Arista’s Evolution to Data-Driven Networking
Arista’s EOS (Extensible Operating System) has been nurtured over the past decade, taking the best principles of extensible, open and scalable networks. While SDN evangelists insisted that the right way to build networks started with the decoupling of hardware and software in the network, manipulated by a centralized, shared controller, many companies failed to provide the core customer requisite in a clean software architecture and implementation coupled with key technical differentiation. This has been the essence of Arista EOS.
Collect hashes from remote computers
I was recently asked to create a script that should calculate the hash values of all files on remote computers. The collection must be done in parallel on all computers. My choice fell on Bash because it allows to quickly collect hashes using a combination of SSH, sshpass, find and hash (coreutils package). The collect_hashes.sh script […]Continue reading...
Where Would You Need DNS Anycast?
One of the publicly observable artifacts of the October 2021 Facebook outage was an intricate interaction between BGP routing and their DNS servers needed to support optimal anycast configuration. Not surprisingly, it was all networking engineers' fault according to some opinions1
There’s no need for anycast2/BGP advertisement for DNS servers. DNS is already highly available by design. Only network people never understand that, which leads to overengineering.
It’s not that hard to find a counter-argument3: while it looks like there are only 13 root name servers4, each one of them is a large set of instances advertising the same IP prefix5 to the Internet.
Where Would You Need DNS Anycast?
One of the publicly observable artifacts of the October 2021 Facebook outage was an intricate interaction between BGP routing and their DNS servers needed to support optimal anycast configuration. Not surprisingly, it was all networking engineers’ fault according to some opinions1
There’s no need for anycast2/BGP advertisement for DNS servers. DNS is already highly available by design. Only network people never understand that, which leads to overengineering.
It’s not that hard to find a counter-argument3: while it looks like there are only 13 root name servers4, each one of them is a large set of instances advertising the same IP prefix5 to the Internet.
Customized COSU Device Management Solutions
Once connected to the network, COSU devices should be monitored to determine where they are located and whether use conforms to policy guidelines.Javascript Notes: Variables
Like most languages, variables in Javascript are defined with the = operator. There are 3 different keywords that can be used to define a variable. var - Depricated, should not be used for ES6+. let - Variable can be re-assigned. Value can be mutated. const - Variable cannot be...continue reading
Vapor IO Realizes Open Grid Vision With INZONE 5G Edge Services
One of the defining characteristics of edge applications is the need for low latency to absorb and analyze data from connected devices deployed in locations such as retail stores, manufacturing facilities, distribution centers, and municipal infrastructure. Until recently, most chatter about “the edge” has been vague, often conflating the extension of cloud service delivery to […]
The post Vapor IO Realizes Open Grid Vision With INZONE 5G Edge Services appeared first on Packet Pushers.
Tech Bytes: Advania Chooses Apstra For Data Center Operations (Sponsored)
Today on the Tech Bytes podcast, sponsored by Juniper, we talk with a customer of Juniper’s Apstra intent-based networking data center software. IT solutions provider Advania uses Apstra internally to operate its own data centers, as well as for customer engagements.
The post Tech Bytes: Advania Chooses Apstra For Data Center Operations (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Advania Chooses Apstra For Data Center Operations (Sponsored)
Today on the Tech Bytes podcast, sponsored by Juniper, we talk with a customer of Juniper’s Apstra intent-based networking data center software. IT solutions provider Advania uses Apstra internally to operate its own data centers, as well as for customer engagements.Sunburst
The recently released open source Sunburst application provides a real-time visualization of the protocols running a network. The Sunburst application runs on the sFlow-RT real-time analytics platform, which receives standard streaming sFlow telemetry from switches and routers throughout the network to provide comprehensive visibility.docker run -p 8008:8008 -p 6343:6343/udp sflow/prometheusThe pre-built sflow/prometheus Docker image packages sFlow-RT with the applications for exploring real-time sFlow analytics. Run the command above, configure network devices to send sFlow to the application on UDP port 6343 (the default sFlow port) and connect with a web browser to port 8008 to access the user interface.
The chart at the top of this article demonstrates the visibility that sFlow can provide into nested protocol stacks that result from network virtualization. For example, the most deeply nested set of protocols shown in the chart is:
- eth: Ethernet
- q: IEEE 802.1Q VLAN
- trill: Transparent Interconnection of Lots of Links (TRILL)
- eth: Ethernet
- q: IEEE 802.1Q VLAN
- ip: Internet Protocol (IP) version 4
- udp: User Datagram Protocol (UDP)
- vxlan: Virtual eXtensible Local Area Network (VXLAN)
- eth: Ethernet
- ip Internet Protocol (IP) version 4
- esp IPsec Encapsulating Continue reading
VXLAN: Virtualizing Data Center Networks for the Cloud Era
This blog reviews what VXLAN is, why it was developed, how it is being used in data centers, and advantages over other virtualization technologies.
The post VXLAN: Virtualizing Data Center Networks for the Cloud Era appeared first on Pluribus Networks.
VXLAN: Virtualizing Data Center Networks for the Cloud Era
Since VXLAN was introduced in 2014 it has become an important component of modern data center network fabrics. This blog reviews what VXLAN is, why it was developed, how it is being used in data centers, and advantages over other virtualization technologies. In an upcoming blog, we will look at some innovative VXLAN applications outside the data center.
What is VXLAN?
