Day Two Cloud 115: Software-Defined Interconnects With Console Connect (Sponsored)
Today's Day Two Cloud sponsored episode dives into software-defined interconnects. The big idea is that you go up to a Web browser, click a few times, and now you've got a circuit stood up between your data center and AWS, or between you and a business partner, and so on. We'll get into the details about how it's done with Console Connect, a PCCW Global company.
The post Day Two Cloud 115: Software-Defined Interconnects With Console Connect (Sponsored) appeared first on Packet Pushers.
Day Two Cloud 115: Software-Defined Interconnects With Console Connect (Sponsored)
Today's Day Two Cloud sponsored episode dives into software-defined interconnects. The big idea is that you go up to a Web browser, click a few times, and now you've got a circuit stood up between your data center and AWS, or between you and a business partner, and so on. We'll get into the details about how it's done with Console Connect, a PCCW Global company.Cloudflare Images Now Available to Everyone
Today, we are launching Cloudflare Images for all customers. Images is a single product that stores, resizes, optimizes and serves images. We built Cloudflare Images so customers of all sizes can build a scalable and affordable image pipeline in minutes.
Store images efficiently
Many legacy image pipelines are architected to take an image and create multiple copies of it to account for different sizes and formats. These copies are then stored in a storage bucket and delivered using a CDN. This architecture can be hard to maintain and adds infrastructure cost in unpredictable ways.
With Cloudflare Images, you don’t need to worry about creating and storing multiple versions of the same image in different sizes and formats. Cloudflare Images makes a clear distinction between your stored images and the variants. Once you upload an image, you can apply any defined variant to the uploaded image. The variants and different formats don’t count towards your stored images quota.
This means that when a user uploads a picture that you need to resize in three different ways and serve in two different formats, you pay for one stored image instead of seven different images (the original, plus three variants for each of Continue reading
Discovering what’s slowing down your website with Web Analytics


Web Analytics is Cloudflare’s privacy-focused real user measurement solution. It leverages a lightweight JavaScript beacon and does not use any client-side state, such as cookies or localStorage, to collect usage metrics. Nor does it “fingerprint” individuals via their IP address, User Agent string, or any other data.
Cloudflare Web Analytics makes essential web analytics, such as the top-performing pages on your website and top referrers, available to everyone for free, and it’s becoming more powerful than ever.
Focusing on Performance
Earlier this year we merged Web Analytics with our Browser Insights product, which enabled customers proxying their websites through Cloudflare to evaluate visitors’ experience on their web properties through Core Web Vitals such as Largest Contentful Paint (LCP) and First Input Delay (FID).
It was important to bring the Core Web Vitals performance measurements into Web Analytics given the outsized impact that page load times have on bounce rates. A page load time increase from 1s to 3s increases bounce rates by 32% and from 1s to 6s increases it by 106% (source).
Now that you know the impact a slow-loading web page can have on your visitors, it’s time for us to make Continue reading
Optimizing images on the web
Images are a massive part of the Internet. On the median web page, images account for 51% of the bytes loaded, so any improvement made to their speed or their size has a significant impact on performance.
Today, we are excited to announce Cloudflare’s Image Optimization Testing Tool. Simply enter your website’s URL, and we’ll run a series of automated tests to determine if there are any possible improvements you could make in delivering optimal images to visitors.
