Burkina Faso experiencing second major Internet disruption this year

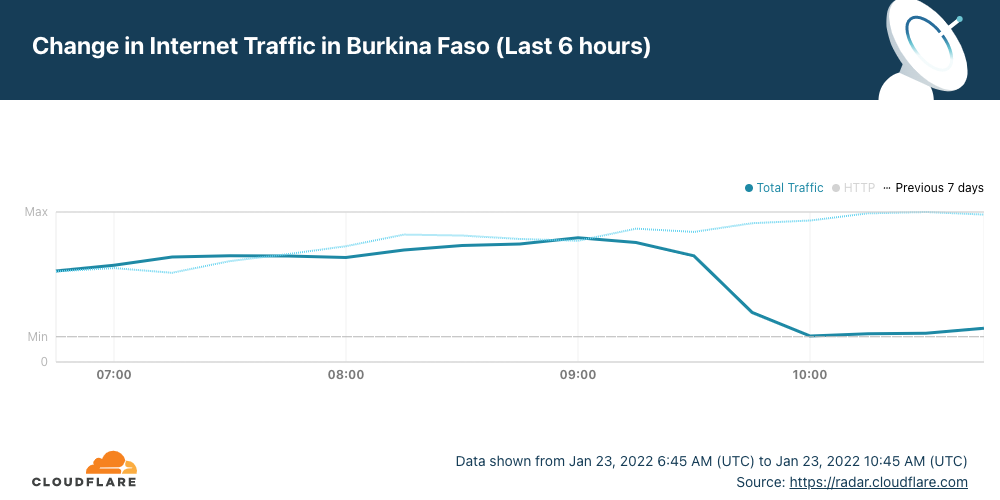
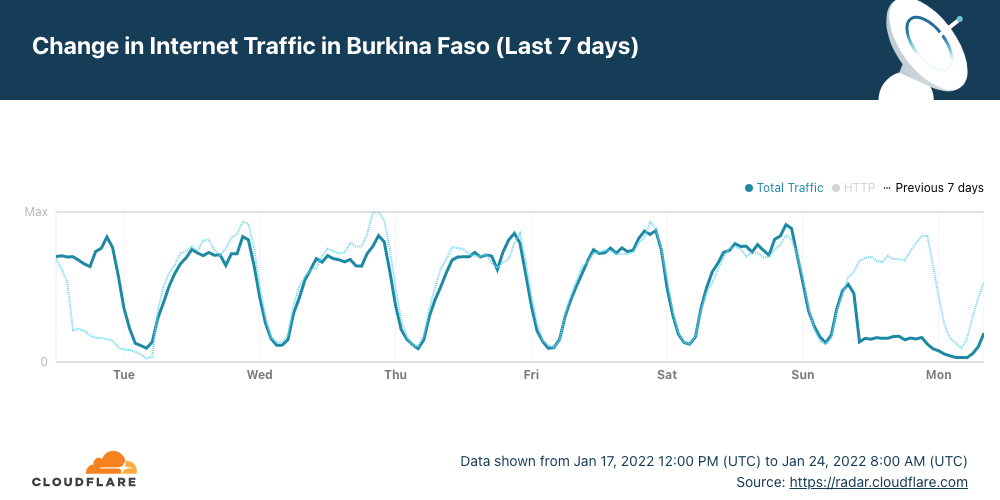
The early hours of Sunday, January 23, 2022, started in Burkina Faso with an Internet outage or shutdown. Heavy gunfire in an army mutiny could be related to the outage according to the New York Times (“mobile Internet services were shut down”). As of today, there are three countries affected by major Internet disruptions — Tonga and Yemen are the others.
Cloudflare Radar shows that Internet traffic dropped significantly in the West African country after ~09:15 UTC (the same in local time) and remains low more than 24 hours later. Burkina Faso also had a mobile Internet shutdown on January 10, 2022, and another we reported in late November 2021.
