Emotet Is Not Dead (Yet)
The state of cyber security is a typical example of a cat-and-mouse game between hackers and defenders. Sometimes, a threat that appears to be under control, if not completely mitigated, comes back with a vengeance. This is exactly what happened to Emotet.
It has been just about a year since the Emotet botnet was taken down, thanks to the international efforts of multiple law enforcement agencies. But the silence from Emotet attackers did not last long. Late last year, we saw a report on the resurface of Emotet distributed by Trickbot. Recently VMware’s Threat Analysis Unit saw another Emotet campaign—where the attacks leveraged the increasingly abused Excel 4.0 (XL4) macros to spread Emotet payloads.
In this blog post, we investigate the first stage of the recent Emotet attacks by analyzing one of the samples from the recent campaign and reveal novel tactics, techniques, and procedures (TTPs) that were not used by Emotet in the past.
The Recent Emotet Campaign
Figure 1 shows the detection timeline of a recent Emotet campaign that affected some of our customers—mostly in the EMEA region. The campaign started on January 11 and peaked the next day before fading Continue reading
Heavy Networking 614: eBPF, Cloud-Native Networking, And Other Modern Networking Trends
Today's Heavy Networking gets deep in the guts of what’s going on with all the modern trends in networking: cloud-native, containers, eBPF, Kubernetes, DPUs, and so on. Guests Brent Salisbury and Dave Tucker give their insider’s view of developments in cutting-edge networking tech. You’ll walk away with a better idea of what to pay attention to in the months and years to come.
