What Is Near-Zero Downtime Migration for SAP Systems
With the right approach, it is possible to drastically minimize scheduled downtime and its impact to the business when conducting an SAP migration.IPv6 Buzz 089: An IPv6 Deployathon With AFRINIC
In this IPv6 Buzz episode, Tom and Ed chat with Mukom Tamon, AFRINIC's head of capacity building, about IPv6 Deployathon events and how Mukom and AFRINIC are helping move IPv6 deployment forward in Africa and beyond.
The post IPv6 Buzz 089: An IPv6 Deployathon With AFRINIC appeared first on Packet Pushers.
IPv6 Buzz 089: An IPv6 Deployathon With AFRINIC
In this IPv6 Buzz episode, Tom and Ed chat with Mukom Tamon, AFRINIC's head of capacity building, about IPv6 Deployathon events and how Mukom and AFRINIC are helping move IPv6 deployment forward in Africa and beyond.What’s New in Calico v3.21
It’s that time again; we’re really happy to announce Calico v3.21! As always, thank you to everyone who contributed to this release! For detailed release notes, please go here. Alongside the usual-but-essential bug fixes and other improvements, there are some big new improvements to be aware of:
BGP Improvements
Calico supports BGP, which is used within the cluster in some scenarios, and to allow you to integrate cluster routing with your upstream network devices. Now though, you can even view the status of your BGP sessions, including RIB / FIB contents, and agent health via the new CalicoNodeStatus API. See the API documentation for more details.
In addition, you get more granular control; you can control BGP advertisement of certain prefixes using the new disableBGPExport option on each IP pool.
Service-based network policy improvements
If you aren’t already familiar with them, the egress policy rules that can match on Kubernetes services, introduced in v3.20, are pretty transformative. However we have improved even further upon them in two ways:
- Now, you can use service matches in Calico NetworkPolicy and GlobalNetworkPolicy ingress rules.
- And, you can even now use service-based network policy rules on Windows nodes!
Option to run Calico Continue reading
HS013 SaaS Solutions – What Does the Customer Lose ?
SaaS is popular as a 'not my problem' solution and easy-on-pocket entrè. So lets examine adversarial question "What does the customer lose?". Johna and Greg discuss many issues on both in the search for critical analysis on SaaS and the longer term impacts.
The post HS013 SaaS Solutions – What Does the Customer Lose ? appeared first on Packet Pushers.
HS013 SaaS Solutions – What Does the Customer Lose ?
SaaS is popular as a 'not my problem' solution and easy-on-pocket entrè. So lets examine adversarial question "What does the customer lose?". Johna and Greg discuss many issues on both in the search for critical analysis on SaaS and the longer term impacts.Workers, Now Even More Unbound: 15 Minutes, 100 Scripts, and No Egress


Our mission is to enable developers to build their applications, end to end, on our platform, and ruthlessly eliminate limitations that may get in the way. Today, we're excited to announce you can build large, data-intensive applications on our network, all without breaking the bank; starting today, we're dropping egress fees to zero.
More Affordable: No Egress Fees
Building more on any platform historically comes with a caveat — high data transfer cost. These costs often come in the form of egress fees. Especially in the case of data intensive workloads, egress data transfer costs can come at a high premium, depending on the provider.
What exactly are data egress fees? They are the costs of retrieving data from a cloud provider. Cloud infrastructure providers generally pay for bandwidth based on capacity, but often bill customers based on the amount of data transferred. Curious to learn more about what this means for end users? We recently wrote an analysis of AWS’ Egregious Egress — a good read if you would like to learn more about the ‘Hotel California’ model AWS has spun up. Effectively, data egress fees lock you into their platform, making you choose your provider based not on Continue reading
Cloudflare Images introduces AVIF, Blur and Bundle with Stream
Two months ago we launched Cloudflare Images for everyone, and we are amazed about the adoption and the feedback we received.
