“It Only Took 22 Years to Get an Education”
Note: This Post was written by Fish’s Mom, Dr Patricia Fishburne No one in my family had gone to college and, having married at 18, there seemed little likelihood that I would either. My husband, on the other hand, had... Read More ›
The post “It Only Took 22 Years to Get an Education” appeared first on Networking with FISH.
Azure Route Server: The Challenge
Imagine you decided to deploy an SD-WAN (or DMVPN) network and make an Azure region one of the sites in the new network because you already deployed some workloads in that region and would like to replace the VPN connectivity you’re using today with the new shiny expensive gadget.
Everyone told you to deploy two SD-WAN instances in the public cloud virtual network to be redundant, so this is what you deploy:
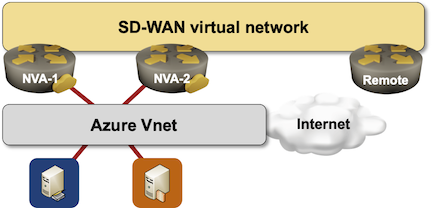
Azure Route Server: The Challenge
Imagine you decided to deploy an SD-WAN (or DMVPN) network and make an Azure region one of the sites in the new network because you already deployed some workloads in that region and would like to replace the VPN connectivity you’re using today with the new shiny expensive gadget.
Everyone told you to deploy two SD-WAN instances in the public cloud virtual network to be redundant, so this is what you deploy:

What ‘Star Trek’ Teaches Us About AI and IT
AIOps holds the promise to help with mundane, time-consuming tasks, and more, thus allowing IT pros to find new and meaningful ways to do their jobs.Notes from the DNS Privacy Workshop at NDSS 2021
There are many issues that lurk just below the surface of the DNS, but in recent years one topic has been very prominent, namely privacy. You see the DNS is a precursor to almost everything we do on the Internet. And this is valuable information.You Can Always Add Another Layer of Indirection (RFC1925, Rule 6a)
Many within the network engineering community have heard of the OSI seven-layer model, and some may have heard of the Recursive Internet Architecture (RINA) model. The truth is, however, that while protocol designers may talk about these things and network designers study them, very few networks today are built using any of these models. What is often used instead is what might be called the Infinitely Layered Functional Indirection (ILFI) model of network engineering. In this model, nothing is solved at a particular layer of the network if it can be moved to another layer, whether successfully or not.
For instance, Ethernet is the physical and data link layer of choice over almost all types of physical medium, including optical and copper. No new type of physical transport layer (other than wireless) can succeed unless if can be described as “Ethernet” in some regard or another, much like almost no new networking software can success unless it has a Command Line Interface (CLI) similar to the one a particular vendor developed some twenty years ago. It’s not that these things are necessarily better, but they are well-known.
Ethernet, however, goes far beyond providing physical layer connectivity. Because many applications rely Continue reading
InfluxDB 2.0 released
InfluxData advances possibilities of time series data with general availability of InfluxDB 2.0 announced the production release of InfluxDB 2.0. This article demonstrates how to import sFlow data into InfluxDB 2.0 using sFlow-RT in order to provide visibility into network traffic.
Real-time network and system metrics as a service describes how to use Docker Desktop to replay previously captured sFlow data. Follow the instructions in the article to start an instance of sFlow-RT.
Create a directory for InfluxDB to use to store data and configuration settings:
mkdir dataNow start InfluxDB using the pre-built influxdb image:
docker run --rm --name=influxdb -p 8086:8086 \
-v $PWD/data:/var/lib/influxdb2 influxdb:alpine \
--nats-max-payload-bytes=10000000
Note: sFlow-RT is collecting metrics for all the sFlow agents embedded in switches, routers, and servers. The default value of nats-max-payload-bytes (1048576) may be too small to hold all the metrics returned when sFlow-RT is queried. The error, nats: maximum payload exceeded, in InfluxDB logs indicates that the limit needs to be increased. In this example, the value has been increased to 10000000.
