Traffic Mirroring- Interesting one — AWS Advanced Networking
MEDIUM: <https://raaki-88.medium.com/traffic-mirroring-interesting-one-aws-advanced-networking-a7e41027c75>
What is Traffic Mirroring ? a. Used for Content Inspection,Threat Monitoring,Troubleshooting b. Can only be implemented with a Load Balancer c. Needs Elastic Fabric Adapter d. Flow logs capture mirrored traffic Answer is at the end of the post, feel free to skip it, I just did not want to make a spoiler residing just below the question
Traffic Mirroring is an awesome concept which can now be implemented with an AWS VPC. You can mirror the traffic and send packets to a EC2 instance or specific appliances for further processing.
- Used for Content Inspection, Threat Monitoring and Troubleshooting.
- An interesting as aspect is Packet-Format
*So when a packet gets mirrored it gets VXLAN encapsulated, end host/appliance should be able to decapsulate VXLAN header( we will see a PCAP ).
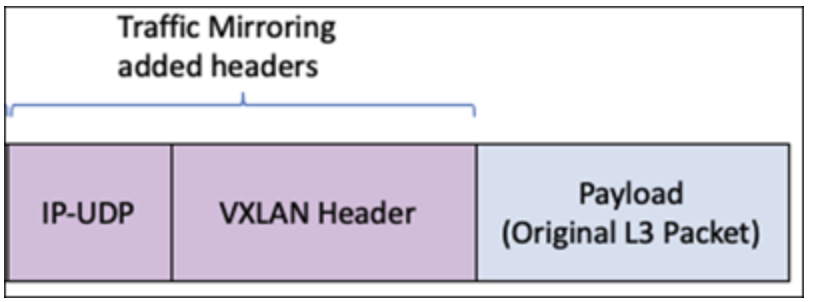
* Two encapsulations – outer GENEVE(from LB if used) and inner VX-LAN
- Connectivity options are good — Inter-region using Transit-VPC or VPC-peering, other post describing Transit VPC — https://towardsaws.com/transit-vpc-aws-advanced-networking-44ca09b80905
- 4 Things for Implementation
* Source (which should be monitored — Network Interface)
*Target (Destination of mirrored Traffic)
*Filter (What traffic types should be Continue reading
Getting Your CIO to Say Yes to Automation: Gluware LiveStream June 28, 2022 (3/7) – Video
Network engineers need to make a business case to get an automation project off the ground, and it needs to describe the benefits and value in language that non-techincal executives can understand. This video offers tips and a simple blueprint to help engineers make the case to CIOs. Host Drew Conry-Murray from the Packet Pushers […]
The post Getting Your CIO to Say Yes to Automation: Gluware LiveStream June 28, 2022 (3/7) – Video appeared first on Packet Pushers.
The Best Outcome Of Automation? Visibility
This post originally appeared on the Packet Pushers’ now-defunct Ignition site on October 28, 2019. I was recently asked a question about the best business outcome of automation. My immediate thought was improved speed of operations by mechanizing operational tasks, like automated software upgrades, creating VLANs, updating ACLs or routing, and so forth. This […]
The post The Best Outcome Of Automation? Visibility appeared first on Packet Pushers.
Friday Mobility Field Day Thoughts

I’m finishing up Mobility Field Day 7 this week and there’s been some exciting discussion here around a lot of technology. I think my favorite, and something I’m going to talk about more, is the continuing battle between 5G and Wi-Fi. However, there’s a lot going on that I figured I’d bring up to whet your appetite for the videos.
- What is mission critical? When you think about all the devices that are in your organization that absolutely must work every time what does that look like? And what are you prepared to do to make them work every time? If it’s a safety switch or some other kind of thing that prevents loss of life are you prepared to spend huge amounts of money to make it never fail?
- Operations teams don’t need easier systems. They need systems that remove complexity. The difference in those two things is subtle but important. Easier means that things are simplified to the point of almost being unusable. Think Apple Airport or even some Meraki devices. Whereas reduced complexity means that you’ve made the up front configuration easy but enabled the ability to configure other features in different places. Maybe that’s by giving Continue reading
Advizex: Automating Security Audits & Remediation with Gluware: LiveStream June 28, 2022 (2/7) – Video
Advizex, a reseller and Gluware customer, discusses how it uses Gluware for security audits and remediation with its clients. This includes network and device discovery, addressing configuration drift, and managing multiple vendors using the Gluware platform. Packet Pushers host Greg Ferro is joined by Michael Burns, Network Architect at Advizex to discuss real-world use cases. […]
The post Advizex: Automating Security Audits & Remediation with Gluware: LiveStream June 28, 2022 (2/7) – Video appeared first on Packet Pushers.