Let’s start with some numbers:
More than 70 million images delivered per day on average in the week of November 5 to 12.
More than 1.5 million images have been uploaded so far, growing faster every day.
But we are just getting started and are happy to announce the release of the most requested features, first we talk about the AVIF support for Images, converting as many images as possible with AVIF results in highly compressed, fast delivered images without compromising on the quality.
Secondly we introduce blur. By blurring an image, in combination with the already supported protection of private images via signed URL, we make Cloudflare Images a great solution for previews for paid content.
For many of our customers it is important to be able to serve Images from their own domain and not only via imagedelivery.net. Here we show an easy solution for this using a custom Worker or a special URL.
Last but not least we announce the launch of new attractively priced bundles for both Cloudflare Images and Stream.
Images Continue reading
Developer Spotlight: Automating Workflows with Airtable and Cloudflare Workers

Next up on the Developer Spotlight is another favourite of mine. Today’s post is by Jacob Hands. Jacob operates TriTails Premium Beef, which is an online store for meat, a very perishable good. So he has a lot of unique challenges when it comes to shipping. To deal with their growth, Jacob, a developer by trade, turned to Airtable and Cloudflare Workers to automate a lot of their workflow.
One of Jacob’s quotes is one of my favourites:
“Sure, Cloudflare Workers allows you to scale to billions of requests per day, but it is also awesome for a few hundred requests a day.”
Here is Jacob talking about how it only took him a few days to put together a fully customised workflow tool by integrating Airtable and Workers. And how it saves them multiple hours every single day.
Shipping Requirements
Working at a new e-commerce business shipping perishable goods has several challenges as operations scale up. One of our biggest challenges is that daily shipping throughput is limited. Partly because of a small workspace, limiting how many employees can simultaneously pack orders, and also because despite having a requested pickup time with UPS, they often show up Continue reading
Modifying HTTP response headers with Transform Rules

HTTP headers are central to how the web works. They are used for passing additional information between the client and server, such as which security permissions to apply and information about the client, allowing the correct content to be served.
Today we are announcing the immediate availability of the third action within Transform Rules, “HTTP Response Header Modification”, available for all Cloudflare plans. This new functionality provides Cloudflare users the ability to set or remove HTTP response headers as traffic returns through Cloudflare back to the client. This allows customers to enrich responses with information about how their request was handled, debugging information and even recruitment messages.
Previously, HTTP response header modification was done using a Cloudflare Worker. Today we’re introducing an easier way to do this without writing a single line of code.
Luggage tags of the World Wide Web

Think of HTTP headers as the “luggage tag” attached to your bags when you check in at the airport.
Generally, you don't need to know what those numbers and words mean. You just know they are important in getting your suitcase from the boarding desk, to the correct airplane, and back to the correct luggage carousel at your destination.
The Cloudflare Developer Expert Program: apply today!


Today we’re launching the Cloudflare Developer Expert Program: an initiative to support and recognize our VIP users who build with Workers, Pages, and the entire Cloudflare developer ecosystem.
A Cloudflare Developer Expert is an early adopter of new releases, a frequent participant in feedback sessions, and an evangelist for Cloudflare products made for the larger developer community.
But first, what are the benefits of becoming a Cloudflare Developer Expert?
- Early access to features (e.g., private betas)
- Admission to a private community of power users
- Routine calls with product managers, engineers, and developer advocates
- Sponsorships for OSS work
- Our best swag, of course
We have already sent invites to our first batch of power users, but if you’d like to join or want to nominate a developer, please fill out this form.
Why We Made This Program
We ship very quickly at Cloudflare.
This is because we want feedback early in development, allowing users to challenge our assumptions and validate what we’re building. In the Workers team, this strategy has been very successful.
