Heavy Networking 573: Using Application Dictionaries For Better Security Policy Management
Today's Heavy Networking thinks hard about how to manage security policy in modern IT infrastructure. We get into sources of truth, application modeling and application dictionaries, approval workflows, and more--all in the context of automation. Our guests are Ken Celenza and Brett Lykins from Network To Code.
The post Heavy Networking 573: Using Application Dictionaries For Better Security Policy Management appeared first on Packet Pushers.
Heavy Networking 573: Using Application Dictionaries For Better Security Policy Management
Today's Heavy Networking thinks hard about how to manage security policy in modern IT infrastructure. We get into sources of truth, application modeling and application dictionaries, approval workflows, and more--all in the context of automation. Our guests are Ken Celenza and Brett Lykins from Network To Code.Cisco’s Personal Insights: Good Intentions On The Road To Hell
New behavioral monitoring capabilities in Cisco Webex are being positioned as insights to improve employee well being and work-life integration, but adding layers of surveillance isn't the way to create a more humane workplace.
The post Cisco’s Personal Insights: Good Intentions On The Road To Hell appeared first on Packet Pushers.
Real Life Ensues

Hey everyone! You probably noticed that I didn’t post a blog last week. Which means for the first time in over ten years I didn’t post one. The streak is done. Why? Well, real life decided to take over for a bit. I was up to my eyeballs in helping put on our BSA council Wood Badge course. I had a great time and completely lost track of time while I was there. And that means I didn’t get a chance to post something. Which is a perfect excuse to discuss why I set goals the way that I do.
Consistency Is Key
I write a lot. Between my blog here and the writing I do for Gestalt IT I do at least 2-3 posts a week. That’s on top of any briefing notes I type out or tweets I send when I have the energy to try and be funny. For someone that felt they weren’t a prolific writer in the past I can honestly say I spend a lot of time writing out things now. Which means that I have to try and keep a consistent schedule of doing things or else I will get swamped by some other Continue reading
Announcing Cloudflare’s Database Partners


Cloudflare Workers is the easiest way for developers to deploy their application’s code with performance, scale and security baked in. No configuration necessary. Worker code scales to serve billions of requests close to your users across Cloudflare’s 200+ data centers.
But that’s not the only interesting problem we need to solve. Every application has two parts: code and state.
State isn’t always the easiest to work in a massive distributed system. When an application runs in 200+ data centers simultaneously, there’s an inherent tradeoff between distributing the data for better performance, availability, scale, and guaranteeing that all data centers see the same data at a given point in time.
Our goal is to make state at the edge seamless. We started that journey with Workers KV, which provides low-latency access to globally distributed data. We’re since added Durable Objects, with strong consistency and the ability to design coordination patterns on top of Workers. We’re continuing to invest in and build out these products.
However, some use cases aren’t easily implemented with Workers KV or Durable Objects. Think querying complex datasets, or communicating with an existing system-of-record. Even if we built this functionality ourselves, there will always be customers who want Continue reading
Cloudflare Stream now supports NFTs

Cloudflare Stream has been helping creators publish their videos online without having to think about video quality, device compatibility, storage buckets or digging through FFmpeg documentation. These creators want to be able to claim ownership of their works and assert control over how that ownership claim is transferred. Increasingly, many of those creators are looking to Non-Fungible Tokens (NFTs).
NFTs are a special type of smart contract that allows provable ownership of the contract on the blockchain. Some call NFTs collectibles because like coins or stamps, collectors who enjoy them buy, sell and trade them. Collectors keep track of NFTs on the Ethereum blockchain which acts as a shared source of truth of all the activity.
Today, we’re introducing a new API that takes a ERC-721 token ID and contact address and sets it on a video so every video on Stream can be represented with an NFT.
curl -X POST -H "Authorization: Bearer $AUTH_TOKEN" --data '{"contract":"0x57f1887a8bf19b14fc0d912b9b2acc9af147ea85","token":"5"}' https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/stream/$VIDEO_ID/nft
Once you set it, you cannot change these values so be sure to set it to an NFT you own! If you set a video you own to an NFT you don’t own, the owner of the NFT can claim Continue reading
Node.js support in Cloudflare Workers
We released Cloudflare Workers three years ago, making edge compute accessible to the masses with native support for the world’s most ubiquitous language — JavaScript.
The Workers platform has transformed so much since its launch. Developers can not only write sandboxed code at our edge, they can also store data at the edge with Workers KV and, more recently, coordinate state within our giant network using Durable Objects. Now, we’re excited to share our support of an 11 year old technology that’s still going strong: Node.js.
Node.js made a breakthrough by enabling developers to build both the frontend and the backend with a single language. It took JavaScript beyond the browser and into the server by using Chrome’s JavaScript engine, V8.
Workers is also built on V8 Isolates and empowers developers in a similar way by allowing you to create entire applications with only JavaScript — except your code runs across Cloudflare’s data centers in over 100 countries.
Our Package Support Today
There is nothing more satisfying than importing a library and watching your code magically work out-of-the-box.
For over 20k packages, Workers supports this magic already: any Node.js package that uses webpack or another polyfill Continue reading
Introducing workers.new, custom builds, and improved logging for Workers


Cloudflare Workers® aims to be the easiest and most powerful platform for developers to build and deploy their applications. With Workers, you can quickly solve problems without having to wonder: “is this going to scale?”
You write the JavaScript and we handle the rest, from distribution to scaling and concurrency.
In the spirit of quickly solving problems, we’re excited to launch three new improvements to the Workers experience, so you can take your next idea and ship it even faster.
Introducing... workers.new

