Who Needs a Network Digital Twin and Why
Organizations with hybrid, multi-cloud environments that require many operators across disciplines will reap the greatest rewards today from using a digital twin.HS033 Getting real about LEO Space Networking
Should LEO space networks be part of your network ? Are there common questions about using and designing for them ? What should be expecting from your telco ?
The post HS033 Getting real about LEO Space Networking appeared first on Packet Pushers.
HS033 Getting real about LEO Space Networking
Should LEO space networks be part of your network ? Are there common questions about using and designing for them ? What should be expecting from your telco ?EVPN/MPLS Bridging Forwarding Model
Most networking engineers immediately think about VXLAN and data center switches when they hear about EVPN. While that’s the most hyped use case, EVPN standardization started in 2012 as a layer-2 VPN solution on top of MPLS transport trying to merge the best of VPLS and MPLS/VPN worlds.
If you want to understand how any technology works, and what its quirks are, you have to know how it was designed to be used. In this blog post we’ll start that journey exploring the basics of EVPN used in a simple MLPS network with three PE-routers:
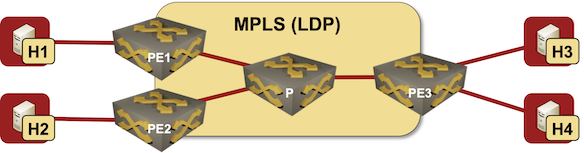
Lab topology
EVPN/MPLS Bridging Forwarding Model
Most networking engineers immediately think about VXLAN and data center switches when they hear about EVPN. While that’s the most hyped use case, EVPN standardization started in 2012 as a layer-2 VPN solution on top of MPLS transport trying to merge the best of VPLS and MPLS/VPN worlds.
If you want to understand how any technology works, and what its quirks are, you have to know how it was designed to be used. In this blog post we’ll start that journey exploring the basics of EVPN used in a simple MLPS network with three PE-routers:

Lab topology
Automate Calico Cloud and EKS cluster integration using AWS Control Tower
Productive, scalable, and cost-effective, cloud infrastructure empowers innovation and faster deliverables. It’s a no-brainer why organizations are migrating to the cloud and containerizing their applications. As businesses scale their cloud infrastructure, they cannot be bottlenecked by security concerns. One way to release these bottlenecks and free up resources is by using automation.
What if you could automate the deployment and integration of your container security services with your cluster’s environment?
In a joint blog post with AWS Marketplace, AWS Sr. Cloud Application Architect, Deepak Sihag, joins Tigera’s Technical Marketing Engineer, Joseph Yostos, to walk you through the process of activating, deploying, and configuring Calico Cloud in your AWS Control Tower environment. And of course, how to automate the process of connecting Calico Cloud to your EKS cluster.
Blog highlights
Aside from showing you how you can fully leverage the preconfigured resources of AWS Control Tower, the solution walkthrough also highlights:
- Event-driven automation to connect an EKS cluster with Calico Cloud
- AWS CloudFormation deployment
- Detailed runthrough of prerequisite configurations
- Step-by-step guide on how to automate Calico Cloud and EKS cluster integration using AWS Control Tower
- How to clean up your account to avoid incurring costs
Why read the blog?
As the Continue reading
Advanced OOBM Tactics Simplify and Reinforce Remote Data Center Access
Modern out-of-band management (OOBM) platforms offer a wealth of new features to aid administrators with zero-touch deployments and robust, failure-resistant remote data center connectivity.Repost: What’s Wrong with Network Automation
Responding to my Infrastructure as Code Sounds Scary blog post, Deepak Arora posted an interesting (and unfortunately way too accurate) list of challenges you might encounter when trying to introduce network automation in an enterprise environment.
He graciously allowed me to repost his thoughts on my blog.
Why don’t we agree on that :
Repost: What’s Wrong with Network Automation
Responding to my Infrastructure as Code Sounds Scary blog post, Deepak Arora posted an interesting (and unfortunately way too accurate) list of challenges you might encounter when trying to introduce network automation in an enterprise environment.
He graciously allowed me to repost his thoughts on my blog.
Why don’t we agree on that :
What we served up for the last Birthday Week before we’re a teenager


Almost a teen. With Cloudflare’s 12th birthday last Tuesday, we’re officially into our thirteenth year. And what a birthday we had!
36 announcements ranging from SIM cards to post quantum encryption via hardware keys and so much more. Here’s a review of everything we announced this week.
Monday
| What | In a sentence… |
|---|---|
| The First Zero Trust SIM | We’re bringing Zero Trust security controls to the humble SIM card, rethinking how mobile device security is done, with the Cloudflare SIM: the world’s first Zero Trust SIM. |
| Securing the Internet of Things | We’ve been defending customers from Internet of Things botnets for years now, and it’s time to turn the tides: we’re bringing the same security behind our Zero Trust platform to IoT. |
| Bringing Zero Trust to mobile network operators | Helping bring the power of Cloudflare’s Zero Trust platform to mobile operators and their subscribers. |
Tuesday
| What | In a sentence… |
|---|---|
| Workers Launchpad | Leading venture capital firms to provide up to $1.25 BILLION to back startups built on Cloudflare Workers. |
| Startup Plan v2.0 | Increasing the scope, eligibility and products we include under our Startup Plan, enabling more developers and startups to build the next big thing on top of Cloudflare. |
| workerd: Continue reading |