More Features, Improved Lock-In
Found an interesting article on High Scalability blog (another must-read web site) on how PostgreSQL improves locking behavior in high-volume transaction environment.
Needless to say, the feature is totally proprietaryrather unique and not available in most other database products. Improved locking behavior ⇒ improved lock-in.
Moral of the story: Stop yammering. Networking is no different from any other field of IT.
Update: Yep, I goofed up on the proprietary bit (it was one of those “I don’t think this word means what you think it means” gotchas). However, if you think open source product can't have proprietary features or you can’t get locked into an open-source product, I congratulate you on your rosy perspective. Reality smudged mine years ago.
Ansible inventory, role variables and facts
I’ve been struggling a bit to understand how to use inventory, role variables and facts in the playbooks i’ve been working on (mostly around provisioning opencontrail on top of kubernetes/openshift-origin). I finally came up with a model that made sense to me. This is probably well understood by everyone else but i couldn’t quite grok it until i worked out the following example.
User configuration options should be set:
– In group_vars/all.yml for settings that affect all hosts;
– In the inventory file, for host and group variables;
As in this example:
It is useful to establish a convention for variables that are specific to the deployment (e.g. user settable variables). In this case i’m using flag_<var> as a convention for deployment specific variables.
Most of these would have defaults. In order to set the defaults, the playbook defines a role variable (flag_user_<var> in this example). The playbook role then uses flag_user_<var> rather than the original flag_<var>.
Role variables can use jinja template logic operations as well as filters. The most common operation is to use a <code>default</code> filter as in the example playbook bellow. But more complex logic can be built using {%if <expression> %}{% endif Continue reading
CCDE – Optical Design Considerations
Introduction
As a network architect you should not have to know all the details of the physical and data link layer. What you need to know though is how different transports can support the topology that you are looking to build. If you buy a circuit from an ISP, what protocols can you run over it? Is running MPLS over the circuit supported? What’s the maximum MTU? Is it possible to run STP over the link? This may be important when connecting data centers together through a Data Center Interconnect (DCI).
To be able to connect two data centers together, you will need to either connect via fibre or over a wavelength or buy circuits from an ISP. Renting a fibre will likely be more expensive but also more flexible if you have the need to run protocols such as MPLS over the link. For a pure DCI, just running IP may be enough so there could be cost savings if buying a circuit from an ISP instead.
For a big enough player it may also be feasible to build it all yourself. This post will look at the difference between Coarse Wave Division Multiplexing (CWDM) and Dense Wave Division Continue reading
SDxCentral Roundup — SDN & OpenFlow World Congress
 Colt leverages SDN for data center connects; ONF conducts multi-vendor wireless transport SDN test.
Colt leverages SDN for data center connects; ONF conducts multi-vendor wireless transport SDN test.
Capture data on open-source router interfaces in GNS3
In this post, I will show how to set up data capture in the GNS3 network simulator when using network devices that are emulated by VirtualBox or QEMU virtual machines.
The GNS3 network simulator makes it easy for users to capture and view data passing across the interfaces of devices running in a GNS3 network simulation. The GNS3 documentation covers how to capture data from devices running on Dynamips in GNS3 but the procedures for capturing data from devices running in other hypervisors, such as VirtualBox or QEMU/KVM, are not well documented.
While GNS3 users may start and stop data capture on Dynamips VM interfaces any time they wish, they must plan ahead when they intend to capture data on open-source routers and hosts running on VirtualBox or QEMU virtual machines.
10 Gbps of Layer 2 throughput is possible using MikroTik’s EoIP tunnel.
[adrotate banner=”5″]
[metaslider id=282]
Getting to 10 Gbps using EoIP
The EoIP tunnel protocol is one of the more popular features we see deployed in MikroTik routers. It is useful anywhere a Layer 2 extension over a Layer 3 network is needed and can be done with very little effort / complexity. One of the questions that seems to come up on the forums frequently is how much traffic can an EoIP tunnel handle which is typically followed by questions about performance with IPSEC turned on. Answers given by MikroTik and others on forums.mikrotik.com typically fall into the 1 to 3 Gbps range with some hints that more is possible. We searched to see if anyone had done 10 Gbps over EoIP with or without IPSEC and came up empty handed. That prompted us to dive into the StubArea51 lab and set up a test network so we could get some hard data and definitive answers.
The EoIP protocol and recent enhancements
Ethernet over IP or EoIP is a protocol that started as an IETF draft somewhere around 2002 and MikroTik developed a proprietary implementation of it that has been in RouterOS for quite a while. Continue reading
Could Cisco Sell Hardware Subscriptions? Brocade, Big Switch Already Do
Brocade and Big Switch offer subscription and capacity pricing models for network hardware. Could Cisco follow?
