Day Two Cloud 123: Managing Multi-Cloud Applications And Infrastructure With vRealize Operations Cloud (Sponsored)
Welcome to Day Two Cloud, where the topic is visibility. Hybrid cloud visibility with a side of Kubernetes, to be specific. VMware has come alongside as today’s sponsor for a discussion about vRealize Operations Cloud to give you that visibility into applications and infrastructure running in complex, multi-cloud environments.How to Accelerate Your Digital Transformation with VMware’s Cloud Networking Capabilities
Realize What’s Possible with Advanced Cloud Networking Capabilities
VMworld 2021 – what a whirlwind. Thank you for attending and making the virtual event a success. With so many sessions and so little time, we thought it was important to point out one of the most notable networking sessions of this year: Automation is Modernizing Networks, delivered by Tom Gills, SVP & General Manager, Networking and Advanced Security.
In case you missed it, we’re going to catch you up on essential insights, networking news, and more.
Networking by the Numbers
The vision behind VMware’s cloud networking is to centralize policy and networking infrastructure. Today, there are more than 23,000 customers using VMware’s virtual networking products. 96 out of the Fortune 100 have chosen VMware to virtualize their network infrastructure. VMware has replaced more than 12,000 power-hungry, hardware load balancer appliances. There are more than 450,000 branch sites globally, accelerating the digital transformation for enterprises of all kinds.
Leveling Up
Taking a step back, we can see how clearly all of these developments are enhancing digital operations for our various constituents. With two strokes of a key, our customers can send applications directly into production. This includes scanning for security/compliance violations, enforcing these security and compliance Continue reading
The Deep Skills Every Network Manager Should Possess
The network manager's role is expanding and evolving. Is your skillset keeping pace with changing technologies and challenges?Python Script Pulling AWS IP Prefixes – Part 3
The two previous posts described what the script does and modules used as well as how the script leverages YAML.
This time, we will go through the function that generates the access-list name. The code for this is below:
def generate_acl_name(interface_name: str) -> str:
"""Generate unique ACL name to avoid conflicts with any existing ACLs
by appending a random number to the outside interface name"""
# Create a random number between 1 and 999
random_number = random.randint(1, 999)
acl_name = f"{interface_name}_{random_number}"
return acl_name
The goal with this code is to generate a new access-list with a unique name. Note that the script doesn’t do any check if this access-list already exists which is something I will look into in an improved version of the script. I wanted to first start with something that works and take you through the process together with myself as I learn and improve on the existing code.
The function takes an interface_name which is a string. This is provided by the YAML data that we stored in the yaml_dict earlier. The function is then called like this:
acl_name = generate_acl_name(yaml_dict["outside_interface"])
The name is stored in the yaml_dict under the outside_interface mapping:
In [6]: yaml_dict Continue reading
Building a Separate Infrastructure for Guest Access
One of my readers sent me an age-old question:
I have my current guest network built on top of my production network. The separation between guest- and corporate network is done using a VLAN – once you connect to the wireless guest network, you’re in guest VLAN that forwards your packets to a guest router and off toward the Internet.
Our security team claims that this design is not secure enough. They claim a user would be able to attach somehow to the switch and jump between VLANs, suggesting that it would be better to run guest access over a separate physical network.
Decades ago, VLAN implementations were buggy, and it was possible (using a carefully crafted stack of VLAN tags) to insert packets from one VLAN to another (see also: VLAN hopping).
Building a Separate Infrastructure for Guest Access
One of my readers sent me an age-old question:
I have my current guest network built on top of my production network. The separation between guest- and corporate network is done using a VLAN – once you connect to the wireless guest network, you’re in guest VLAN that forwards your packets to a guest router and off toward the Internet.
Our security team claims that this design is not secure enough. They claim a user would be able to attach somehow to the switch and jump between VLANs, suggesting that it would be better to run guest access over a separate physical network.
Decades ago, VLAN implementations were buggy, and it was possible (using a carefully crafted stack of VLAN tags) to insert packets from one VLAN to another (see also: VLAN hopping).
RSA vs ECDSA in DNSSEC
Is it time to jump over from RSA to ECDSA in DNSSEC?Rockport’s Switchless Networking – Don’t Call It A SmartNIC
Rockport Networks has announced a switchless data center networking product that targets high-performance compute clusters running latency-sensitive workloads. Instead of switches in a leaf-spine or Clos fabric design, Rockport builds a multi-path mesh using network cards installed in the PCIe slots of servers and storage systems.
The post Rockport’s Switchless Networking – Don’t Call It A SmartNIC appeared first on Packet Pushers.
Bringing Security up to the Speed of the Cloud
There is no reason for security to lag behind and stick to old models when there are the capabilities and infrastructure to enable cloud-first network security.The 400G Era
As an industry leader in data-driven networking, Arista’s introduction of 400G platforms in 2019 intersected the emerging needs of hyper-scale cloud and HPC customers to dramatically increase bandwidth for specific ultra-high performance applications.
