AWS Summit London – Come For The IaaS, Stay For the PaaS
I attended the AWS Summit in London yesterday. Here are some observations in no particular order. Come for the IaaS, Stay for the PaaS. AWS made a strong case about their portfolio of software services such as AWS Lambda, Cloudformation, KMS and Cloudtrail. Its no longer just compute, storage and networking its all about the […]
The post AWS Summit London – Come For The IaaS, Stay For the PaaS appeared first on EtherealMind.
Protection against critical Windows vulnerability (CVE-2015-1635)
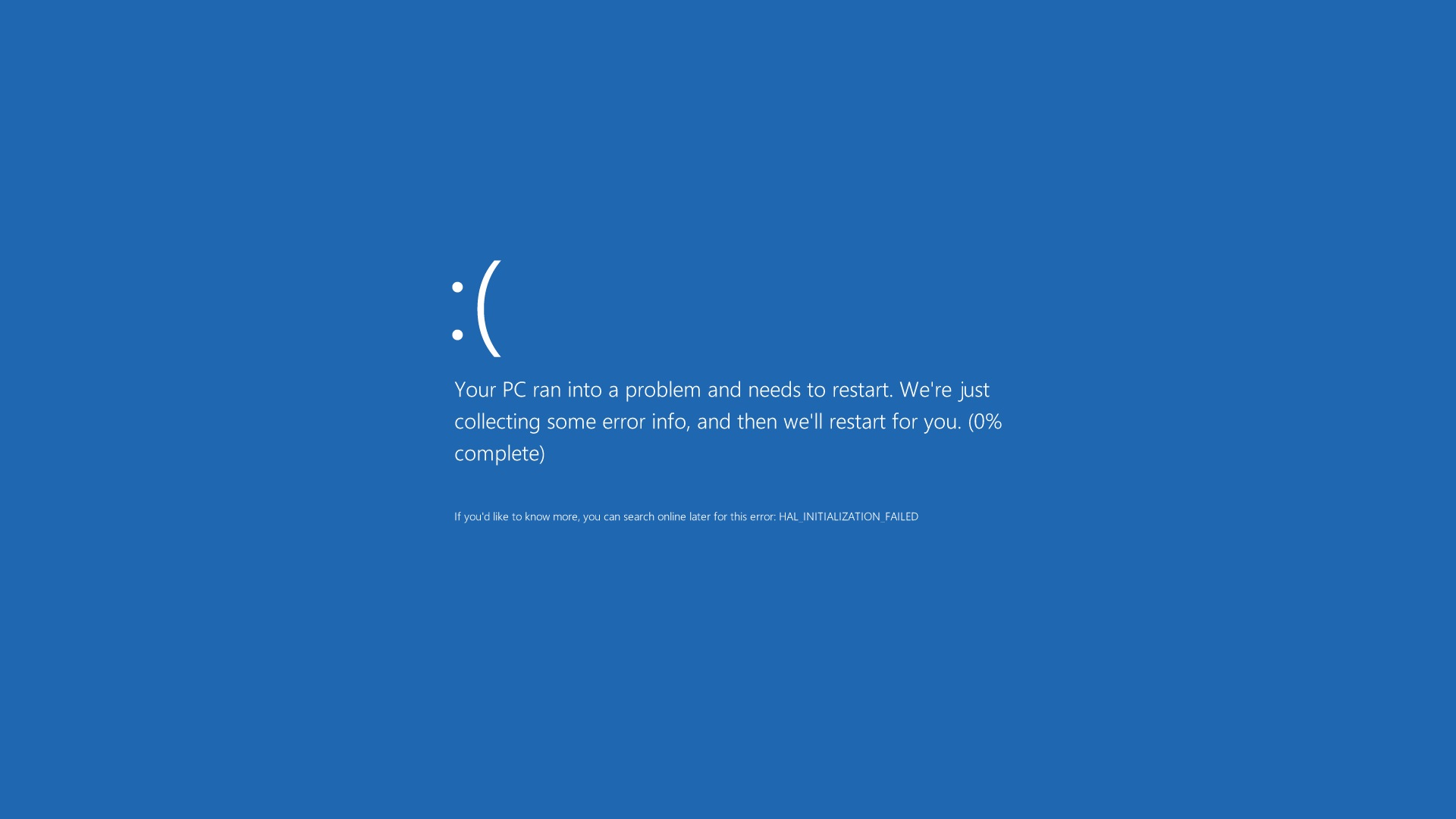
A few hours ago, more details surfaced about the MS15-034 vulnerability. Simple PoC code has been widely published that will hang a Windows web server if sent a request with an HTTP Range header containing large byte offsets.
We have rolled out a WAF rule that blocks these requests.
Customers on a paid plan and who have the WAF enabled are automatically protected against this problem. It is highly recommended that you upgrade your IIS and your Windows servers as soon as possible; in the meantime any requests coming into CloudFlare that try and exploit this DoS/RCE will be blocked.
Nokia to Acquire Alcatel-Lucent for $16.6 Billion
 Well, that was quick. Two days after rumors started, Nokia and Alcatel-Lucent announce a $16.6B hookup.
Well, that was quick. Two days after rumors started, Nokia and Alcatel-Lucent announce a $16.6B hookup.
Handy Link For SCP Commands
Putting this here because I’m constantly forgetting it.
Originally from here: http://www.hypexr.org/linux_scp_help.php
Copy the file “foobar.txt” from a remote host to the local host:
$ scp [email protected]:foobar.txt /some/local/directory
Copy the file “foobar.txt” from the local host to a remote host:
$ scp foobar.txt [email protected]:/some/remote/directory
Design Challenge: Multiple Data Centers Connected with Slow Links
One of my readers sent me this question:
What is best practice to get a copy of the VM image from DC1 to DC2 for DR when you have subrate (155 Mbps in my case) Metro Ethernet services between DC1 and DC2?
The slow link between the data centers effectively rules out any ideas of live VM migration; to figure out what you should be doing, you have to focus on business needs.
Read more ...Route Hijacking of Sensitive Network Traffic Highlights BGP Security Issues
Route Hijacking of Sensitive Network Traffic Highlights BGP Security Issues
by Cengiz Alaettinoglu, CTO - April 15, 2015
Last month web traffic designated for some highly sensitive UK entities – including the nuclear weapons agency that provides and maintains warheads for the Royal Navy – was routed through Ukrainian and Russian telecoms before arriving at its original destination. This route hijacking was the result of a bad route announced by Ukraine's Vega telecom. As Russell Brandom, describing the incident for The Verge, wrote: “It's still likely that the redirection was simply an innocent error, but it underscores the insecure nature of the global routing system.”
I couldn’t agree more and is why I recently wrote an article for Network Computing describing the security vulnerabilities of BGP. In this piece, I outlined the types of BGP incidents (including route hijacking), described several malicious ones perpetrated in recent years, and explained two efforts by the IETF over the years to fix BGP, with limited success. I also discussed how SDN and route analytics can help.
Check out the article and the thoughtful comments from readers as well. As I state at the end of the article, to stop BGP security Continue reading
Nokia-Alcatel Deal Could Push Ericsson Into M&A Mode
 A megamerger could be trouble for Ericsson and even for Juniper.
A megamerger could be trouble for Ericsson and even for Juniper.