Virtual eXtensible Local Area Network (VXLAN) is an Internet standard protocol that provides a means of encapsulating Ethernet (Layer 2) frames over an IP (Layer 3) network, a concept often referred to as “tunneling.” This allows devices and applications to communicate across a large physical network as if they were located on the same Ethernet Layer 2 network.
Tunneling approaches such as VXLAN provide an important tool to virtualize the physical network, often called the “underlay,” and allow for connectivity to be defined and managed as a set of virtual connections, called the “overlay.” These virtual connections can be created, modified and removed as needed without any change to the physical underlay network. (Mike Capuano’s blog, What to Know About Data Center Overlay Networks, provides a deeper dive on overlays.)
While VXLAN is only one Continue reading
Network Break 357: Switchless Networking? Startup Rockport Says Yes; ISPs Monetize Customer Surveillance
Take a Network Break! This week we discuss how startup Rockport Networks brings switchless networking to the data center. The FTC says ISPs are amassing and monetizing sensitive customer data. Cisco unveils new routing silicon, Juniper sees revenues rise and income fall, and more tech news.
The post Network Break 357: Switchless Networking? Startup Rockport Says Yes; ISPs Monetize Customer Surveillance appeared first on Packet Pushers.
Network Break 357: Switchless Networking? Startup Rockport Says Yes; ISPs Monetize Customer Surveillance
Take a Network Break! This week we discuss how startup Rockport Networks brings switchless networking to the data center. The FTC says ISPs are amassing and monetizing sensitive customer data. Cisco unveils new routing silicon, Juniper sees revenues rise and income fall, and more tech news.LEO Satellite Broadband: Top Considerations for Enterprise IT
The low-earth orbit satellite (LEO) space race is underway and warrants watching and continued evaluation.Sudan: seven days without Internet access (and counting)


It's not every day that there is no Internet access in an entire country. In the case of Sudan, it has been five days without Internet after political turmoil that started last Monday, October 25, 2021 (as we described).
The outage continues with almost a flat line and just a trickle of Internet traffic from Sudan. Cloudflare Radar shows that the Internet in Sudan is still almost completely cut off.
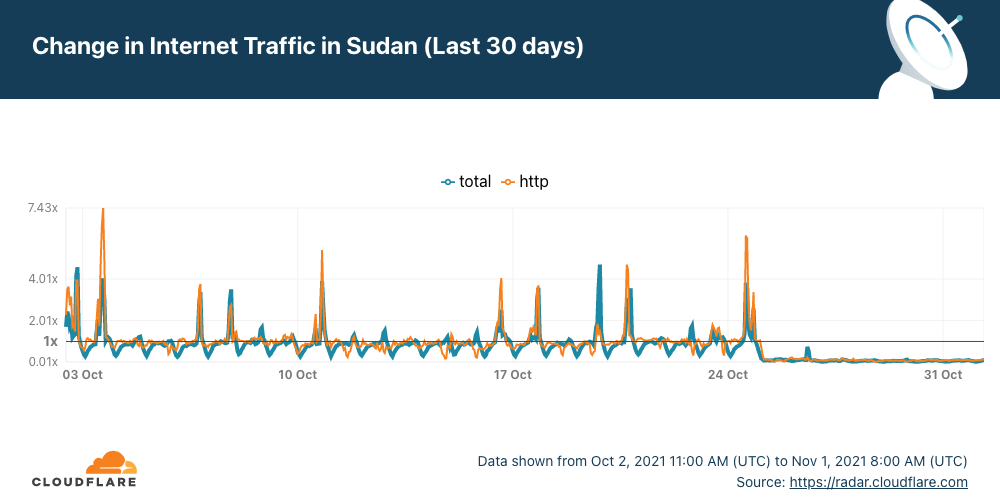
There was a blip of traffic on Tuesday at ~14:00 UTC, for about one hour, but it flattened out again, and it continues like that — anyone can track the evolution on the Sudan page of Cloudflare Radar.
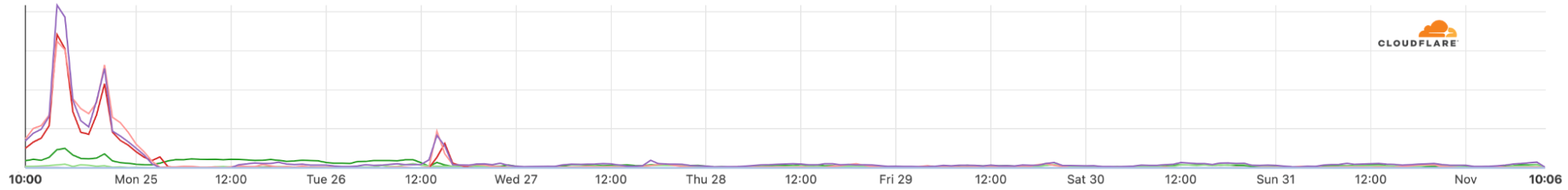
Internet shutdowns are not that rare
Internet disruptions, including shutdowns and social media restrictions, are common occurrences in some countries and Sudan is one where this happens more frequently than most countries according to Human Rights Watch. In our June blog, we talked about Sudan when the country decided to shut down the Internet to prevent cheating in exams, but there were situations in the past more similar to this days-long shutdown — something that usually happens when there’s political unrest.
The country's longest recorded network disruption was back in Continue reading