Day Two Cloud 185: Grappling With Cloud Strategies With Tim Banks
Today on Day Two Cloud we engage in strategic thinking about cloud, workload repatriation, costs and spending, DevOps and Kubernetes, and more with guest Tim Banks. Tim is a Lead Developer Advocate at Dell Technologies and has done stints at AWS, Equinix, and the Duckbill Group. Besides being a techie, Tim Banks is also a Brazilian Jiu Jitsu champion and world-ranked competitor in his class.
The post Day Two Cloud 185: Grappling With Cloud Strategies With Tim Banks appeared first on Packet Pushers.
Day Two Cloud 185: Grappling With Cloud Strategies With Tim Banks
Today on Day Two Cloud we engage in strategic thinking about cloud, workload repatriation, costs and spending, DevOps and Kubernetes, and more with guest Tim Banks. Tim is a Lead Developer Advocate at Dell Technologies and has done stints at AWS, Equinix, and the Duckbill Group. Besides being a techie, Tim Banks is also a Brazilian Jiu Jitsu champion and world-ranked competitor in his class.Enabling SD-WAN and SASE – An Ideal Edge Computing Use Case
Standardized SD-WAN and SASE have emerged as crucial use cases for edge computing as they allow the provisioning of computing resources and connectivity needed to improve application performance, minimize latency, and enhance the user experience.HS0042 Is ChatGPT Coming For Your Job
Short answer is yes. Long answer is long. CHatGPT is useful for demonstrating potential and getting more funding for AI. In terms of potential for real work, well, its not good enough.
The post HS0042 Is ChatGPT Coming For Your Job appeared first on Packet Pushers.
HS042 Is ChatGPT Coming For Your Job
Short answer is yes. Long answer is long. CHatGPT is useful for demonstrating potential and getting more funding for AI. In terms of potential for real work, well, its not good enough.Embrace equity on International Women’s Day (and every day)

This post is also available in 简体中文, 日本語, 한국어, Deutsch, Français, Español and 繁體中文.

Happy International Women’s Day! The global theme for 2023 is #EmbraceEquity, which is part of an ongoing effort to raise awareness around “Why equal opportunities are no longer enough.” Today is a time to highlight achievements made by women, but also an opportunity to become better informed, and collaborate and brainstorm about the path forward.
“People start from different places, so true inclusion and belonging require equitable action.” — internationalwomensday.com
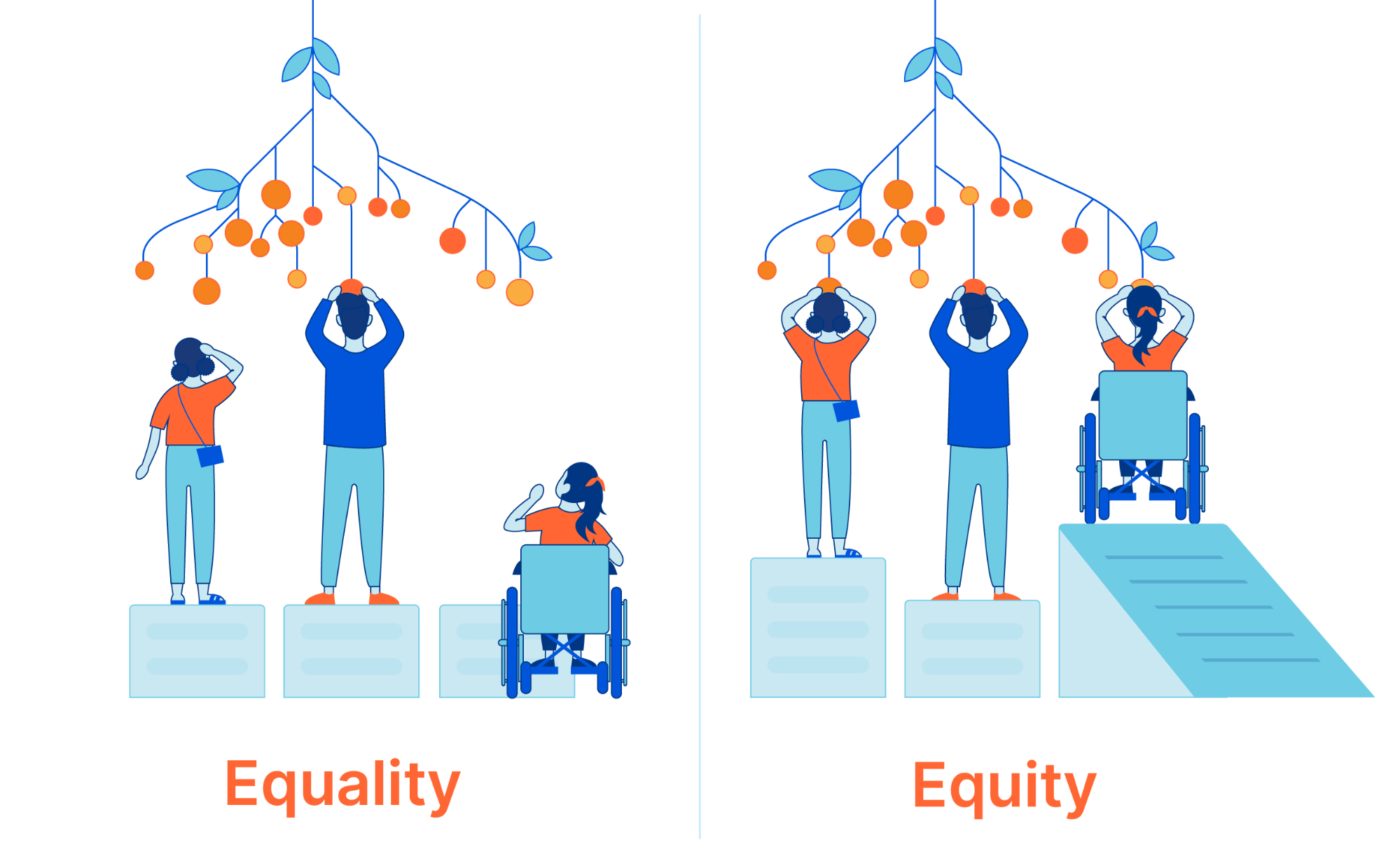
Help put an end to gender bias and discrimination
Consider taking a few minutes today to learn about pervasive challenges affecting women, including in the workplace. Since unconscious bias is a major driver of hurdles holding women back, it is beneficial for people of all gender identities to educate ourselves about the varied experiences of others.
Here are some resources to get help get you started:
- Recognize the difference between equity and equality and see why striving for equality can interfere with inclusion-related efforts.
- Read highlights from the Women in the Workplace report from McKinsey and LeanIn.Org to examine factors that are holding women back from Continue reading
Accelerate building resiliency into systems with Cloudflare Workers


