Blessay: My New Criteria for Network Design and Architecture
Today you design resilient, redundant networks with what you have. Tomorrow, we need networks that use using software and freedom to be predictable and safe.
The post Blessay: My New Criteria for Network Design and Architecture appeared first on EtherealMind.
What does really MPLS layer 2 VPN mean ?
Couple days before I received an email from one of my readers related with his design. He designed a network infrastructure for his customer and wanted me to take a look as well. But I realized that He has some misunderstanding on the usage of MPLS layer 2 VPNs and I thought just briefly mentioning… Read More »
The post What does really MPLS layer 2 VPN mean ? appeared first on Network Design and Architecture.
Troubleshooting Networks: Tips from a Network Detective
For over 30 years I’ve been in the playing in the “world of IT” and wow has that world changed a great deal in those years. But through all that change, there has been a thread, for me, that has always remained constant.
Troubleshooting!
…. For the rest please go to Packet Pushers
http://packetpushers.net/troubleshooting-networks-tips-from-a-network-detective/
Troubleshooting Networks: Tips from a Network Detective
For over 30 years I’ve been in the playing in the “world of IT” and wow has that world changed a great deal in those years. But through all that change, there has been a thread, for me, that has always remained constant. Troubleshooting! The thrill of the “chase” and the challenge of solving the […]
Author information
The post Troubleshooting Networks: Tips from a Network Detective appeared first on Packet Pushers Podcast and was written by Denise "Fish" Fishburne.
You can’t put the future on hold
Greg Ferro recently participated in an “Ask Me Anything” thread on Reddit. In that thread, user “1DumbQuestion” made this comment:
Last, never finished my CCIE because of what I perceive will happen with SDN in the next coming years.
I’ve seen similar comments from others over the last couple of years. This concerns me because it seems that people are saying “There’s too much change going on here, and I don’t know how it will all work out. So I’ll just do nothing.”
Don’t be one of those people.
You should take a hard look at your career, and try to understand where the industry is going. If you think that CCIE study is not the best use of your time, that’s fine. But you should make a conscious choice about that. Crucially, you must decide where else to invest your time and energy.
If you firmly believe that networking will change dramatically over the next few years, then take active steps to prepare yourself. Think about your current skills, and where you have gaps. Maybe you need to learn more about Linux. Maybe it’s configuration management, or Python scripting. Put your time into Continue reading
CCIE RS study planning, books, notes
Study planning Books, workbooks, videos, software, rack rental tokens, laptop hardware and software have all been purchased; it’s time to get this party started. So, what’s the plan? The urge to dive right into the sexy labs and save the boring planning stuff for later was strong. More than once I had to channel my […]
Author information
The post CCIE RS study planning, books, notes appeared first on Packet Pushers Podcast and was written by quingenerd.
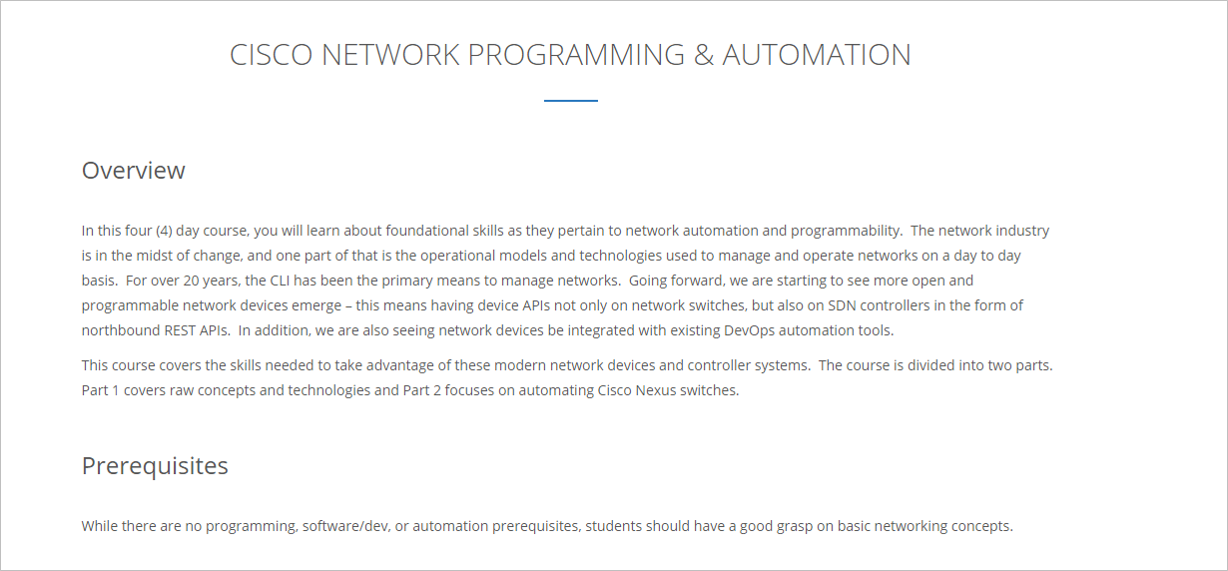
Network Automation Training