The post Could Cisco Sell Hardware Subscriptions? Brocade, Big Switch Already Do appeared first on Packet Pushers.
IBM Snags OpenStack Expert from HP
 Mestery will lead an IBM team focused on OpenStack networking.
Mestery will lead an IBM team focused on OpenStack networking.
PlexxiPulse—Forrester Tech Mixer Recap & A New PlexxiTube Video
Earlier this week our team was in Cambridge at the Forrester Tech Mixer. We had engaging conversations with Forrester analystsand emerging technology companies in the area. We always enjoy attending these events to hear about industry trends and innovative new technologies. It was a great time had by all!


We’ve also uploaded a new PlexxiTube video on Plexxi’s automated network. Take a look!
Below are a few of our top picks for our favorite news articles of the week. Have a great weekend.
FierceEnterpriseCommunications: Plexxi CEO: The future of networking is photonic underlays
By Chris Talbot
As he approaches his first anniversary as CEO of next-generation networking vendor Plexxi, Rich Napolitano is talking about the future of networks, and they’re not going to be focused on software-defined networking technology. SDN will play a huge role, of course, but it’s an overlay technology. Plexxi is focused on redefining the underlay, and it’s using photonic technology to do it.
Network Computing: SDN’s Northbound Interface Evolves
By Dr. Jim Metzler
Software defined networking requires both northbound and southbound interfaces to facilitate communication between physical devices, the SDN software and applications running on the network. On the southbound side, standards such as OpenFlow define Continue reading
SDxCentral Weekly News Roundup — October 16, 2015
 OpenStack debuts Liberty, ONUG announces POC for Nov. conference, new ETSI specs among this week’s news
OpenStack debuts Liberty, ONUG announces POC for Nov. conference, new ETSI specs among this week’s news
Red Hat Snaps Up IT Automation Startup Ansible
 Red Hat becomes more nimble with Ansible's IT automation technology.
Red Hat becomes more nimble with Ansible's IT automation technology.
Carrier SDN vs Overlay SDN: Duel or Duality?
 SDN is just the start of the journey to dynamic network services.
SDN is just the start of the journey to dynamic network services.
SD-WAN Vendor Roundup
The SD-WAN vendor scrum grows; an increasing number of companies are contending for a place in your WAN traffic patterns. Here’s a list of the companies (some of whom are Packet Pushers sponsors) I've heard present about their SD-WAN products, sorted alphabetically.
The post SD-WAN Vendor Roundup appeared first on Packet Pushers.
Getting Started with Packet Pushers Community Podcasting
We wrote this introductory guide to help those considering Packet Pushers community podcasting understand what is required. This is not a detailed list of everything you will need to know. Rather, this guide shares enough information to get you started. You'll still have to do a bit of Googling, research, and decision making of your own. We hope this helps. Happy podcasting!
The post Getting Started with Packet Pushers Community Podcasting appeared first on Packet Pushers.
iPexpert’s Newest “CCIE Wall of Fame” Additions 10/16/2015
Please join us in congratulating the following iPexpert students who have passed their CCIE lab!
A Look at the New WordPress Brute Force Amplification Attack
Recently, a new brute force attack method for WordPress instances was identified by Sucuri. This latest technique allows attackers to try a large number of WordPress username and password login combinations in a single HTTP request.
The vulnerability can easily be abused by a simple script to try a significant number of username and password combinations with a relatively small number of HTTP requests. The following diagram shows a 4-fold increase in login attempts to HTTP requests, but this can trivially be expanded to a thousand logins.