For example, we began beta testing custom builds for Wrangler (our CLI tool) that allow you to run any JavaScript bundler you want. This was Continue reading
Hardware Differences between Routers and Switches
One of my readers sent me this age-old question:
Is there a real difference in the underlying hardware of switches and routers in terms of the traffic processing chips and their capabilities in terms of routing and switching (or should I say only switching)?
Let’s get the terminology straight. Router is a technical term for a device that forwards packets based on network layer information. Switch is a marketing term for a device that does something with packets.
Rephrasing the question: is there a hardware difference between a box marketed as a router and another box marketed as a layer-3 switch?
TL&DR: Yes.
Doing packet forwarding at high speeds is expensive, and simpler forwarding pipeline results in cheaper (or faster) silicon.
If you don’t need complex high-speed functionality (like a thousand interface output queues with per-flow classifier), you create a simpler ASIC and call the device a switch. If you thrive on overpriced products, you create as complex an ASIC as you can make it and call the device using it a router. EX9200 is an obvious counterexample, but then Juniper always looked like DEC of networking to me.
There’s even a difference in capabilities between spine- and leaf data Continue reading
Hardware Differences between Routers and Switches
One of my readers sent me this age-old question:
Is there a real difference in the underlying hardware of switches and routers in terms of the traffic processing chips and their capabilities in terms of routing and switching (or should I say only switching)?
Let’s get the terminology straight. Router is a technical term for a device that forwards packets based on network layer information. Switch is a marketing term for a device that does something with packets.
Rephrasing the question: is there a hardware difference between a box marketed as a router and another box marketed as a layer-3 switch?
TL&DR: Yes.
Day Two Cloud 124: New Cloud Security Thinking
Today on Day Two Cloud, we talk about new ways of thinking about security for cloud. As organizations adopt cloud services, they're applying on-prem security designs. Our guest Adeel Ahmad is here to argue that this doesn't work, and that you need a different approach.
The post Day Two Cloud 124: New Cloud Security Thinking appeared first on Packet Pushers.
Day Two Cloud 124: New Cloud Security Thinking
Today on Day Two Cloud, we talk about new ways of thinking about security for cloud. As organizations adopt cloud services, they're applying on-prem security designs. Our guest Adeel Ahmad is here to argue that this doesn't work, and that you need a different approach.Top Issues in Evaluating UC Reporting and Analysis Packages
Advanced capabilities and analytics take center stage as enterprises consider third-party offerings to span the premises, cloud, and hybrid communications scenarios.How William Hill Achieved Success in their Journey to Multi-Cloud
A commonly used term in the sports betting world is handicapper. A handicapper is a person who analyzes sports events to predict the winning team or player. This person (or team) focuses on all the moving pieces in a chaotic or high-stakes environment to make business-critical decisions. Similarly, in managing a multi-cloud environment, organizations have a lot at stake, and they must make crucial operational choices for the sake of security and the end-user experience. Having the ability to spot challenges in advance when moving through a multi-cloud journey will make the difference between success and failure. We’re going to look at three of the key multi-cloud challenges organizations face, as well as a real-life customer success story, William Hill, and how they overcame some of their biggest obstacles in their quest for multi-cloud success.
3 Roadblocks to Multi-Cloud
Regardless of where your organization started, there are three primary challenges you will likely face in moving to multi-cloud. To begin, every cloud is different in the way that it operates. This creates issues when it comes to connecting services across different cloud environments. Second, each cloud has its own methods and APIs when it comes to securing workloads. Thus, the process can lose consistency when different clouds are trying to communicate with one another. Lastly, providing a winning end-user experience requires strong observability within a multi-cloud environment. If that doesn’t exist, the bread and butter of your enterprise is at stake.
So, how do you move past these roadblocks?
