Kubernetes observability challenges in cloud-native architecture
Kubernetes is the de-facto platform for orchestrating containerized workloads and microservices, which are the building blocks of cloud-native applications. Kubernetes workloads are highly dynamic, ephemeral, and are deployed on a distributed and agile infrastructure. Although the benefits of cloud-native applications managed by Kubernetes are plenty, Kubernetes presents a new set of observability challenges in cloud-native applications.
Let’s consider some observability challenges:
- Data silos – Traditional monitoring tools specialize in collecting metrics at the application and infrastructure level. Given the highly dynamic, distributed, and ephemeral nature of cloud-native applications, this style of metrics collection creates data in silos that need to be stitched together in the context of a service in order to enable DevOps and SREs to debug service issues (e.g. slow response time, downtime, etc.). Further, if DevOps or service owners add new metrics for observation, data silos can cause broken cross-references and data misinterpretation, leading to data misalignment, slower communication, and incorrect analysis.
- Data volume and granular components – Kubernetes deployments have granular components such as pods, containers, and microservices that are running on top of distributed and ephemeral infrastructure. An incredibly high volume of granular data is generated at each layer as alerts, logs, and Continue reading
Docker, Openvswitch & Aruba VXLAN Network Build
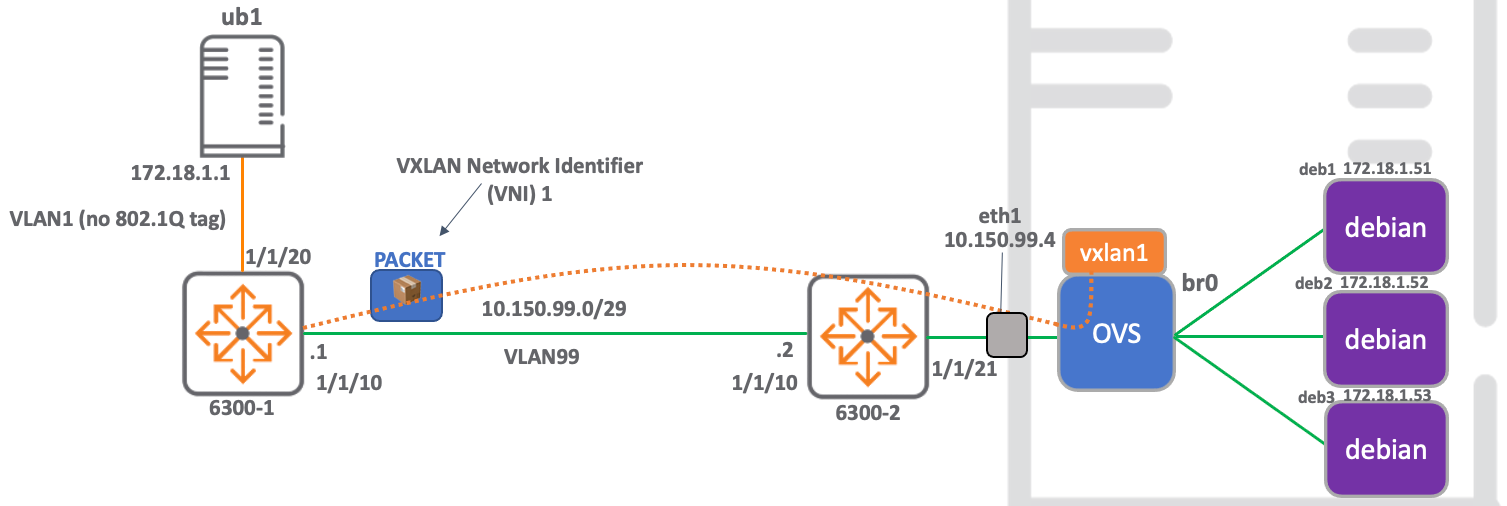
This blog provides details of how to build a static VXLAN network that connects physical hardware to a virtualised network, enabling communication from docker containers to external nodes.
The build is comprised of a hardware ArubaOS-Switch acting as a VTEP and an openvswitch VTEP running on an ubuntu server, which is the host for the docker containers.
This network also serves to prove interoperability between the ArubaOS-Switch VXLAN stack and that running on openvswitch.
The use of docker containers as target nodes enables rapid deploy and tear-down of network components, which is particularly useful in lab environments for testing.
Kit List
2 x ArubaOS-CX 6300 hardware switch (only 1 is required.)
1 x HP EliteDesk PC running Hyper-V hosting an ubuntu 21.04 VM
1 x HP EliteDesk PC running ubuntu 21.04 bare metal.
Notes:
I used a VM for the openvswitch / docker linux server to take advantage of snapshots while documenting this build. This server can be any linux server.
