Opening up VXLAN with OpenStack
VXLAN is hot. We constantly hear about VXLAN at conferences, in product announcements, blog posts, and most importantly, we hear about it from our customers.
VXLAN exciting technology that’s been integrated into a number of product offerings from networking and cloud vendors. OpenStack® supports VXLAN via a set of Neutron plugins, and Metacloud OpenStack® has supported VXLAN for a few releases already.
One of the challenges with deploying and scaling VXLAN has been the MAC-to-VTEP learning and BUM (Broadcast, Unknown Unicast, Multicast) packet flooding. The VXLAN spec uses a simple multicast solution to solve this problem. Multicast has its own set of scaling challenges, and reliable multicast routing between network segments isn’t always available. The majority of vendors who have VXLAN support have attempted to solve this problem by implementing their own form of learning and flooding. Some of these solutions work well, but all of them require you to operate in a homogenous network environment or pay expensive per CPU or per VM licensing fees.
Until today…
Metacloud, in partnership with our friends at Cumulus Networks®, have been working together on a solution to these problems for the past year. Starting today, VXFLD is open source and freely Continue reading
EIGRP OTP example
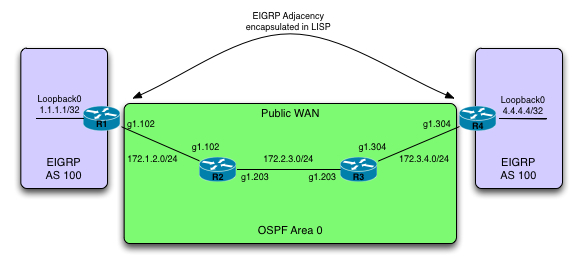
In this post id like to provide an example of a fairly new development to EIGRP which is called EIGRP Over The Top (OTP).
In all its simplicity it establish an EIGRP multihop adjacency using LISP as the encapsulation method for transport through the WAN network.
One of the applications of this would be to avoid relying on the SP in an MPLS L3 VPN. You could simply use the L3 VPN for transport between the interfaces directly connected to the Service Provider and run your own adjacency directly between your CPE routers (without the use of a GRE tunnel, which would be another method to do it)
The topology used for this example consists of 4 routers. All 4 of the routers are using OSPF to provide connectivity (you could take this example and do a L3 VPN using MPLS as an exercise). Im simply taking the lazy path and doing it this way ![]()
R1 and R4 are running EIGRP in a named process “test”. This process is in Autonomous system 100 and the Loopback 0 interfaces are advertised into the V4 address-family.
Lets verify that we have connectivity between R1’s g1.102 interface and R4’s g1.304 Continue reading
Corsa Adds BGP, Proves OpenFlow In Hardware Scales
A constant refrain from vendors and software makers is that OpenFlow technology doesn't scale, is too complex, and doesn't work in hardware. Startups like Corsa are proving them wrong.
The post Corsa Adds BGP, Proves OpenFlow In Hardware Scales appeared first on EtherealMind.
Comware IRF: L2 MAC Address roaming
IRF is used on Comware switches (and some routers as well now) to virtualize 2 or more devices as 1 virtual device. This is a very convenient way to simplify the network setup and management. Although IRF is very easy … Continue readingUnified wireless: AP template rename
On the Unified Wireless controllers, it is common to enable the auto-ap and auto-persistent features to make it easy to adopt new Access Points. The new APs will be discovered and auto-registered as AP template based on the AP MAC … Continue readingUnified wireless : AP console/telnet access
With the Unified controllers, the APs which come online will dynamically get their configuration from the controller when they establish the LWAPP tunnel. When AP based feature are configured, such as AP provisioning or AP-based user authentication (de-central authentication), it … Continue readingTraining Wheels and Protective Gear
Throughout the development cycle of new features and functions for any network platform (or probably most other products not targeted at the mass market consumer) this one question will always come up: should we protect the user of our product from doing this? And “this” is always something that would allow the user of the product to really mess things up if not done right. As a product management organization you almost have to take a philosophical stand when it comes to these questions.
Protect the user
Sure enough, the question came up last week as part of the development of one our features. When putting the finishing touches on a feature that allows very direct control over some of the fundamental portions of what creates a Plexxi fabric, our QA team (very appropriately) raised the concern: if the user does this, bad things can happen, should we not allow the user to change this portion of the feature?
This balancing act is part of what as made networking as complex as it has become. As an industry we have been extremely flexible in what we have exposed to our users. We have given access to portions of our products Continue reading
I Challenge Me And You To 30 Blogs in 30 days
There are many people who are dissatisfied with the social media platforms. I am too. I'm challenging myself to blog 30 times in 30 days to highlight the blog as the best social media platform.
The post I Challenge Me And You To 30 Blogs in 30 days appeared first on EtherealMind.
VXLAN and OTV: The Saga Continues
Randall Greer left a comment on my Revisited: Layer-2 DCI over VXLAN post saying:
Could you please elaborate on how VXLAN is a better option than OTV? As far as I can see, OTV doesn't suffer from the traffic tromboning you get from VXLAN. Sure you have to stretch your VLANs, but you're protected from bridging failures going over your DCI. OTV is also able to have multiple edge devices per site, so there's no single failure domain. It's even integrated with LISP to mitigate any sub-optimal traffic flows.
Before going through the individual points, let’s focus on the big picture: the failure domains.
Read more ...Show 208 – So, You Want To Work For A Vendor?
Lauren Malhoit, Paul Stewart, and Ed Henry join Packet Pushers hosts Greg Ferro and Ethan Banks for a discussion about what it’s like to work for a networking vendor. Lauren and Paul recently started working at Cisco in two very different roles, while Ed went the startup route, landing at Plexxi. Why did they do it? What […]
Author information
The post Show 208 – So, You Want To Work For A Vendor? appeared first on Packet Pushers Podcast and was written by Ethan Banks.
