Cloudflare One DLP integrates with Microsoft Information Protection labels


The crown jewels for an organization are often data, and the first step in protection should be locating where the most critical information lives. Yet, maintaining a thorough inventory of sensitive data is harder than it seems and generally a massive lift for security teams. To help overcome data security troubles, Microsoft offers their customers data classification and protection tools. One popular option are the sensitivity labels available with Microsoft Purview Information Protection. However, customers need the ability to track sensitive data movement even as it migrates beyond the visibility of Microsoft.
Today, we are excited to announce that Cloudflare One now offers Data Loss Prevention (DLP) detections for Microsoft Purview Information Protection labels. Simply integrate with your Microsoft account, retrieve your labels, and build rules to guide the movement of your labeled data. This extends the power of Microsoft’s labels to any of your corporate traffic in just a few clicks.
Data Classification with Microsoft Labels
Every organization has a wealth of data to manage, from publicly accessible data, like documentation, to internal data, like the launch date of a new product. Then, of course, there is the data requiring the highest levels of protection, such as customer PII. Continue reading
Adding Zero Trust signals to Sumo Logic for better security insights


A picture is worth a thousand words and the same is true when it comes to getting visualizations, trends, and data in the form of a ready-made security dashboard.
Today we’re excited to announce the expansion of support for automated normalization and correlation of Zero Trust logs for Logpush in Sumo Logic’s Cloud SIEM. As a Cloudflare technology partner, Sumo Logic is the pioneer in continuous intelligence, a new category of software which enables organizations of all sizes to address the data challenges and opportunities presented by digital transformation, modern applications, and cloud computing.
The updated content in Sumo Logic Cloud SIEM helps joint Cloudflare customers reduce alert fatigue tied to Zero Trust logs and accelerates the triage process for security analysts by converging security and network data into high-fidelity insights. This new functionality complements the existing Cloudflare App for Sumo Logic designed to help IT and security teams gain insights, understand anomalous activity, and better trend security and network performance data over time.
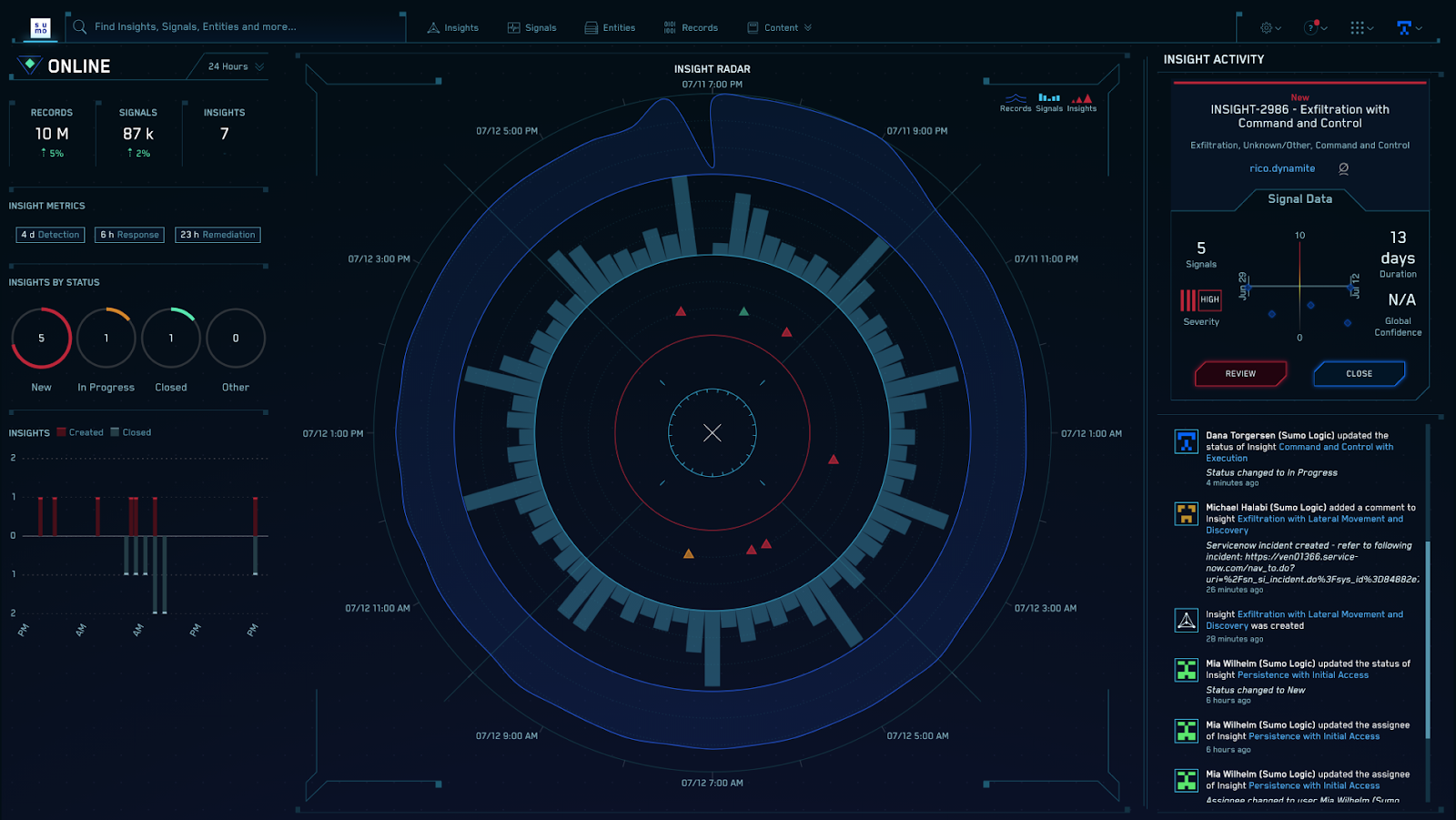