A Brief History of the Meris Botnet
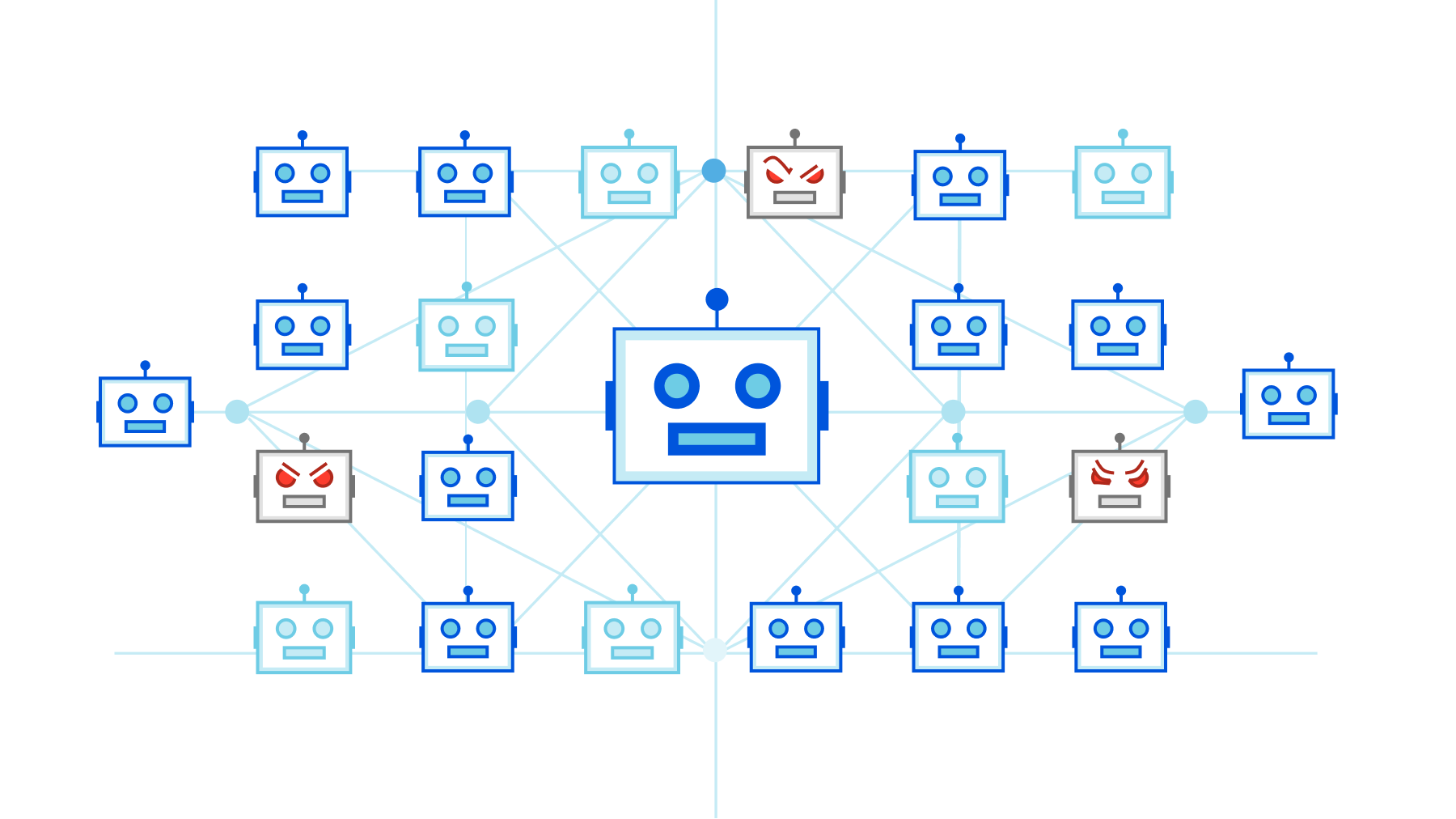
Meris first got our attention due to an exceptionally large 17.2 million requests per second (rps) DDoS attack that it launched against one of our customers. This attack, along with subsequent attacks originated by the Meris botnet, was automatically detected and mitigated by our DDoS protection systems. Cloudflare customers, even ones on the free plan, are protected against Meris attacks.
Over the past months, we’ve been tracking and analyzing the activity of the Meris botnet. Some main highlights include:
- Meris targets approximately 50 different websites every single day with a daily average of 104 unique DDoS attacks.
- More than 33% of all Meris DDoS attack traffic targeted China-based websites.
- More than 12% of all websites that were attacked by Meris are operated by US-based companies.
View more Meris attack insights and trends in the interactive Radar dashboard.
So what is Meris?
Meris (Latvian for plague) is the name of an active botnet behind a series of recent DDoS attacks that have targeted thousands of websites around the world. It was originally detected in late June 2021 by QRator in joint research they conducted with Yandex. Their initial research identified 30,000 to 56,000 bots, but they estimated that the numbers Continue reading
Anycast in Segment Routing
MPLS or Anycast Routing – for a long time, you had to choose one. Segment Routing allows you to have both.
Introduction
It’s hard to overstate how important anycast routing is. DNS root servers and CDN rely on it to …
