Use Additional BGP Paths for IBGP Load Balancing
I wrote about the optimal BGP path selection with BGP additional paths in 2021, and I probably mentioned (in one of the 360 BGP-related blog posts) that you need it to implement IBGP load balancing in networks using BGP route reflectors. If you want to try that out, check out the IBGP Load Balancing with BGP Additional Paths lab exercise.
Click here to start the lab in your browser using GitHub Codespaces (or set up your own lab infrastructure). After starting the lab environment, change the directory to lb/4-ibgp-add-path and execute netlab up.
Connect and secure any private or public app by hostname, not IP — free for everyone in Cloudflare One
Connecting to an application should be as simple as knowing its name. Yet, many security models still force us to rely on brittle, ever-changing IP addresses. And we heard from many of you that managing those ever-changing IP lists was a constant struggle.
Today, we’re taking a major step toward making that a relic of the past.
We're excited to announce that you can now route traffic to Cloudflare Tunnel based on a hostname or a domain. This allows you to use Cloudflare Tunnel to build simple zero-trust and egress policies for your private and public web applications without ever needing to know their underlying IP. This is one more step on our mission to strengthen platform-wide support for hostname- and domain-based policies in the Cloudflare One SASE platform, simplifying complexity and improving security for our customers and end users.
In August 2020, the National Institute of Standards (NIST) published Special Publication 800-207, encouraging organizations to abandon the "castle-and-moat" model of security (where trust is established on the basis of network location) and move to a Zero Trust model (where we “verify anything and everything attempting to establish access").
LIU000: Announcing Life In Uptime, a New Podcast to Get You Started on Your IT Journey
Life In Uptime is a brand-new podcast that explores the real journeys of the people who build and run enterprise IT. Each episode dives into the personal and professional paths that got each guest to where they are today—because the road to a career in technology isn’t one-size-fits-all. This show is for anyone wondering how... Read more »Arista EOS Hates a Routing Instance with No Interfaces
I always ask engineers reporting a netlab bug to provide a minimal lab topology that would reproduce the error, sometimes resulting in “interesting” side effects. For example, I was trying to debug a BGP-related Arista EOS issue using a netlab topology similar to this one:
defaults.device: eos
module: [ bgp ]
nodes:
a: { bgp.as: 65000 }
b: { bgp.as: 65001 }
Imagine my astonishment when the two switches failed to configure BGP. Here’s the error message I got when running the netlab’s deploy device configurations Ansible playbook:
The RUM Diaries: enabling Web Analytics by default
Measuring and improving performance on the Internet can be a daunting task because it spans multiple layers: from the user’s device and browser, to DNS lookups and the network routes, to edge configurations and origin server location. Each layer introduces its own variability such as last-mile bandwidth constraints, third-party scripts, or limited CPU resources, that are often invisible unless you have robust observability tooling in place. Even if you gather data from most of these Internet hops, performance engineers still need to correlate different metrics like front-end events, network processing times, and server-side logs in order to pinpoint where and why elusive “latency” occurs to understand how to fix it.
We want to solve this problem by providing a powerful, in-depth monitoring solution that helps you debug and optimize applications, so you can understand and trace performance issues across the Internet, end to end.
That’s why we’re excited to announce the start of a major upgrade to Cloudflare’s performance analytics suite: Web Analytics as part of our real user monitoring (RUM) tools will soon be combined with network-level insights to help you pinpoint performance issues anywhere on a packet’s journey — from a visitor’s browser, through Cloudflare’s network, to your Continue reading
TCG058: Creating the Internet Layer That Should Have Been With Avery Pennarun
In this deep dive episode, we explore the evolution of networking with Avery Pennarun, Co-Founder and CEO of Tailscale. Avery shares his extensive journey through VPN technologies, from writing his first mesh VPN protocol in 1997 called “Tunnel Vision” to building Tailscale, a zero-trust networking solution. We discuss how Tailscale reimagines the OSI stack by... Read more »NAN100: A Retrospective On 100 Episodes of Network Automation Nerds
Network Automation Nerds has reached a special milestone: episode 100! Eric Chou looks back on 5 years of conversations with network automation pioneers, practitioners, and visionaries. Drew Conry-Murray from the Packet Pushers joins Eric, along with online guest Ioannis Theodoridis, to find out why Eric started the podcast, his goals for all these conversations, a... Read more »IPB183: Measuring IPv6 and IPv6 Statistics
Today we talk about measuring IPv6 and IPv6 statistics. We talk about why it’s useful to measure IPv6, how to track v6 deployment initiatives, and tools to help with your measurements. Episode Links: Google IPv6 – Google IPv6 Global Statistics Dashboard IPv6 Enabled – Hexabuild Episode Transcript: This episode was transcribed by AI and lightly... Read more »SwiNOG 40: When a Routing Control Functions Is Too Fresh
During integration testing, I find unexpected quirks in network devices way too often. However, that’s infinitely better than experiencing them in production (even after thoroughly testing stuff) while discovering that your peers don’t care about routing security, RPKI, and similar useless stuff.