In this blog post we’ll discuss how Cloudflare Workers enabled us to quickly improve the resiliency of a legacy system. In particular, we’ll discuss how we prevented the email notification systems within Cloudflare from outages caused by external vendors.
Email notification services
At Cloudflare, we send email notifications to customers such as billing invoices, password resets, OTP logins and certificate status updates. We rely on external Email Service Providers (ESPs) to deliver these emails to customers.
The following diagram shows how the system looks. Multiple services in our control plane dispatch emails through an external email vendor. They use HTTP Transmission APIs and also SMTP to send messages to the vendor. If dispatching an email fails, they are retried with exponential back-off mechanisms. Even when our ESP has outages, the retry mechanisms in place guarantee that we don’t lose any messages.

Why did we need to improve resilience?
In some cases, it isn’t sufficient to just deliver the email to the customer; it must be delivered on time. For example, OTP login emails are extremely time sensitive; their validity is short-lived such that a delay in sending them is as bad as not sending them at all. If the ESP Continue reading
New: Anycast Resource Page
I wrote two dozen blog posts describing IP anycast concepts, from first-hop anycast gateways to anycast between DNS servers and global anycast (as used by large web properties), but never organized them in any usable form.
That’s fixed: everything I ever wrote about anycast is nicely structured on the new Anycast Resources page.
New: Anycast Resource Page
I wrote two dozen blog posts describing IP anycast concepts, from first-hop anycast gateways to anycast between DNS servers and global anycast (as used by large web properties), but never organized them in any usable form.
That’s fixed: everything I ever wrote about anycast is nicely structured on the new Anycast Resources page.
Kubernetes secrets management: 3 approaches and 9 best practices
Secrets, such as usernames, passwords, API tokens, and TLS certificates, contain confidential data that can be used to authenticate and authorize users, groups, or entities. As the name implies, secrets are not meant to be known or seen by others. So how do we keep them safe?
The key to keeping secrets safe lies within how you manage them. Where to store secrets, how to retrieve them, and how to make them available in an application as needed are all early design choices a developer must make when migrating an application or microservice to Kubernetes. Part of this design choice is to ensure the secrets can become available without compromising the application’s security posture.
In this article, I will provide approaches and recommended best practices for managing secrets in Kubernetes.
How to approach secrets management in Kubernetes
Let’s start with some approaches. Below are three approaches I recommend for Kubernetes secrets management.
etcd
etcd is a supported datastore in Kubernetes, and a lot of developers opt to store secrets in a Base64-encoded format in etcd as a key-value pair. Secrets stored in etcd can be made available from within Kubernetes deployment specs as an environment variable, which is stored in Continue reading
Friction as a Network Security Concept