If you are a frequent reader of my blog, you know that last year I left my job to do something that I was intrinsically motivated to do. Unfortunately, because of this, I haven’t been able to write as much as I normally would. I do hope that changes. But, time is money now – literally. My time has been spent driving business, negotiating, writing Scopes of Work, building a website, managing finances, and producing quality work for customers, and I hope all of that continues.
Up until this point, I’ve been focused on providing services to end user customers. Today, I’m happy to say that I’ve officially launched the first, of hopefully many, training courses. This one is focused on foundational skills as it pertains to network automation. More detail can be found here.
Training and Education are paramount for technology adoption and hopefully courses like this can play a small part with empowering network engineers to not only expand their skill set, but realize the value that could be had by these skills for their own organizations and employers.
As always, I’m open to comments and feedback below or through the contact page.
Thanks,
Jason
Twitter: @jedelman8
Bacony goodness + math + 3D printing = an inedible endless Bacon Möbius strip
If you take a strip of bacon and twist one end through 180 degrees then join the two ends you get a piece of bacon with only one side, a Bacon Möbius strip. Cool. But if you want such a thing to adorn your desk (and who wouldn't?) then being made of real bacon would be, to say the least, a bad idea. So, to memorialize this mathematical and culinary wonder, why not print a look-alike on a 3D printer? Why not indeed?
This exactly is what a designer with the handle "joabaldwin" created using the Shapeways 3D printing service.
To read this article in full or to leave a comment, please click here
My CLUS 2015 Schedule for San Diego
With roughly two months to go before Cisco Live starts, here is my preliminary schedule for San Diego.
I have two CCDE sessions booked to help me prepare for the CCDE exam. I have the written scheduled on wednesday and we’ll see how that goes.
I have a pretty strong focus on DC because I want to learn more in that area and that should also help me prepare for the CCDE.
I have the Routed Fast Convergence because it’s a good session and Denise Fishburne is an amazing instructor and person.
Are you going? Do you have any sessions in common? Please say hi if we meet in San Diego.
What’s In My Bag (Hint: not much)
Recently @BobMcCouch posted a photo of the contents of his bags. He’s got a lot of gear, including a hammer, and a dent-puller. He assures us that it’s for lifting tiles, but I’m not so sure. Sounds to me like he’s worried about a few dings in the supermarket carpark.
It all sounded a bit scary. I want to provide a different perspective, that of someone who tries to minimise what they carry. I don’t want young engineers to think that they have to build up a huge toolbox, and the physical strength to lug it around. You might choose to do that, but it’s not the only path.
The Bag Itself
My general rules for a laptop bag are that it should be as small as I can get away with, and it should not look too much like a laptop bag. So pretty much anything from Targus is inappropriate.
Today I use the “ Continue reading
Network Break 34 – Fixed
Excerpt: Coffee, virtual doughnuts and networking. A perfect combination.
Author information
The post Network Break 34 – Fixed appeared first on Packet Pushers Podcast and was written by Greg Ferro.