Multicasting Content in the Twilight of Social Media

During Cisco Live EMEA last week I had an interesting conversation with a few people at the show around social media and how the usage of the platforms appears to be changing thanks to decisions made by the smartest people in a given broom closet. With the acceleration of the demise of Twitter as a platform I couldn’t help but comment on the fact that social media is becoming less about conversation and more about broadcast, which seemed to catch some of the people in the conversation off guard.
Back and Forth
Ever since the beginning of my time on Twitter, I’ve seen the platform as conversational instead of content-focused. Perhaps that’s the reason why the idea of a tweet storm has irritated me so much over the past few years. Twitter is about talking to people. It’s about interacting with them and creating a conversation in the noise. Twitter allows us to connect to people and exchange ideas and viewpoints.
Contrast that with other platforms in the social media spectrum. Specifically I’m thinking of Youtube video or TikTok videos. These platforms are designed to create content and send it to a number of people to view. It’s multicasting content Continue reading
Building a SQL-like language to filter flows
Akvorado collects network flows using IPFIX or sFlow. It stores them in a ClickHouse database. A web console allows a user to query the data and plot some graphs. A nice aspect of this console is how we can filter flows with a SQL-like language:
Often, web interfaces expose a query builder to build such filters. I think combining a SQL-like language with an editor supporting completion, syntax highlighting, and linting is a better approach.1
The language parser is built with pigeon (Go) from a parsing expression grammar—or PEG. The editor component is CodeMirror (TypeScript).
Language parser
PEG grammars are relatively recent2 and are an alternative to context-free grammars. They are easier to write and they can generate better error messages. Python switched from an LL(1)-based parser to a PEG-based parser in Python 3.9.
pigeon generates a parser for Go. A grammar is a set of rules. Each rule is
an identifier, with an optional user-friendly label for error messages, an
expression, and an action in Go to be executed on match. You can find the
complete grammar in parser.peg. Here is Continue reading
Start Large netlab Topologies in Smaller Batches
It’s incredible how little CPU resources some network devices consume in a steady state – a netlab user managed to run almost 100 Mikrotik routers on a 24-core server. Starting them simultaneously (like vagrant up tries to do when used with the vagrant-libvirt plugin) is a different story. The router virtual machines are configured with two CPU cores for a good reason, and if they don’t get enough CPU cycles during the boot time, they get sluggish, Vagrant gives up, and the lab start procedure fails.
One could use a nasty workaround:
Start Large netlab Topologies in Smaller Batches
It’s incredible how little CPU resources some network devices consume in a steady state – a netlab user managed to run almost 100 Mikrotik routers on a 24-core server. Starting them simultaneously (like vagrant up tries to do when used with the vagrant-libvirt plugin) is a different story. The router virtual machines are configured with two CPU cores for a good reason, and if they don’t get enough CPU cycles during the boot time, they get sluggish, Vagrant gives up, and the lab start procedure fails.
One could use a nasty workaround:
DDoS Protection 1. Collecting and Visualizing NetFlow Data from Nokia SR OS using FastNetMon (FNM).
Dear friend,
It wouldn’t be an overestimation to say that in the modern world the availability of service online plays one of the key role for success of any business: we buy, sell and use goods and services via Internet from various private and public companies as well as governmental bodies. As such, if services are not unavailable online, we, as consumers, cannot get what we need and suppliers cannot provide use the service (and, therefore, cannot make some money). That’s why the information security in general, and protection of service online becomes the hot topic these days.
Can Network Security Be Automated?
Absolutely it can be. Ensuring that configuration of network devices and online services are in-line with the security hardening blueprints is one of the most straightforward automation use cases, which provides significant value by ensuring that the amount of attack vectors is reduced and is limited to the set of services, which are really needed. Besides that, we have the whole range of vulnerability scanning, software upgrade, etc.
