Five Next-Gen Networker Skills
With all the flux that is going on in the networking space, it’s hard to figure out what to do next. You may want to add to your skillset, but you’re not sure where to throw your effort. I’d like to focus on five different areas you can focus on, without talking about a specific product - at the end of the day, that’s just implementation details. These areas are going to be increasingly more valuable and will help you be more marketable when added to your existing network knowledge and experience.
This isn’t meant to say that all of these skills are required to move your career forward; indeed, everyone’s situation is unique. These are just ideas - the way you implement these skillsets in your own life is up to you.
1. Software Skills
Here, I’m not necessarily talking about full-fledged code knowledge. This section isn’t about going and getting a 4 year CS degree. This is mostly about tools, methodologies, and workflows. For some, this will include some kind of interpreted language like Python, but will vary in degree greatly from person to person.
To help get more detailed with this point, I’d like to drill down on four very Continue reading
Testing Cumulus Linux with Serverspec
As configuration management software has matured, engineers have recognized the importance of testing and validation. A comprehensive set of tools has been been developed around configuration management software such as Chef, Puppet, Ansible and others that allow you to test your configuration management scripts.
One of these tools is Serverspec, which is an RSpec testing framework for checking that servers are configured correctly by testing their actual state.
Serverspec can execute its tests on a remote host (such as a Cumulus Linux switch) via. SSH. The tests express how the system should be configured and Serverspec will test that the current system configuration meets those expectations.
Using Serverspec to validate your switch configuration means that you can make changes to your configuration management scripts and be confident that the changes have been applied correctly and worked as intended.
Getting started
Because Serverspec natively supports Cumulus Linux, all you have to do is install Serverspec and create your tests. If you’ve never used Serverspec before, the serverspec-init command will create an example called sample_spec.rb. Adding your own files is very simple; just make sure the filename ends in _spec.rb and the first line of the file is require 'spec_helper'
Writing tests
Individual Serverspec tests are Continue reading
Per-Packet Load Balancing on WAN links
One of my readers got an interesting idea: he’s trying to make the most of his WAN links by doing per-packet load balancing between a 30 Mbps and a 50 Mbps link. Not exactly surprisingly, the results are not what he expected.
Read more ...Upcoming webinar with Daniel Dib
Just wanted to let you know that Daniel from lostintransit.se is doing a webinar on network design. I will be attending and helping out any way i can.
Go here to learn more: https://learningnetwork.cisco.com/blogs/community_cafe/2015/01/21/network-design-fundamentals-webinar-with-ciscovip-daniel-dib
Quick ACL Entry Comparison Script
The ACL_compare function takes two lists of strings and compares the first to the second and returns a list comprising strings that are present in the first that are not in the second.
The listconvert function converts a file read into memory into a list of strings. Handy for when you use filenames as arguments when you run the script.
Essentially it’s all just string comparison really.
def ACL_compare(fwsm_ACL,asa_ACL):
comparison=[]
for line in fwsm_ACL:
if line in asa_ACL:
pass
else:
comparison.append(line)
return comparison
def listconvert(file):
newlist=file.readlines()
return newlist
Network Design Webinar With Yours Truly at CLN
I’m hosting a network design webinar at the Cisco Learning Network on Feb 19th, 20.00 UTC+1.
As you may know, I am studying for the CCDE so I’m focusing on design right now but my other reason for hosting this is to remind people that with all the buzzwords around SDN and NfV going around, the networking fundamentals still hold true. TCP/IP is as important as ever, building a properly designed network is a must if you want to have overlays running on it. If you build a house and do a sloppy job with the foundation, what will happen? The same holds true in networking.
I will introduce the concepts of network design. What does a network designer do? What tools are used? What is CAPEX? What is OPEX? What certifications are available? What is important in network design? We will also look at a couple of design scenarios and reason about the impact of our choices. There is always a tradeoff!
If you are interested in network design or just want to tune in to yours truly, follow this link to CLN.
I hope to see you there!
Kubernetes 101 – Networking
 One of the reasons that I’m so interested in docker and it’s associated technologies is because of the new networking paradigm it brings along with it. Kubernetes has a unique (and pretty awesome) way of dealing with these networking challenges but it can be hard to understand at first glance. My goal in this post is to walk you through deploying a couple of Kubernetes constructs and analyze what Kubernetes is doing at the network layer to make it happen. That being said, let’s start with the basics of deploying a pod. We’ll be using the lab we created in the first post and some of the config file examples we created in the second post.