There are three must-haves to keep in mind — and to keep you calm, cool, and collected when facing Continue reading
Cloudflare Pages Goes Full Stack


When we announced Cloudflare Pages as generally available in April, we promised you it was just the beginning. The journey of our platform started with support for static sites with small bits of dynamic functionality like setting redirects and custom headers. But we wanted to give even more power to you and your teams to begin building the unimaginable. We envisioned a future where your entire application — frontend, APIs, storage, data — could all be deployed with a single commit, easily testable in staging and requiring a single merge to deploy to production. So in the spirit of “Full Stack” Week, we’re bringing you the tools to do just that.
Welcome to the future, everyone. We’re thrilled to announce that Pages is now a Full Stack platform with help from But how? It works the exact same way Pages always has: write your code, Cloudflare Workers provides a serverless execution environment that allows you to create entirely new applications or augment existing ones without configuring or maintaining infrastructure. Before today, it was possible to connect Workers to a Pages project—installing Wrangler and manually deploying a Worker by writing your app in both Pages and Workers. But we didn’t just want “possible”, we wanted something that came as second nature to you so you wouldn’t have to think twice about adding dynamic functionality to your site. By using your repo’s filesystem convention and exporting one or more function handlers, Pages can leverage Workers to deploy serverless functions on your behalf. To begin, simply add a If you perform a Under the hood, Pages generates Workers which include all your routing and functionality from the source. Functions supports deeply-nested routes, wildcard matching, middleware for things like authentication and error-handling, and more! To demonstrate all of its bells and whistles, we’ve created a blog post to walk through an example full stack application. As your site grows in complexity, with Pages’ new full stack functionality, your developer experience doesn’t have to. You can enjoy the workflow you know and love while unlocking even more depth to your site. In the same way we’ve handled builds and deployments with your static sites — with a `git commit` and `git push` — we’ll deploy your functions for you automatically. As long as your directory follows the proper structure, Pages will identify and deploy your functions to our network with your site. While bringing your Workers to Pages, bindings are a big part of what makes your application a full stack application. We’re so excited to bring to Pages all the bindings you’ve previously used with regular Workers! With the deployment of your serverless functions, you can still enjoy the ease of collaboration and testing like you did previously. Before you deploy to production, you can easily deploy your project to a preview environment to stage your changes. Even with your functions, Pages lets you keep a version history of every commit with a unique URL for each, making it easy to gather feedback whether it’s from a fellow developer, PM, designer or marketer! You can also enjoy the same infinite staging privileges that you did for static sites, with a consistent URL for the latest changes. However, we realize that building and deploying with every small change just