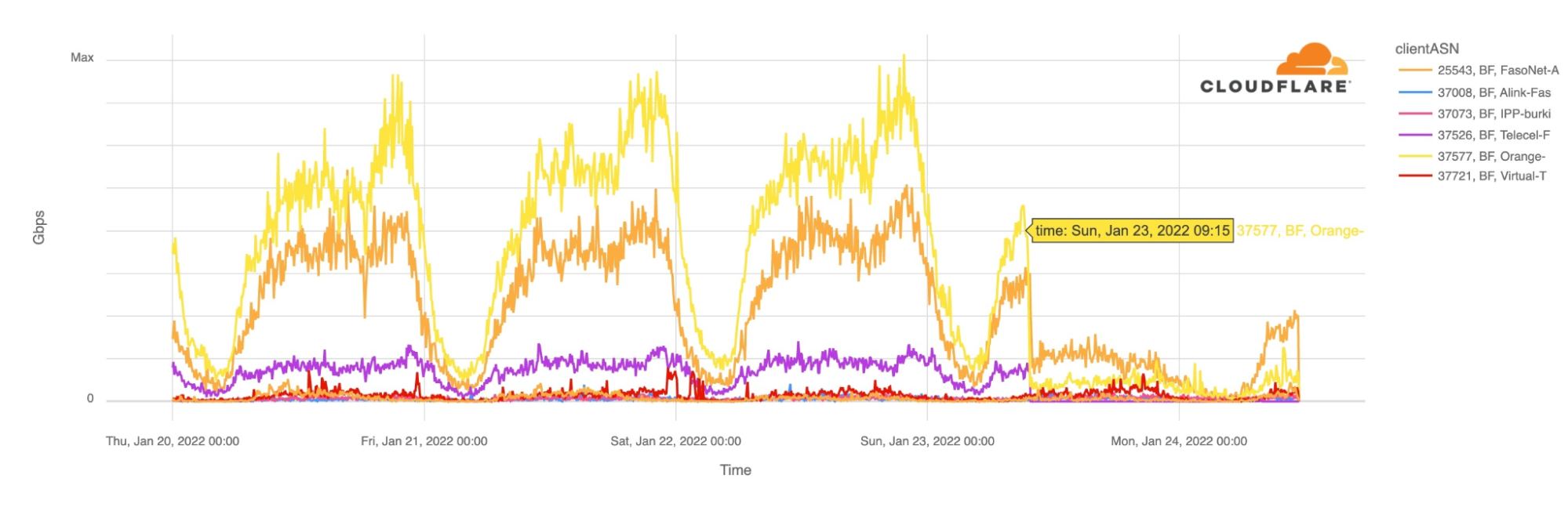
The main ISPs from Burkina Faso were affected. The two leading Internet Service Providers Orange and FasoNet lost Internet traffic after 09:15 UTC, but also Telecel Faso, as the next chart shows. This morning, at around 10:00 UTC there was some traffic from FasoNet but less than half of what we saw at the same time in preceding days.
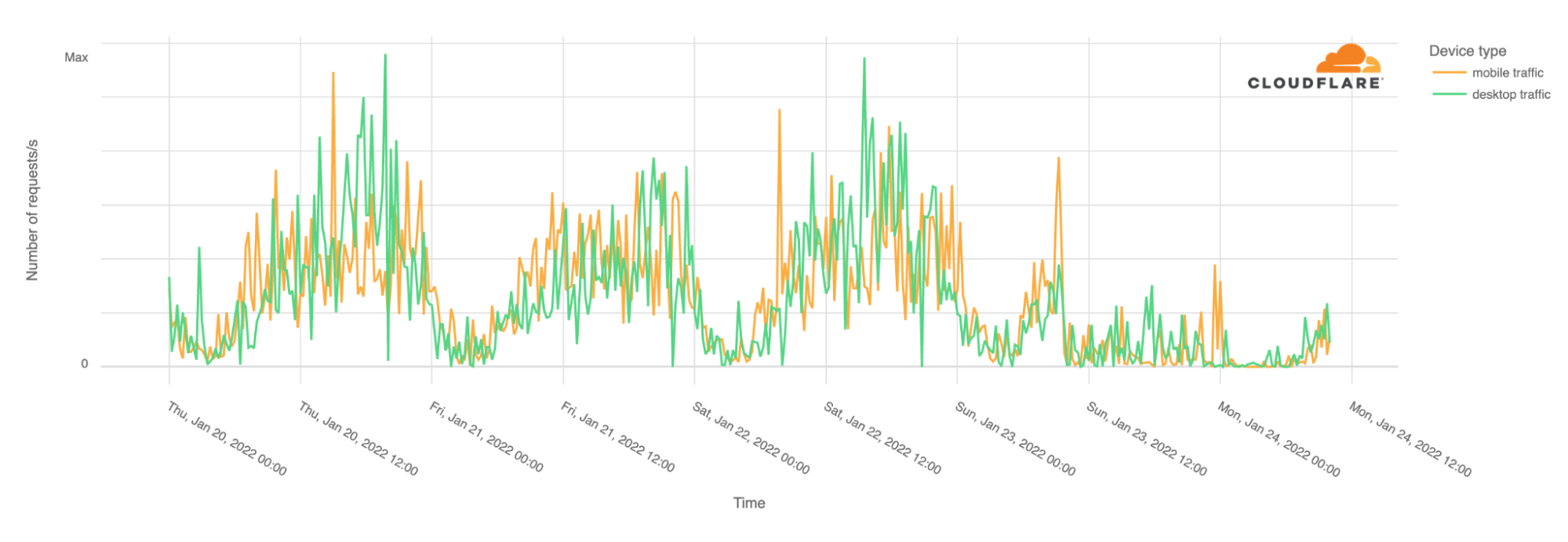
It’s not only mobile traffic that is affected. Desktop traffic is also impacted. In Burkina Faso, our data shows that mobile devices normally represent 70% of Internet traffic.
With the Burkina Continue reading
Sample Lab: RSVP TE on Junos
It’s amazing how creative networking engineers become once they have the basic tools to get the job done a bit quicker. Last week Pete Crocker published the largest topology I’ve seen built with netsim-tools so far: a 13-router lab running RSVP TE to transport IP traffic between external autonomous systems1.

