Announcing Turnstile, a user-friendly, privacy-preserving alternative to CAPTCHA

Today, we’re announcing the open beta of Turnstile, an invisible alternative to CAPTCHA. Anyone, anywhere on the Internet, who wants to replace CAPTCHA on their site will be able to call a simple API, without having to be a Cloudflare customer or sending traffic through the Cloudflare global network. Sign up here for free.
There is no point in rehashing the fact that CAPTCHA provides a terrible user experience. It's been discussed in detail before on this blog, and countless times elsewhere. The creator of the CAPTCHA has even publicly lamented that he “unwittingly created a system that was frittering away, in ten-second increments, millions of hours of a most precious resource: human brain cycles.” We hate it, you hate it, everyone hates it. Today we’re giving everyone a better option.
Turnstile is our smart CAPTCHA alternative. It automatically chooses from a rotating suite of non-intrusive browser challenges based on telemetry and client behavior exhibited during a session. We talked in an earlier post about how we’ve used our Managed Challenge system to reduce our use of CAPTCHA by 91%. Now anyone can take advantage of this same technology to stop using CAPTCHA on their own site.
UX Continue reading
Monitor your own network with free network flow analytics from Cloudflare


As a network engineer or manager, answering questions about the traffic flowing across your infrastructure is a key part of your job. Cloudflare built Magic Network Monitoring (previously called Flow Based Monitoring) to give you better visibility into your network and to answer questions like, “What is my network’s peak traffic volume? What are the sources of that traffic? When does my network see that traffic?” Today, Cloudflare is excited to announce early access to a free version of Magic Network Monitoring that will be available to everyone. You can request early access by filling out this form.
Magic Network Monitoring now features a powerful analytics dashboard, self-serve configuration, and a step-by-step onboarding wizard. You’ll have access to a tool that helps you visualize your traffic and filter by packet characteristics including protocols, source IPs, destination IPs, ports, TCP flags, and router IP. Magic Network Monitoring also includes network traffic volume alerts for specific IP addresses or IP prefixes on your network.
Making Network Monitoring easy
Magic Networking Monitoring allows customers to collect network analytics without installing a physical device like a network TAP (Test Access Point) or setting up overly complex remote monitoring systems. Our product works Continue reading
Introducing Cloudflare’s free Botnet Threat Feed for service providers

We’re pleased to introduce Cloudflare’s free Botnet Threat Feed for Service Providers. This includes all types of service providers, ranging from hosting providers to ISPs and cloud compute providers.
This feed will give service providers threat intelligence on their own IP addresses that have participated in HTTP DDoS attacks as observed from the Cloudflare network — allowing them to crack down on abusers, take down botnet nodes, reduce their abuse-driven costs, and ultimately reduce the amount and force of DDoS attacks across the Internet. We’re giving away this feed for free as part of our mission to help build a better Internet.
Service providers that operate their own IP space can now sign up to the early access waiting list.
Cloudflare’s unique vantage point on DDoS attacks
Cloudflare provides services to millions of customers ranging from small businesses and individual developers to large enterprises, including 29% of Fortune 1000 companies. Today, about 20% of websites rely directly on Cloudflare’s services. This gives us a unique vantage point on tremendous amounts of DDoS attacks that target our customers.
DDoS attacks, by definition, are distributed. They originate from botnets of many sources — in some cases, from hundreds of thousands to millions Continue reading
Private by design: building privacy-preserving products with Cloudflare’s Privacy Edge


When Cloudflare was founded, our value proposition had three pillars: more secure, more reliable, and more performant. Over time, we’ve realized that a better Internet is also a more private Internet, and we want to play a role in building it.
User awareness and expectations of and for privacy are higher than ever, but we believe that application developers and platforms shouldn’t have to start from scratch. We’re excited to introduce Privacy Edge – Code Auditability, Privacy Gateway, Privacy Proxy, and Cooperative Analytics – a suite of products that make it easy for site owners and developers to build privacy into their products, by default.
Building network-level privacy into the foundations of app infrastructure
As you’re browsing the web every day, information from the networks and apps you use can expose more information than you intend. When accumulated over time, identifiers like your IP address, cookies, browser and device characteristics create a unique profile that can be used to track your browsing activity. We don’t think this status quo is right for the Internet, or that consumers should have to understand the complex ecosystem of third-party trackers to maintain privacy. Instead, we’ve been working on technologies that encourage and enable Continue reading
We’ve shipped so many products the Cloudflare dashboard needed its own search engine


