Multihoming Cannot Be Solved within a Network
Henk made an interesting comment that finally triggered me to organize my thoughts about network-level host multihoming1:
The problems I see with routing are: [hard stuff], host multihoming, [even more hard stuff]. To solve some of those, we should have true identifier/locator separation. Not an after-thought like LISP, but something built into the layer-3 addressing architecture.
Proponents of various clean-slate (RINA) and pimp-my-Internet (LISP) approaches are quick to point out how their solution solves multihoming. I might be missing something, but it seems like that problem cannot be solved within the network.
Multihoming Cannot Be Solved within a Network
Henk made an interesting comment that finally triggered me to organize my thoughts about network-level host multihoming1:
The problems I see with routing are: [hard stuff], host multihoming, [even more hard stuff]. To solve some of those, we should have true identifier/locator separation. Not an after-thought like LISP, but something built into the layer-3 addressing architecture.
Proponents of various clean-slate (RINA) and pimp-my-Internet (LISP) approaches are quick to point out how their solution solves multihoming. I might be missing something, but it seems like that problem cannot be solved within the network.
A Kubernetes Primer
As Kubernetes continues to gain popularity, engineers have to know how Kubernetes works, and why it might make sense in their environment. What benefits does Kubernetes have in your environment and ultimately, what do technologies like containerization do for organizations. In this blog post, I’ll provide some basic background on containers and Kubernetes, and some […]
The post A Kubernetes Primer appeared first on Packet Pushers.
The Hedge 155: DNS Deployment in Real Life with Andreas Taudte
Network engineers normally use and support DNS as a service, but don’t tend to deploy, manage, and interact with DNS servers at an application level. For this episode of the Hedge, Andreas Taudte joins Tom Ammon and Russ White to discuss the many lessons learned from planning and deploying DNS as a service.
Networking and Security in VMware Cloud on AWS: New Video Series
VMware Cloud on AWS provides a range of powerful security and networking capabilities. From enforcing granular security rules for traffic using NSX Advanced Firewall, to managing complex routes between your AWS environment and external resources via Transit Connect, there’s no shortage of tools available for supporting your business’s unique requirements when you leverage AWS as part of a VMware-based SDDC strategy.
To showcase some of the most powerful security and networking features of VMware Cloud on AWS, we’ve prepared a set of short videos where Ron Fuller, Senior Technical Product Manager at VMware, explains how the features work and how to get started using them. If you’re looking for a quick introduction to key security and networking concepts that impact VMware Cloud on AWS workloads, these videos are for you.
Keep reading for links to the videos, along with summaries of what you’ll learn from each one. We recommend watching the videos in order because Ron explains core Software-Defined Data Center (SDDC) concepts as he progresses through the videos, although viewers who are already familiar with SDDC may prefer to skip ahead.
Video 1: Introduction to Security Tools in VMware Cloud on AWS
Network and Services Technologies Fuel Personalization Push for Sports Venues
Data-driven decisions help operators optimize current and new processes to profile and monetize the fan.Day Two Cloud 172: Lock Down Access With Zero Standing Privilege (Sponsored)
On today’s Day Two Cloud we talk through the idea of “zero standing privilege”. Zero standing privilege is an evolution of credentials management that goes beyond always-on usernames and passwords and more advanced forms of privileged access management to help lock down access to sensitive systems. Our sponsor is strongDM and our guest is Britt Crawford, Director of Product.
The post Day Two Cloud 172: Lock Down Access With Zero Standing Privilege (Sponsored) appeared first on Packet Pushers.
Day Two Cloud 172: Lock Down Access With Zero Standing Privilege (Sponsored)
On today’s Day Two Cloud we talk through the idea of “zero standing privilege”. Zero standing privilege is an evolution of credentials management that goes beyond always-on usernames and passwords and more advanced forms of privileged access management to help lock down access to sensitive systems. Our sponsor is strongDM and our guest is Britt Crawford, Director of Product.RDMA network visibility
The Remote Direct Memory Access (RDMA) data shown in the chart was gathered from The International Conference for High Performance Computing, Networking, Storage, and Analysis (SC22) being held this week in Dallas. The conference network, SCinet, is described as the fastest and most powerful network on Earth, connecting the SC community to the world. Resilient Distributed Processing and Reconfigurable Networks is one of the demonstrations using SCinet - Location: Booth 2847 (StarLight). Planned SC22 focus is on RDMA enabled data movement and dynamic network control.- RDMA Tbps performance over global distance for timely Terabyte bulk data transfers (goal << 1 min Tbyte transfer on N by 400G network).
- Dynamic shifting of processing and network resources from on location/path/system to another (in response to demand and availability).
UPDATE Supercloud SET status = ‘open alpha’ WHERE product = ‘D1’;