For example, what happens if you define a new Routing Control Function (RFC) on Arista EOS and apply it to BGP routing updates in the same configuration session? You’ll find out in the Sorry We Messed Up (video) presentation Stefan Funke had at SwiNOG 40 (note: the bug has been fixed in the meantime).
Calico Whisker vs. Traditional Observability: Why Context Matters in Kubernetes Networking
Are you tired of digging through cryptic logs to understand your Kubernetes network? In today’s fast-paced cloud environments, clear, real-time visibility isn’t a luxury, it’s a necessity. Traditional logging and metrics often fall short, leaving you without the context needed to troubleshoot effectively.
That’s precisely what Calico Whisker’s recent launch (with Calico v3.30) aims to solve. This tool provides clarity where logs alone fall short. In the sections below, you’ll get a practical overview of how it works and how it fits into modern Kubernetes networking and security workflows.
If you’re relying on logs for network observability, you’re not alone. While this approach can provide some insights, it’s often a manual, resource-intensive process that puts significant load on your distributed systems. It’s simply not a cloud-native solution for real-time insights.
So are we doomed? No. Calico Whisker transforms network observability from a chore into a superpower.
What is Calico Whisker?
Calico Whisker is a free, lightweight, Kubernetes-native observability user interface (UI) created by Tigera and introduced with Calico Open Source v3.30. It’s designed to give you a simple yet powerful window into your cluster’s network traffic, helping you understand network flows and evaluate policy behavior in real-time.
PP078: Using Free Tools for Detection Engineering
You can build effective, scalable detection pipelines using free and open-source tools like Zeek, Suricata, YARA, and Security Onion. Today on Packet Protector we welcome Matt Gracie, Senior Engineer at Security Onion Solutions — the team behind the open-source platform used for detection engineering, network security monitoring, and log management. Matt has over 15 years... Read more »HS112: Standardizing NaaS Service Definitions
Network-as-a-Service (NaaS) promises enterprises the ability to set up and configure connectivity and network security with a couple of clicks. But for NaaS to truly transform enterprise networking, one thing has been missing: standards. Enter Mplify (formerly the Metro Ethernet Forum), a non-profit focused on standardizing NaaS service definitions. Mplify’s CTO, Pascal Menezes, joins Johna... Read more »Configuring Palo Alto Administrator Authentication with Cisco ISE (Radius)

Let’s assume a simple scenario. You have two different teams managing your Palo Alto firewalls. One team is made up of network administrators who need full access to the firewalls. The other team only needs limited access and should not be able to make any configuration changes.
A common way to handle this is by using Admin Roles and a remote Radius server. You can assign different admin roles based on who is logging in, without creating local users on every firewall. In this post, we will look at how to achieve this using Cisco ISE and Radius. You do not have to use Cisco ISE, any Radius server can do the job, but this post focuses on Cisco ISE since it is commonly used in enterprise environments.

Overview
For this example, we will have two users, each belonging to a different group with different access requirements. In most environments, group membership is managed by something like Active Directory. For the sake of simplicity, Continue reading
Updated: netlab Network Topology Graphs
netlab release 25.09 introduced numerous graphing enhancements and a new graph type (IS-IS graphs), so I decided to write a series of blog posts explaining how you can generate graphs from netlab lab topologies.
I wrote an intro to netlab topology graphs years ago, and as expected, it was hopelessly outdated, so I started the project with a complete overhaul of that article.
N4N038: Well Actually 02 – OSPF Multi-Area and LSA Types
We got some interesting listener feedback from our series on OSPF, so today’s N Is for Networking is another “Well actually” episode where we dig into that feedback. In particular, we’ll cover a defense of OSPF multi-area deployments, and dig into OSPF LSA types. Episode Links: OSPF Basics – N Is For Networking Episode 38... Read more »Integrating CrowdStrike Falcon Fusion SOAR with Cloudflare’s SASE platform
Security teams know all too well the grind of manual investigations and remediation. With the mass adoption of AI and increasingly automated attacks, defenders cannot afford to rely on overly manual, low priority, and complex workflows.
Heavily burdensome manual response introduces delays as analysts bounce between consoles and high alert volumes, contributing to alert fatigue. Even worse, it prevents security teams from dedicating time to high-priority threats and strategic, innovative work. To keep pace, SOCs need automated responses that contain and remediate common threats at machine speed before they become business-impacting incidents.