The post Heavy Networking 614: eBPF, Cloud-Native Networking, And Other Modern Networking Trends appeared first on Packet Pushers.
Heavy Networking 614: eBPF, Cloud-Native Networking, And Other Modern Networking Trends
Today's Heavy Networking gets deep in the guts of what’s going on with all the modern trends in networking: cloud-native, containers, eBPF, Kubernetes, DPUs, and so on. Guests Brent Salisbury and Dave Tucker give their insider’s view of developments in cutting-edge networking tech. You’ll walk away with a better idea of what to pay attention to in the months and years to come.Internet outage in Yemen amid airstrikes

The early hours of Friday, January 21, 2022, started in Yemen with a country-wide Internet outage. According to local and global news reports airstrikes are happening in the country and the outage is likely related, as there are reports that a telecommunications building in Al-Hudaydah where the FALCON undersea cable lands was hit.
Cloudflare Radar shows that Internet traffic dropped close to zero between 21:30 UTC (January 20, 2022) and by 22:00 UTC (01:00 in local time).
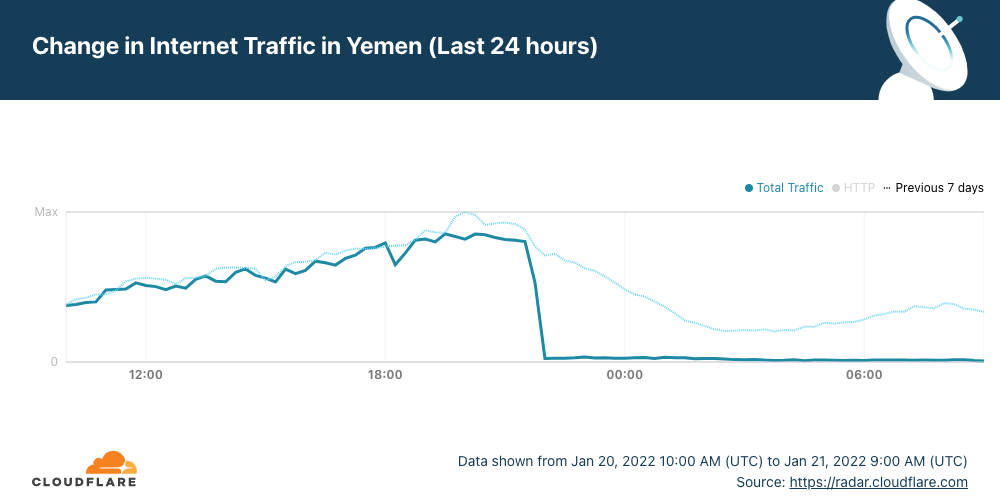
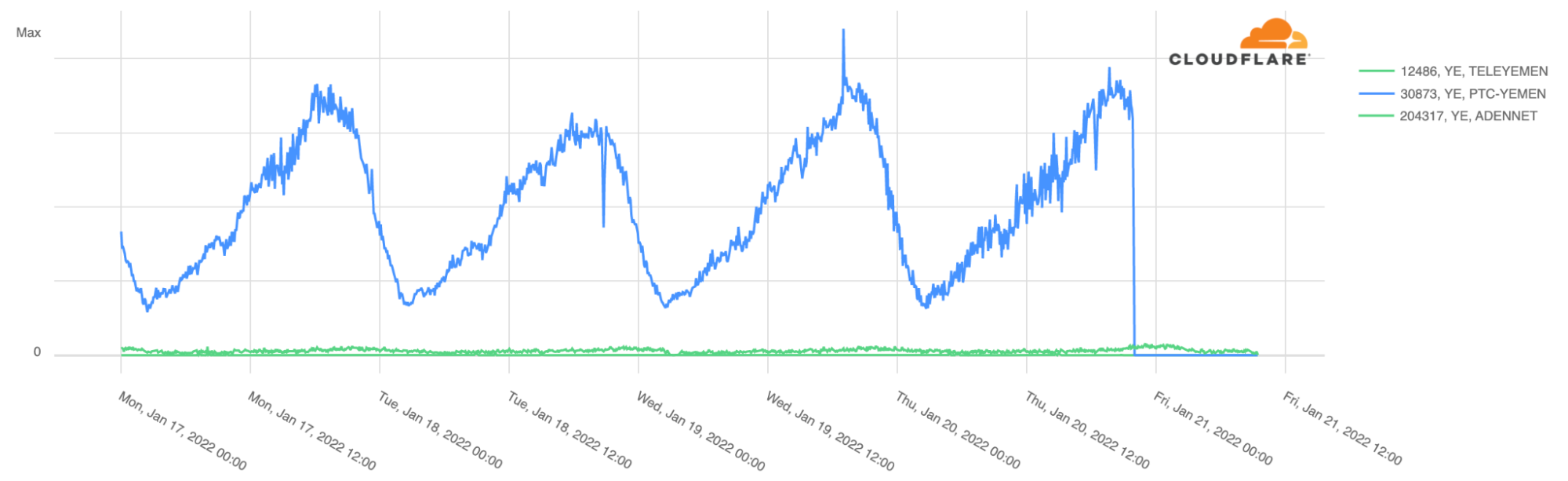
The outage affected the main state-owned ISP, Public Telecommunication Corporation (AS30873 in blue in the next chart), which represents almost all the Internet traffic in the country.