Deeper integration to deliver Zero Trust insights
Using Cloudflare Zero Trust helps protect users, devices, and data, and in the process can create a large volume of logs. These logs are helpful and important because Continue reading
The state of application security in 2023


One year ago we published our first Application Security Report. For Security Week 2023, we are providing updated insights and trends around mitigated traffic, bot and API traffic, and account takeover attacks.
Cloudflare has grown significantly over the last year. In February 2023, Netcraft noted that Cloudflare had become the most commonly used web server vendor within the top million sites at the start of 2023, and continues to grow, reaching a 21.71% market share, up from 19.4% in February 2022.
This continued growth now equates to Cloudflare handling over 45 million HTTP requests/second on average (up from 32 million last year), with more than 61 million HTTP requests/second at peak. DNS queries handled by the network are also growing and stand at approximately 24.6 million queries/second. All of this traffic flow gives us an unprecedented view into Internet trends.
Before we dive in, we need to define our terms.
Definitions
Throughout this report, we will refer to the following terms:
- Mitigated traffic: any eyeball HTTP* request that had a “terminating” action applied to it by the Cloudflare platform. These include the following actions:
BLOCK,CHALLENGE,JS_CHALLENGEandMANAGED_CHALLENGE. This does not include Continue reading
Scan and secure Atlassian with Cloudflare CASB


As part of Security Week, two new integrations are coming to Cloudflare CASB, one for Atlassian Confluence and the other for Atlassian Jira.
We’re excited to launch support for these two new SaaS applications (in addition to those we already support) given the reliance that we’ve seen organizations from around the world place in them for streamlined, end-to-end project management.
Let’s dive into what Cloudflare Zero Trust customers can expect from these new integrations.
CASB: Security for your SaaS apps
First, a quick recap. CASB, or Cloud Access Security Broker, is one of Cloudflare’s newer offerings, released last September to provide security operators - CISOs and security engineers - clear visibility and administrative control over the security of their SaaS apps.
Whether it’s Google Workspace, Microsoft 365, Slack, Salesforce, Box, GitHub, or Atlassian (whew!), CASB can easily connect and scan these apps for critical security issues, and provide users an exhaustive list of identified problems, organized for triage.
