Equinix Adopts Facebook’s Wedge Switch
Equinix joins Open Compute Project and will deploy Wedge in its 145 data center hubs.
Digital Transformation Via The Cloud
Walmart’s OneOps illustrates how the cloud can be a starting point for creating a digital business.
Cisco VIRL Troubleshooting
Find out how to resolve issues when modeling multiple devices using Cisco Virtual Internet Routing Lab.
Subscriber management on Juniper MX with FreeRadius
Quite often on my travels I sometimes encounter technologies I worked on a long time ago that I seem to bump into again later in life, in this case it’s terminating broadband subscribers. Many years ago I worked on large-scale Cisco platform terminating DSL business broadband users on Cisco 7200s over ATM, recently I’ve been involved in a couple of jobs where FTTC users are being terminated on Juniper MX480 routers, using double-tagging and PPPoE, this first post looks into how to setup a Juniper MX router from scratch and terminate PPPoE subscribers authenticated by RADIUS (in this case FreeRadius)
The topology:
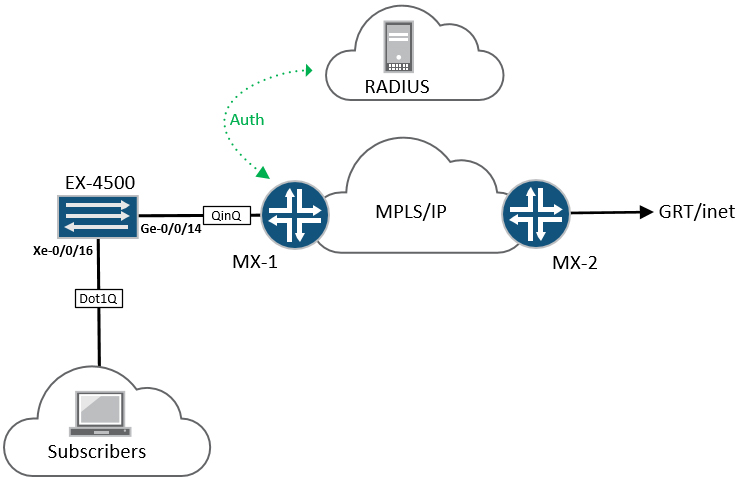
Equipment used for this is as follows:
- MX-1 is a Juniper MX-5 router, acting as the BRAS or BNG
- MX-2 is also an MX-5 is a generic PE with simulated external connectivity
- EX-4500 is self explanatory, and is basically doing QinQ towards the BNG
- RADIUS is an Ubuntu server running FreeRadius (explained in more detail later)
- For Broadband subscribers, I’m lucky to have access to an IXIA XG12 tester
Before we get to the BNG side of things, lets take a look at the access network (EX-4500) essentially, this switch is doing several things:
- Each individual subscriber Continue reading
SDN 101: Centralized Control Plane
I spent the first half of the Introduction to SDN webinar explaining various attempts at defining SDN, and the obvious place to start was the centralized control plane mantra.
This part of the webinar is now public; to access the rest of the webinar, register on my web site.
CCIE – CCIE SPv4 Review by Nick Russo
My friend Nick Russo just took the SPv4 lab and passed it. This is his story.
On 8 March 2016, I passed Cisco’s CCIE Service Provider version 4 lab exam. It was my second attempt. I realize there is little information on the Internet about this test because it is still rather new. This blog post will detail my personal strategy for passing the CCIE SPv4 lab exam. Most CCIEs and CCDEs agree that a smart strategy is a critical part of passing any Cisco expert-level lab; many folks are technically proficient but need to remain organized to be effective.
Note: the views expressed in this blog post are mine alone and do not necessarily represent the views of Cisco. No correlation between my comments and Cisco’s recommendation study strategies should be made. Also note that no technical exam content is discussed here in accordance with Cisco’s CCIE NDA. Comments fishing for such information will be deleted.
First, the new blueprint has 3 sections: Troubleshooting (TSHOOT), Diagnostic (DIAG), and Configuration (CONFIG). The CCIE SPv4 program explains these topics in detail within the new blueprint so that is not discussed again here. Since each section is slightly different, one should have Continue reading
Junos Space – checking processes are running
After two miserable nights trying to upgrade Space 13.1R1.6 to 14.1R1.9, I finally called up JTAC for some assistance. For some reason the upgrade started, but never finished – the GUI remaining in ‘maintenance mode’ for several hours.
What they did:
Checked the services – all were showing as down:
service jmp-watchdog status
service jboss status
service jboss-dc status
Tried to start jboss-dc, but it complained that it couldn’t write or create /var/log/jboss.
Did the following to change ownership from root:root on the /var/log directory:
chown jboss:root /var/log
Did this:
service jboss-dc start
service jboss start
At this point the GUI started showing ‘Junos space is preparing to start up’, and after 20 minutes it changed to say the applications were deploying.
PHPBB and website integration
I needed to integrate a website login with a phpBB3 forum recently, and this blog post came in really useful: http://www.3cc.org/blog/2010/03/integrating-your-existing-site-into-phpbb3/
The only issue with it was the logout section – it uses $_GET, but when I implement this I get a message saying that this is an ‘illegal use of $_GET’.
Instead, the logout code that worked for me was this – it uses request_var() instead:
<?php
$cp = request_var('cp', '');
if ($cp == "logout") {
$user->session_kill();
$user->session_begin();
echo "Logged out";
}
?>SANs Are a ‘Pain Point’ in Converged Data Centers, Says Plexxi
 Plexxi has created a product and lined up resellers.
Plexxi has created a product and lined up resellers.
Going to CiscoLive US 2016? Don’t Forget Your Kilt!
I don’t recall the exact details of how “#KiltedMonday” started last year at CiscoLive US 2015.
I just know
- Erik (@ucgod), Steve (@wifijanitor), and JD (@subnetwork) were pivotal to the wonderfully fantastic and fun idea
- I’m SO joining this year! — Just ordered my kilt.
- Scott (@ScottMorrisCCIE) is not only planning on joining this year… but he is hoping it falls on the day he will be presenting