On I-Shaped and T-Shaped Skills
Several of the conversations I had at the recent RIPE70 meeting were focused on career advice (usually along the lines of “which technology should I focus on next”) and inevitably we ended up discussing the benefits of T-shaped skills versus I-shaped skills… and I couldn’t resist drawing a few graphs illustrating them.
Read more ...A New Home: Looking Back
I have moved to a new blogging platform! The timing was interesting, since the wordpress installation on which Keeping It Classless has operated for so long is about 5 years old (I operated on an older domain before Keeping It Classless was born). WOW. Five years is a long time in blog years. I could not have possibly predicted back then what this blog would do for me. In going over these old posts, I saw a very interesting progression of my own skillsets and mentality, and I figured I’d share.A New Home: Looking Back
I have moved to a new blogging platform! The timing was interesting, since the wordpress installation on which Keeping It Classless has operated for so long is about 5 years old (I operated on an older domain before Keeping It Classless was born). WOW. Five years is a long time in blog years. I could not have possibly predicted back then what this blog would do for me. In going over these old posts, I saw a very interesting progression of my own skillsets and mentality, and I figured I’d share.YAMware Old Malware can still be fun!
YAMware Old Malware can still be fun!
(Side note, this blog post was written and then forgotten about quite a while ago, So I’ve finished it off, it was halfway done.)
While on holiday in the evenings with downtime to spare, I had realised that
MPLS VPN’s over mGRE
This blog post outlines what “MPLS VPNs over mGRE” is all about as well as provide an example of such a configuration.
So what is “MPLS VPNs over mGRE”? – Well, basically its taking regular MPLS VPN’s and using it over an IP only core network. Since VPN’s over MPLS is one of the primary drivers for implementing an MPLS network in the first place, using the same functionality over an IP-only core might be very compelling for some not willing/able to run MPLS label switching in the core.
Instead of using labels to switch the traffic from one PE to another, mGRE (Multipoint GRE) is used as the encapsulation technology instead.
Be advised that 1 label is still being used however. This is the VPN label that’s used to identify which VRF interface to switch the traffic to when its received by a PE. This label is, just as in regular MPLS VPN’s, assigned by the PE through MP-BGP.
So how is this actually performed? – Well, lets take a look at an example.
The topology I will be using is as follows:
** Note: I ran into an issue with VIRL, causing Continue reading
Moving Soon!
I would like to take the opportunity to let you all know that Keeping It Classless will be moving to a different blogging platform in the near future. For the vast majority of you, this will not be a problem. My intent is to keep as much as possible consistent between moves.
However, some of you subscribe to my blog using some WordPress-specific features such as email subscription, as well as following me through the WordPress service itself. After the move, these services will have no way of being updated. If this applies to you, please check out the following options:
- I will continue to link to each new blog post to my social media accounts, such as Twitter, Facebook, Google+, and LinkedIn. Follow me at whichever you prefer, and you’ll get all new posts in the relevant news feed.
- I will continue to provide an RSS feed at http://keepingitclassless.net/feed/. Currently this redirects to feedburner, which is likely what you have in your RSS reader, if you’ve already done this. The transition away from WordPress will break this automatic redirection, but don’t worry – feedburner will continue to deliver post updates to you, at least until I Continue reading
Introducing the Citizens of Tech Podcast
Citizens of Tech is not a show about gadgets and apps, at least not specifically. It's not a show about networking. It's not a constipated show about IT. Rather, it's a show for nerds who like science, gaming, books, contrarian thinking, entertainment, space exploration, transportation, energy, complex world problems, and anything else that's somehow technology-related. Sure, that might include gadgets, apps, IT, and so on, but we're trying to appeal to a certain kind of mind -- probably yours -- and not a certain kind of industry.Citizens of Tech 003 – Racing Cricket Phone Turbines
Eric in a mitre. Cricket protein. Micro wind turbines. Stash your cash. Blue crude. RF into power. Wikimedia's money. Carly for POTUS. A racing simulator that can kill you. All this and more on this week's Citizens of Tech.
Author information
The post Citizens of Tech 003 – Racing Cricket Phone Turbines appeared first on Packet Pushers Podcast and was written by Ethan Banks.
Citizens of Tech 003 – Racing Cricket Phone Turbines
Eric in a mitre. Cricket protein. Micro wind turbines. Stash your cash. Blue crude. RF into power. Wikimedia's money. Carly for POTUS. A racing simulator that can kill you. All this and more on this week's Citizens of Tech.