Network Diagram
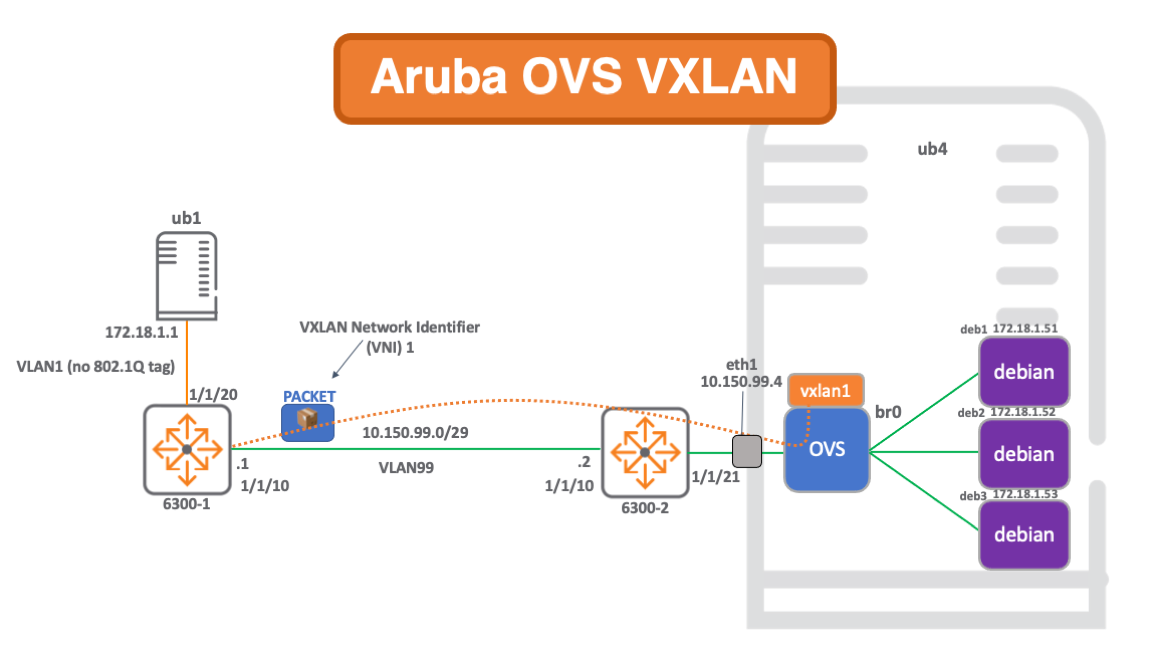
Build Steps
Configure the ArubaOS-CX hardware switch
- Configure the ArubaOS-CX switch and local server (172.18.1.1) so that they are in the same subnet and can ping each other.
- Configure the ArubaOS-CX Continue reading
Hedge 95: Mike Bushong and Agile
We’ve all been told agile is better … but as anyone who’s listened here long enough knows, if you haven’t found the tradeoffs, you haven’t looked hard enough. What is agile better for? Are there time when agile is better, and times when more traditional project management processes are better? Mike Bushong joins Tom Ammon, Eyvonne Sharp, and Russ White on this, the 95th episode of the Hedge, to discuss his experience with implementing agile, where it works, and where it doesn’t.
Day Two Cloud 110: Automation’s Unintended Consequences – The Bunny.net Outage Saga
Today's Day Two Cloud podcast walks through a massive outage that hit CDN provider Bunny.net. An automated update triggered cascading failures that essentially took the company offline for two frantic hours. The company shared a detailed postmortem of what happened, and we're joined by company founder Dejan Pelze to walk us through the issues and share lessons learned about infrastructure, automation, and dependencies.
The post Day Two Cloud 110: Automation’s Unintended Consequences – The Bunny.net Outage Saga appeared first on Packet Pushers.
Day Two Cloud 110: Automation’s Unintended Consequences – The Bunny.net Outage Saga
Today's Day Two Cloud podcast walks through a massive outage that hit CDN provider Bunny.net. An automated update triggered cascading failures that essentially took the company offline for two frantic hours. The company shared a detailed postmortem of what happened, and we're joined by company founder Dejan Pelze to walk us through the issues and share lessons learned about infrastructure, automation, and dependencies.New in NFA v21.08: AS Path Length filter, BGP routes visibility and more.
We’ve had a busy month here at Noction and have just released the latest NFA version. The product’s new features and capabilities
The post New in NFA v21.08: AS Path Length filter, BGP routes visibility and more. appeared first on Noction.
LISP – OMP – BGP EVPN Interoperability – Part VIII: LISP, OMP, and BGP EVPN Comparison
IP reachability
Every Overlay Network solution requires IP reachability between edge devices via Underlay Network. This section explains the basic routing solution in Underlay Network from Campus Fabric, SD-WAN, and Datacenter Fabric perspectives. Figure 7-1 illustrates the IP reachability requirements for Campus Fabric, SD-WAN, and Datacenter Fabric.
Figure 7-1: IP Reachability Requirements.
Continue reading
Infrastructure 1. Building Virtualized Environment with Debian Linux and Proxmox on HP and Supermicro
Hello my friend,
Just the last week we finished our Zero-to-Hero Network Automation Training, which was very intensive and very interesting. The one could think: it is time for vacation now!.. Not quite yet. We decided to use the time wisely and upgrade our lab to bring possibilities for customers to use it. Lab upgrade means a major infrastructure project, which involves brining new hardware, changing topology and new software to simplify its management. Sounds interesting? Jump to details!
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
What is Infrastructure Automation?
Each and every element of your entire IT landscape requires two actions. It shall be monitored and it shall be managed. Being managed means that the element shall be configured and this is the first step for all sort of automations. Configuration management is a perfect use case to start automating your infrastructure, which spans servers, network devices, VMs, containers and much more. And we are here to help you to do Continue reading
Storage Should Not be Treated Like an Unloved Part of IT
Because storage needs and technologies have diversified greatly over the past 20 years, it makes sense to enact an IT strategy that coalesces with overall IT architecture planning.Noction Flow Analyzer v 21.08 has just been released.
The post Noction Flow Analyzer v 21.08 has just been released. appeared first on Noction.