Now access the InfluxDB web interface at http://localhost:8086/
The screen capture above shows three scrapers configured in InfluxDB 2.0:- sflow-analyzer
URL: http://host.docker.internal:8008/prometheus/analyzer/txt - sflow-metrics
Continue reading
App Modernization Goes Mainstream Again
The reality of modernization as a survival skill for business is seen in the way modernization has morphed from competitive advantage to mainstream initiative.Control web applications with two-clicks in Cloudflare Gateway

Nearly a year ago, we announced Cloudflare for Teams, Cloudflare’s platform for securing users, devices, and data. With Cloudflare for Teams, our global network becomes your team’s network, replacing on-premise appliances and security subscriptions with a single solution delivered closer to your users — wherever they work. Cloudflare for Teams centers around two core products: Cloudflare Access and Cloudflare Gateway.
Cloudflare Gateway protects employees from security threats on the Internet and enforces appropriate use policies. We built Gateway to help customers replace the pain of backhauling user traffic through centralized firewalls. With Gateway, users instead connect to one of Cloudflare’s data centers in 200 cities around the world where our network can apply consistent security policies for all of their Internet traffic.
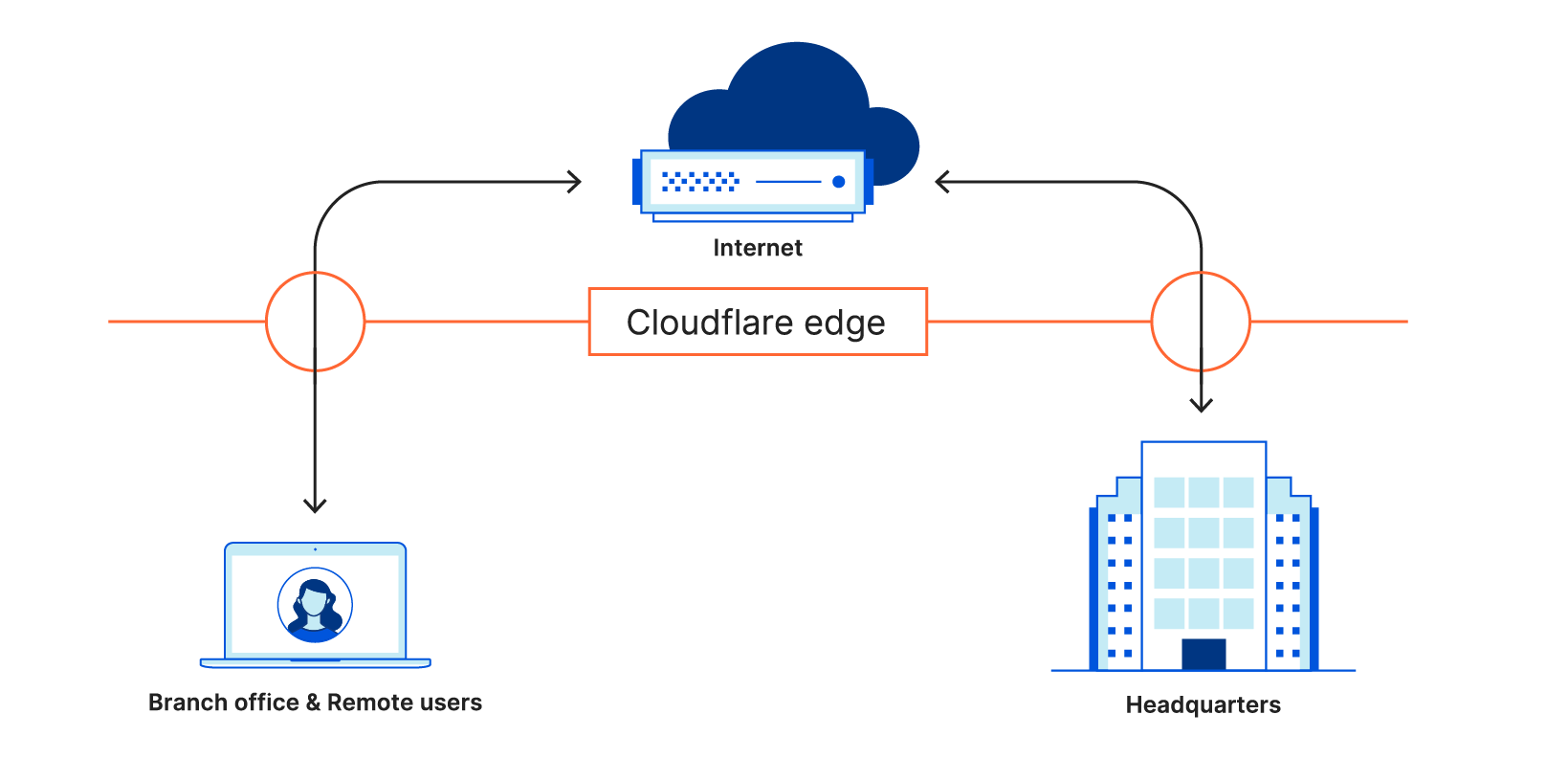
In March 2020, we launched Gateway’s first feature, a secure DNS filtering solution. With Gateway’s DNS filtering, administrators can click a single button to block known threats, like sources of malware or phishing sites. Policies can also be used to block specific risky categories, like gambling or social media. When users request a filtered site, Gateway stops the DNS query from resolving and prevents the device from connecting to a malicious destination or hostname with blocked material.