The post Citizens of Tech 003 – Racing Cricket Phone Turbines appeared first on Packet Pushers.
Moving Soon!
I would like to take the opportunity to let you all know that Keeping It Classless will be moving to a different blogging platform in the near future. For the vast majority of you, this will not be a problem. My intent is to keep as much as possible consistent between moves.
However, some of you subscribe to my blog using some WordPress-specific features such as email subscription, as well as following me through the WordPress service itself. After the move, these services will have no way of being updated. If this applies to you, please check out the following options:
I will continue to link to each new blog post to my social media accounts, such as Twitter, Facebook, Google+, and LinkedIn. Follow me at whichever you prefer, and you’ll get all new posts in the relevant news feed. I will continue to provide an RSS feed at http://keepingitclassless.net/feed/. Currently this redirects to feedburner, which is likely what you have in your RSS reader, if you’ve already done this. The transition away from WordPress will break this automatic redirection, but don’t worry – feedburner will continue to deliver post updates to you, at least until I move off Continue reading
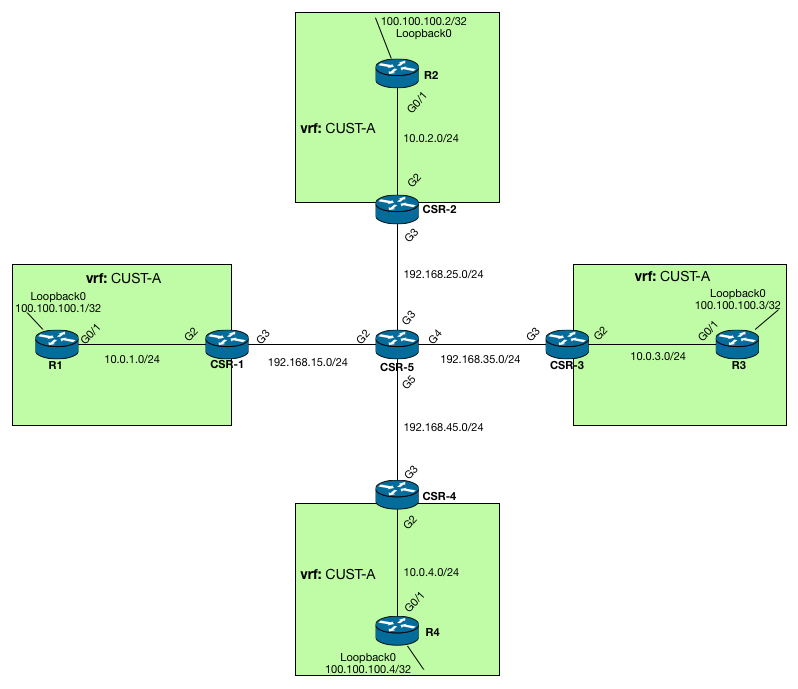
Configuring NAT-NVI on IOU l3
Here is an example of Customer VRFs & Common VRF service + Dynamic NAT NVI in both directions NAT NVI topology on GNS3:HP IMC Adapter Directory Naming
This week’s lesson: Be consistent with your vendor naming when working with HP IMC Custom Device Adapters. When you create the new adapter directory, use exactly the same vendor name as used within the UI. Otherwise IMC may not recognise your new adapter. Case matters too, even on Windows!
HP IMC ships with a set of “Device Adapters” that define functions such as backups, configuration deployment, firmware upgrades, etc. These adapters are sets of XML, TCL and Perl files. They define which devices are supported, for what functions, and how to execute those functions.
Obviously HP can’t support every device ever made. But they’re quite happy for you to write your own adapters, or extend the ones they have. So if you’ve got a few unsupported switches, and they have some sort of sensible interface, you can write your own adapters.
These are stored at /server/conf/adapters/ICC/. Under there, you have a set of folders for each vendor. Under each vendor folder is an adapter-index.xml file, which maps SNMP sysOIDs to adapters. You must have a mapping in the adapter-index.xml file for your sysOID. (nb you can use wildcards). If those XML files change, you need to restart IMC.
SDxCentral Weekly News Roundup — May 15, 2015
 Giddy up, news! It's time for the SDxCentral roundup!
Giddy up, news! It's time for the SDxCentral roundup!