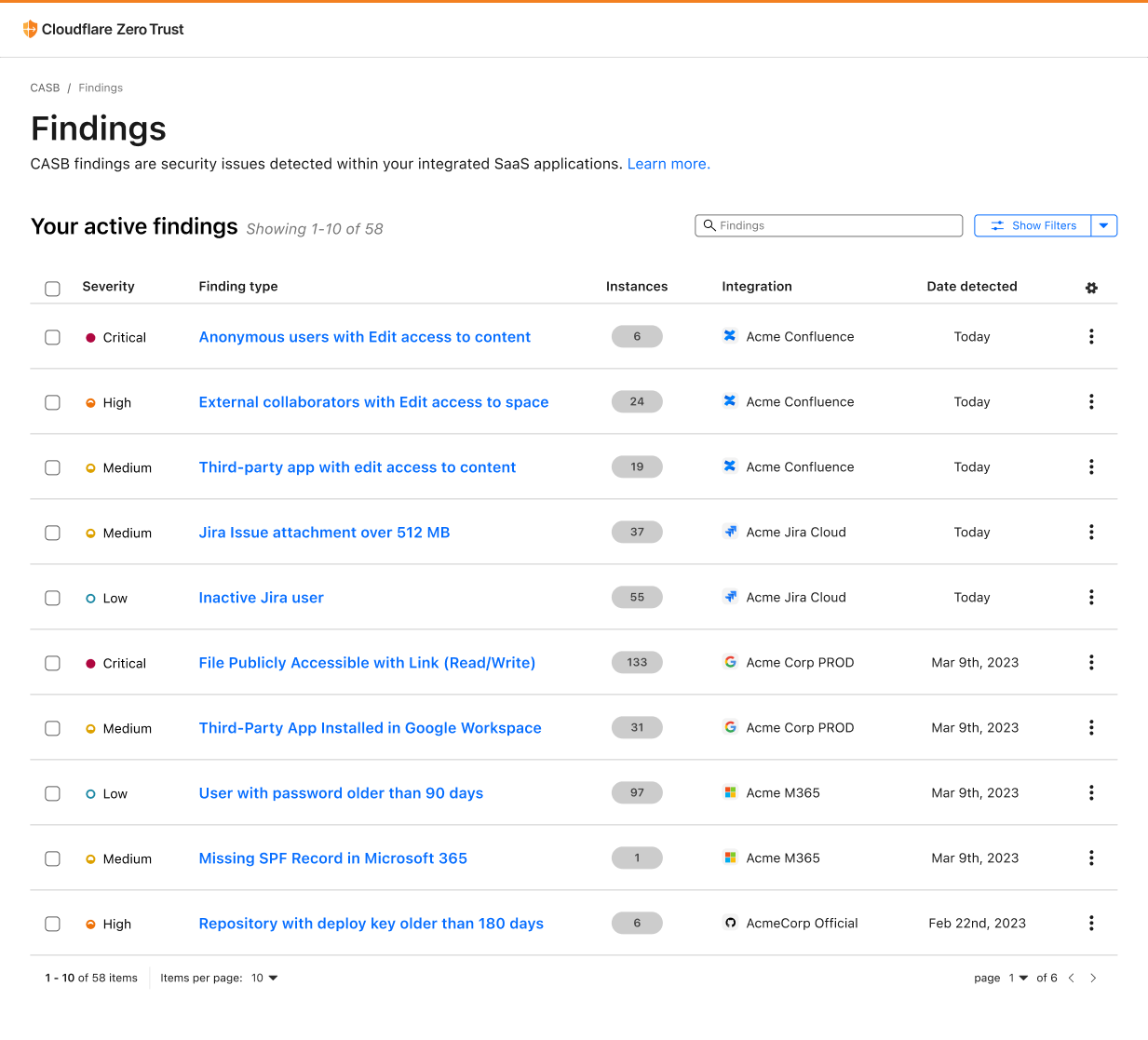
Scan Confluence with Cloudflare CASB
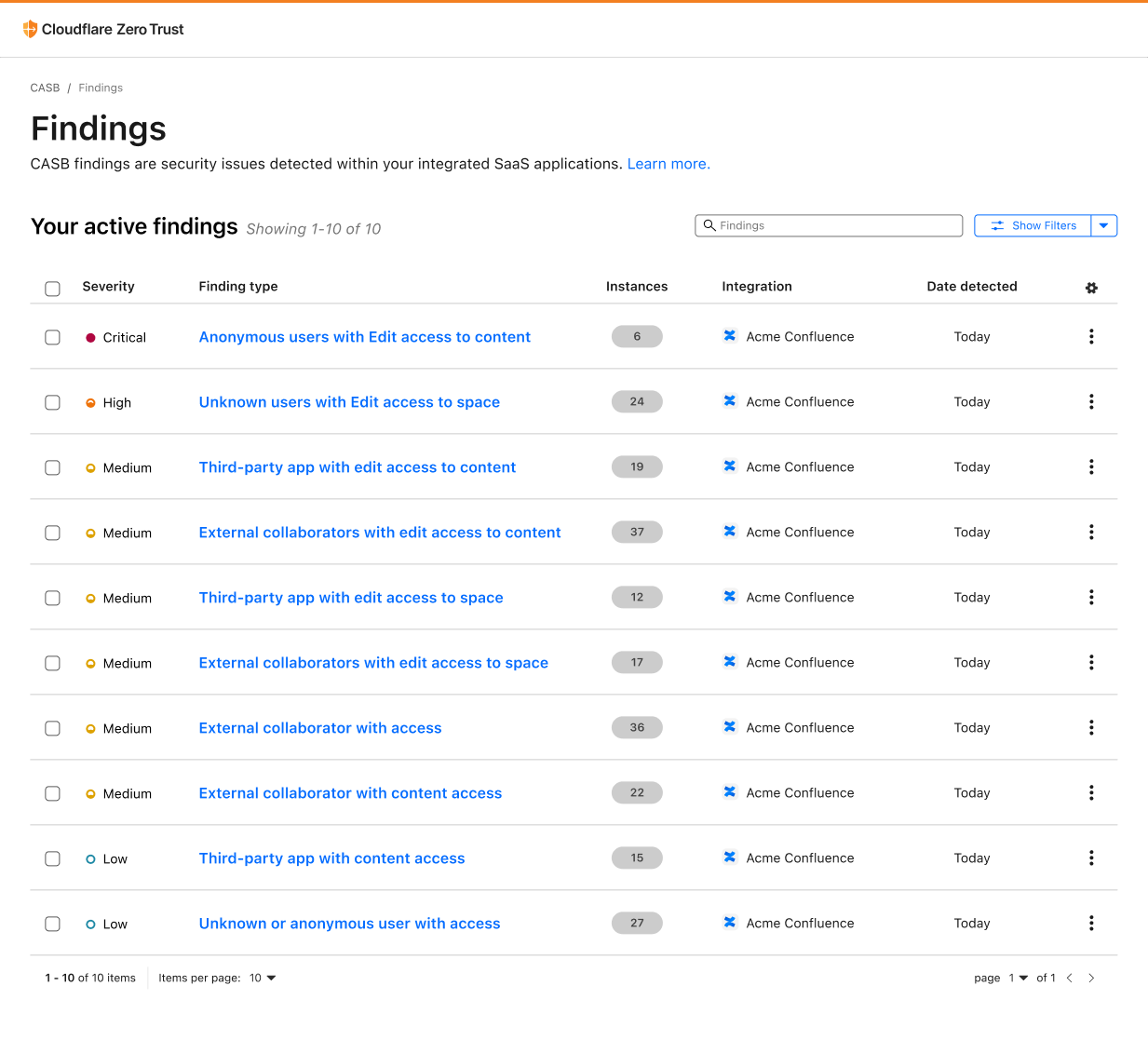
Over time, Atlassian Confluence has become the go-to collaboration platform for teams to create, organize, and share content, such as documents, notes, and meeting minutes. However, from a security perspective, Confluence's flexibility and wide Continue reading
Zero Trust security with Ping Identity and Cloudflare Access
In today's digital landscape, traditional perimeter based security models are no longer enough to protect sensitive data and applications. As cyber threats become increasingly sophisticated, it's essential to adopt a security approach that assumes that all access is unauthorized, rather than relying on network perimeter-based security.
Zero Trust is a security model that requires all users and devices to be authenticated and authorized before being granted access to applications and data. This approach offers a comprehensive security solution that is particularly effective in today's distributed and cloud-based environments. In this context, Cloudflare Access and Ping Identity offer a powerful solution for organizations looking to implement Zero Trust security controls to protect their applications and data.