Lab topology
Sample Lab: RSVP TE on Junos
It’s amazing how creative networking engineers become once they have the basic tools to get the job done a bit quicker. Last week Pete Crocker published the largest topology I’ve seen built with netlab so far: a 13-router lab running RSVP TE to transport IP traffic between external autonomous systems1.
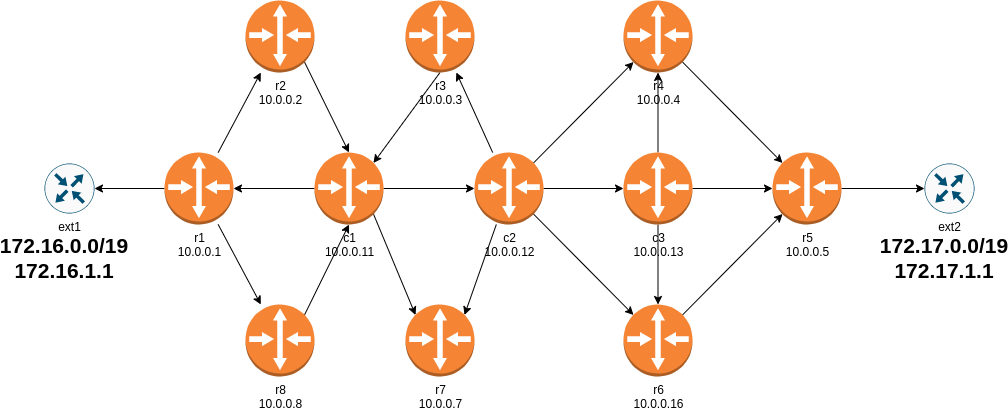
Lab topology
Junos Part I – the basics
In this post, we take an introductory look at the operating system used in Juniper platforms, called Junos OS. This post serves as an introduction to the CLI. We also cover basic bridging.
Automation 10. Installing NAPALM Community Driver for Nokia SRO OS and comparing NAPALM and OpenConfig/YANG.