Today we’re proud to announce our first release of quick search for the Cloudflare dashboard, a beta version of our first ever cross-dashboard search tool to help you navigate our products and features. This first release is now available to a small percentage of our customers. Want to request early access? Let us know by filling out this form.
What we’re launching
We’re launching quick search to speed up common interactions with the Cloudflare dashboard. Our dashboard allows you to configure Cloudflare’s full suite of products and features, and quick search gives you a shortcut.
To get started, you can access the quick search tool from anywhere within the Cloudflare dashboard by clicking the magnifying glass button in the top navigation, or hitting Ctrl + K on Linux and Windows or ⌘ + K on Mac. (If you find yourself forgetting which key combination it is just remember that it’s ⌘ or Ctrl-K-wik.) From there, enter a search term and then select from the results shown below.
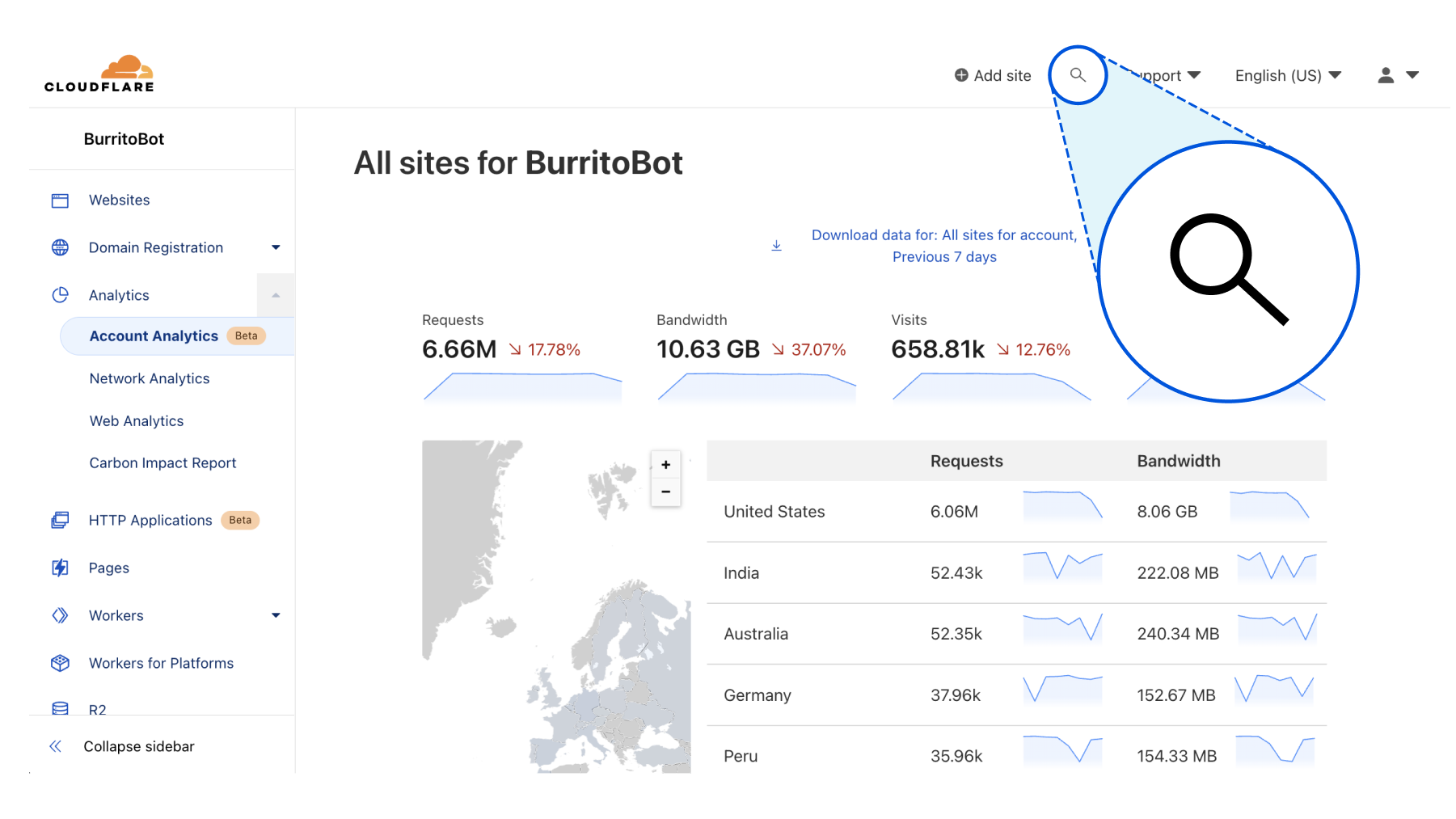
Current supported functionality
What functionality will Continue reading
Combining MLAG Clusters with VXLAN Fabric
In the previous MLAG Deep Dive blog posts we discussed the innards of a standalone MLAG cluster. Now let’s see what happens when we connect such a cluster to a VXLAN fabric – we’ll use our standard MLAG topology and add a VXLAN transport underlay to it with another switch connected to the other end of the underlay network.
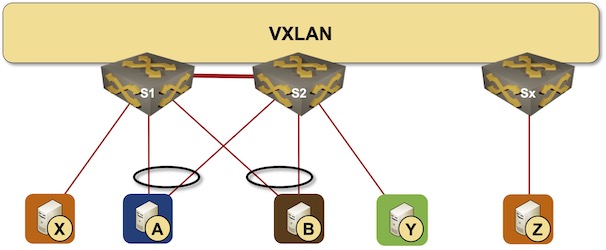
MLAG cluster connected to a VXLAN fabric
Combining MLAG Clusters with VXLAN Fabric
In the previous MLAG Deep Dive blog posts we discussed the innards of a standalone MLAG cluster. Now let’s see what happens when we connect such a cluster to a VXLAN fabric – we’ll use our standard MLAG topology and add a VXLAN transport underlay to it with another switch connected to the other end of the underlay network.

