Unreliable Multicast means Unreliable VMware VSAN
Howard Marks from Deep Storage and long-term curmudgeon sent Ethan & I the following email: As I continue to tilt at the VMware windmill I’m facing fanbois telling me that all you have to do is plug the EVO:RAIL in and turn it on. This of course leaves out the fact that the little sucker still […]
The post Unreliable Multicast means Unreliable VMware VSAN appeared first on EtherealMind.
Great Wi-Fi Starts with Proper Design
I’m sure that we have all experienced poorly designed Wi-Fi networks. When a technology is so ubiquitous, so easily accessible, and is increasingly the most relied upon method of Internet access for mobile devices and cloud computing, then there are bound to be some issues. Unfortunately, the prevalence of underperforming Wi-Fi networks is still much too common for my liking.
Great Wi-Fi starts with proper design. There are various approaches to WLAN design that have evolved over time, ranging from providing basic coverage to maximum capacity and situations in-between.
At one end of the spectrum, we have a basic coverage oriented design. This was the historical way of designing a WLAN that simply involved ensuring adequate signal strength from access points was present in desired locations. At the other end of the spectrum is a design focusing on maximum capacity. This involves careful RF planning in order to integrate the most Wi-Fi cells as possible into a physical area.

The problem with both of these approaches is that they are the extremes and aren't applicable for many wireless networks. Basic coverage designs may still work for warehouses and some retailers and maximum capacity designs are great for stadiums and Continue reading
Comware5: Send test SNMP traps and syslog messages
When configuring a network device to be managed by an NMS such as HP IMC, you may want to send some test syslog or snmp traps to verify the correct operation of your settings. You can generate traps/logs by triggering … Continue readingHP 6125XLG FCoE NPV mode white paper
The HP 6125XLG is a Comware 7 based blade interconnect switch which has full support for FCoE. I found this technical whitepaper with a sample FCoE NPV mode configuration, it is shown with uplinks to an existing Nexus 5500/6000 FCoE … Continue readingHP Unified Wireless: Whitepapers published by HP
The HP Unified Wireless manuals are quite extensive, but it can be challenging to get a complete picture of a certain feature. HP has now published a series of whitepapers covering specific use cases and technologies, they can be found … Continue readingJust Published: Scaling Overlay Virtual Networking Videos
The edited videos for Scaling Overlay Virtual Networking webinar are available on ipSpace.net Content site. Nuage Networks sponsored the webinar; the videos are thus publicly available (without registration).
Network Access Broker Conceptual Demo
The Network Access Broker Conceptual Demo
by Kris Olander, Sr. Technical Marketing Engineer - December 16, 2014
Talk is cheap when it comes to SDN, but at Packet Design we’ve created a working SDN analytics and orchestration prototype that will enable network engineers to effectively manage hybrid networks. In this new demo, we outline how our Network Access Broker (NAB) – based on our core Route Explorer™ System – analyzes application requests for network resources, assesses their impact on services, and provisions them optimally using a combination of the following (if you’re already familiar with SDN and its management challenges, you can skip the intro and head straight to the demo at the 2:47 mark):
- A layer 3 network topology model maintained in real time (IGP, BGP, and SDN controller-provided topologies like OpenFlow),
- A traffic demand matrix,
- Predicted network loads from historical baselines, and
- Analytics algorithms that compute efficient paths based on link utilizations/end-to-end delays, model new demand, and predict the impact of link/node failures on routing and traffic. Once the optimal paths have been computed, the NAB configures the network to provision them using the SDN controller (OpenDaylight in this example).
In the NAB demo, we use Continue reading
GNS3 Holiday Mission: Free GNS3 T-Shirt
We want to hear your feedback on the networking products that made the top of your list in 2014. We are excited to launch our GNS3IPv6
Recently, I’ve heard several people suggest that the advent of IPv6 changes the requirements for data-center virtual network solutions. For instance, making the claim that network overlays are no longer necessary. The assumption made is that once an instance has a globally unique IP address that all requirements are met.
