Feedback: Business Aspects of Networking
Every other blue moon someone asks me to do a not-so-technical presentation at an event, and being a firm believer in frugality I turn most of them into live webinar sessions collected under the Business Aspects of Networking umbrella.
At least some networking engineers find that perspective useful. Here’s what Adrian Giacometti had to say about that webinar:
Proxmox Import QCOW2 Image
I recently migrated my homelab servers from running bare metal KVM/QEMU on Ubuntu, to running Proxmox as a hypervisor. As part of that process I migrated some of the VM's from KVM to Proxmox. In this post I will show you how I imported the qcow2 VM's from KVM/QEMU into...continue reading
Managing Hierarchical Device Configurations
Parsing and modifying IOS-like hierarchical device configurations is an interesting challenge, more so if you have no idea what the configuration commands mean or whether their order is relevant (I’m looking at you, Ansible ;).
Network to Code team decided to solve that problem for good, open-sourced Hierarchical Configuration Python library, and published a getting started article on their blog.
Managing Hierarchical Device Configurations
Parsing and modifying IOS-like hierarchical device configurations is an interesting challenge, more so if you have no idea what the configuration commands mean or whether their order is relevant (I’m looking at you, Ansible ;).
Network to Code team decided to solve that problem for good, open-sourced Hierarchical Configuration Python library, and published a getting started article on their blog.
Automation 4. Extracting and Exploring 6WING YANG Modules with NETCONF, Pyang and Ansible
Hello my friend,
Some time ago we’ve explained how to deploy a 6WING vRouter in a Linux environmennt, such as our Open Source Virtualised cloud with Debian Linux and ProxMox. One of the good things about 6WIND is that its configuration is entirely based on YANG modules and is exposable via NETCONF. Today you will learn how to get 6WIND YANG modules, how are they structured with Pyang and how to automate its extraction with Ansible.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Why Is Everyone so Passionate about Model-Driven Automation and YANG?
All we love nice configuration files made in easy readable YANG or JSON, isn’t it? The beauty of working with them is that you don’t need to create a text string parsers, which is always a difficult task. One of the reasons, why it is so difficult to create parsers, is because of ever changing CLI structures and also values in the semi-formatted text, our ascii tables we see Continue reading
How to rsync files between two remotes?
scp -3 can copy files between two remote hosts through localhost.
This comes in handy when the two servers cannot communicate
directly or if they are unable to authenticate one to the
other.1 Unfortunately, rsync does not support such a feature.
Here is a trick to emulate the behavior of scp -3 with SSH tunnels.
When syncing with a remote host, rsync invokes ssh to spawn a
remote rsync --server process. It interacts with it through its
standard input and output. The idea is to recreate the same setup
using SSH tunnels and socat, a versatile tool to establish
bidirectional data transfers.
The first step is to connect to the source server and ask rsync the
command-line to spawn the remote rsync --server process. The -e
flag overrides the command to use to get a remote shell: instead of
ssh, we use echo.
$ ssh web04 $ rsync -e 'sh -c ">&2 echo $@" echo' -aLv /data/. web05:/data/. web05 rsync --server -vlogDtpre.iLsfxCIvu . /data/. rsync: connection unexpectedly closed (0 bytes received so far) [sender] rsync error: error in rsync protocol data stream (code 12) at io.c(228) [sender=3.2.3]
The second step is to connect to Continue reading
Soap Opera: SRv6 Is Insecure
I heard about SRv6 when it was still on the drawing board, and my initial reaction was “Another attempt to implement source routing. We know how that ends.” The then-counter-argument by one of the proponents went along the lines of “but we’ll use signed headers to prevent abuse” and I thought “yeah, that will work really well in silicon implementations”.
Years later, Andrew Alston decided to document the state of the emperor’s wardrobe (TL&DR: of course SRv6 is insecure and can be easily abused) and the counter-argument this time was “but that applies to any tunnel technology”. Thank you, we knew that all along, and that’s not what was promised.
You might want to browse the rest of that email thread; it’s fun reading unless you built your next-generation network design on SRv6 running across third-party networks… which was another PowerPoint case study used by SRv6 proponents.
Soap Opera: SRv6 Is Insecure
I heard about SRv6 when it was still on the drawing board, and my initial reaction was “Another attempt to implement source routing. We know how that ends.” The then-counter-argument by one of the proponents went along the lines of “but we’ll use signed headers to prevent abuse” and I thought “yeah, that will work really well in silicon implementations”.
Years later, Andrew Alston decided to document the state of the emperor’s wardrobe (TL&DR: of course SRv6 is insecure and can be easily abused) and the counter-argument this time was “but that applies to any tunnel technology”. Thank you, we knew that all along, and that’s not what was promised.
You might want to browse the rest of that email thread; it’s fun reading unless you built your next-generation network design on SRv6 running across third-party networks… which was another PowerPoint case study used by SRv6 proponents.
Heavy Networking 605: How cnvrg.io Metacloud Can Help Solve MLOps Challenges (Sponsored)
Today on Heavy Networking, we consider a newly announced platform for artificial intelligence workloads, the cnvrg.io Meta Cloud. Our sponsor is Intel, and our guest is Yochay Ettun, Co-founder and CEO at cnvrg.io.
The post Heavy Networking 605: How cnvrg.io Metacloud Can Help Solve MLOps Challenges (Sponsored) appeared first on Packet Pushers.
