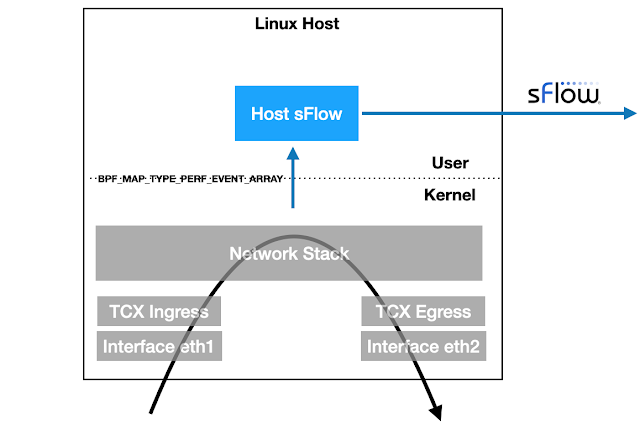
Linux packet sampling using eBPF
Linux 6.11+ kernels provide TCX attachment points for eBPF programs to efficiently examine packets as they ingress and egress the host. The latest version of the open source Host sFlow agent includes support for TCX packet sampling to stream industry standard sFlow telemetry to a central collector for network wide visibility, e.g. Deploy real-time network dashboards using Docker compose describes how to quickly set up a Prometheus database and use Grafana to build network dashboards.
static __always_inline void sample_packet(struct __sk_buff *skb, __u8 direction) {
__u32 key = skb->ifindex;
__u32 *rate = bpf_map_lookup_elem(&sampling, &key);
if (!rate || (*rate > 0 && bpf_get_prandom_u32() % *rate != 0))
return;
struct packet_event_t pkt = {};
pkt.timestamp = bpf_ktime_get_ns();
pkt.ifindex = skb->ifindex;
pkt.sampling_rate = *rate;
pkt.ingress_ifindex = skb->ingress_ifindex;
pkt.routed_ifindex = direction ? 0 : get_route(skb);
pkt.pkt_len = skb->len;
pkt.direction = direction;
__u32 hdr_len = skb->len < MAX_PKT_HDR_LEN ? skb->len : MAX_PKT_HDR_LEN;
if (hdr_len > 0 && bpf_skb_load_bytes(skb, 0, pkt.hdr, hdr_len) < 0)
return;
bpf_perf_event_output(skb, &events, BPF_F_CURRENT_CPU, &pkt, sizeof(pkt));
}
SEC("tcx/ingress")
int tcx_ingress(struct __sk_buff *skb) {
sample_packet(skb, 0);
return TCX_NEXT;
}
SEC("tcx/egress")
int tcx_egress(struct __sk_buff *skb) {
sample_packet(skb, 1);
return TCX_NEXT;
}
The sample.bpf.c file Continue reading
NB536: Fortinet FortiOS Goes Post-Quantum; Intel Scales Back Global Projects
Take a Network Break! In our Red Alert section we note that memory safety bugs bug Firefox and Thunderbird, and on-prem SharePoint instances are under attack. In tech news, Fortinet adds support for Post Quantum Cryptography in FortiOS, Cato Networks integrates Azure Virtual WANs to its SASE offering, and we weigh the pros and cons... Read more »Fun Reading: Who is LLM?
Is an LLM a stubborn donkey, a genie, or a slot machine (and why)? Find out in the Who is LLM? article by Martin Fowler.
HN789: How a Global Payments Processor Automates Firewall Changes at Scale
Adyen is a global payments processor whose primary business is providing payment services for merchants, retailers, and venues, as well as online payments. On today’s Heavy Networking we talk about a firewall automation project the company has undertaken. With dozens of change requests coming in every day that need to touch network and host firewalls,... Read more »TNO036: Bridging Networking and Security with Auvik (Sponsored)
Auvik is network management software that lets users monitor, manage, and troubleshoot their networks. On today’s sponsored episode we talk with Doug Murray, CEO; and John Harden, Director of Strategy & Technology Evangelism, both from Auvik, about the challenges facing today’s network operators. We look at the rise of the IT generalist, workloads and burnout,... Read more »ArubaCX: When BGP Soft Reconfiguration Becomes a No-Op
Changing an existing BGP routing policy is always tricky on platforms that apply line-by-line changes to device configurations (Cisco IOS and most other platforms claiming to have industry-standard CLI, with the notable exception of Arista EOS). The safest approach seems to be:
- Do not panic when the user makes changes to route maps and underlying filters (prefix lists, AS-path access lists, or community lists).