Ansible For Network Automation Lesson 6: Ansible Vault And Loops – Video
In this lesson on using Ansible for network automation, Josh VanDeraa looks at how to get started with Ansible Vault, re-using tasks in multiple playbooks with include_tasks, and leveraging loops in your playbooks. Josh has created a GitHub repo to store additional material, including links and documentation: https://github.com/jvanderaa/AnsibleForNetworkAutomation You can subscribe to the Packet Pushers’ […]
The post Ansible For Network Automation Lesson 6: Ansible Vault And Loops – Video appeared first on Packet Pushers.
Heavy Networking 638: Don’t Block DNS Over TCP
DNS is our subject on today's Heavy Networking. More specifically, DNS transport over TCP. We talk with John Kristoff, one of the forces behind RFC9210, which covers the operational requirements for DNS transport over TCP. This is not an esoteric document covering a tiny, nuanced DNS use case. Instead this doc will likely affect most of you listening, whether you’re a network operator or a name server operator. We talk with John about the implications of this RFC.
The post Heavy Networking 638: Don’t Block DNS Over TCP appeared first on Packet Pushers.
Heavy Networking 638: Don’t Block DNS Over TCP
DNS is our subject on today's Heavy Networking. More specifically, DNS transport over TCP. We talk with John Kristoff, one of the forces behind RFC9210, which covers the operational requirements for DNS transport over TCP. This is not an esoteric document covering a tiny, nuanced DNS use case. Instead this doc will likely affect most of you listening, whether you’re a network operator or a name server operator. We talk with John about the implications of this RFC.Setting Up Public-Private Keys For SSH Authentication
This post originally appeared on the Packet Pushers’ Ignition site on February 18, 2020. The more pedantic in the tech community argue about the merits of public-private key authentication vs. simple password authentication when logging into an SSH host. I have no strong opinion regarding your security posture when using one vs. the other. […]
The post Setting Up Public-Private Keys For SSH Authentication appeared first on Packet Pushers.
Working in public — our docs-as-code approach


Docs-as-code is an approach to writing and publishing documentation with the same tools and processes developers use to create code. This philosophy has become more popular in recent years, especially in tech companies. Automatic link checking is part of this process, which ensures that writer's changes are sound and safe to deploy. By setting the stage with a docs-as-code approach, technical writers can focus on what they do best: ensure that our readers get useful and accurate information that is easy to find, and our documentation speaks a single language.
Besides following a docs-as-code approach, at Cloudflare we handle our documentation changes in public, in our cloudflare-docs GitHub repository. Having our documentation open to external contributions has helped us improve our documentation over time — our community is great at finding issues! While we need to review these contributions and ensure that they fit our style guide and content strategy, the contributions provided by the Cloudflare community have been instrumental in making our documentation better every day. While Cloudflare helps build a better Internet, our community helps build better documentation.
Docs-as-code at Cloudflare
At Cloudflare, we follow a docs-as-code approach to create and publish product documentation in Developer Docs.
Such Continue reading
Worth Exploring: Akvorado Flow Collector and Visualizer
The results you can get when you know how to apply proper glue to a bunch of open-source tools never cease to amaze me. The latest entrant in that category: Akvorado, a Netflow/IPFIX collector and analyzer by Vincent Bernat.
Some of the sample graphs (shown in the GitHub repo) are not far off from those that knocked our socks off during the first Kentik Networking Field Day presentation. Definitely a tool worth exploring ;)
Worth Exploring: Akvorado Flow Collector and Visualizer
The results you can get when you know how to apply proper glue to a bunch of open-source tools never cease to amaze me. The latest entrant in that category: Akvorado, a Netflow/IPFIX collector and analyzer by Vincent Bernat.
Some of the sample graphs (shown in the GitHub repo) are not far off from those that knocked our socks off during the first Kentik Networking Field Day presentation. Definitely a tool worth exploring ;)
Kubernetes Unpacked 004: Pros And Cons Of Using Terraform With Kubernetes
On today's Kubernetes Unpacked podcast we explore tradeoffs that come with using Terraform to manage Kubernetes. My guest is Luke Orellana, an SRE who uses Kubernetes. He's also a HashiCorp Ambassador. We also discuss differences between managing VMs and Kubernetes, Kubernetes benefits including self-healing, and downsides such as dealing with the complexity that comes from containers and microservices.
The post Kubernetes Unpacked 004: Pros And Cons Of Using Terraform With Kubernetes appeared first on Packet Pushers.