In my view, this analysis fails in two dimensions:
- In the assumption that it is desirable to give instances direct internet access (via a globally routed address);
- In the assumption that overlay solutions are deployed to solve address translation related problems;
Neither of these assumptions hold when examined in detail.
While there are IaaS use cases of users that just want to be able to fire up a single virtual-machine and use it as a personal server, the most interesting use case for IaaS or PaaS platforms is to deploy applications.
These applications, serve content for a specific virtual IP address registered in the DNS and/or global load-balancers; that doesn’t mean that this virtual IP should be associated with any specific instance. There is layer of load-balancing that maps the virtual IP into the specific instance(s) service the content. Typically this is done with a load-balancer in proxy mode.
As an aside, enabling IPv6 in the load-balancer Continue reading
Stop thief!
The Host-sFlow project recently added added CPU steal to the set of CPU metrics exported.steal (since Linux 2.6.11)Keeping close track of the stolen time metric is particularly import when running managing virtual machines in a public cloud. For example, Netflix and Stolen Time includes the discussion:
(8) Stolen time, which is the time spent in other operating systems
when running in a virtualized environment
So how does Netflix handle this problem when using Amazon’s Cloud? Adrian admits that they tracked this statistic so closely that when an instance crossed a stolen time threshold the standard operating procedure at Netflix was to kill the VM and start it up on a different hypervisor. What Netflix realized over time was that once a VM was performing poorly because another VM was crashing the party, usually due to a poorly written or compute intensive application hogging the machine, it never really got any better and their best learned approach was to get off that machine.The following articles describe how to monitor public cloud instances using Host sFlow agents:
The CPU steal metric is particularly relevant to Network Function Virtualization (NFV). Virtual Continue reading
Using bird to pull global BGP route counts
For an electronics project I’m working on I wanted a way to check the current global routing table every five minutes for both IPv4 and IPv6. I did not want to log into anyone else’s router or looking glass as checking every 5 minutes may be considered abuse. So I thought to spin up a […]The proliferation of kustom virtual machine builds.
I think there is something really wrong with me when I start playing an app on my phone and I start thinking, "Can I emulate this on myThe Tale of the Mysterious PIM Prune
Christmas is lurking around the corner and in the spirit of Denise “Fish” Fishburne, I give you the “The Tale of the Mysterious PIM Prune”.
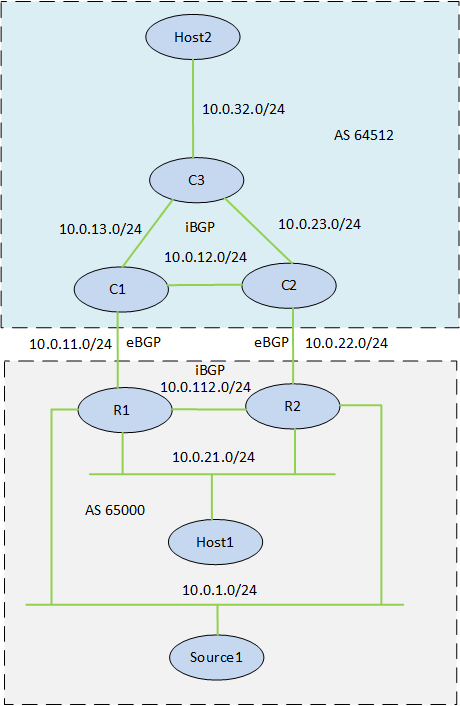
I have been working a lot with multicast lately which is also why I’ve blogged about it. To start off this story, let’s begin with a network topology.
The multicast source is located in AS 65000 and contains two routers that are connected to the multicast source. The routers run BFD, OSPF, iBGP, PIM internally and the RP is located on C1. There is a local receiver in AS 65000 and a remote one in AS 64512. The networks 10.0.1.0/24 and 10.0.21.0/24 come off the same physical interface. If you want to replicate this lab, all the configs are provided here.
