EVPN Configuration
In my last blog I explained the features and use cases of the EVPN technology. In this blog I want to show how easy it is to configure, enable and expand EVPN. The configuration is focused on the Juniper MX platform, but as Junos is the single operating system across the entire Juniper portfolio, configuration on other platforms (like EX9200) is equal.
Design
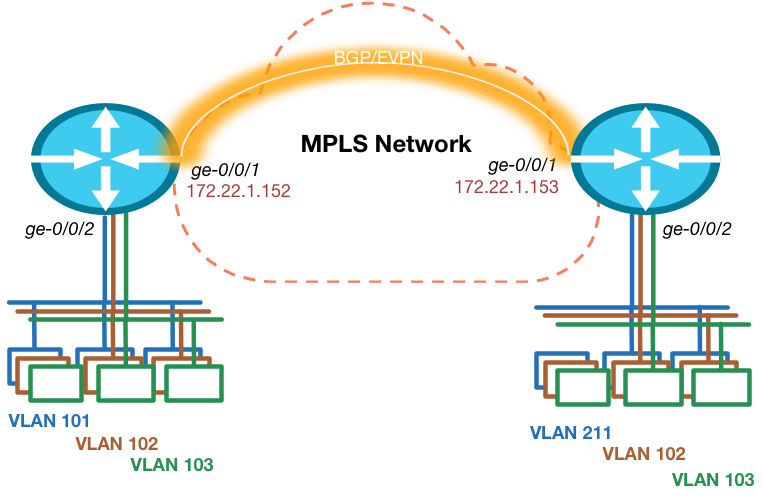
The topology is really simple. I’m using 2 routers in this example, so multi-homing is not in scope. Each router has an Ethernet segment connected that consists of multiple VLANs on each side. There is 1 VLAN ID that is not equal on both sides, so this has to be taken care of.
Prepare for EVPN
To make sure we can start creating our VPN, we have to ensure the foundation is in place. This means we need IP reachability to the other Data Center routers loopback address and we need BGP with the EVPN address family enabled. The Junos release I’m testing with needs a special knob to be enabled to ensure packet lookups are done in the right way. Other versions will see this knob disappear as it is default moving forward.
routing-options {
autonomous-system 64999;
forwarding-table {
Continue reading
Cisco Announces Version 3 of the CCIE Wireless Blueprint
The wait is finally over and version 3 of the wireless CCIE blueprint has finally been announced. On September 14, the new version of the written and lab exams will go live. This will bring a very long-in-the-tooth version 2 blueprint to an end after a nearly 4-year run. While we tearfully say goodbye to WCS, let’s take a look at what version 3 is bringing to the table.
New Lab Exam Format
First off, let’s look at what has changed in the format of the lab itself. The wireless track is following suit with the R&S and SP tracks and including multiple sections to the lab. The wireless lab will now begin with a 1 hour Diagnostic section, followed by a 7 hour Configuration section.
The Diagnostic section is similar to what was done in R&S and SP. This section tests your ability to assess and diagnose issues in a network without any access to the devices themselves. Basically, you are given access to a number of pieces of information (emails, topology diagrams, logs, etc) that describe an issue and give the needed information to figure out the root cause. You Continue reading
CCIE Data Center Rack Rental Scheduling Changes
In an effort to make our CCIE Data Center Rack Rentals have a better fair scheduler, we’ve implemented a new QoS policy for them as follows:
- Users can have a maximum of 3 concurrent sessions scheduled
- Sessions can be a maximum of 9 hours apiece
- Maximum hours per month limit is now removed
- Base sessions (Nexus 7K/5K) and add-ons (UCS/SAN & Nexus 2K/SAN) are now 8 tokens per hour
Note that these changes will only affect new session bookings, not any sessions that you already have reserved.
For those of you looking for more dedicated rack time I would suggest to look into our CCIE Data Center Bootcamp, where students get 12 days of 24/7 access to all hardware platforms in our racks (Nexus 7K/5K/2K, MDS, & UCS).
Happy Labbing!
IBM Exec: ‘Perfect Storm’ Poised to Transform Networking
 How IoT could change network management.
How IoT could change network management.
Carrier SDN Efforts Require New Service Orchestration
 Decades-old telco software is due for an SDN-driven makeover.
Decades-old telco software is due for an SDN-driven makeover.
Use Cases and Requirements for Service Centric SDN Management and Orchestration
Use Cases and Requirements for Service Centric SDN Management and Orchestration
by Cengiz Alaettinoglu, CTO - March 17, 2015
Ever since we unveiled our SDN MANO (management and orchestration) prototype at the Cisco Live event last May, we have been demonstrating it to many service providers, industry analysts, and partners. The response has been very positive due to the simplicity and depth of our approach, facilitated by the 10+ years of rich analytics in our arsenal. Aside from demonstrating the prototype, we have also been collecting SDN MANO requirements. The feedback indicates SDN MANO needs to be service centric.
Currently, Packet Design has the right foundation for service centric SDN monitoring and management, including the real-time topology, both current and predictive future traffic matrices, and the service awareness that these devices, paths and traffic flows encompass. Using these ingredients, we compute shortest and constraint-based non-shortest paths for these services.
For us and for the industry, the next step is service activation and policy. For example, for one of our mobile operator customers, the main use of these traffic-engineered paths is fast-re-route. When a link (or a router/switch) fails, they would like to pre-setup a bypass path so that packets are Continue reading