In May 2022, we announced our quest to simplify databases – building them, maintaining them, integrating them. Our goal is to empower you with the tools to run a database that is powerful, scalable, with world-beating performance without any hassle. And we first set our sights on reimagining the database development experience for every type of user – not just database experts.
Over the past couple of months, we’ve been working to create just that, while learning some very important lessons along the way. As it turns out, building a global relational database product on top of Workers pushes the boundaries of the developer platform to their absolute limit, and often beyond them, but in a way that’s absolutely thrilling to us at Cloudflare. It means that while our progress might seem slow from outside, every improvement, bug fix or stress test helps lay down a path for all of our customers to build the world’s most ambitious serverless application.
However, as we continue down the road to making D1 production ready, it wouldn’t be “the Cloudflare way” unless we stopped for feedback first – even though it’s not quite finished yet. In the spirit of Developer Week, there is Continue reading
Bringing authentication and identification to Workers through Mutual TLS
We’re excited to announce that Workers will soon be able to send outbound requests through a mutually authenticated channel via mutual TLS authentication!
When making outbound requests from a Worker, TLS is always used on the server side, so that the client can validate that the information is being sent to the right destination. But in the same way, the server may want to authenticate the client to ensure that the request is coming from an authorized client. This two-way street of authentication is called Mutual TLS. In this blog, we’re going to talk through the importance of mutual TLS authentication, what it means to use mutual TLS within Workers, and how in a few months you’ll be able to use it to send information through an authenticated channel — adding a layer of security to your application!
mTLS between Cloudflare and an Origin
Mutual TLS authentication works by having a server validate the client certificate against a CA. If the validation passes then the server knows that it’s the right client and will let the request go through. If the validation fails or if a client certificate is not presented then the server can choose to drop the request.
Xata Workers: client-side database access without client-side secrets


We’re excited to have Xata building their serverless functions product – Xata Workers – on top of Workers for Platforms. Xata Workers act as middleware to simplify database access and allow their developers to deploy functions that sit in front of their databases. Workers for Platforms opens up a whole suite of use cases for Xata developers all while providing the security, scalability and performance of Cloudflare Workers.
Now, handing it over to Alexis, a Senior Software Engineer at Xata to tell us more.
Introduction
In the last few years, there's been a rise of Jamstack, and new ways of thinking about the cloud that some people call serverless or edge computing. Instead of maintaining dedicated servers to run a single service, these architectures split applications in smaller services or functions.
By simplifying the state and context of our applications, we can benefit from external providers deploying these functions in dozens of servers across the globe. This architecture benefits the developer and user experience alike. Developers don’t have to manage servers, and users don’t have to experience latency. Your application simply scales, even if you receive hundreds of thousands of unexpected visitors.
When it comes to databases though, we still Continue reading
Automate an isolated browser instance with just a few lines of code
If you’ve ever created a website that shows any kind of analytics, you’ve probably also thought about adding a “Save Image” or “Save as PDF” button to store and share results. This isn’t as easy as it seems (I can attest to this firsthand) and it’s not long before you go down a rabbit hole of trying 10 different libraries, hoping one will work.
This is why we’re excited to announce a private beta of the Workers Browser Rendering API, improving the browser automation experience for developers. With browser automation, you can programmatically do anything that a user can do when interacting with a browser.
The Workers Browser Rendering API, or just Rendering API for short, is our out-of-the-box solution for simplifying developer workflows, including capturing images or screenshots, by running browser automation in Workers.
Browser automation, everywhere
As with many of the best Cloudflare products, Rendering API was born out of an internal need. Many of our teams were setting up or wanted to set up their own tools to perform what sounds like an incredibly simple task: taking automated screenshots.
When gathering use cases, we realized that much of what our internal teams wanted would also be useful Continue reading
Making static sites dynamic with Cloudflare D1