And for all these, and other network security automation activities, we are using the same set of tools as for “ordinary network automation”. Therefore, come and learn with us:
Review: Compulab Fitlet2

A while ago, in June 2021, we were discussing home routers that can keep up with 1G+ internet connections in the CommunityRack telegram channel. Of course at IPng Networks we are fond of the Supermicro Xeon D1518 [ref], which has a bunch of 10Gbit X522 and 1Gbit i350 and i210 intel NICs, but it does come at a certain price.
For smaller applications, PC Engines APU6 [ref] is kind of cool and definitely more affordable. But, in this chat, Patrick offered an alternative, the [Fitlet2] which is a small, passively cooled, and expandable IoT-esque machine.
Fast forward 18 months, and Patrick decided to sell off his units, so I bought one off of him, and decided to loadtest it. Considering the pricetag (the unit I will be testing will ship for around $400), and has the ability to use (1G/SFP) fiber optics, it may be a pretty cool one!
Executive Summary
TL/DR: Definitely a cool VPP router, 3x 1Gbit line rate, A- would buy again
With some care on the VPP configuration (notably RX/TX descriptors), this unit can handle L2XC at (almost) line rate in both directions (2.94Mpps out a theoretical 2.97Mpps), Continue reading
Hacking the Geberit Sigma 70 flush plate
My toilet is equipped with a Geberit Sigma 70 flush plate. The sales pitch for this hydraulic-assisted device praises the “ingenious mount that acts like a rocker switch.” In practice, the flush is very capricious and has a very high failure rate. Avoid this type of mechanism! Prefer a fully mechanical version like the Geberit Sigma 20.
After several plumbers, exchanges with Geberit’s technical department, and the expensive replacement of the entire mechanism, I was still getting a failure rate of over 50% for the small flush. I finally managed to decrease this rate to 5% by applying two 8 mm silicone bumpers on the back of the plate. Their locations are indicated by red circles on the picture below:
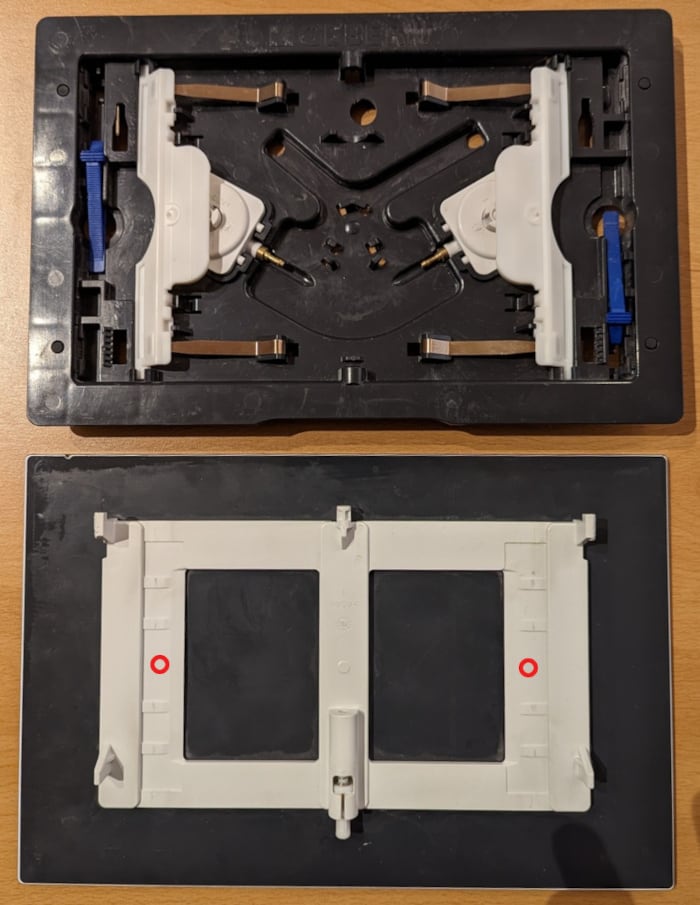
Expect to pay about 5 € and as many minutes for this operation.