First, we’re introducing https://workers.new, a shortcut that takes you directly to a JavaScript editor for creating a new Worker. Anytime you have a cool idea, need a quick fix to a problem, or just want to debug some JavaScript, you now have a simple way to go from idea to prototype. What’s more is you don’t even need to deploy the Worker to try it out!
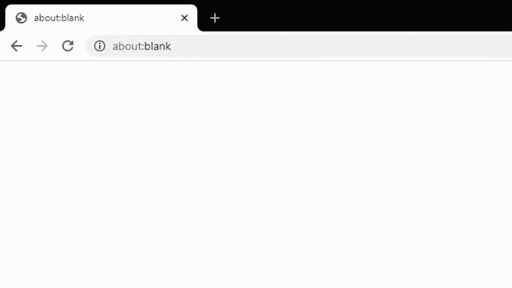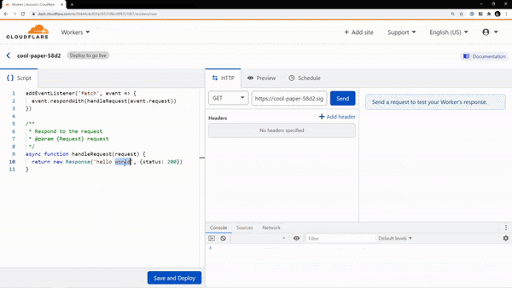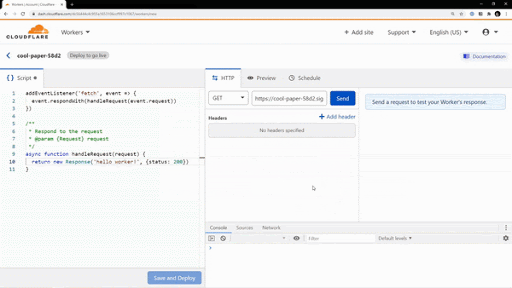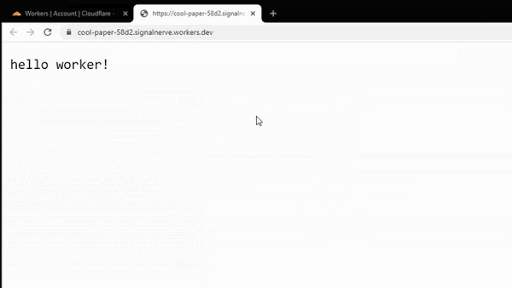
We’ve also updated the default Worker template to help you go a few steps beyond the typical “Hello, World!”. When you open the editor, you’ll now see a few examples that demonstrate how to redirect requests, modify headers, and parse responses.
Customize your build scripts

For developers Continue reading
Video: Transparent Bridging Fundamentals
Years ago I wrote a series of blog posts comparing transparent bridging and IP routing, and creating How Networks Really Work materials seemed like a perfect opportunity to make that information more structured, starting with Transparent Bridging Fundamentals.
Video: Transparent Bridging Fundamentals
Years ago I wrote a series of blog posts comparing transparent bridging and IP routing, and creating How Networks Really Work materials seemed like a perfect opportunity to make that information more structured, starting with Transparent Bridging Fundamentals.
Sky’s the Limit: Pluribus Keeps Growing with Second Consecutive Financial Times ‘Americas’ Fastest Growing Companies’ Ranking
I’m thrilled to share news that Pluribus has been named to the list of the Americas’ Fastest Growing Companies, a...
The post Sky’s the Limit: Pluribus Keeps Growing with Second Consecutive Financial Times ‘Americas’ Fastest Growing Companies’ Ranking appeared first on Pluribus Networks.
The Hedge 79: Brooks Westbrook and the Data Driven Lens
Many networks are designed and operationally drive by the configuration and management of features supporting applications and use cases. For network engineering to catch up to the rest of the operational world, it needs to move rapidly towards data driven management based on a solid understanding of the underlying protocols and systems. Brooks Westbrook joins Tom Amman and Russ White to discuss the data driven lens in this episode of the Hedge.
What Does Aruba Do With No SASE To Sell? It Changes The Conversation
SASE was clearly on the minds of Aruba executives during its Atmosphere 2021 event, but without an actual SASE offering in its portfolio, Aruba had to steer the conversation toward SD-WAN and Aruba's role as a partner that can help enterprises transform at their own pace.
The post What Does Aruba Do With No SASE To Sell? It Changes The Conversation appeared first on Packet Pushers.
Network Architecture 2021: Old Network Technologies Remain Relevant
Solved problems are still there but they don't need attention
The post Network Architecture 2021: Old Network Technologies Remain Relevant appeared first on Packet Pushers.
Benefits Of Coworking Spaces
Coworking spaces have seen a rapid increase in recent years. In 2018, coworking spaces in the U.S increased by more than 16%. On the other hand, these spaces outside the U.S increased by 36%. So, what is the reason for this increase?
Are coworking spaces that effective? Let’s find out.
1. People Find Work More Meaningful In Coworking Spaces
We are all familiar with office politics. It exists in every business, and there is no way out of it. However, freelancers sharing coworking spaces don’t feel the need to put another persona when they work here.
That is because they are among people doing different kinds of work, and no one competes with each other. That is why it enhances the identity of one’s own work. Through this strong identity, people find more meaning as what they do seems more unique and interesting in such an environment.
2. Networking
Networking is perhaps one of the most important benefits of utilizing a coworking space. People connect with each other that they would not normally meet if it wasn’t for the space. These connections help in being part of a community.
However, if you are running a small business through Continue reading