I had the recent opportunity to record a podcast with Curtis Preston about security, data protection, and networking. I loved being a guest and we talked about quite a bit in the episode about how networking operates and how to address ransomware issues when they arise. I wanted to talk a bit more about some concepts here to help flesh out my advice as we talked about it.
Compromise is Inevitable
If there’s one thing I could say that would make everything make sense it’s this: you will be compromised. It’s not a question of if. You will have your data stolen or encrypted at some point. The question is really more about how much gets taken or how effectively attackers are able to penetrate your defenses before they get caught.
Defenses are designed to keep people out. But they also need to be designed to contain damage. Think about a ship on the ocean. Those giant bulkheads aren’t just there for looks. They’re designed to act as compartments to seal off areas in case of catastrophic damage. The ship doesn’t assume that it’s never going to have a leak. Instead, the designers created it in such a way as Continue reading
New Zero Trust navigation coming soon (and we need your feedback)

We’re updating the Zero Trust navigation

On March 20, 2023, we will be launching an updated navigation in the Zero Trust dashboard, offering all of our Zero Trust users a more seamless experience across Cloudflare as a whole. This change will allow you to more easily manage your Zero Trust organization alongside your application and network services, developer tools, and more.
As part of this upcoming release, you will see three key changes:
Quicker navigation
Instead of opening another window or typing in a URL, you can go back to the Cloudflare dashboard in one click.

Switch accounts with ease
View and switch accounts at the top of your sidebar.

Resources and support
Find helpful links to our Community, developer documentation, and support team at the top of your navigation bar.

Why we’re updating the Zero Trust navigation
In 2020, Gateway was broadly released as the first Cloudflare product that didn’t require a site hosted on Cloudflare’s infrastructure. In other words, Gateway was unconstrained by the site-specific model most other Cloudflare products relied on at the time, while also used in close conjunction with Access. And so, the Cloudflare for Teams dashboard was built on a new model, designed from Continue reading
The White House’s National Cybersecurity Strategy asks the private sector to step up to fight cyber attacks. Cloudflare is ready

On Thursday, March 2, 2023, the Biden-Harris Administration released the National Cybersecurity Strategy aimed at securing the Internet. Cloudflare welcomes the Strategy, and congratulates the White House on this comprehensive, much-needed policy initiative. The goal of the Strategy is to make the digital ecosystem defensible, resistant, and values-aligned. This is a goal that Cloudflare fully supports. The Strategy recognizes the vital role that the private sector has to play in defending the United States against cyber attacks.
The Strategy aims to make a fundamental shift and transformation of roles, responsibilities, and resources in cyberspace by (1) rebalancing the responsibility to defend cyberspace by shifting the burden away from individuals, small businesses, and local governments, and onto organizations that are most capable and best-positioned to reduce risks, like data holders and technology providers; and (2) realigning incentives to favor long-term investments by balancing defending the United States against urgent threats today and simultaneously investing in a resilient future. The Strategy envisions attaining these goals through five collaborative pillars:
- Pillar One: defending critical infrastructure;
- Pillar Two: disrupting and dismantling threat actors;
- Pillar Three: shaping market forces to drive security and resilience;
- Pillar Four: investing in a resilient future; and
- Pillar Five: forging Continue reading
Tackling the Volume Challenge, Computational Storage Sets Up for Mainstream Adoption
Computational storage embeds processors in a drive to offload the server CPU from burdensome tasks such as compression and encryption.Keeping the Cloudflare API ‘all green’ using Python-based testing


At Cloudflare, we reuse existing core systems to power multiple products and testing of these core systems is essential. In particular, we require being able to have a wide and thorough visibility of our live APIs’ behaviors. We want to be able to detect regressions, prevent incidents and maintain healthy APIs. That is why we built Scout.
Scout is an automated system periodically running Python tests verifying the end to end behavior of our APIs. Scout allows us to evaluate APIs in production-like environments and thus ensures we can green light a production deployment while also monitoring the behavior of APIs in production.
Why Scout?
Before Scout, we were using an automated test system leveraging the Robot Framework. This older system was limiting our testing capabilities. In fact, we could not easily match json responses against keys we were looking for. We would abandon covering different behaviors of our APIs as it was impossible to decide on which resources a given test suite would run. Two different test suites would create false negatives as they were running on the same account.
Regarding schema validation, only API responses were validated against a json schema and tests would not fail if the Continue reading