Enforcing strong authentication and access controls
Web applications provide businesses with enhanced scalability, flexibility, and cost savings, but they can also create vulnerabilities that malicious actors can exploit. Ping Identity and Cloudflare Access can be used together to secure applications by enforcing strong authentication and access controls.
One of the key features of Ping Identity is its ability to provide single sign-on (SSO) capabilities, allowing users to log in once and be granted access to all applications they are authorized to use. This feature streamlines Continue reading
No hassle migration from Zscaler to Cloudflare One with The Descaler Program

This post is also available in 简体中文, 日本語, Deutsch Français and Español.

Today, Cloudflare is excited to launch the Descaler Program, a frictionless path to migrate existing Zscaler customers to Cloudflare One. With this announcement, Cloudflare is making it even easier for enterprise customers to make the switch to a faster, simpler, and more agile foundation for security and network transformation.
Zscaler customers are increasingly telling us that they’re unhappy with the way in which they have to manage multiple solutions to achieve their goals and with the commercial terms they are being offered. Cloudflare One offers a larger network, a ‘single stack’ solution with no service chaining that enables innovation at an incredible rate, meaning lots of new product and feature releases.
At its core, the Descaler Program helps derisk change. It’s designed to be simple and straightforward, with technical resources to ensure a smooth transition and strategic consultation to ensure the migration achieves your organization's goals. Customers can expect to be up and running on Cloudflare One in a matter of weeks without disruption to their business operations.
What makes up the Descaler Program?
Knowledgeable people. Clear process. Like-magic technology. Getting the people, process, and Continue reading
Leaf-and-Spine Fabrics Between Theory and Reality
I’m always envious of how easy networking challenges seem when you’re solving them in PowerPoint, for example, when an innovation specialist explains how scalability works in leaf-and-spine fabrics in a LinkedIn comment:
One of the main benefits of a CLOS folded spine topology is the scale out spine where you can scale out the number of spine nodes increasing your leaf-spine n-way ECMP as well as minimizing the blast radius with the more spine nodes the more redundancy and resiliency.
Isn’t that wonderful? If you need more bandwidth, sprinkle the magic spine powder on your fabric, add water, and voila! Problem solved. Also, it looks like adding spine switches reduces the blast radius. Who would have known?
Leaf-and-Spine Fabrics Between Theory and Reality
I’m always envious of how easy networking challenges seem when you’re solving them in PowerPoint, for example, when an innovation specialist explains how scalability works in leaf-and-spine fabrics in a LinkedIn comment:
One of the main benefits of a CLOS folded spine topology is the scale out spine where you can scale out the number of spine nodes increasing your leaf-spine n-way ECMP as well as minimizing the blast radius with the more spine nodes the more redundancy and resiliency.
Isn’t that wonderful? If you need more bandwidth, sprinkle the magic spine powder on your fabric, add water, and voila! Problem solved. Also, it looks like adding spine switches reduces the blast radius. Who would have known?
Securing the NSX management plane against exploits
Helping organizations protect their assets and infrastructure from evolving attack tactics and techniques is a priority at VMware. API-focused ransomware attacks have become an all-too-common trend, and we recommend that customers take extra care to reduce their attack surface by deploying NSX Manager — and any other manager console — in a hardened manner.
Management infrastructure and common services typically allow broad access to other potentially more valuable resources within an organization, which in turn provides malicious actors with convenient platforms from which they can launch more damaging attacks. To manage that risk, VMware recommends the following steps to protect your management networks and services deployed within those networks:
- Do not expose NSX Manager to the internet: Like any other management console, NSX Manager should be installed within your internal network and accessed remotely only through a secure VPN connection.
- Use strong authentication methods: Ensure that strong authentication methods, such as multi-factor authentication, are used for all NSX Manager logins.
- Use secure communication protocols: Use secure communication protocols, such as SSL/TLS, to protect the communication between NSX Manager and other components in the environment.