Tier 1 Carriers Performance Report: February, 2021
The post Tier 1 Carriers Performance Report: February, 2021 appeared first on Noction.
Interesting Tool: Schema Enforcer
It looks like JSON Schema is the new black. Last week I wrote about a new Ansible module using JSON Schema to validate data structures passed to it; a few weeks ago NetworkToCode released Schema Enforcer, a similar CLI tool (which means it’s easy to use it in any CI/CD pipeline).
Here are just a few things Schema Enforcer can do:
Interesting Tool: Schema Enforcer
It looks like JSON Schema is the new black. Last week I wrote about a new Ansible module using JSON Schema to validate data structures passed to it; a few weeks ago NetworkToCode released Schema Enforcer, a similar CLI tool (which means it’s easy to use it in any CI/CD pipeline).
Here are just a few things Schema Enforcer can do:
Tiling window manager
A couple of months ago it occurred to me that I’ve been manually tiling my windows. That is, I use all the screen real estate, and don’t have windows overlapping each other.
In various window manages (and on Windows) I have used Super+Left and Super+Right to divide the screen 50/50.
So why am I not running a tiling window manager? That’s literally what they do, and they allow more flexibility in how to tile, without wasting space.
Switching to tiling
A quick googling says that i3 is what I want. Fast, small, efficient. No bells and whistles.
I used it for a little while, but then because I wanted to make it even harder on myself, err… I mean to join the 21st century, I thought I’d switch from X11 to Wayland, too. Luckily there’s a Wayland Compositor that’s equilavent to the i3 Window Manager called Sway.
It’s great! I knew X11 and Gnome had issues, but I didn’t realize just how much better I feel when I don’t have to deal with their deficiencies.
Like:
- screen tearing when scrolling in terminal windows
- changing focus can take up to a second, sometimes
- X11 resets keyboard settings when it bloody feels Continue reading
Announcing the Final Candidate Slates for the 2021 Board of Trustees Elections

On behalf of the 2020-2021 Nominations Committee, I am pleased to announce the final slates of candidates for the 2021 Internet Society Board of Trustees elections.
Chapters Election
As announced to this community on March 1, we received the required number of signatures in support of Glenn McKnight’s petition to stand as a candidate in the Chapters election. No other petitions were filed for the Chapters election. Therefore, the final slate for the Chapters Election is as follows:
- Leiska Evanson
- Luis Martinez
- Glenn Carl McKnight
- Rao Naveed Bin Rais
- Muhammad Shabbir
- Niels ten Oever
Chapter voters will elect one trustee in the 2021 election.
Separately, the Board, acting pursuant to its authority under Article II, Section 1(d), of the Internet Society By-Laws, has announced its intention to offer the runner-up in the Chapters Election a one-year appointment as trustee. This will restore the board to its usual complement of 12 voting members comprised of equal numbers from all three communities: Chapters, Organizational Members and the IETF. The number of voting members fell to 11 when Olga Cavalli resigned with one year remaining in her term.
Organizational Members Election
There were no successful petitions in the Organizational Members election, so Continue reading