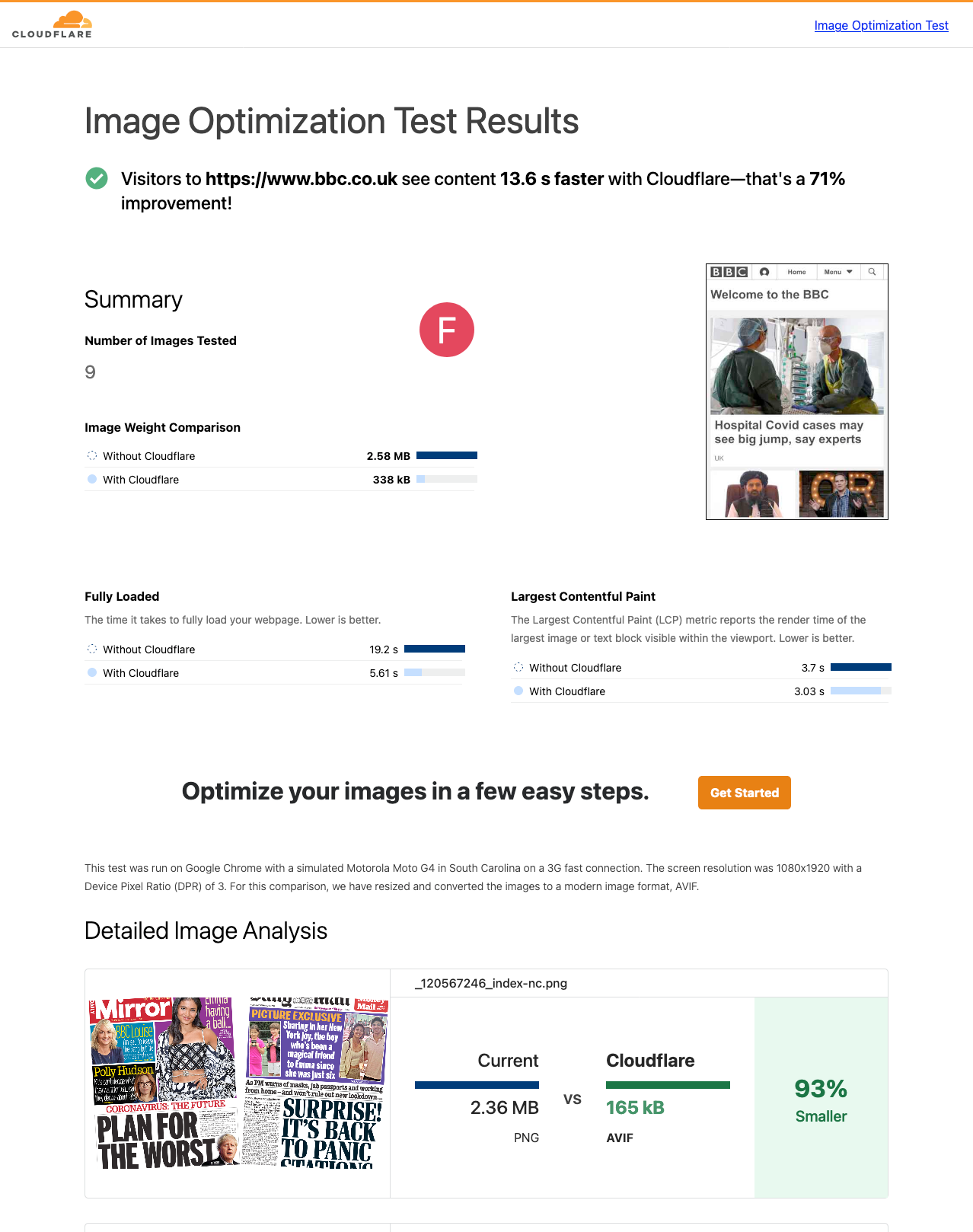
How users experience speed
Everyone who has ever browsed the web has experienced a website that was slow to load. Often, this is a result of poorly optimized images on that webpage that are either too large for purpose or that were embedded on the page with insufficient information.
Images on a page might take painfully long to load as pixels agonizingly fill in from top-to-bottom; or worse still, they might cause massive shifts of the page layout as the browser learns about their dimensions. These problems are a serious annoyance to users and as of August 2021, search engines punish pages accordingly.
Understandably, slow page loads have an adverse effect on a page's “bounce rate” which is the percentage of Continue reading
New: ipSpace.net Design Clinic
In early September, I started yet another project that’s been on the back burner for over a year: ipSpace.net Design Clinic (aka Ask Me Anything Reasonable in a more structured format). Instead of collecting questions and answering them in a podcast (example: Deep Questions podcast), I decided to make it more interactive with a live audience and real-time discussions. I also wanted to keep it valuable to anyone interested in watching the recordings, so we won’t discuss obscure failures of broken designs or dirty tricks that should have remained in CCIE lab exams.