MLAG cluster connected to a VXLAN fabric
Revisiting BGP EVPN VXLAN to the hosts with SR Linux 22.6.3
Featuring Netlab 1.3.1 and FRR 8.3.1

At the beginning of this year I wrote about my SR Linux BGP EVPN adventures, with considerations around underlay and overlay design and the illustrious iBGP-over-eBGP approach. Some readers may have noticed a resemblance to the constellation of Ursa Major — the Big Bear: A reference to our friends at CloudBear, a recent SR Linux customer.
Fast forward to September 2022 and we now have SR Linux 22.6.3 with some features I have been waiting for, like (e)BGP Unnumbered. From my side, I have been working with the open source community to extend support for tools like Netlab (formerly Netsim-tools), Containerlab and FRR to enable sophisticated and advanced network topologies using truly open source tools and components.
New features and changes
The issue of running BGP to Linux hosts using FRR popped up in several discussions. Though technically possible, it can be challenging to configure, and there are many design variations with implications that aren’t always obvious. To enable simple experimentation and quick design iterations, I decided to help out by extending Netlab with VLAN, VXLAN and VRF support for FRR. I also made some changes to Continue reading
Service Mesh and Ingress In Kubernetes: Lesson 6 – Consul Service Mesh And App Installation – Video
Continuing with examples of installing a service mesh, this video walks through deploying the Consul mesh. Host Michael Levan brings his background in system administration, software development, and DevOps to this video series. He has Kubernetes experience as both a developer and infrastructure engineer. He’s also a consultant and Pluralsight author, and host of the […]
The post Service Mesh and Ingress In Kubernetes: Lesson 6 – Consul Service Mesh And App Installation – Video appeared first on Packet Pushers.
Why Connectivity Makes Work From Home a Work in Progress
Residences can require business-class access services to support greater productivity, broadband bandwidth for collaboration, and robust security to better protect the expanded enterprise network.What is new in Calico v3.24
A couple of weeks ago, TIgera engineers released the new version of Calico, as part of a community effort to drive cloud security and networking even further. But before I begin diving into the details of this new release, I want to first spotlight a few of our community members who have merged their contributions to Calico Open Source for the first time.
Shout out to @agaffney for adding configurable labels and annotations to the tigera-operator deployment in Helm charts.
Shout out to @backjo for improving the Calico Windows installation script and adding support for IMDSv2 in AWS EC2 data retrieval.
Shout out to @EugenMayer for pointing out an improvement for the calicoctl binary in a Helm chart installation and @lou-lan for making it happen.
Shout out to @joskuijpers for informing the community about the outdated ipset package in the calico-node ARM64 image and @ScOut3R for updating it.
Shout out to @juanfresia for contributing changes to enable Calico to run without programming the route table, useful when integrating with other routing mechanisms.
Shout out to @muff1nman, who added Wireguard traffic to the Calico failsafe ports, allowing us to confidently apply network security policies without worrying about accidentally cutting off Continue reading
The Redesign of BPA Platforms is Long Overdue
The challenge for IT architects, operations personnel, application developers, and business users is that all processes and workflows are impacted if the platform or any of its services go down or are taken offline.Cloudflare named a Leader in WAF by Forrester


Forrester has recognised Cloudflare as a Leader in The Forrester Wave™: Web Application Firewalls, Q3 2022 report. The report evaluated 12 Web Application Firewall (WAF) providers on 24 criteria across current offering, strategy and market presence.
You can register for a complimentary copy of the report here. The report helps security and risk professionals select the correct offering for their needs.
We believe this achievement, along with recent WAF developments, reinforces our commitment and continued investment in the Cloudflare Web Application Firewall (WAF), one of our core product offerings.
The WAF, along with our DDoS Mitigation and CDN services, has in fact been an offering since Cloudflare’s founding, and we could not think of a better time to receive this recognition: Birthday Week.
We’d also like to take this opportunity to thank Forrester.
Leading WAF in strategy
Cloudflare received the highest score of all assessed vendors in the strategy category. We also received the highest possible scores in 10 criteria, including:
- Innovation
- Management UI
- Rule creation and modification
- Log4Shell response
- Incident investigation
- Security operations feedback loops
According to Forrester, “Cloudflare Web Application Firewall shines in configuration and rule creation”, “Cloudflare stands out for its active online user community and its Continue reading
Leading venture capital firms to provide up to $1.25 BILLION to back startups built on Cloudflare Workers

This post is also available in 简体中文, 日本語, Français, Deutsch and Español.

