Worth Reading: Building a (human) network, part 2

The post Worth Reading: Building a (human) network, part 2 appeared first on 'net work.
Drop and bogons list on Cisco router
The Cyberspace a.k.a. the Internet is full of bad guys wanting to mess with our computers right? Of course everyone of us have a firewall configured with proper access and inspection rules, don’t ya? Spamhaus and Team Cymru can help providing list of known bad IPs and subnets that should be filtered in our networks. […]Prophylactic Network Security

This week’s comedy gold was listening to a conversation emanating from a nearby inhabitant of our corporate cube accomodations, where one of my colleagues, Bob, was explaining to another coworker, George, the reasoning behind the decision to deploy firewalls to a particular new location.
Roughly summarized, the argument was this:
George, deploying a firewall is like having sex.
(No; I confess I had not anticipated ever typing that particular sentence, and I hope I never have to type it again.)
When you want to have sex, you decide whether you want a baby, and thus you choose whether or not to use contraception. If you don’t use contraception, while there’s no guarantee that a baby will arrive, there’s a real good chance that it will, so don’t be surprised if it does. Contraception isn’t perfect, but it at least reduces the likelihood of having a baby.
I confess I was laughing hard as I listened to the explanation because it’s an inspired analogy. However, buried somewhere in my subconscious was an Australian voice saying something like All these security products are a waste of money. It’s cheaper to save the money you would have spent, deal with a breach Continue reading
Featured Interview: CA Technologies’ Tim Diep – Why Network Assurance is Vital to the Service Chain
 Network assurance saves you time, money and keeps you away from implementation sweats. Learn more with CA Technologies' Tim Diep.
Network assurance saves you time, money and keeps you away from implementation sweats. Learn more with CA Technologies' Tim Diep.
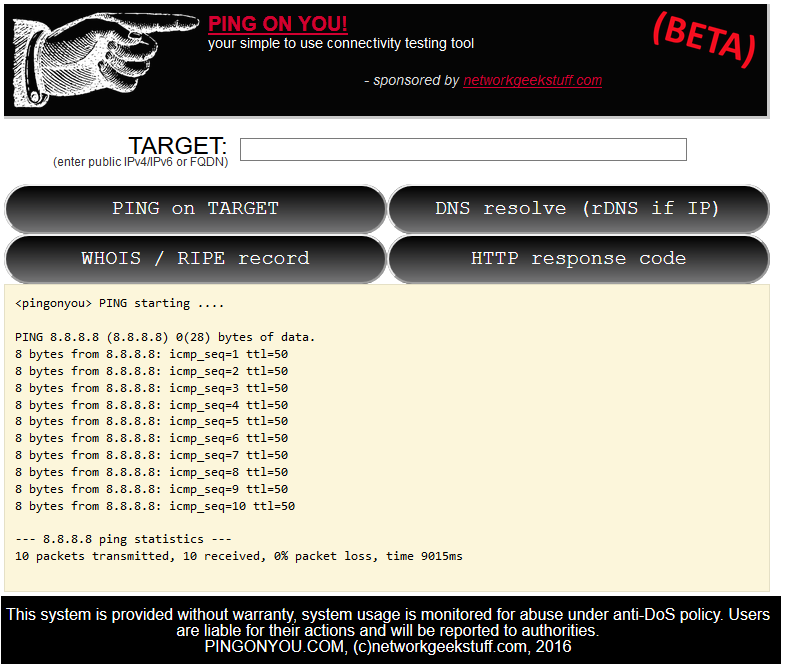
Ping on You! – small weekend web/CGI project
For best article visual quality, open Ping on You! – small weekend web/CGI project directly at NetworkGeekStuff.
After a few previous web programming endeavors (both here on networkgeekstuff.com with SDN programming and in real life job) I had a taste to develop “something” and since I am a network geek, I wondered what I have needed in the past as network tools that would ideally be placed on the internet. So I came to the very basic list of things like ping, nslookup or putty as tool accessible only via a browser.
So without more delay, I give you first beta release of Ping on You! – pingonyou.com the list of current features is:
- ping
- nslookup
- wget (for http response checks)
- whois / ripe database
Here is a quick view how it looks when you try to ping google’s public DNS service on 8.8.8.8, since in the background a linux like ping tool is used, you have the same output:
Additionally, here are some features that I plan to do when I get more time, however no release date right now because there are much more complex than the above ones:
- TCP port openings checks Continue reading
[minipost] Windows partition editing with diskpart
For best article visual quality, open [minipost] Windows partition editing with diskpart directly at NetworkGeekStuff.
This will really be a micro-post as I only want to document this for my benefit. This is a way how to change partition table for disks, or USB sticks. In my example, I had a linux live boot USB stick that I needed to quickly convert into a usable storage USB stick with NTFS under windows and of course the visual GUI tools under My Computer -> Manage -> Disk Management was not having full visibility on all partitions that the linux created on this USB stick, so this is how to actually do partitioning on windows.
So without more delay, this is an example how to clean the USB stick partition table and reformat it for windows use:
- start command prompt as Administrator and type “diskpart”
- enter “list disk”
- enter “select disk X”, where X is the and number of your USB stick ( ergo “select disk 1″ )
- enter “clean”
- enter “create partition primary”
- enter “select partition 1″
- enter “active”
- enter “format quick fs=ntfs”
- enter “assign”
- enter “exit” to leave diskpart
In summary, short, but hopefully useful minipost for someone.
Beyond Software-Defined Networks
In the future, will software define everything?
Containers & Comparisons: Shovel Or Spoon?
Evaluating container technologies and tools requires looking at appropriate metrics and asking the right questions.
Securing A Cisco Router: The Basics
Don’t leave your Cisco device exposed on the Internet. Take these steps for basic security.
California Nurds by Katy Sperry