to stage your changes can be cumbersome at times if you’re iterating quickly. You can now develop full stack Pages applications with the latest release of our wrangler CLI. Backed by Miniflare, you can run your entire application locally with support for mocked secrets, environment variables, and KV (Durable Objects support coming soon!). Point wrangler at a directory of static assets, or seamlessly connect to your existing tools: This is just the beginning of Pages' integrations with wrangler. Stay tuned as we continue to enhance your developer experience. Everything you can do with HTTP Workers today! When deploying a Pages application with functions, Pages is compiling and deploying first class Workers on your behalf. This means there is zero functionality loss when deploying a Worker within your Pages application — instead, there are only new benefits to be gained! SvelteKit is a web framework for building Svelte applications. It’s built and maintained by the Svelte team, which makes it the Svelte user’s go-to solution for all their application needs. Out of the box, SvelteKit allows users to build projects with complex API backends. As of today, SvelteKit projects can attach and configure the You are now able to intercept any request that comes into your Pages project. This means that you can define Workers logic that will receive incoming URLs and, instead of serving static HTML, your Worker can render fresh HTML responses with dynamic data. For example, an application with a product page can define a single If you already have a single Worker and want to bring it right on over to Pages to reap the developer experience benefits of our platform, our announcement today also enables you to do precisely that. Your build can generate an ES module Worker called We’re thrilled to be releasing our open beta today for everyone to try at no additional cost to your Cloudflare plan. While we will still have limits in place, we are using this open beta period to learn more about how you and your teams are deploying functions with your Pages projects. For the time being, we encourage you to lean into your creativity and build out that site you’ve been thinking about for a long time — without the worry of getting billed. In just a few short months, when we announce General Availability, you can expect our billing to reflect that of the Workers Bundled plan — after all, these are just Workers under the hood! As we’re only announcing this release as an open beta, we have some really exciting things planned for the coming weeks and months. We want to improve on the quick and easy Pages developer experience that you're already familiar with by adding support for integrated logging and more analytics for your deployed functions. Beyond that, we'll be expanding our first-class support for the next generation of frontend frameworks. As we've shown with SvelteKit, Pages' ability to seamlessly deploy both static and dynamic code together enables unbeatable end-user performance & developer ease, and we're excited to unlock that for more people. Fans of similar frameworks & technologies, such as NextJS, NuxtJS, React Server Components, Remix, Hydrogen, etc., stay tuned to this blog for more announcements. Or better yet, come join us and help make it happen! Additionally, as we’ve done with SvelteKit, we’re looking to include more first-class integration with existing frameworks, so Pages can become the primary home for your preferred