Building a Small Network with ChatGPT
I must be a good prompt engineer – every time I ask ChatGPT something really simple it spews out nonsense. This time I asked it to build a small network with four routers:
I have a network with four Cisco routers (A,B,C,D). They are connected as follow: A-B, B-C, A-D, D-C. Each router has a loopback interface. Create router configurations that will result in A being able to reach loopback interfaces of all other routers.
Here’s what I got back1:
Here’s an example configuration for the four routers that should allow Router A to reach the loopback interfaces of all other routers:
Amazon & De Beers to Power Quantum Networks With Synthetic Diamonds
Diamond-enabled quantum networking through a collaboration between AWS and De Beers subsidiary Element Six could bring enhanced communication and data security in fields such as finance, healthcare, and defense.Edge Computing Use Cases: Helping Businesses Access SD-WAN/SSE
How can edge computing be leveraged to ensure every small business benefits from the latest SD-WAN/SSE technologies?Announcing VMware HCX+ Initial Availability
If you had to sum up multi-cloud management in a single word, “complex” would be a fair choice. Although multi-cloud strategies vary from one organization to the next—i.e., some use a mix of public and private clouds while others might use only public or only private infrastructures—all multi-cloud architectures significantly increase the complexity and challenges that IT organizations must navigate.
Today, we’re excited to announce a new offering, HCX+, designed to help mitigate the challenges of thriving in a multi-cloud world. By helping to streamline and accelerate workload migration and mobility between on-premises, public cloud, and private cloud environments, HCX+ simplifies complex processes like data center modernization, hardware refresh, data center consolidation, data center evacuation, cloud migration, data center extension, cloud bursting, and cloud rebalancing.
Keep reading for an overview of the major benefits and features that HCX+ brings to the table.
Announcing HCX+ Initial Availability
HCX+, which is in initial availability as of today, is a SaaS-based workload migration and mobility service from VMware that provides centralized management, orchestration, and observability for migration, repatriation, and rebalancing initiatives across multi-cloud environments.
HCX+ builds on VMware’s existing HCX solution, enabling easier and faster configuration and operability. With HCX+, migration Continue reading
Day Two Cloud 190: Serious Public Clouds Invest In Infrastructure With Charles Fitzgerald
On today's Day Two Cloud we dive into how the public clouds spend their money and what IT and engineering folks can learn from those spending patterns. We also look at the notion of cloud repatriation and how prevalent (or not) it is. Our guest is Charles Fitzgerald, a CapEx obsessive who writes the Platformonomics blog.
The post Day Two Cloud 190: Serious Public Clouds Invest In Infrastructure With Charles Fitzgerald appeared first on Packet Pushers.
Day Two Cloud 190: Serious Public Clouds Invest In Infrastructure With Charles Fitzgerald
On today's Day Two Cloud we dive into how the public clouds spend their money and what IT and engineering folks can learn from those spending patterns. We also look at the notion of cloud repatriation and how prevalent (or not) it is. Our guest is Charles Fitzgerald, a CapEx obsessive who writes the Platformonomics blog.Introducing Cloudflare’s new Network Analytics dashboard


We’re pleased to introduce Cloudflare’s new and improved Network Analytics dashboard. It’s now available to Magic Transit and Spectrum customers on the Enterprise plan.