Heavy Networking 665: Augtera Network AI Automates NetOps And Works To Prevent Incidents (Sponsored)
The Packet Pushers' Heavy Networking podcast dives into sponsor Augtera and how its AI platform, purpose-built for networking, improves network operations and enables automation. We'll examine how Augtera works, how it aims to move beyond the automation of configurations to automate operations and fault management, the kinds of data it collects and how, and how customers are using Augtera in production networks
The post Heavy Networking 665: Augtera Network AI Automates NetOps And Works To Prevent Incidents (Sponsored) appeared first on Packet Pushers.
Heavy Networking 665: Augtera Network AI Automates NetOps And Works To Prevent Incidents (Sponsored)
The Packet Pushers' Heavy Networking podcast dives into sponsor Augtera and how its AI platform, purpose-built for networking, improves network operations and enables automation. We'll examine how Augtera works, how it aims to move beyond the automation of configurations to automate operations and fault management, the kinds of data it collects and how, and how customers are using Augtera in production networksWhat CISOs Should Understand About the Zero Trust Security Model
The way forward for enterprises in the new era of work is to implement a zero trust security model to enhance the organizational cybersecurity posture.Video: Kubernetes SDN Architecture
Stuart Charlton started the Kubernetes Networking Deep Dive webinar with an overview of basic concepts including the networking model and services. After covering the fundamentals, it was time for The Real Stuff: Container Networking Interface, starting with an overview of Kubernetes SDN architecture.
Video: Kubernetes SDN Architecture
Stuart Charlton started the Kubernetes Networking Deep Dive webinar with an overview of basic concepts including the networking model and services. After covering the fundamentals, it was time for The Real Stuff: Container Networking Interface, starting with an overview of Kubernetes SDN architecture.
Migrating Cisco FabricPath and Classic Ethernet Environments to VXLAN BGP/EVPN over a 400Gb-based Clos Topology, part 1 – the why
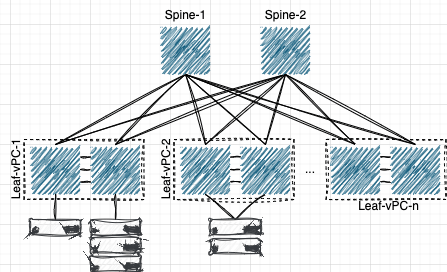
During the past three years, I have spent a good portion of my time testing, planning, designing, and then migrating our DC network from Cisco FabricPath and Classic Ethernet environments to VXLAN BGP/EVPN. And simultaneously, from a hierarchical classic two-tier architecture to a more modern Clos 400Gb-based topology. The migration is not yet 100% completed, but it is well underway. And I have gained significant experience on the subject, so I think it’s time to share my knowledge and experiments with our community. This is my first post on this…
The post Migrating Cisco FabricPath and Classic Ethernet Environments to VXLAN BGP/EVPN over a 400Gb-based Clos Topology, part 1 – the why appeared first on AboutNetworks.net.
Hedge 165: Low Earth Orbit with Dan York

Have you ever wondered about Starlink and similar Low Earth Orbit (LEO) satellite systems? How are they different from geosynchronous satellites? What about the delay of sending traffic through satellites? And the future of satellites? Join Tom Ammon, Dan York, and Russ White as we discuss the ins and outs of satellite technologies.
IPv6 Buzz 119: Operational Issues With IPv6 Neighbor Discovery
In today's IPv6 Buzz podcast we discuss IPv6 Neighbor Discovery and some of the operational issues that can happen when configuring and operating IPv6, and what can help listeners understand and resolve those issues.
The post IPv6 Buzz 119: Operational Issues With IPv6 Neighbor Discovery appeared first on Packet Pushers.
 s launch, and itâ€
s launch, and itâ€