frameworks of choice. Work is underway on making NextJS, NuxtJS, React Server Components, Shopify Hydrogen and more integrate seamlessly as you develop your full stack apps. Finally, we’re working to speed up those build times, so you can focus on pushing changes and iterating quickly — without the wait! To get started head over to our Pages docs and check out our demo blog to learn more about how to deploy serverless functions to Pages using Cloudflare Workers. Of course, what we love most is seeing what you build! Pop into our Discord and show us how you’re using Pages to build your full stack apps.git push to your git provider (now supporting GitLab!) and we’ll deploy your entire site for you. The only difference is, it won’t just be your frontend but your backend too using Cloudflare Workers to help deploy serverless functions.The integration you’ve been waiting for
How it works
./functions directory in the root of your project, and inside a JavaScript or TypeScript file, export a function handler. For example, let’s say in your ./functions directory, you have a file, hello.js, containing:// GET requests to /filename would return "Hello, world!"
export const onRequestGet = () => {
return new Response("Hello, world!")
}
// POST requests to /filename with a JSON-encoded body would return "Hello, <name>!"
export const onRequestPost = async ({ request }) => {
const { name } = await request.json()
return new Response(`Hello, ${name}!`)
}
git commit, it will trigger a new Pages build to deploy your dynamic site! During the build pipeline, Pages traverses your directory, mapping the filenames to URLs relative to your repo structure.Letting you do what you do best
Seamlessly build
Define your bindings
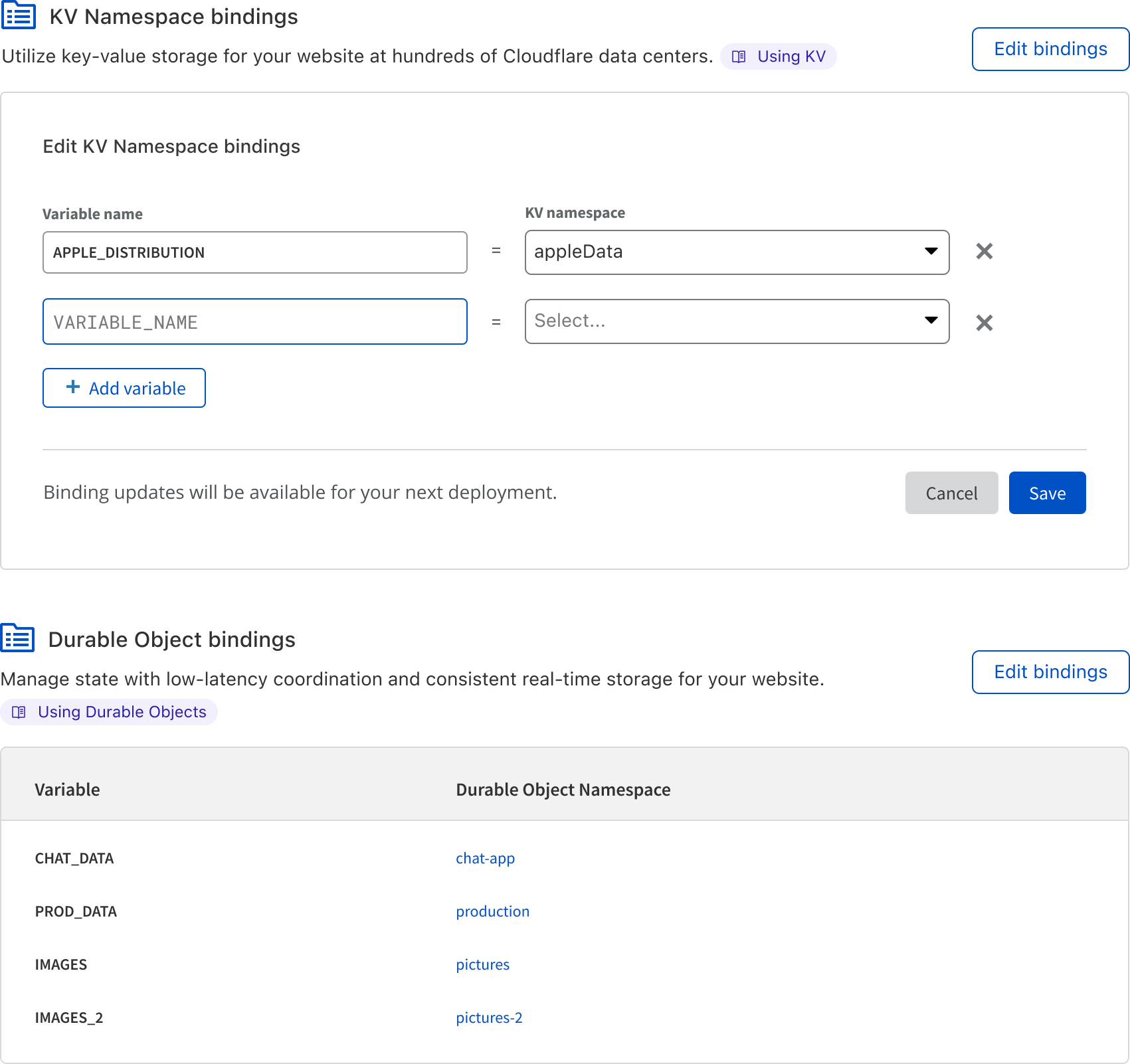
Preview deployments — now for your backend too
Develop and preview locally too
# Install wrangler v2 beta
npm install wrangler@beta
# Serve a folder of static assets
npx wrangler pages dev ./dist
# Or automatically proxy your existing tools
npx wrangler pages dev -- npx react-scripts start
What else can you do?
Integrate with SvelteKit — out of the box!
@sveltejs/adapter-cloudflare package. After doing this, the project can be added to Pages and is ready for its first deployment! With Pages, your SvelteKit project(s) can deploy with API endpoints and full server-side rendering support. Better yet, the entire project — including the API endpoints — can enjoy the benefits of preview deployments, too! This, even on its own, is a huge victory for advanced projects that were previously on the Workers adapter. Check out this example to see the SvelteKit adapter for Pages in action!Use server-side rendering
product/[id].js file that will receive the id parameter, retrieve the product information from a Workers KV binding, and then generate an HTML response for that page. Compared to a static-site generator approach, this is more succinct and easier to maintain over time since you do not need to build a static HTML page per product at build-time… which may potentially be tens or even hundreds of thousands of pages!Already have a Worker? We’ve got you!
_worker.js in the output directory of your project, perform your git commands to deploy, and we’ll take care of the rest! This can be especially advantageous to you if you’re a framework author or have a more complex use case that doesn’t follow our provided file structure.Try it at no cost — for a limited time only
Coming up…
Getting started