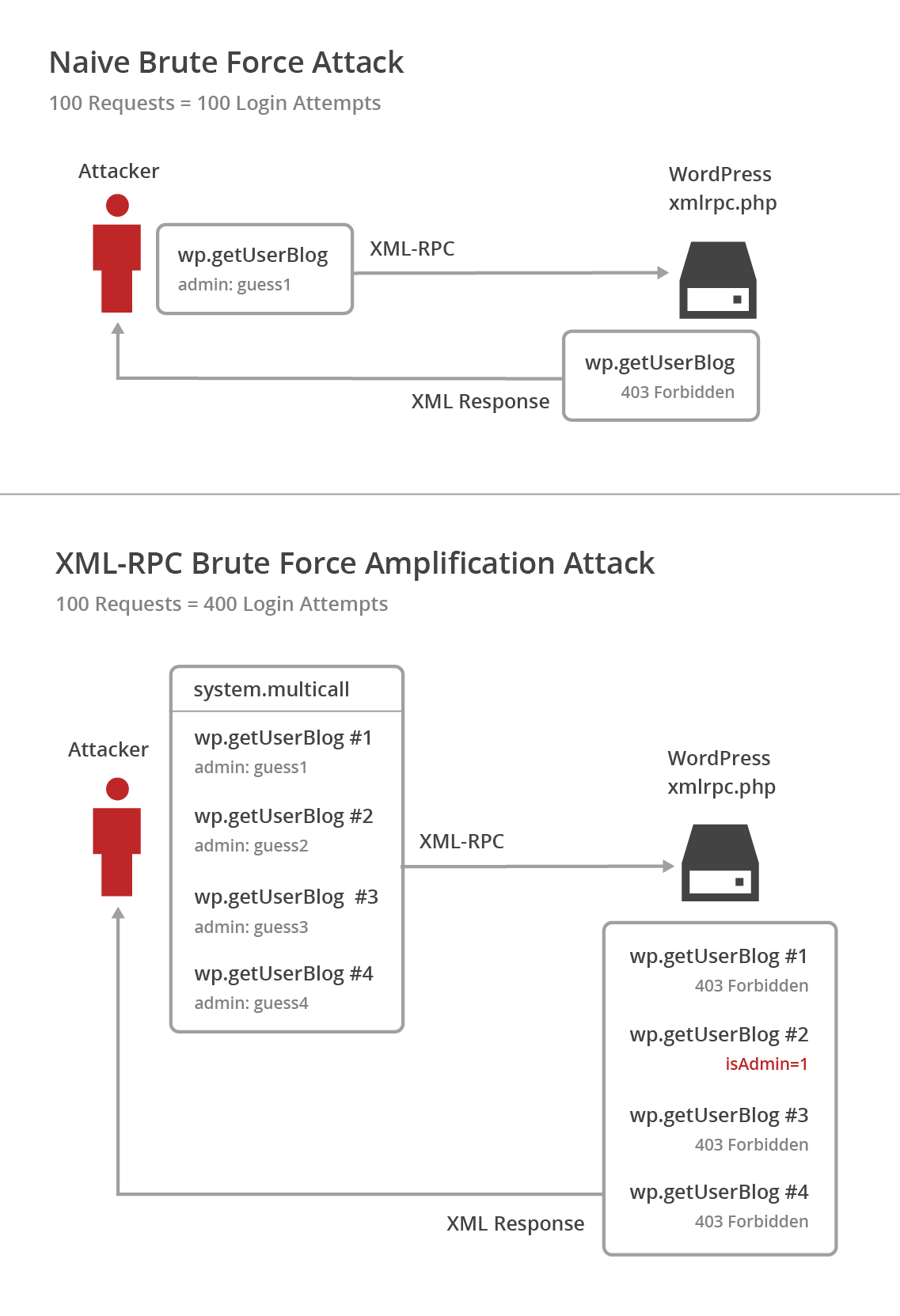
This form of brute force attack is harder to detect, since you won’t necessarily see a flood of requests. Fortunately, all CloudFlare paid customers have the option to enable a Web Application Firewall ruleset to stop this new attack method.
What is XML-RPC?
To understand the vulnerability, it’s important to understand the basics of the XML remote procedure protocol (XML-RPC).
XML-RPC uses XML encoding over HTTP to provide a remote procedure call protocol. It’s commonly used to execute various functions in a WordPress instance for APIs and other automated tasks. Requests that modify, manipulate, or view data using XML-RPC require user credentials with sufficient permissions.
Here is an example that requests a list Continue reading
Before adding solid-state drives, right-size your infrastructure using workload profiling
This vendor-written tech primer has been edited by Network World to eliminate product promotion, but readers should note it will likely favor the submitter’s approach.
If you’re looking to add Solid-State Drives to your storage environment you want to avoid under-provisioning to ensure performance and scalability, but to meet cost goals and avoid unnecessary spending you need to avoid over-provisioning. Workload profiling can help you achieve the critical balance.
A recent survey of 115 Global 500 companies by GatePoint Research and sponsored by Load DynamiX showed that 65% of storage architects say they are doing some sort of pre-deployment testing before making their investment decision. Alarmingly, only 36% understand their application workload I/O profiles and performance requirements. They don’t know what workload profiling is and how it can be used to accurately evaluate vendors against the actual applications that will be running over their particular storage infrastructure.
To read this article in full or to leave a comment, please click here
Radisys Integrates FlowEngine With Sanctum’s SDN Controller
 Radisys and Sanctum target CSPs with a blended SDN platform.
Radisys and Sanctum target CSPs with a blended SDN platform.
