Heavy Networking 623: Growing From Junior To Senior Engineer
Today's Heavy Networking is a roundtable conversation about career growth. Maybe your title is junior engineer, but you want to be a senior engineer. Be careful what you wish for! Maybe your title is junior but you feel you’re doing the job of a senior. Are you really? How would you justify this to your manager? We address these and other questions and issues including certs vs. experience, paying dues, the importance of communication skills, and more.
The post Heavy Networking 623: Growing From Junior To Senior Engineer appeared first on Packet Pushers.
Heavy Networking 623: Growing From Junior To Senior Engineer
Today's Heavy Networking is a roundtable conversation about career growth. Maybe your title is junior engineer, but you want to be a senior engineer. Be careful what you wish for! Maybe your title is junior but you feel you’re doing the job of a senior. Are you really? How would you justify this to your manager? We address these and other questions and issues including certs vs. experience, paying dues, the importance of communication skills, and more.Walmart to Hire 5K as Tech Job Market Stays Tight
Walmart Global Tech, the technology organization within the retail giant, says it will hire 5,000 tech pros in cybersecurity, software engineering, data science, and other specialities in 2022 after growing its numbers by 26% last year.Understanding Data Center Fabrics 05: Butterfly Scaling – Video
Episode of this series focuses on the butterfly fabric. While similar to a Clos fabric, the butterfly design is built around pods of switches. In this video, Russ White explains the differences in the butterfly design, physical limitations for ToR switches, how to scale the fabric to thousands of available ports without using chassis switches, […]
The post Understanding Data Center Fabrics 05: Butterfly Scaling – Video appeared first on Packet Pushers.
Embarking on a Cloud Journey? Don’t Forget to add an SD-WAN Multicloud Strategy!
When selecting a SD-WAN provider for their multicloud strategy, organizations must ensure it offers simplified connectivity to different cloud providers with automation, all while delivering the best user experience from anywhere.Ridiculously easy to use Tunnels
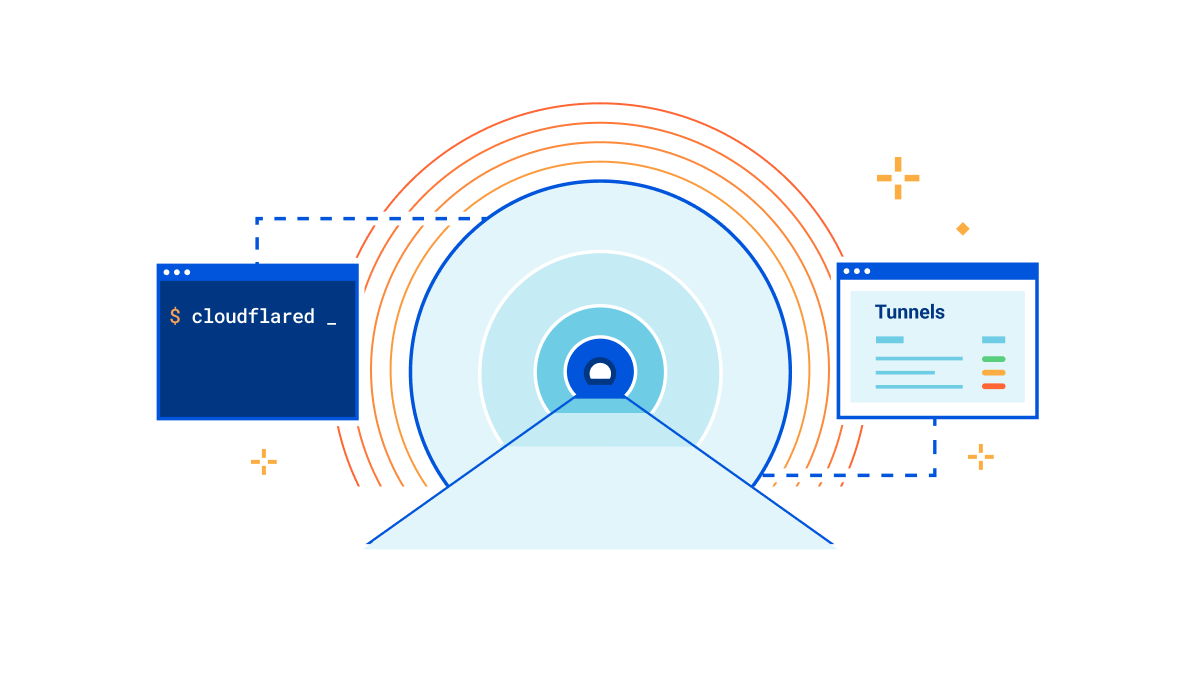
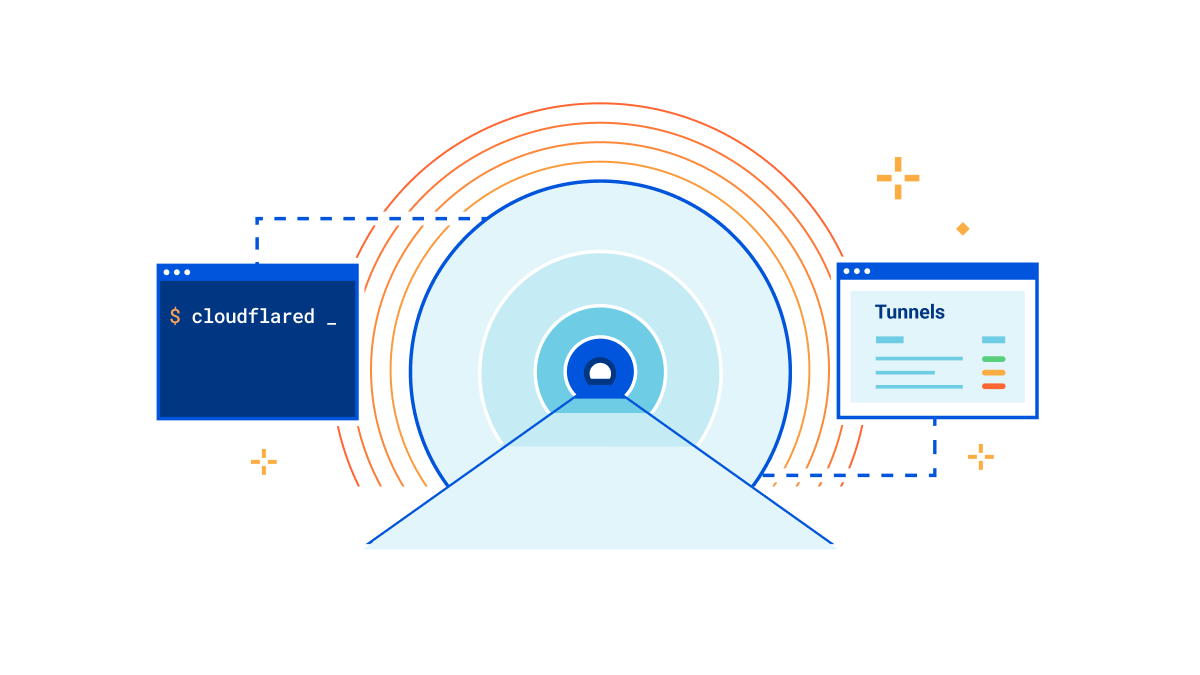
A little over a decade ago, Cloudflare launched at TechCrunch Disrupt. At the time, we talked about three core principles that differentiated Cloudflare from traditional security vendors: be more secure, more performant, and ridiculously easy to use. Ease of use is at the heart of every decision we make, and this is no different for Cloudflare Tunnel.
That’s why we’re thrilled to announce today that creating tunnels, which previously required up to 14 commands in the terminal, can now be accomplished in just three simple steps directly from the Zero Trust dashboard.
If you’ve heard enough, jump over to sign-up/teams to unplug your VPN and start building your private network with Cloudflare. If you’re interested in learning more about our motivations for this release and what we’re building next, keep scrolling.