The dashboard provides network operators better visibility into traffic behavior, firewall events, and DDoS attacks as observed across Cloudflare’s global network. Some of the dashboard’s data points include:
- Top traffic and attack attributes
- Visibility into DDoS mitigations and Magic Firewall events
- Detailed packet samples including full packets headers and metadata
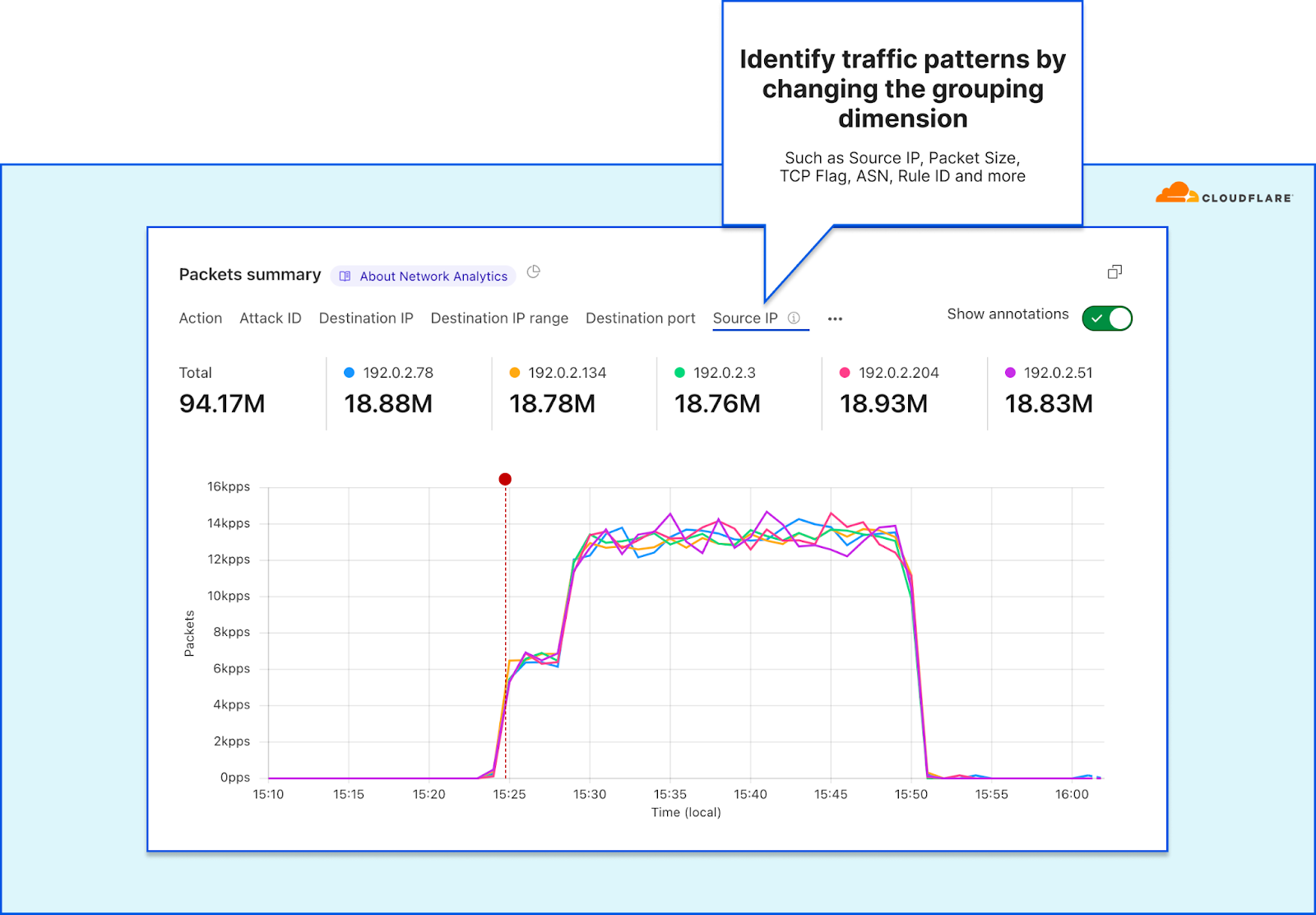
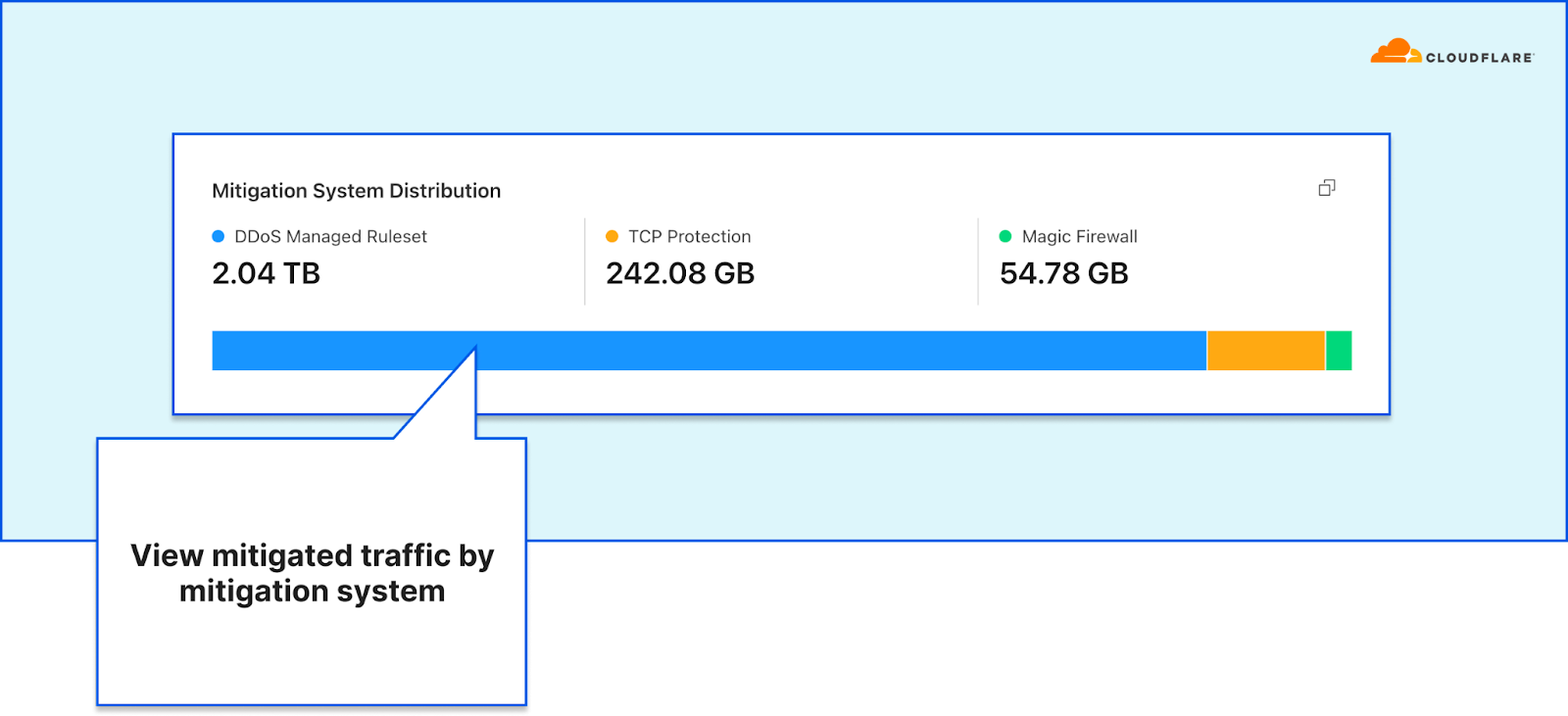
This dashboard was the outcome of a full refactoring of our network-layer data logging pipeline. The new data pipeline is decentralized and much more flexible than the previous one — making it more resilient, performant, and scalable for when we add new mitigation systems, introduce new sampling points, and roll out new services. A technical deep-dive blog is coming soon, so stay tuned.
In this blog post, we will demonstrate how the dashboard helps network operators:
- Understand their network better
- Respond to DDoS attacks faster
- Easily generate security reports for peers and managers
Understand your network better
One of the main responsibilities network operators bare is ensuring the operational stability Continue reading
Internet disruptions overview for Q1 2023

Cloudflare operates in more than 285 cities in over 100 countries, where we interconnect with over 11,500 network providers in order to provide a broad range of services to millions of customers. The breadth of both our network and our customer base provides us with a unique perspective on Internet resilience, enabling us to observe the impact of Internet disruptions.