California Nurds
I know a place
Where the tech is truly awesome
Smart network folks; all clustered
inside CA’s borders
Cablin’ guys and gals
Running fibers to the servers.
We’re all hard core geeks, we are
certified nerf herders.
You may think you are sad,
But nothing comes close
To the silicon coast
Santa Clara’s just mad, you can’t
help your nerd lust
Oooooh Oh Oooooh
California nurds;
we are incredible!
Armed with Flukes,
we’re testing non stop.
Wi Fi smarts
so hot
we’ll melt your antenna
Oooooh Oh Oooooh
California nurds,
we like telemetry;
But we don’t
like SNMP.
West Coast time is lame
so we use UTC
Oooooh Oh Oooooh
We love unicorns, shooting
rainbows from their rear ends.
We’re Software Defined, running
everything in Python.
–John Herbert, with sincere apologies to Katy Perry
If you liked this post, please do click through to the source at California Nurds by Katy Sperry and give me a share/like. Thank you!
Test-Driving OSPF on RouterOS – Interoperability
So I wrote about OSPF on RouterOS in my previous post. It was a nice experiment to learn about routing protocols. I wanted to take it a little further and test Interoperability of RouterOS with other open source solutions. This post is an update from the previous one and I will add OSPF neighbor nodes … Continue reading Test-Driving OSPF on RouterOS – InteroperabilityTest-driving OSPF on RouterOS
I came across RouterOS by MikroTik© which provides advances routing protocol support. What is more amazing is they provide a RouterOS in a virtual form-factor called Cloud Hosted Router (CHR) that can be installed on hypervisors like KVM/VirtualBox/VMware. Please look at licensing model at http://wiki.mikrotik.com/wiki/Manual:CHR#CHR_Licensing This is perfect for learning purposes and experimenting at home. … Continue reading Test-driving OSPF on RouterOSSDxCentral Weekly News Roundup — March 25, 2016
 There were big personnel changes at Cisco and Cumulus.
There were big personnel changes at Cisco and Cumulus.