Blessay: Human Infrastructure Poverty & Over-Capitalisation In The Enterprise – Part 2
Is Enterprise IT starving its operational process by reducing headcount and overcapitalising on assets ? If so, what arguments can we make for or against this idea ? Part 2 of an essay on investing in people instead of equipment.
The post Blessay: Human Infrastructure Poverty & Over-Capitalisation In The Enterprise – Part 2 appeared first on EtherealMind.
Internet Regulation: Section 706 vs Title II
At the NANOG meeting in Baltimore this week I listened to a presentation by Patrick Gilmore on “The Open Internet Debate: Section 706 vs Title II”. It’s true that this is a title that would normally induce a comatose reaction from any audience, but don’t let the title put you off. Behind this is an impassioned debate about the nature of the retail Internet for the United States, and, I suspect, a debate about the Internet itself and the nature of the industry that provides it.A bit of maintenance
I am currently performing a bit of maintenance on the blog (moving host), so there might be some small errors here and there. I apologise for this! – Hopefully everything will be up and running smoothly in a few days time.
Thank you for your patience!
/KP
Technology Short Take #45
Welcome to Technology Short Take #45. As usual, I’ve gathered a collection of links to various articles pertaining to data center-related technologies for your enjoyment. Here’s hoping you find something useful!
Networking
- Cormac Hogan has a list of a few useful NSX troubleshooting tips.
- If you’re not really a networking pro and need a “gentle” introduction to VXLAN, this post might be a good place to start.
- Also along those lines—perhaps you’re a VMware administrator who wants to branch into networking with NSX, or you’re a networking guru who needs to learn more about how this NSX stuff works. vBrownBag has been running a VCP-NV series covering various objectives from the VCP-NV exam. Check them out—objective 1, objective 2, objective 3, and objective 4 have been posted so far.
Servers/Hardware
- I’m going to go out on a limb and make a prediction: In a few years time (let’s say 3–5 years), Intel SGX (Software Guard Extensions) will be regarded as important if not more important than the virtualization extensions. What is Intel SGX, you ask? See here, here, and here for a breakdown of the SGX design objectives. Let’s be real—the ability for an Continue reading
Cisco NX-API 1.0 Update
If you weren’t paying attention, it was easy to miss. NX-API, Cisco’s new JSON/XML switch API is now shipping as version 1.0. NX-API originated on the Nexus 9000 platform created by the Insieme group, and I’ve explored this in detail before.
In review, NX-API is a new, programmatic method of interacting with a Cisco Nexus switch. In many ways, Cisco is playing catch-up here, since this interface is really just a wrapper for the CLI (admittedly with some convenient output parsing), and most of their competitors have had similar interfaces for a while. Nevertheless, it is better than scraping an SSH session, so it’s worth looking into.
I’d like to go over a few new things you should know about if you are or will be working with this interface.
NX-API 1.0 Updates
From a strictly API perspective, not a lot seems to have changed. I would be more specific, but as of yet I’ve been unable to find release notes from Cisco on what’s changed from 0.1 to 1.0. If I ever find something like this, I’ll get my hands on it – part of publishing a good API means publishing good documentation, and Continue reading
Talking Tech Series: VMware NSX Edge Scale Out with Equal-Cost Multi-Path Routing
This post was written by Roie Ben Haim and Max Ardica, with a special thanks to Jerome Catrouillet, Michael Haines, Tiran Efrat and Ofir Nissim for their valuable input.
****
The modern data center design is changing, following a shift in the habits of consumers using mobile devices, the number of new applications that appear every day and the rate of end-user browsing which has grown exponentially. Planning a new data center requires meeting certain fundamental design guidelines. The principal goals in data center design are: Scalability, Redundancy and High-bandwidth.
In this blog we will describe the Equal Cost Multi-Path functionality (ECMP) introduced in VMware NSX release 6.1 and discuss how it addresses the requirements of scalability, redundancy and high bandwidth. ECMP has the potential to offer substantial increases in bandwidth by load-balancing traffic over multiple paths as well as providing fault tolerance for failed paths. This is a feature which is available on physical networks but we are now introducing this capability for virtual networking as well. ECMP uses a dynamic routing protocol to learn the next-hop towards a final destination and to converge in case of failures. For a great demo of how this works, you can Continue reading
Dependency management and organic IT integrations
If the future of IT is about integrated infrastructure, where will this integration take place? Most people will naturally tend to integrate systems and tools that occupy adjacent spaces in common workflows. That is to say that where two systems must interact (typically through some manual intervention), integration will take place. If left unattended, integration will grow up organically out of the infrastructure.
But is organic growth ideally suited for creating a sustainable infrastructure?
A with B with C
In the most basic sense, integration will tend to occur at system boundaries. If A and B share a boundary in some workflow, then integrating A with B makes perfect sense. And if B and C share a boundary in a different (or even further down the same) workflow, then it makes equal sense to integrate B with C.
In less abstract terms, if you use a monitoring application to detect warning conditions on the network, then integrating the monitoring application and the network makes good sense. If that system then flags issues that trigger some troubleshooting process, then integrating the tools with your help desk ticketing system might make sense to automatically open up trouble tickets as issues arise.
Data Center Design Case Studies on Amazon – Take 2
In July I wrote about an Amazon Kindle version of my Data Center Design Case Studies book and complained about their royalties model. Someone quickly pointed out how to adapt to their system: split the book into multiple volumes and charge $9.99 for each.
It took me months to get there, but the first two volumes are finally on Amazon:
Read more ...