. Not only do we save a significant amount of money in hardware costs, the micro-segmentation available through VMware NSX provides a dramatically more secure design than we could get with a physical firewall with DMZs.” — Iain Leiter, Network Engineer, A.T. Still University
Download the case study
The post A.T. Still University greatly improves firewall performance and security with cost-effective VMware NSX solution appeared first on The Network Virtualization Blog.
7 Reasons You Need 802.11ac
Find out how the latest WiFi protocol can boost WLAN performance.
SolarWinds Attacks the Hybrid IT Market
 SolarWinds' NPM 12 might give the company a leg up on other NPM vendors.
SolarWinds' NPM 12 might give the company a leg up on other NPM vendors.
Best Linux Command-Line Tools For Network Engineers
These Linux utilities come in handy when designing, implementing or troubleshooting a network.
Response: Why On-Premises Software Will Die Sooner
This is the most compelling article I’ve ever read about why on-premises applications/software are less competitive. I am reasonably certain that private cloud infrastructure can be as efficient as public cloud and cheaper over some period. What I’m coming to understand is that many of types of cloud-based applications may be much more efficent than […]
The post Response: Why On-Premises Software Will Die Sooner appeared first on EtherealMind.
Is BGP Really that Complex?
Anyone following the popular networking blogs and podcasts is probably familiar with the claim that BGP is way too complex to be used in whatever environment. On the other hand, more and more smart people use it when building their data center or WAN infrastructure. There’s something wrong with this picture.
Read more ...Fortinet Weaves AccelOps Into Its Security Fabric
 The deal ties Fortinet into the SIEM crowd.
The deal ties Fortinet into the SIEM crowd.
Forensic Lab Game Zero – Level 1 Results
The goal of the post is to provide solutions for the first level of the game for "hackers" created by forensic lab of CESNET association. With this game CESNET introduces a work of forensic analysts and test your knowledge of Linux OS. They are several assignments and practical tasks included inside Debian image which is available for download here. The question / answer sheet is located inside the home directory of user kassad.
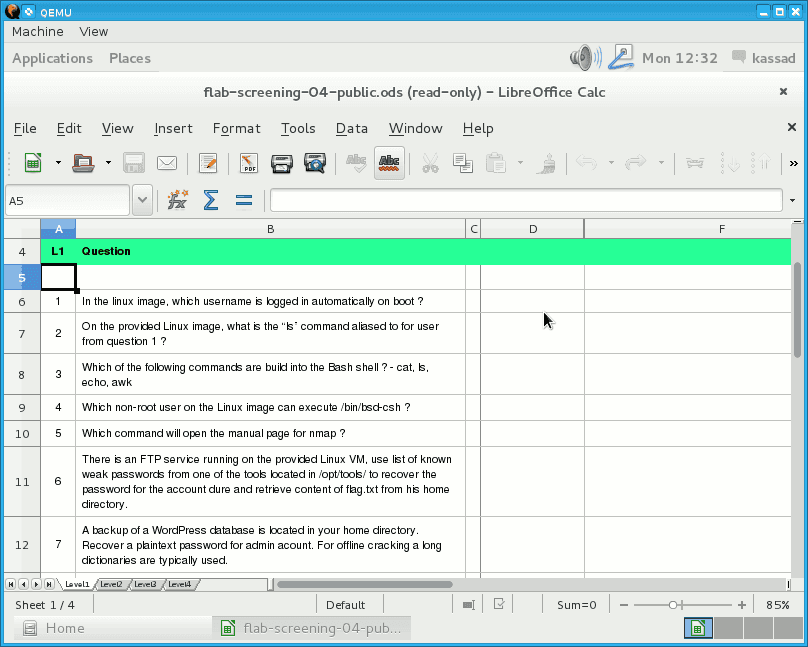
Picture 1 - Answer Sheet
1. In the Linux image, which username is logged in automatically on boot?
Check the desktop environment.
kassad@debian1989:~$ echo $DESKOP_SESSION
gnome-fallback
Check if automated login is enabled for Gnome desktop.
kassad@debian1989:~$ grep 'AutomaticLogin' /etc/gdm3/daemon.conf
AutomaticLoginEnable = true
AutomaticLogin = kassad
The automated login is enabled for the user kassad. Now we need to compute the sha1 hash for the result.
kassad@debian1989:~$ echo -n 'kassad' | sha1sum
fb1216c760d6c0996991108886d1797d8bd4ca27
2. On the provided Linux image, what is the “ls” command aliased to for user from question 1 ?
kassad@debian1989:~$ type ls
ls is aliased to `ls --color=auto'
We can get the result also by checking the content of the file /home/kassad/.bashrc.
kassad@debian1989:~$ grep 'alias ls' /home/kassad/.bashrc
alias ls='ls --color=auto'
kassad@debian1989:~$ echo -n 'ls --color=auto' Continue reading