One of the reasons that I’m so interested in docker and it’s associated technologies is because of the new networking paradigm it brings along with it. Kubernetes has a unique (and pretty awesome) way of dealing with these networking challenges but it can be hard to understand at first glance. My goal in this post is to walk you through deploying a couple of Kubernetes constructs and analyze what Kubernetes is doing at the network layer to make it happen. That being said, let’s start with the basics of deploying a pod. We’ll be using the lab we created in the first post and some of the config file examples we created in the second post.
Note: I should point out here again that this lab is built with bare metal hardware. The network model in this type of lab is likely slightly different that what you’d see with a cloud provider. However, the mechanics behind what Kubernetes is doing from a network perspective should be identical.
So just to level set, here is what our lab looks like…
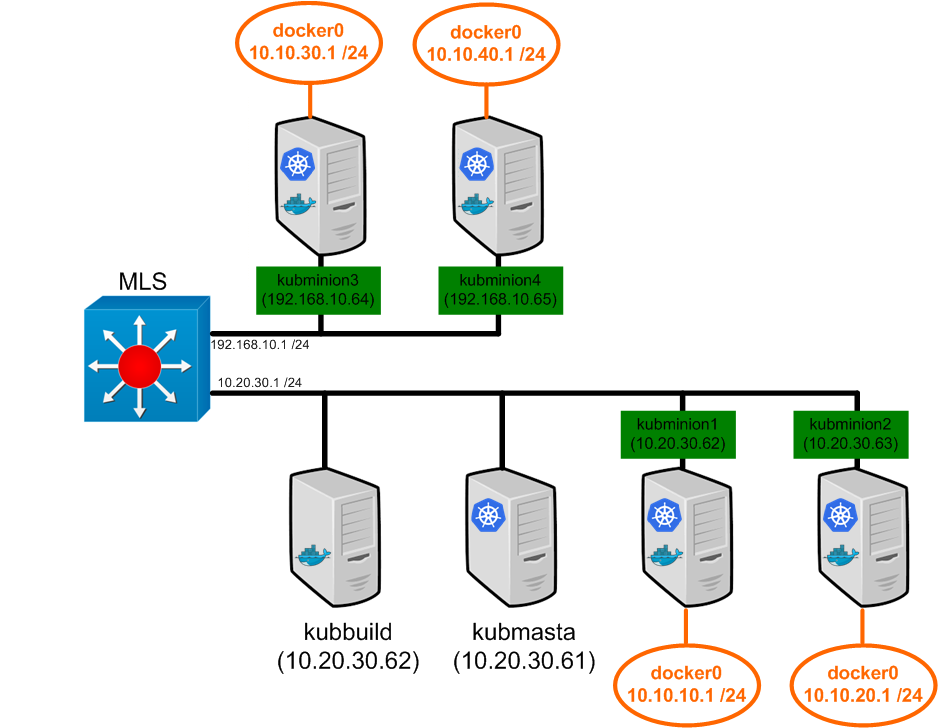
We touched on the topic of pod IP addressing before, but let’s provide Continue reading
Five Next-Gen Networker Skills
With all the flux that is going on in the networking space, it’s hard to figure out what to do next. You may want to add to your skillset, but you’re not sure where to throw your effort. I’d like to focus on five different areas you can focus on, without talking about a specific product - at the end of the day, that’s just implementation details. These areas are going to be increasingly more valuable and will help you be more marketable when added to your existing network knowledge and experience.Five Next-Gen Networker Skills
With all the flux that is going on in the networking space, it’s hard to figure out what to do next. You may want to add to your skillset, but you’re not sure where to throw your effort. I’d like to focus on five different areas you can focus on, without talking about a specific product - at the end of the day, that’s just implementation details. These areas are going to be increasingly more valuable and will help you be more marketable when added to your existing network knowledge and experience.How to run GUI applications on an Amazon AWS cloud server
In a previous post, I showed how easy it is to set up a remote server on Amazon’s AWS service. Now I would like see if I can run one or more of the open-source network simulators I’ve been using on this remote server. I want be able to access a network simulator from any device such as a personal computer, a tablet, or even a smart phone.
To accomplish this, I first need to install a Linux desktop environment on the remote Ubuntu server. Then, I need to set up the server and my client devices to allow the graphical user interface displayed on a remote server to be viewed on a local client.
In this post I will show how to install a Linux desktop (in this case, XFCE) and how to set up either VNC or X11 on a server and client.
Required software
Linux desktop
In this example, I chose to run the XFCE desktop environment on the Amzaon AWS remote server because XFCE uses less resources than other desktop environments such as Gnome or KDE.
Remote-access methods
There are two common methods for accessing a remote server’s graphical user interface:
- VNC, Virtual Network Computing, Continue reading