Hello my friend,
In the previous blogpost we have compared the usage of NAPALM and OpenConfig YANG modules with NETCONF transport for Cisco IOS XR and Arista EOS. Those two operation systems are so called core operating systems for NAPALM and are included in its standard distribution. Besides them, other three (there are five core network operating systems in NAPALM) are Cisco IOS, Cisco Nexus, and Juniper Junos. You though can use NAPALM with other operating systems, if there are community drivers available. In today’s blogpost we cover installation and usage of NAPALM Community Driver for Nokia SR OS and its comparison against OpenConfig/YANG with NETCONF.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
How Is It Important to Know Python?
Recently we were engaged with one of our customers to help with OpenStack deployment. The first step for us was to build the lab, which could replicate the desired setup. The installation of OpenStack manually (there are means to automate that as Continue reading
Decoding Content-centric Digital Transformation
A digital transformation strategy with content as the key driver allows organizations to embrace divergent business models and deliver transformed experiences.Simplifying Multi-Cloud Networking: Stateless, Competitors See Opportunity In NaaS
This article was originally posted on Packet Pushers Ignition on May 12, 2021. To business executives and the IT subordinates seeking to appease them, being a cloud-first company is no longer enough. Now they feel compelled to be multi-cloud, on the premise that if one is good, two or more are better. Multi-cloud adherents believe […]
The post Simplifying Multi-Cloud Networking: Stateless, Competitors See Opportunity In NaaS appeared first on Packet Pushers.
The Demise of G-Suite

In case you missed it this week, Google is killing off the free edition of Google Apps/G-Suite/Workspace. The short version is that you need to convert to a paid plan by May 1, 2022. If you don’t you’re going to lose everything in July. The initial offering of the free tier was back in 2006 and the free plan hasn’t been available since 2012. I suppose a decade is a long time to enjoy custom email but I’m still a bit miffed at the decision.
Value Added, Value Lost
It’s pretty easy to see that the free version of Workspace was designed to encourage people to use it and then upgrade to a paid account to gain more features. As time wore on Google realized that people were taking advantage of having a full suite of 50 accounts and never moving, which is why 2012 was the original cutoff date. Now there has been some other change that has forced their hand into dropping the plan entirely.
I won’t speculate about what’s happening because I’m sure it’s complex and tied to ad revenue and privacy restrictions that people are implementing that is reducing the value of the data Google has Continue reading
Troubleshooting 101 – What About the Ports?
Tony Fortunato of The Technology Firm walks you through a typical network performance troubleshooting workflow.Emotet Is Not Dead (Yet)
The state of cyber security is a typical example of a cat-and-mouse game between hackers and defenders. Sometimes, a threat that appears to be under control, if not completely mitigated, comes back with a vengeance. This is exactly what happened to Emotet.
It has been just about a year since the Emotet botnet was taken down, thanks to the international efforts of multiple law enforcement agencies. But the silence from Emotet attackers did not last long. Late last year, we saw a report on the resurface of Emotet distributed by Trickbot. Recently VMware’s Threat Analysis Unit saw another Emotet campaign—where the attacks leveraged the increasingly abused Excel 4.0 (XL4) macros to spread Emotet payloads.
In this blog post, we investigate the first stage of the recent Emotet attacks by analyzing one of the samples from the recent campaign and reveal novel tactics, techniques, and procedures (TTPs) that were not used by Emotet in the past.
The Recent Emotet Campaign
Figure 1 shows the detection timeline of a recent Emotet campaign that affected some of our customers—mostly in the EMEA region. The campaign started on January 11 and peaked the next day before fading Continue reading
Heavy Networking 614: eBPF, Cloud-Native Networking, And Other Modern Networking Trends
Today's Heavy Networking gets deep in the guts of what’s going on with all the modern trends in networking: cloud-native, containers, eBPF, Kubernetes, DPUs, and so on. Guests Brent Salisbury and Dave Tucker give their insider’s view of developments in cutting-edge networking tech. You’ll walk away with a better idea of what to pay attention to in the months and years to come.
The post Heavy Networking 614: eBPF, Cloud-Native Networking, And Other Modern Networking Trends appeared first on Packet Pushers.