That’s why today, we’re excited to announce a new integration between the Cloudflare One platform and CrowdStrike's Falcon® Fusion SOAR.
As part of our ongoing partnership with CrowdStrike, this integration introduces two out-of-the-box integrations for Zero Trust and Email Security designed for organizations already leveraging CrowdStrike Falcon® Insight XDR or CrowdStrike Falcon® Next-Gen SIEM.
This allows SOC teams to gain powerful new capabilities to stop phishing, malware, and suspicious behavior faster, with less manual effort.
Although teams can always create custom automations, we’ve made it simple to get started with two Continue reading
NB543: Splunk, ServiceNow Announce AI Agents; Data Center Spending Runs Amok
Take a Network Break! We start with a listener correction on Cisco’s history of wireless certifications, then dig into a couple of red alerts on Microsoft Defender and a backdoor in Outlook. On the news front, Cisco announces new AI agents and SoC packages for Splunk; F5 spends $180 million to buy an AI security... Read more »[FATAL] Ansible Release 12.0 Breaks netlab Jinja2 Templates
On September 9th, the ansible release 12.0 appeared on PyPi. It requires ansible-core release 2.19, which includes breaking changes to Jinja2 templating. netlab Jinja2 templates rely on a few Ansible Jinja2 filters; netlab thus imports and uses those filters, and it looks like those imports pulled in the breaking changes that consequently broke the netlab containerlab configuration file template (details).
netlab did not check the Ansible core version (we never had a similar problem in the past), and the installation scripts did not pin the Ansible version (feel free to blame me for this one), which means that any new netlab installation created after September 9th crashed miserably on the simplest lab topologies.
This is the workaround we implemented in netlab release 25.09-post1 (released earlier today):
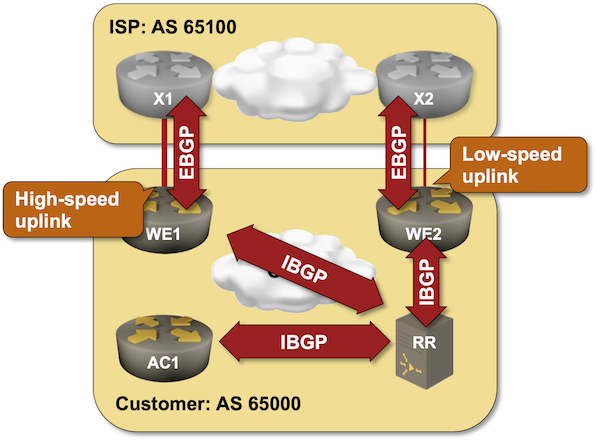
BGP Multi-Homed with Two ISPs and Two Routers

If you are a Network Engineer working for an Enterprise, you may not work with BGP as often as someone at an ISP does. In most cases, you will only run BGP at the edge of your network to peer with your ISP and leave it at that. There are many ways to connect to an ISP. If you are a small company without your own IP address space or autonomous system, you typically rely on the ISP to allocate a portion of their IP space for you, and you use a static route pointing to them (single-homed). For redundancy, you might connect to two ISPs or take two diverse links from the same ISP (dual-homed/multi-homed). In many of those setups, you may not run BGP yourself, but it depends on the design.
In this post, we will look at a scenario where you already have your own IP address space and an AS number, and you connect to two different ISPs. You will advertise your IP space to the Internet via both ISPs and, at the same time, receive the full Internet routing table from both ISPs.
If you are completely new to BGP, I recommend checking out Continue reading
A deep dive into Cloudflare’s September 12, 2025 dashboard and API outage
We had an outage in our Tenant Service API which led to a broad outage of many of our APIs and the Cloudflare Dashboard.
The incident’s impact stemmed from several issues, but the immediate trigger was a bug in the dashboard. This bug caused repeated, unnecessary calls to the Tenant Service API. The API calls were managed by a React useEffect hook, but we mistakenly included a problematic object in its dependency array. Because this object was recreated on every state or prop change, React treated it as “always new,” causing the useEffect to re-run each time. As a result, the API call executed many times during a single dashboard render instead of just once. This behavior coincided with a service update to the Tenant Service API, compounding instability and ultimately overwhelming the service, which then failed to recover.
When the Tenant Service became overloaded, it had an impact on other APIs and the dashboard because Tenant Service is part of our API request authorization logic. Without Tenant Service, API request authorization can not be evaluated. When authorization evaluation fails, API requests return 5xx status codes.
We’re very sorry about the disruption. The rest Continue reading