- Implement network segmentation: Segment the network to limit the Continue reading
Submarine Cable Resilience
How do you protect a submarine cable from interference? Do you use more amour plating? Or laying the cable in a sea floor trench? Or simply lay more cables? Or do you head off into radio-based systems?You’re Responsible for the User Experience—No Matter Which Networks It’s Delivered Over
The following post is by Jeremy Rossbach, Chief Technical Evangelist at Broadcom. We thank Broadcom for being a sponsor. Hybrid work and the ongoing transformations ushered in by SD-WAN, cloud, SaaS, and SASE have created an entirely new network landscape for today’s network operations (NetOps) teams to manage and monitor. Now, the user experience is […]
The post You’re Responsible for the User Experience—No Matter Which Networks It’s Delivered Over appeared first on Packet Pushers.
Tech Bytes: Automating Network Administration At Scale With BackBox (Sponsored)
Today's Tech Bytes podcast gets into network automation with sponsor BackBox. BackBox’s approach to automation is to focus on network engineers and integrate automation with how they already do their jobs. BackBox works with more than 180 network and security vendors.
The post Tech Bytes: Automating Network Administration At Scale With BackBox (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Automating Network Administration At Scale With BackBox (Sponsored)
Today's Tech Bytes podcast gets into network automation with sponsor BackBox. BackBox’s approach to automation is to focus on network engineers and integrate automation with how they already do their jobs. BackBox works with more than 180 network and security vendors.Geopolitics and Climate Change Heighten Undersea Cable Concerns
Global political unrest and climate change are bringing new attention to the fragility of the undersea cable networks that carry about 95% of international digital traffic.Network Break 421: Huawei Is Both In And Out Of German Networks; Hot-Desking Rubs Hybrid Workers Wrong
Take a Network Break! On today's episode we discuss a record quarter for switch sales, examine Germany's mixed signals about allowing Huawei gear in its networks, and debate whether employees' frustration over Google's desk-sharing plan is just entitled whining or a legitimate complaint. Plus more IT news.
The post Network Break 421: Huawei Is Both In And Out Of German Networks; Hot-Desking Rubs Hybrid Workers Wrong appeared first on Packet Pushers.
Network Break 421: Huawei Is Both In And Out Of German Networks; Hot-Desking Rubs Hybrid Workers Wrong
Take a Network Break! On today's episode we discuss a record quarter for switch sales, examine Germany's mixed signals about allowing Huawei gear in its networks, and debate whether employees' frustration over Google's desk-sharing plan is just entitled whining or a legitimate complaint. Plus more IT news.Top 50 most impersonated brands in phishing attacks and new tools you can use to protect your employees from them


Someone in your organization may have just submitted an administrator username and password for an internal system to the wrong website. And just like that, an attacker is now able to exfiltrate sensitive data.
How did it all happen? A well crafted email.
Detecting, blocking, and mitigating the risks of phishing attacks is arguably one of the hardest challenges any security team is constantly facing.
Starting today, we are opening beta access to our new brand and anti-phishing tools directly from our Security Center dashboard, allowing you to catch and mitigate phishing campaigns targeting your organization even before they happen.
The challenge of phishing attacks
Perhaps the most publicized threat vector over the past several months has been phishing attacks. These attacks are highly sophisticated, difficult to detect, becoming more frequent, and can have devastating consequences for businesses that fall victim to them.
One of the biggest challenges in preventing phishing attacks is the sheer volume and the difficulty of distinguishing legitimate emails and websites from fraudulent ones. Even when users are vigilant, it can be hard to spot the subtle differences that attackers use to make their phishing emails and websites look convincing.
For example, last July our Cloudflare Continue reading
Locking down your JavaScript: positive blocking with Page Shield policies


Web development teams are tasked with delivering feature-rich applications at lightning speeds. To help them, there are thousands of pre-built JavaScript libraries that they can integrate with little effort.
Not always, however, are these libraries backed with hardened security measures to ensure the code they provide is not tampered with by malicious actors. This ultimately leads to an increased risk of an application being compromised.
Starting today, tackling the risk of external JavaScript libraries just got easier. We are adding a new feature to our client side security solution: Page Shield policies. Using policies you can now ensure only allowed and vetted libraries are executed by your application by simply reviewing a checklist.