New: ipSpace.net Design Clinic
In early September, I started yet another project that’s been on the back burner for over a year: ipSpace.net Design Clinic (aka Ask Me Anything Reasonable in a more structured format). Instead of collecting questions and answering them in a podcast (example: Deep Questions podcast), I decided to make it more interactive with a live audience and real-time discussions. I also wanted to keep it valuable to anyone interested in watching the recordings, so we won’t discuss obscure failures of broken designs or dirty tricks that should have remained in CCIE lab exams.
Bringing the Power of SDN Automation to BGP EVPN Overlays
Some customers have asked whether Pluribus can create an overlay using BGP EVPN throughout the fabric, like other vendors do, and not just at the edge. The answer is “yes” we absolutely can do that, but unlike other vendors, we can apply the power of SDN automation to make it simpler.
The post Bringing the Power of SDN Automation to BGP EVPN Overlays appeared first on Pluribus Networks.
Russ’ Rules of Network Design
We have the twelve truths of networking, and possibly Akin’s Laws, but is there a set of rules for network design? I couldn’t find one, so I decided to create one, containing 18 laws I’ve listed below.
Russ’ Rules of Network Design
- If you haven’t found the tradeoffs, you haven’t looked hard enough.
- Design is an iterative process. You probably need one more iteration than you’ve done to get it right.
- A design isn’t finished when everything needed is added, it’s finished when everything possible is taken away.
- Good design isn’t making it work, it’s making it fail gracefully.
- Effective, elegant, efficient. All other orders are incorrect.
- Don’t fix blame; fix problems.
- Local and global optimization are mutually exclusive.
- Reducing state always reduces optimization someplace.
- Reducing state always creates interaction surfaces; shallow and narrow interaction surfaces are better than deep and broad ones.
- The easiest place to improve or screw up a design is at the interaction surfaces.
- The optimum is almost always in the middle someplace; eschew extremes.
- Sometimes its just better to start over.
- There are a handful of right solutions; there is an infinite array of wrong ones.
- You are not immensely smarter than anyone else in Continue reading
Troubleshooting Webinar this Friday

I’m teaching my troubleshooting webinar this Friday. I’ve revamped the slides entirely, so this will likely be a big change for anyone who’s attended previous versions of this. Three hours, 109 slides, and interaction through the chat window … all to develop some really good skills in how to troubleshoot. For those who are curious, I was taught formal troubleshooting skills in my early life in electronics, learning my lessons on ILS, RADAR, and radio systems of various kinds. This webinar is my adaptation of those skills for network engineers.
What’s your Digital Dilemma?
There are many ways to describe the need for IT organizations to do things better. There are multiple opportunities to get it wrong. Certainly, compromising today in the name of tomorrow is what many IT leaders now call the digital dilemma. Derek Britton of Micro Focus offers the vendor perspective.Back-to-Office Canceled: The New Phase of IT Spending
As we hit IT budget season for 2022, many organizations are delaying their back-to-the-office plans. Here's what that will mean for CIO IT spending priorities next year.Blessay: Enterprise DevOps is about Hiring More People
 The hidden secret of DevOps is headcount justification
The hidden secret of DevOps is headcount justification
Response: Survey Reveals Talent Shortages as Biggest Barrier to Emerging Technologies Adoption
 Lack of training not lack of talent
Lack of training not lack of talent
Stateful Switchover (SSO) 101
Stateful Switchover (SSO) is another seemingly awesome technology that can help you implement high availability when facing a broken non-redundant network design. Here’s how it’s supposed to work:
- A network device runs two copies of the control plane (primary and backup);
- Primary control plane continuously synchronizes its state with the backup control plane;
- When the primary control plane crashes, the backup control plane already has all the required state and is ready to take over in moments.
Delighted? You might be disappointed once you start digging into the details.
Stateful Switchover (SSO) 101
Stateful Switchover (SSO) is another seemingly awesome technology that can help you implement high availability when facing a broken non-redundant network design. Here’s how it’s supposed to work:
- A network device runs two copies of the control plane (primary and backup);
- Primary control plane continuously synchronizes its state with the backup control plane;
- When the primary control plane crashes, the backup control plane already has all the required state and is ready to take over in moments.
Delighted? You might be disappointed once you start digging into the details.