Our connector
Cloudflare Tunnel is the easiest way to connect your infrastructure to Cloudflare, whether that be a local HTTP server, web services served by a Kubernetes cluster, or a private network segment. This connectivity is made possible through our lightweight, open-source connector, cloudflared. Our connector offers high-availability by design, creating four long-lived connections to two distinct data centers within Cloudflare’s network. This means that whether an individual Continue reading
Video: Managed SD-WAN Services
Should service providers offer managed SD-WAN services? According to Betteridge’s law of headlines, the answer is NO, and that’s exactly what I explained in a short video with the same name.
Turns out there’s not much to explain; even with my usual verbosity I was done in five minutes, so you might want to watch SD-WAN Technical Challenges as well.
Video: Managed SD-WAN Services
Should service providers offer managed SD-WAN services? According to Betteridge’s law of headlines, the answer is NO, and that’s exactly what I explained in a short video with the same name.
Turns out there’s not much to explain; even with my usual verbosity I was done in five minutes, so you might want to watch SD-WAN Technical Challenges as well.
How to secure Kubernetes at the infrastructure level: 10 best practices
Infrastructure security is something that is important to get right so that attacks can be prevented—or, in the case of a successful attack—damage can be minimized. It is especially important in a Kubernetes environment because, by default, a large number of Kubernetes configurations are not secure.
Securing Kubernetes at the infrastructure level requires a combination of host hardening, cluster hardening, and network security.
- Host hardening – Secures the servers or virtual machines on which Kubernetes is hosted
- Cluster hardening – Secures Kubernetes’s control plane components
- Network security – Ensures secure integration of the cluster with surrounding infrastructure
Let’s dive into each of these and look at best practices for securing both self-hosted and managed Kubernetes clusters.
Host hardening
There are many techniques that can be used to ensure a secure host. Here are three best practices for host hardening.
Use a modern immutable Linux distribution
If you have the flexibility to choose an operating system (i.e. your organization doesn’t standardize on one operating system across all infrastructure), use a modern immutable Linux distribution, such as Flatcar Container Linux or Bottlerocket. This type of operating system is specifically designed for containers and offers several benefits, including:
- Immutability – This type Continue reading
Hedge 123: Geoff Huston and the State of BGP
Another year of massive growth in the number and speed of connections to the global Internet—what is the impact on the global routing table? Goeff Huston joins Tom Ammon and Russ White to discuss the current state of the BGP table, the changes in the last several years, where things might go, and what all of this means. This is part 1 of a two part episode.
IPv6 Buzz 097: Selling An IPv6 Project To Your Organization
Today's IPv6 Buzz discusses how to sell IPv6 as a project. That is, doing the advocacy work in your organization to drive IPv6 adoption. We examine the business and technical arguments you can make, including tying IPv6 to initiatives around cloud, containers, and zero trust.
The post IPv6 Buzz 097: Selling An IPv6 Project To Your Organization appeared first on Packet Pushers.
IPv6 Buzz 097: Selling An IPv6 Project To Your Organization
Today's IPv6 Buzz discusses how to sell IPv6 as a project. That is, doing the advocacy work in your organization to drive IPv6 adoption. We examine the business and technical arguments you can make, including tying IPv6 to initiatives around cloud, containers, and zero trust.Cloudflare Radar’s new ASN pages


An AS, or Autonomous System, is a group of routable IP prefixes belonging to a single entity, and is one of the key building blocks of the Internet. Internet providers, public clouds, governments, and other organizations have one or more ASes that they use to connect their users or systems to the rest of the Internet by advertising how to reach them.
Per AS traffic statistics and trends help when we need insight into unusual events, like Internet outages, infrastructure anomalies, targeted attacks, or any other changes from service providers.
Today, we are opening more of our data and launching the Cloudflare Radar pages for Autonomous Systems. When navigating to a country or region page on Cloudflare Radar you will see a list of five selected ASes for that country or region. But you shouldn’t feel limited to those, as you can deep dive into any AS by plugging its ASN (Autonomous System Number) into the Radar URL (https://radar.cloudflare.com/asn/<number>). We have excluded some statistical trends from ASes with small amounts of traffic as that data would be difficult to interpret.

The AS page is similar to the country page on Cloudflare Radar. You can find traffic levels, protocol Continue reading