Questions I’m Asking Myself About SD-WAN Solutions
There’s a lot to SD-WAN technology, and there are a number of devils in the implementation details that have been nagging at me as I listen to briefings and record podcasts from vendors in the space. SD-WAN technology questions that bother me… What’s the impact to hosts on virtual machine based endpoints, i.e. how much CPU does […]PlexxiPulse—Leading the pack
This week, Facebook announced a new modular switch called the “6-pack,” which builds off of The Wedge (Facebook’s innovative piece of networking equipment announced last June.) The development of the “6-pack” comes on the heels of a relatively new white box movement within the networking industry where generic, off-the-shelf switching and routing hardware is used rather than custom-made infrastructure, making networks more manageable and easy to scale. Julie Bort covered this very topic earlier this week in her Cisco earnings roundup for Business Insider, and cited Plexxi as one of the startups leading the charge against complicated, legacy-type infrastructures like Cisco. Here at Plexxi, one of our top priorities is to provide our customers with the most efficient network possible and we’re proud to be recognized as an industry trailblazer.
Below please find a few of our top picks for our favorite news articles of the week. Have a great weekend!
Streetwise Journal: Cisco CEO: We Will Crush Facebook and Have Fun Beating VMware
By Larry Banks
On fire since a decent quarterly earnings report in which Cisco revenues rose by 7% and forecast 3 to 5% growth next quarter, the company CEO John Chambers was hugely confident Continue reading
iPexpert’s Newest “CCIE Wall of Fame” Additions 2/13/2015
Please join us in congratulating the following iPexpert client’s who have passed their CCIE lab!
This Week’s CCIE Success Stories
- Steven Allspach, CCIE #46810 (Routing & Switching)
- Ahmed Hussain, CCIE #46833 (Routing & Switching)
- Oluwaseyi Bello, CCIE #46897 (Routing & Switching)
- Michael O’Nan, CCIE #46879 (Collaboration)
- Justin Lenhart, CCIE #46911 (Collaboration)
- Esteban Araya Paniagua, CCIE #46910 (Collaboration)
- Ade Adeoshun, CCIE #46959 (Collaboration)
This Week’s CCIE Testimonials
Steven Allspach, CCIE #46810
“To prepare for my lab, I used all of iPexpert’s videos and workbooks. I also took their 10-day onsite bootcamp (one of week technology focused labbing and the one-week lab experience). The bootcamp was by far the best decision I had made during my studies. The bootcamp allowed me to completely submerge myself in the CCIE technologies uninterrupted for 12 straight days 12-16 hours per day. I feel like I gained over 3-months of preparation in 12-days. I gained so much confidence after the bootcamp in November that I immediately scheduled my exam for February.
The OWLE bootamp prepared me in ways I never imagined. It gave me the practice of doing full 8-hour mock labs (TSHOOT/Diag/Config). Each day we would complete a Continue reading
Basics: The Difference Between Bandwidth and Speed
A link in a network is determined by two factors, bandwidth and speed. These are usually the same but not always. Speed is bit rate of the circuit while bandwidth is the amount of “speed” available for use. As an example, a 500 Megabit Ethernet MPLS service which uses a 1 Gigabit Ethernet connection to site […]
The post Basics: The Difference Between Bandwidth and Speed appeared first on EtherealMind.
Hands-On Tail-F Experience on Software Gone Wild
Tail-F NCS implements one of the most realistic approaches to service abstraction (the cornerstone of SDN – at least in my humble opinion) – an orchestration system that automates service provisioning on existing infrastructure.
Is the product really as good as everyone claims? How hard is it to use? How steep is the learning curve? Boštjan Šuštar and Marko Tišler from NIL Data Communications have months of hands-on experience and were willing to share it in Episode 22 of Software Gone Wild.
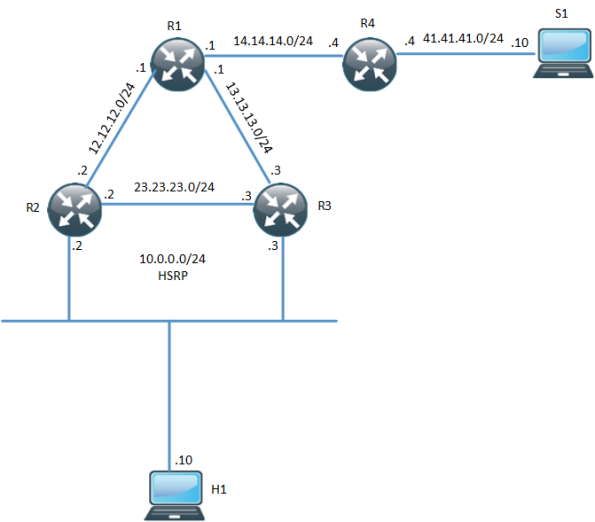
HSRP AWARE PIM
In environments that require redundancy towards clients, HSRP will normally be running. HSRP is a proven protocol and it works but how do we handle when we have clients that need multicast? What triggers multicast to converge when the Active Router (AR) goes down? The following topology is used:
One thing to notice here is that R3 is the PIM DR even though R2 is the HSRP AR. The network has been setup with OSPF, PIM and R1 is the RP. Both R2 and R3 will receive IGMP reports but only R3 will send PIM Join, due to it being the PIM DR. R3 builds the (*,G) towards the RP:
R3#sh ip mroute 239.0.0.1
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Continue reading
DMVPN Dynamic Multipoint VPN
DMVPN is dynamic, scalable and easy to configure Cisco specific VPN solution. DMVPN uses two major technologies for its operation : NHRP Next Hop Resolution Protocol mGRE Multipoint GRE In this post I will explain all the basics of DMVPN. For detailed routing protocol design over DMVPN will be covered in different post which will… Read More »
The post DMVPN Dynamic Multipoint VPN appeared first on Network Design and Architecture.
Musing: Who Cares About FCoE in 2015 ?
While I continue to scratch my head about who is foolish enough to actually deploy FCoE, perhaps a more important question is which vendors care about it ?
The post Musing: Who Cares About FCoE in 2015 ? appeared first on EtherealMind.