Introduction

There are many ways to store data in your applications. For example, in Cloudflare Workers applications, we have Workers KV for key-value storage and Durable Objects for real-time, coordinated storage without compromising on consistency. Outside the Cloudflare ecosystem, you can also plug in other tools like NoSQL and graph databases.
But sometimes, you want SQL. Indexes allow us to retrieve data quickly. Joins enable us to describe complex relationships between different tables. SQL declaratively describes how our application's data is validated, created, and performantly queried.
D1 was released today in open alpha, and to celebrate, I want to share my experience building apps with D1: specifically, how to get started, and why I’m excited about D1 joining the long list of tools you can use to build apps on Cloudflare.
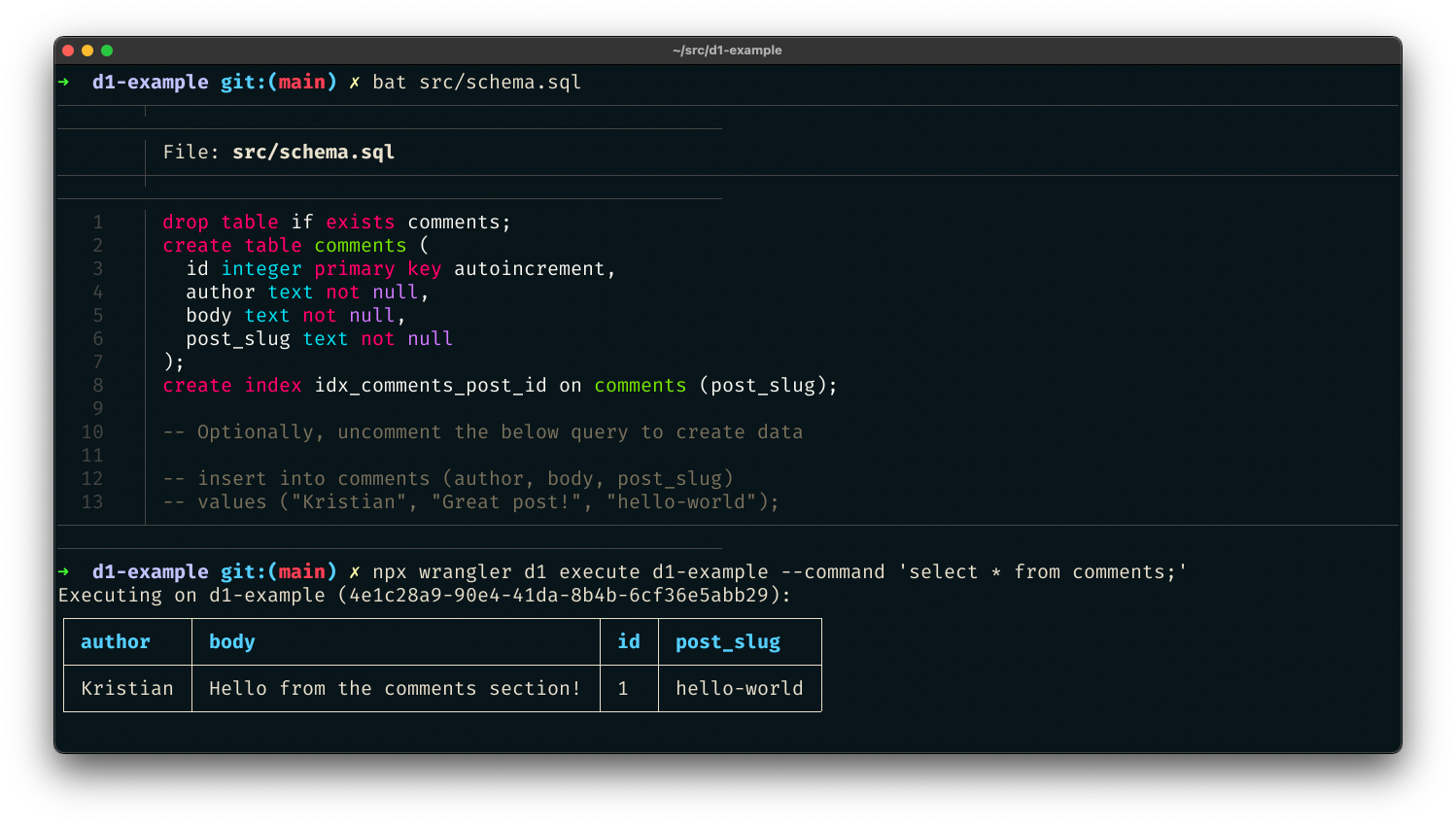
D1 is remarkable because it's an instant value-add to applications without needing new tools or stepping out of the Cloudflare ecosystem. Using wrangler, we can do local development on our Workers applications, and with the addition of D1 in wrangler, we can now develop proper stateful applications locally as well. Then, when it's time to deploy the application, wrangler allows us to both access and execute commands to Continue reading
Iteration isn’t just for code: here are our latest API docs

We’re excited to share that the next iteration of Cloudflare’s API reference documentation is now available. The new docs standardize our API content and improve the overall developer experience for interacting with Cloudflare’s API.
Why does API documentation matter?
Everyone talks about how important APIs are, but not everyone acknowledges the critical role that API documentation plays in an API’s usability. Throwing docs together is easy. Getting them right is harder.
At Cloudflare, we try to meet our users where they are. For the majority of customers, that means providing clear, easy-to-use products in our dashboard. But developers don’t always want what our dashboard provides. Some developers prefer to use a CLI or Wrangler to have a higher level of control over what’s happening with their Cloudflare products. Others want more customization and deeper ties into their company’s internal applications. Some want all the above.

A developer’s job is to create, debug, and optimize code - whether that’s an application, interface, database, etc. - as efficiently as possible and ensure that code runs as efficiently as possible. APIs enable that efficiency through automation. Let’s say a developer wants to run a cache purge every time content is updated on their Continue reading


