We Is Us — OPNFV & ETSI Accelerate NFV Adoption
 A look at the role each group is playing in the evolution of NFV.
A look at the role each group is playing in the evolution of NFV.
Convergence & Standards in IT Infrastructure
In this "nominal 15 minute analysis" I"m looking at technology convergence and how it needs standards for the market to operate.
The post Convergence & Standards in IT Infrastructure appeared first on EtherealMind.
Worth Reading 06:12
According to the Data Center Journal:
What’s the problem with IT resumes? They’re useless.
The real problem with IT resumes, though, is we want to see a long list of technologies, because we want to find the specific technology we want to implement (or are implementing) — rather than a good engineer. The hiring process is a fishing expedition rather than a search for solid talent and personality fit. If we want to fix this problem we can. The question is — do we want to?
Bruce Schneier has some wise thoughts on airport security this week —
We don’t need perfect airport security. We just need security that’s good enough to dissuade someone from building a plot around evading it. If you’re caught with a gun or a bomb, the TSA will detain you and call the FBI. Under those circumstances, even a medium chance of getting caught is enough to dissuade a sane terrorist
Replace “airport” with “network,” and you get the drift of where network security is going, I think. Of course, there’s the reality that you can’t stop insane attackers… Worth remembering. The same point can be made for network uptime, by the way. Perfection is Continue reading
The IOS XR CLI
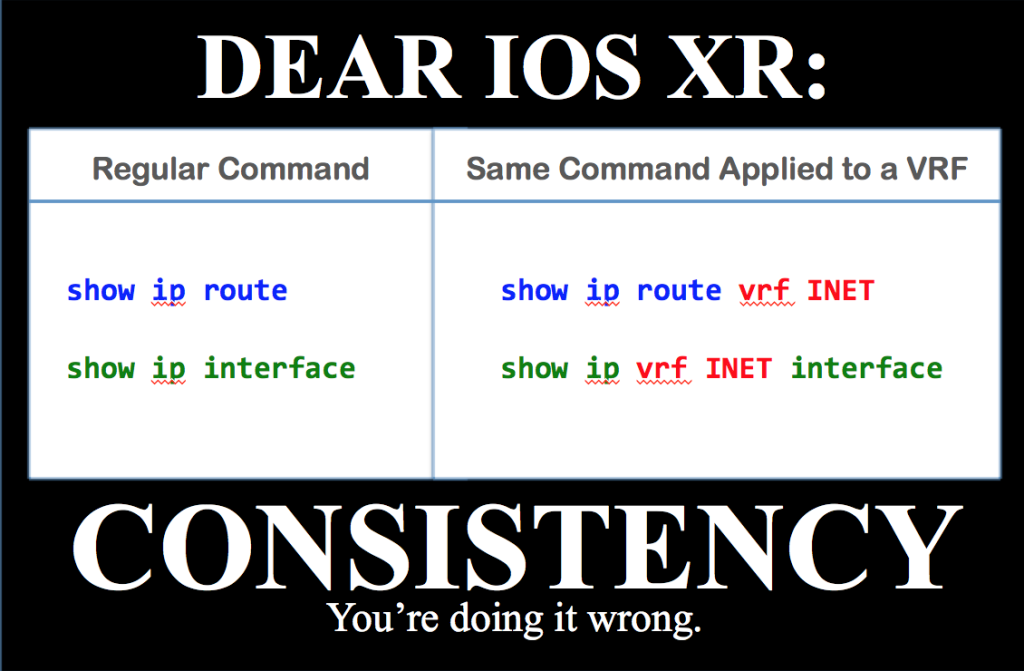
If you liked this post, please do click through to the source at The IOS XR CLI and give me a share/like. Thank you!
Massive route leak causes Internet slowdown
Earlier today a massive route leak initiated by Telekom Malaysia (AS4788) caused significant network problems for the global routing system. Primarily affected was Level3 (AS3549 – formerly known as Global Crossing) and their customers. Below are some of the details as we know them now.
Starting at 08:43 UTC today June 12th, AS4788 Telekom Malaysia started to announce about 179,000 of prefixes to Level3 (AS3549, the Global crossing AS), whom in turn accepted these and propagated them to their peers and customers. Since Telekom Malaysia had inserted itself between these thousands of prefixes and Level3 it was now responsible for delivering these packets to the intended destinations.
This event resulted in significant packet loss and Internet slow down in all parts of the world. The Level3 network in particular suffered from severe service degradation between the Asia pacific region and the rest of their network. The graph below for example shows the packet loss as measured by OpenDNS between London over Level3 and Hong Kong. The same loss patterns were visible from other Level3 locations globally to for example Singapore, Hong Kong and Sydney.