- Let the user decide when they’re done and process the BGP table with the new routing policy at that time.
The White House AI Action Plan: a new chapter in U.S. AI policy
On July 23, 2025, the White House unveiled its AI Action Plan (Plan), a significant policy document outlining the current administration's priorities and deliverables in Artificial Intelligence. This plan emerged after the White House received over 10,000 public comments in response to a February 2025 Request for Information (RFI). Cloudflare’s comments urged the White House to foster conditions for U.S. leadership in AI and support open-source AI, among other recommendations.
There is a lot packed into the three pillar, 28-page Plan.
Pillar I: Accelerate AI Innovation. Focuses on removing regulations, enabling AI adoption and developing, and ensuring the availability of open-source and open-weight AI models.
Pillar II: Build American AI Infrastructure. Prioritizes the construction of high-security data centers, bolstering critical infrastructure cybersecurity, and promoting Secure-by-Design AI technologies.
Pillar III: Lead in International AI Diplomacy and Security. Centers on providing America’s allies and partners with access to AI, as well as strengthening AI compute export control enforcement.
Each of these pillars outlines policy recommendations for various federal agencies to advance the plan’s overarching goals. There’s much that the Plan gets right. Below we cover a few parts of the Plan that we think are particularly important. Continue reading
Testing Arista AVD with GNS3 and EOS
Arista AVD (Architect, Validate, Deploy) – https://avd.arista.com – is a powerful tool that brings network architecture into the world of Infrastructure-as-Code. I wanted to try it out in a lab setting and see how it works in a non-standard environment. Since my go-to lab tool is GNS3 with Arista cEOS images — while the AVD […]
<p>The post Testing Arista AVD with GNS3 and EOS first appeared on IPNET.</p>
TL017: From the Mailbag: Yes and No, and Mid-Year Evaluations
Laura Santamaria opens the listener mailbag to answer questions, including how to say yes or no to leadership opportunities without tanking your career or trashing your work-life balance. She also explores the mid-year review process and offers tips for successful self-evaluation and paths to self-growth. Episode Links: The Line Between Management and IC Leadership –... Read more »Kubernetes Is Powerful, But Not Secure (at least not by default)
Kubernetes has transformed how we deploy and manage applications. It gives us the ability to spin up a virtual data center in minutes, scaling infrastructure with ease. But with great power comes great complexities, and in the case of Kubernetes, that complexity is security.
By default, Kubernetes permits all traffic between workloads in a cluster. This “allow by default” stance is convenient during development, and testing but it’s dangerous in production. It’s up to DevOps, DevSecOps, and cloud platform teams to lock things down.
To improve the security posture of a Kubernetes cluster, we can use microsegmentation, a practice that limits each workload’s network reach so it can only talk to the specific resources it needs. This is an essential security method in today’s cloud-native environments.
Why Is Microsegmentation So Hard?
We all understand that network policies can achieve microsegmentation; or in other words, it can divide our Kubernetes network model into isolated pieces. This is important since Kubernetes is usually used to provide multiple teams with their infrastructural needs or host multiple workloads for different tenants. With that, you would think network policies are first citizens of clusters. However, when we dig into implementing them, three operational challenges Continue reading
Hedge 275: Jevon’s Paradox
What is Jevon’s Paradox? Tom, Eyvonne, and Russ discuss how this famous paradox impact network engineering.