We entered 2023 with Internet disruptions due to causes that ran the gamut, including several government-directed Internet shutdowns, cyclones, a massive earthquake, power outages, cable cuts, cyberattacks, technical problems, and military action. As we have noted in the past, this post is intended as a summary overview of observed disruptions, and is not an exhaustive or complete list of issues that have occurred during the quarter.
Government directed
Iran
Over the last six-plus months, government-directed Internet shutdowns in Iran have largely been in response to protests over the death of Mahsa Amini while in police custody. While these shutdowns are still occurring in a limited fashion, a notable shutdown observed in January was intended to prevent cheating on academic exams. Internet shutdowns with a similar purpose have been observed across a number of other countries, and have also occurred in Continue reading
Should I Care About RPKI and Internet Routing Security?
One of my subscribers sent me this question:
I’m being asked to enter a working group on RPKI and route origination. I’m doing research, listening to Jeff Tantsura, who seems optimistic about taking steps to improve BGP security vs Geoff Huston, who isn’t as optimistic. Should I recommend to the group that the application security is the better investment?
You need both. RPKI is slowly becoming the baseline of global routing hygiene (like washing hands, only virtual, and done once every blue moon when you get new IP address space or when the certificates expire). More and more Internet Service Providers (including many tier-1 providers) filter RPKI invalids thus preventing the worst cases of unintentional route leaks.
Should I Care About RPKI and Internet Routing Security?
One of my subscribers sent me this question:
I’m being asked to enter a working group on RPKI and route origination. I’m doing research, listening to Jeff Tantsura, who seems optimistic about taking steps to improve BGP security vs Geoff Huston, who isn’t as optimistic. Should I recommend to the group that the application security is the better investment?
You need both. RPKI is slowly becoming the baseline of global routing hygiene (like washing hands, only virtual, and done once every blue moon when you get new IP address space or when the certificates expire). More and more Internet Service Providers (including many tier-1 providers) filter RPKI invalids thus preventing the worst cases of unintentional route leaks.
Stable Diffusion Installation on Linux
Stable Diffusion is a text-to-image latent diffusion model created by the researchers and engineers from […]
The post Stable Diffusion Installation on Linux first appeared on Brezular's Blog.
FCC Creates New Space Bureau to Fuel Satellite Industry Expansion
The move is designed to give rise to Internet access and emerging satellite-to-cellular services for enterprises from SpaceX, OneWeb, Globalstar, Amazon, Iridium, and their wireless operator partners.Privacy And Networking Part 8: IPv6 Addresses And Privacy
One of the biggest advantages of IPv6 is the ease of renumbering thanks to SLAAC and DHCPv6. Easy renumbering of IPv6 addresses should, in theory, make some privacy protection methods easy to implement. Here's how it works, and and how it doesn't solve all privacy problems.
The post Privacy And Networking Part 8: IPv6 Addresses And Privacy appeared first on Packet Pushers.
What is SOC 2 and how do you achieve SOC 2 compliance for containers and Kubernetes?
SOC 2 is a compliance standard for service organizations, developed by the American Institute of CPAs (AICPA), which specifies how organizations should manage customer data. SOC 2 is based on five overarching Trust Services Criteria (TSC): security, availability, processing integrity, confidentiality, and privacy. Specifically, the security criteria are broken down into nine sections called common criteria (CC):
- CC1: Control Environment
- CC2: Communication and Information
- CC3: Risk Assessment
- CC4: Monitoring Activities
- CC5: Control Activities
- CC6: Logical and Physical Access Controls
- CC7: System Operations
- CC8: Change Management
- CC9: Risk Mitigation
How does SOC 2 compliance apply to containers and Kubernetes?
Running Kubernetes clusters often presents challenges for CC6 (logical and physical access), CC7 (systems operations), and CC8 (change management) when trying to comply with SOC 2 standards.
In this technical blog, we will dive into how Calico can help you achieve full compliance in achieving all the requirements of CC6. To understand how to achieve compliance with CC7 and CC8, you can review our SOC 2 white paper.
| Control # | Compliance requirements | Calico controls |
| CC 6.1, 6.6, 6.7, 6.8
|
Implement logical access security measures to authorized systems only, implement controls to prevent or detect and act upon Continue reading |