From our earliest days, Cloudflare has stood for helping build a better Internet that’s accessible to all. It’s core to our mission that anyone who wants to start building on the Internet should be able to do so easily, and without the barriers of prohibitively expensive or difficult to use infrastructure.
Nowhere is this philosophy more important – and more impactful to the Internet – than with our developer platform, Cloudflare Workers. Workers is, quite simply, where developers and entrepreneurs start on Day 1. It’s a full developer platform that includes cloud storage; website hosting; SQL databases; and of course, the industry’s leading serverless product. The platform’s ease-of-use and accessible pricing (all the way down to free) are critical in advancing our mission. For startups, this translates into fast, easy deployment and iteration, that scales seamlessly with predictable, transparent and cost-effective pricing. Building a great business from scratch is hard enough – we ought to know! – and so we’re aiming to take all the complexity out of your application infrastructure.
Announcing the Workers Launchpad funding program
Today, we’re taking things a step further and Continue reading
Introducing workerd: the Open Source Workers runtime
Today I'm proud to introduce the first beta release of workerd, the JavaScript/Wasm runtime based on the same code that powers Cloudflare Workers. workerd is Open Source under the Apache License version 2.0.
workerd shares most of its code with the runtime that powers Cloudflare Workers, but with some changes designed to make it more portable to other environments. The name "workerd" (pronounced "worker dee") comes from the Unix tradition of naming servers with a "-d" suffix standing for "daemon". The name is not capitalized because it is a program name, which are traditionally lower-case in Unix-like environments.
What it's for
Self-hosting Workers
workerd can be used to self-host applications that you'd otherwise run on Cloudflare Workers. It is intended to be a production-ready web server for this purpose. workerd has been designed to be unopinionated about hosting environments, so that it should fit nicely into whatever server/VM/container hosting and orchestration system you prefer. It's just a web server.
Workers has always been based on standardized APIs, so that Continue reading
D1: our quest to simplify databases


When we announced D1 in May of this year, we knew it would be the start of something new – our first SQL database with Cloudflare Workers. Prior to D1 we’ve announced storage options like KV (key-value store), Durable Objects (single location, strongly consistent data storage) and R2 (blob storage). But the question always remained “How can I store and query relational data without latency concerns and an easy API?”
The long awaited “Cloudflare Database'' was the true missing piece to build your application entirely on Cloudflare’s global network, going from a blank canvas in VSCode to a full stack application in seconds. Compatible with the popular SQLite API, D1 empowers developers to build out their databases without getting bogged down by complexity and having to manage every underlying layer.
Since our launch announcement in May and private beta in June, we’ve made great strides in building out our vision of a serverless database. With D1 still in private beta but an open beta on the horizon, we’re excited to show and tell our journey of building D1 and what’s to come.
The D1 Experience
We knew from Cloudflare Workers feedback that using Wrangler as the mechanism to create Continue reading
Build your next startup on Cloudflare with our comprehensive Startup Plan, v2.0


Starting a business is hard. And we know that the first few years of your business are crucial to your success.
Cloudflare’s Startup Plan is here to help.
Last year, we piloted a program to a select group of startups for free, with a selection of products that are very high leverage for young startups, early in their product development, like Workers, Stream, and Zero Trust.
Over the past year, startup founders repeatedly wrote into [email protected], and most of these emails followed one of 2 patterns:
- A startup would like to request additional products that are not a part of the startup plan, often Workers KV, Pages, Cloudflare for SaaS, R2, Argo, etc.
- A startup that is not a part of any accelerator program but would like to get on the startup plan.
Based on this feedback, we are thrilled to announce that today we will be increasing the scope of the program to also include popularly requested products! Beyond that, we’re also super excited to be broadening the eligibility criteria, so more startups can qualify for the plan.
What does the Cloudflare Startup Plan include?
There’s a lot of additional value that’s in the latest version of Continue reading
Dynamic URL redirects: 301 to the future
The Internet is a dynamic place. Websites are constantly changing as technologies and business practices evolve. What was front-page news is quickly moved into a sub-directory. To ensure website visitors continue to see the correct webpage even if it has been moved, administrators often implement URL redirects.
A URL redirect is a mapping from one location on the Internet to another, effectively telling the visitor's browser that the location of the page has changed, and where they can now find it. This is achieved by providing a virtual ‘link’ between the content’s original and new location.
URL Redirects have typically been implemented as Page Rules within Cloudflare, however Page Rules only match on the URL, rather than other elements such as the visitor's source country or preferred language. This limitation meant customers with a need for more dynamic URL redirects had to implement alternative solutions such Cloudflare Workers to achieve their goals.
To simplify the management of these more complex use cases we have created Dynamic Redirects. With Dynamic Redirects, users can redirect visitors to another webpage or website based upon hundreds of options such as the visitor's country of origin or language, without having to write a single line Continue reading