This network requires fast convergence and I have been troubleshooting a scenario where the active multicast router (R1) has its LAN interface go down, meaning that the traffic from the source must come in on R2. In this scenario I have seen convergence in up to 60 seconds which is not acceptable. The BGP design is for R2 to still exit out via R1 if the link is Continue reading
Network Break 24
It’s time for the Network Break! Sit back, grab a coffee, and join us for an analysis of the latest IT news, vendor moves and new product announcements. We’ll separate the signal from the noise--or at least make some noise of our own.
Author information
The post Network Break 24 appeared first on Packet Pushers Podcast and was written by Greg Ferro.
Are SDN Controllers a Security Risk ?
No. When compared to the operation of existing networks, SDN is much more secure.
The post Are SDN Controllers a Security Risk ? appeared first on EtherealMind.
When and when not to multithread
At the end of my last post on Python multithreading, I said my example was not the best. Let me expand some more on this. While testing code in the previous post, I noticed that certain code was slower when multiple threads were running. Also these threads are not tied to a CPU. If we […]HP Unified Wireless: Portal free user-url
On the Unified wireless solution, guest users can be authenticated through the captive web-portal feature of the portal server. The network admin could allow some guest traffic to pass without guest authentication to provide a “walled-garden” solution. This was already … Continue readingWhy Your Presentation Stinks (Part 1)
Powerpoint doesn’t stink. Our presentation skills do. So how do we fix it?
First, you must decide: what do I want this presentation to be? We’ve all seen the brilliant TED talks about new ideas. We’ve all seen the really cool sample presentations from those online presentation sites about someone’s trip around the world. When you’re looking at those talks, though, remember this: they are selected out of millions of talks for their content, and their content fits their format. I’ve seen folks do fairly standard slideshows with Prezy. It doesn’t work. I’ve also seen people do “let me tell you about my trip” presentations with Powerpoint. Again, it doesn’t work.
So, just like network engineering, pick the right tool for the job. Since most of an engineer’s presentations aren’t going to feature exciting trips down the River of Doubt, or even up Doubtin’ Mountain, we’re probably pretty safe to stick with a fairly standard presentation package — slides, warts, and all.
Yes, it’s important to get the flow right. I once stood in for a presenter who’d lost his voice — the material was router architecture (hardware and software), so it’s a topic I know well, so I wasn’t Continue reading
Dial-Peer Digit Manipulation
In the CCIE Collaboration lab, understanding dial-peers is extremely important. Lack of knowledge in this area can yield devastating results in your lab score report since they can be found in so many different sections of the exam. We must be thoroughly prepared to tackle every aspect of this technology should we be presented with it at some point.
I recently got a great question in our forums about digit manipulation within POTS dial-peers and how they interact with translation rules and profiles. I figured that since this is such an important topic, my answer to his question bears repeating so it can reach a wider audience.
Let’s begin with the simple example of dialing the number “123” from a CUCME phone. Of course, the POTS dial-peer must be created to support the desired behavior.
When this pattern is selected, all digits will be stripped automatically since they are explicitly defined. This is due to the “automatic POTS dial-peer digit strip” feature in IOS. See below for the ISDN Q.931 debug output (no Called Party Number).
Since we are not currently sending a Called Party Number, we’ll need some way to add the digits back to the string to Continue reading
Enterprises Have Many Unprofitable Applications, Public Clouds Do Not
Enterprise IT supports many unprofitable applications. Microsoft Exchange, legacy databases, obsolete accounting systems, end-of-life desktop operating systems and much more. Public clouds can, and do, cancel unprofitable products. This is a brutal truth in cloud planning. Takeaways: Enterprise IT supports many applications that are unprofitable to own and maintain Executives and managers are commonly unprepared […]
The post Enterprises Have Many Unprofitable Applications, Public Clouds Do Not appeared first on EtherealMind.