download
N4N034: OSPF Network Types
Ethan and Holly continue their OSPF journey this week with OSPF Network Types. They discuss the two main OSPF network types used today: the broadcast and point to point networks. They also explain designated routers, backup designated routers, and when those are used and why. Lastly they discuss some soft skills – knowing your vendor... Read more »Serverless Statusphere: a walk through building serverless ATProto applications on Cloudflare’s Developer Platform
Social media users are tired of losing their identity and data every time a platform shuts down or pivots. In the ATProto ecosystem — short for Authenticated Transfer Protocol — users own their data and identities. Everything they publish becomes part of a global, cryptographically signed shared social web. Bluesky is the first big example, but a new wave of decentralized social networks is just beginning. In this post I’ll show you how to get started, by building and deploying a fully serverless ATProto application on Cloudflare’s Developer Platform.
Why serverless? The overhead of managing VMs, scaling databases, maintaining CI pipelines, distributing data across availability zones, and securing APIs against DDoS attacks pulls focus away from actually building.
That’s where Cloudflare comes in. You can take advantage of our Developer Platform to build applications that run on our global network: Workers deploy code globally in milliseconds, KV provides fast, globally distributed caching, D1 offers a distributed relational database, and Durable Objects manage WebSockets and handle real-time coordination. Best of all, everything you need to build your serverless ATProto application is available on our free tier, so you can get started without spending a cent. You can find the code in Continue reading
TCG054: Framing Up the Future of Infrastructure-as-Code and User Experience with Cory O’Daniel
How is Infrastructure-as-Code (IaC) evolving? How does user experience fit in? Today on The Cloud Gambit, Cory O’Daniel, Co-Founder & CEO of Massdriver, lends his experience as a coder, architect, and founder to help us answer these questions. Cory also discusses what it was like building and funding a startup in the 2021-2022 market, the... Read more »NAN096: NautobotGPT – An AI Assistant for Network Automation
NautobotGPT is a new AI assistant for Nautobot that helps engineers with network automation, answers questions, recommends tooling, and delivers working code. We discuss the user experience of NautobotGPT with Matthew Schwen, Associate Director of Network Automation at Humana, CoFounder and CTO of PortalCX; and Brad Haas, VP of Professional Services at Network to Code.... Read more »Building Jetflow: a framework for flexible, performant data pipelines at Cloudflare
The Cloudflare Business Intelligence team manages a petabyte-scale data lake and ingests thousands of tables every day from many different sources. These include internal databases such as Postgres and ClickHouse, as well as external SaaS applications such as Salesforce. These tasks are often complex and tables may have hundreds of millions or billions of rows of new data each day. They are also business-critical for product decisions, growth plannings, and internal monitoring. In total, about 141 billion rows are ingested every day.
As Cloudflare has grown, the data has become ever larger and more complex. Our existing Extract Load Transform (ELT) solution could no longer meet our technical and business requirements. After evaluating other common ELT solutions, we concluded that their performance generally did not surpass our current system, either.
It became clear that we needed to build our own framework to cope with our unique requirements — and so Jetflow was born.
Over 100x efficiency improvement in GB-s:
Our longest running job with 19 billion rows was taking 48 hours using 300 GB of memory, and now completes in 5.5 hours using 4 GB of memory
We estimate that ingestion of Continue reading
Ultra Ethernet: Reinventing X.25
One should never trust the technical details published by the industry press, but assuming the Tomahawk Ultra puff piece isn’t too far off the mark, the new Broadcom ASIC (supposedly loosely based on emerging Ultra Ethernet specs):
- Uses Optimized Ethernet Header, replacing IP/UDP header with a 10-byte something (let’s call it session identifier)
- Makes Ethernet lossless with hop-by-hop retransmission/error recovery
- Uses credit-based flow control (the receiver continuously updates the sender about the amount of available space)
If you’re ancient enough, you might recognize #3 as part of Fibre Channel, #2 and #3 as part of IEEE 802.1 LLC2 (used by IBM to implement SNA over Token Ring and Ethernet), and all three as the fundamental ideas of X.25 that Broadcom obviously reinvented at 800 Gbps speeds, proving (yet again) RFC 1925 Rule 11.