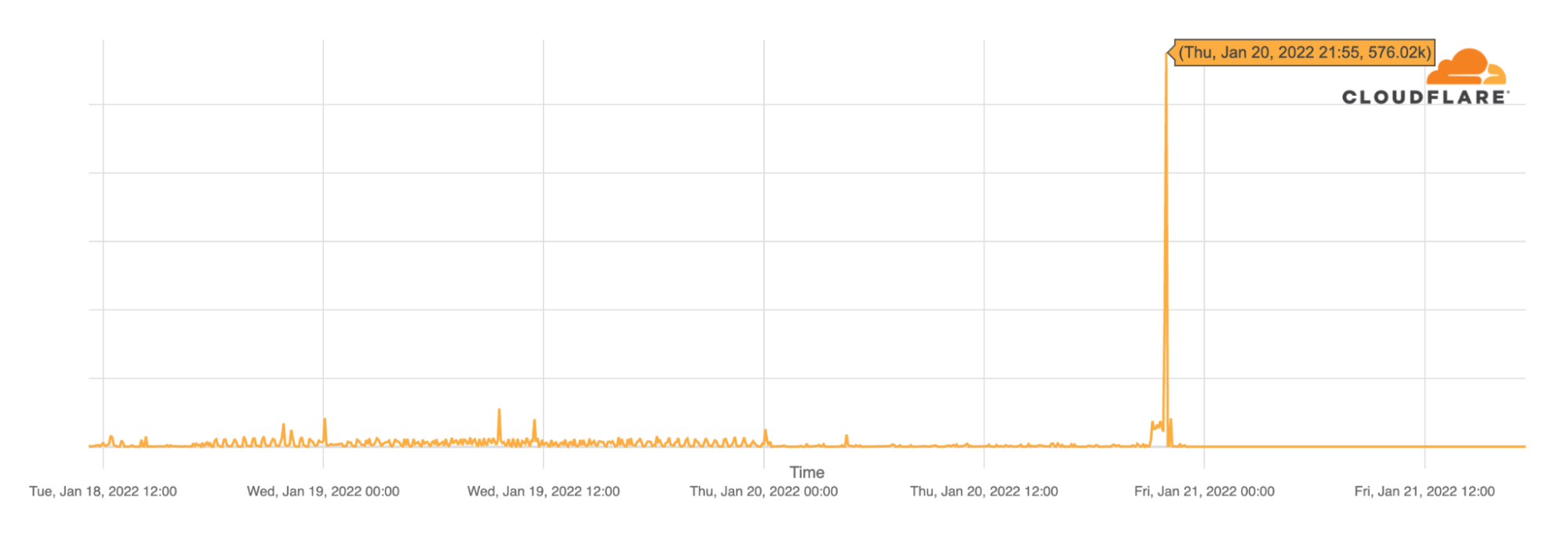
Looking at BGP (Border Gateway Protocol) updates from Yemen’s ASNs around the time of the outage, we see a clear spike at the same time the main ASN was affected ~21:55 UTC, January 20, 2022. These update messages are BGP signalling that Yemen’s main ASN was no longer routable, something similar to what we saw happening in The Gambia and Kazakhstan but for very different reasons.
So far, 2022 has started with a few significant Internet disruptions for different reasons:
1. An Internet outage in The Gambia because of a cable problem.
2. An Internet Continue reading
Video: Machine Learning Techniques
After Javier Antich walked us through the AI/ML hype and described the basics of machine learning it was time for a more thorough look at:
- Machine learning techniques, including unsupervised learning (clustering and anomaly detection), supervised learning (regression, classification and generation) and reinforced learning
- Machine learning implementations, including neural networks, deep neural networks and convolutional neural networks.
Video: Machine Learning Techniques
After Javier Antich walked us through the AI/ML hype and described the basics of machine learning it was time for a more thorough look at:
- Machine learning techniques, including unsupervised learning (clustering and anomaly detection), supervised learning (regression, classification and generation) and reinforced learning
- Machine learning implementations, including neural networks, deep neural networks and convolutional neural networks.
Juniper Networks’ SD-WAN Can Now Be Operated Via Mist Cloud
Juniper Networks’ SD-WAN appliances and software can now be fully managed from Juniper’s Mist Cloud. It’s part of Juniper’s larger goal to Mist-ify its LAN and WAN portfolio. Juniper’s SD-WAN product is based on the Session Smart Routers (SSRs) from Juniper’s acquisition of 128 Technology. Customers can now use Mist Cloud to onboard SSR hardware, […]
The post Juniper Networks’ SD-WAN Can Now Be Operated Via Mist Cloud appeared first on Packet Pushers.
Hedge 115: Mat Duggan and DevOps

Devops is the new normal—but, far too often, operations folks (like network engineers) are expected to become full-on developers, and developers are expected to understand operations in ways they never had to before. Mat Duggan joins Tom Ammon and Russ White to discuss why operations is not development IT
HS015: Targeting in IT Marketing – Who and When
With so much money allocated to marketing teams, why do customers find it disagreeable and unpleasant to be a victim of their activities ?
The post HS015: Targeting in IT Marketing – Who and When appeared first on Packet Pushers.