At the same time the round trip time between these Continue reading
SDN SOFTWARE DEFINED NETWORKS: AN OVERVIEW
How does Internet work - We know what is networking
Flowing text is a project done as a part of academic work that I am involved with for last few years at the University of Rijeka – Department of Informatics. It’s a short overview at latest achievements in the field of network automation with some lab experiments done to test different paths across the network. The work was presented at 6th International Conference on Information Technologies and Information Society (ITIS2014). The scope of ITIS events are the applications of IT, particularly in social sciences. The conference also covers a wider range of topics related to IT and computational modeling and
29 – Interconnecting dual-Fabric: Full-Mesh or Partial-Mesh
This post discusses about design considerations when interconnecting two tightly coupled fabrics using dark fibers or DWDM, but not limited to Metro distances. If we think very long distances, the point-to-point links can be also established using a virtual overlay such as EoMPLS port x-connect; nonetheless the debate will be the same.
Notice that this discussion is not limited to one type of network fabric transport, but any solutions that use multi-pathing is concerned, such as FabricPath, VxLAN or ACI.
Assuming the distance between DC-1 and DC-2 is about 100 km; if the following two design options sound quite simple to guess which one might be the most efficient, actually it’s not as obvious as we could think of, and a bad choice may have a huge impact for some applications. I met several networkers discussing about the best choice between full-mesh and partial-mesh for interconnecting 2 fabrics. Some folks think that full-mesh is the best solution. Actually, albeit it depends on the distances between network fabrics, this is certainly not the most efficient design option for interconnecting them together.
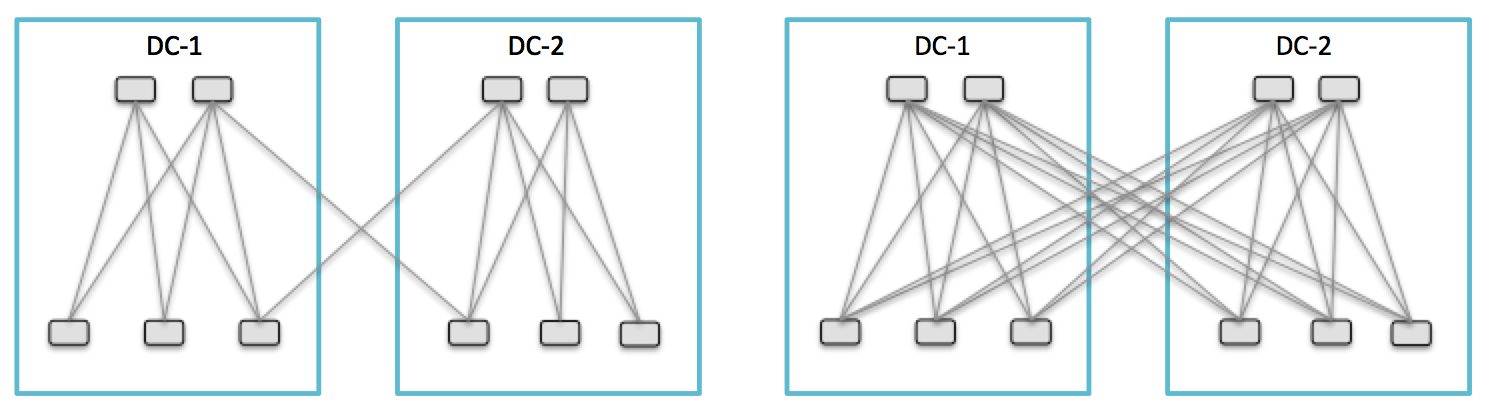
Partial-Mesh with transit leafs design (left) Continue reading
NAPALM: Integrating Ansible with Network Devices on Software Gone Wild
What happens when network engineers with strong programming background and focus on open source tools have to implement network automation in a multi-vendor network? Instead of complaining or ranting about the stupidities of traditional networking vendors and CLI they write an abstraction layer that allows them to treat all their devices in the same way and immediately open-source it.
Read more ...Apple and IPv6
It’s Apple’s Developers Conference time again, and in amongst the various announcements was week, in the “Platforms Status of the Union” presentation, was the mention of some recent IPv6 developments by Apple. As far as supporting IPv6 is concerned Apple still appear to get it. But do they really get all of it?Musing: Does Oracle Prove that OpEx Beats CapEx in the Enterprise ?
Oracle has a tough quarter with its top line business shrinking quickly as developers choose open source databases instead. – Source: Bloomberg At a business level, there is definitely a trend by corporates to “avoid” Oracle as licensing fees have increased dramatically to reach a pain threshold that CIOs cannot ignore. While the choice for […]
The post Musing: Does Oracle Prove that OpEx Beats CapEx in the Enterprise ? appeared first on EtherealMind.