Client side libraries
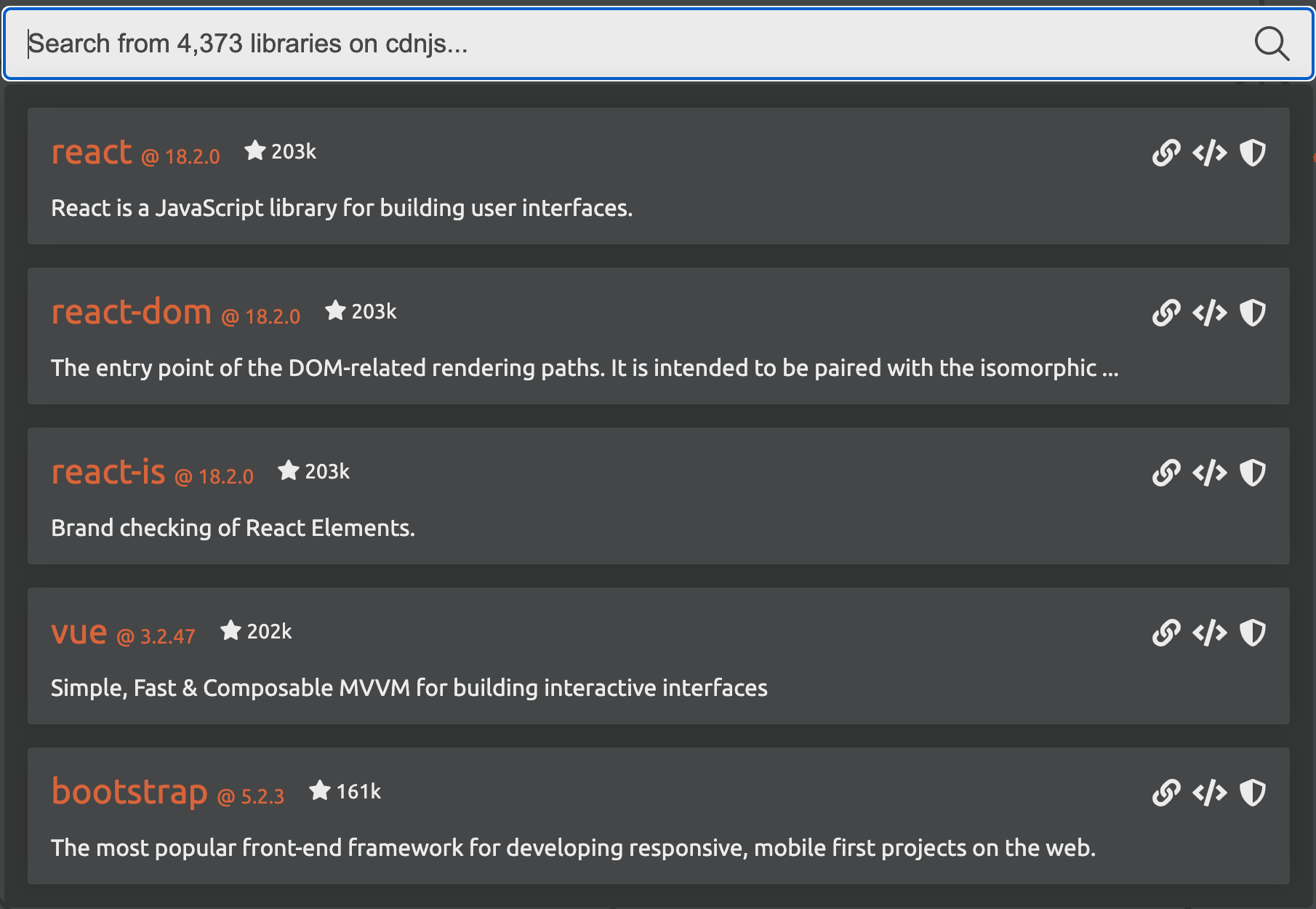
There are more than 4,373 libraries available on cdnjs, a popular JavaScript repository, at the time of writing. These libraries provide access to pre-built functionality to build web applications. The screenshot below shows the most popular on the platform such as React, Vue.js and Bootstrap. Bootstrap alone, according to W3Techs, is used on more than 20% of all websites.
In addition to library repositories like cdnjs, there are thousands of plugins provided directly by SaaS platforms including from names such as Continue reading