Heavy Networking 605: How cnvrg.io Metacloud Can Help Solve MLOps Challenges (Sponsored)
Today on Heavy Networking, we consider a newly announced platform for artificial intelligence workloads, the cnvrg.io Meta Cloud. Our sponsor is Intel, and our guest is Yochay Ettun, Co-founder and CEO at cnvrg.io.Is the M1 MacBook Pro Wi-Fi Really Slower?
![]()
I ordered a new M1 MacBook Pro to upgrade my existing model from 2016. I’m still waiting on it to arrive by managed to catch a sensationalist headline in the process:
“New MacBook Wi-Fi Slower than Intel Model!”
The article referenced this spec sheet from Apple referencing the various cards and capabilities of the MacBook Pro line. I looked it over and found that, according to the tables, the wireless card in the M1 MacBook Pro is capable of a maximum data rate of 1200 Mbps. The wireless card in the older model Intel MacBook Pro all the way back to 2017 is capable of 1300 Mbps. Case closed! The older one is indeed faster. Except that’s not the case anywhere but on paper.
PHYs, Damned Lies, and Statistics
You’d be forgiven for jumping right to the numbers in the table and using your first grade inequality math to figure out that 1300 is bigger than 1200. I’m sure it’s what the authors of the article did. Me? I decided to dig in a little deeper to find some answers.
It only took me about 10 seconds to find the first answer as to one of the differences in Continue reading
Cloud May See More AI, Face Increased Geopolitical Friction
Analysts at Gartner and Forrester respectively see the next few years bringing wider use of automation and elevated government involvement in the cloud sector.Tier 1 Carriers Performance Report: October, 2021
The post Tier 1 Carriers Performance Report: October, 2021 appeared first on Noction.
When students go back to school mobile usage goes down


For many (especially in the Northern Hemisphere, where about 87% of humans live), September is the “get back to school” (or work) month after a summer break and that also reflects changes in the Internet traffic, particularly in mobile usage.
Looking at our data (you can see many of these insights in Cloudflare Radar) there’s a global trend: mobile traffic lost importance (compared with desktop traffic) in September. The next chart shows there was less percentage of Internet traffic from mobile devices after Monday, September 6, 2021, with a difference of -2% in some days, compared with the previous four weeks (August), and in late September it’s more than -3%.
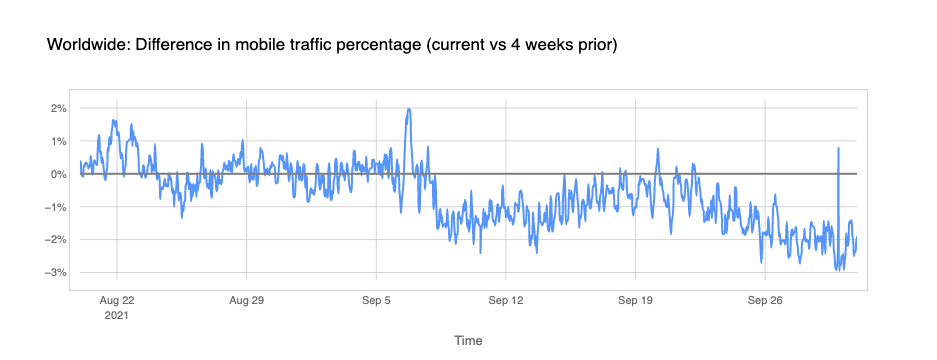
We can also see that the percentage of desktop traffic increased in September compared to August (we compare here to complete weeks between both months because there are significant differences between weekdays and weekends).
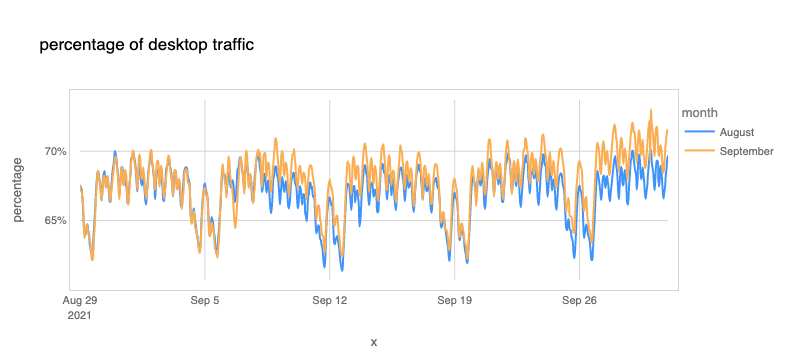
A few of weeks ago, we saw there are considerable differences between countries regarding the importance of mobile usage. Getting back to work (or office hours) usually means an increase in desktop traffic. In that blog we highlighted the advantages that mobile devices brought to developing countries — many had their first contact with Continue reading
Video: How Can You Master Public Cloud Networking?
If you’re a regular reader of this blog, you’ve probably realized there’s still need for networking in public clouds, and mastering it requires slightly different set of skills. What could you as a networking engineer to get fluent in this different world? I collected a few hints in the last video in Introduction to Cloud Computing webinar.
Video: How Can You Master Public Cloud Networking?
If you’re a regular reader of this blog, you’ve probably realized there’s still need for networking in public clouds, and mastering it requires slightly different set of skills. What could you as a networking engineer to get fluent in this different world? I collected a few hints in the last video in Introduction to Cloud Computing webinar.